Risky Biz News: Israeli spyware vendor QuaDream has allegedly shut down
In other news: NCR gets ransomwared; India passes online "fact-checking" law; and Russian hackers broke into Ukrainian security cameras to track western aid convoys.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
We're back from our one-week hiatus. While our newsletters typically cover events from the infosec industry from the past 2-3 days, this edition will cover the biggest events (not all) from the last ten days.
There's been quite the interesting news over the past week, but by far, the most interesting one—at least to us—has been the joint reports from Microsoft and CitizenLab blowing the lid on another Israeli cyber-surveillance vendor, namely a company named QuaDream.
Reports linking QuaDream to the spyware business were published in 2021 and 2022 by Haaretz and Reuters, respectively, so this is not a major revelation.
What we had from Microsoft and CitizenLab the past week were the first technical details about QuaDream's iOS hacking capabilities—a spyware tool named KingsPawn.
According to the two companies, KingsPawn was deployed using "invisible iCloud calendar invitations" sent by QuaDream customers to their targets. The invites used an exploit for iOS 14 named ENDOFDAYS to deploy KingsPawn on the device, and then used KingsPawn to exfiltrate data, track victims, and hack their online accounts.

Per Microsoft and CitizenLab, KingsPawn is just one of the tool of QuaDream's main product, the REIGN surveillance platform, which also comes with similar Android hacking capabilities. Details about QuaDream's Android spyware are still unknown.
QuaDream also appears to have tested social media hacking capabilities as well. In December 2022 [PDF], Meta said it suspended 250 Facebook and Instagram that were operated by QuaDream to "test capabilities to exfiltrate various types of data including messages, images, video and audio files, and geolocation." Meta says that once the accounts were suspended, it saw no more malicious activity.
What we know so far is that Citizen Lab was able to identify operator locations for QuaDream systems in Bulgaria, Czechia, Hungary, Ghana, Israel, Mexico, Romania, Singapore, United Arab Emirates, and Uzbekistan.
Furthermore, CitizenLab was also able to identify some of the targeted victims, which allegedly included journalists, political opposition figures, and NGO workers.
While CitizenLab didn't provide additional details, it's quite obvious QuaDream's tools are being abused for illegal surveillance operations, just like the tools of fellow surveillance vendors NSO Group and Cytrox have been used in the past.
Reuters's 2022 report linked QuaDream not only to former Israeli intelligence officials but also to former NSO Group employees who appear to have jumped ship when things were getting too hot at the company following media attention.
Per CitizenLab, QuaDream appears to have started operations in 2017 and has conducted most of its business through InReach, a Cypriot company that acted as a reseller for its tools in order to avoid the Israeli government's strict export rules. Things eventually soured, and CitizenLab says the two companies headed to court when InReach allegedly decided to keep the profits from REIGN sales for itself.
Following all the media attention the company got last week, Israeli news outlet Calcalist reports the company's execs have decided to shutter operations. (machine translated quotes below)
"According to the sources, all the company's employees were summoned for a hearing, and in practice, it has already stopped its activities.
[...]
According to sources, the company has been in a difficult situation for several months, and the research was the last nail in its coffin. Apparently, the company is no longer active, and there are only two employees left in its offices whose job it is to look after the computers and other equipment. At the same time, the board of directors is trying to sell its intellectual property."
Calcalist's reporting makes sense when you put it into context with how NSO's businesses withered once its operations became broadly associated with human rights abuses and oppressive regimes.
At this point, those former NSO members probably know they need to pull a "ransomware" and just create a new company under a new and untainted brand.
Breaches and hacks
NCR gets ransomwared: NCR, the world's largest banking and payments software maker, has confirmed that a recent data center outage was caused by a ransomware attack. According to NCR, the incident has impacted the availability of its Aloha PoS payments platform. The intrusion was claimed by the AlphV ransomware gang, which temporarily listed the company on its dark web leak site.
Cyber-attack on irrigation systems: A cyber-attack is suspected of having disrupted the operations of irrigation systems in Israel's Upper Galilee region. Water controllers for irrigating fields in the Jordan Valley and control systems for the Galil Sewage Corporation were down last week during yearly cyberattacks aimed at Israeli targets known as OpsIsrael. While several hacktivist groups announced their participation in OpsIsrael this year, the identity of the attacker remains unknown, the Jerusalem Post reported.
Hyundai data breach: Hyundai's Italian and French branches have leaked customers' details. Exposed data includes email addresses, telephone numbers, physical addresses, and vehicle chassis numbers.
MSI ransomware attack: Taiwanese hardware vendor MSI has confirmed a security breach after the MoneyMessage ransomware gang claimed to have breached and encrypted some of the company's systems.
Hundred Finance crypto-heist: The Hundred Finance platform was hacked for $7.4 million following a flash-loan attack.
GDAC crypto-heist: South Korean cryptocurrency platform GDAC was hacked earlier this month for $13 million worth of assets.
Bitrue crypto-heist: The Bitrue cryptocurrency exchange says it was hacked and lost $23 million worth of assets following an attack on one of its hot wallets on April 14. Bitrue says it's currently investigating the incident and doesn't know how the hack took place.
Yearn Finance crypto-heist: A threat actor exploited a bug in the Yearn Finance platform to steal $11.6 million worth of cryptocurrency assets.
Terraport crypto-heist: The Terraport DeFi platform was hacked for $4 million worth of crypto-assets.
General tech and privacy
Google Assured OSS: Google Cloud has formally launched Assured OSS, a service that will let its customers use the same Java and Python packages that Google uses internally for its own applications. The service is free of charge.
New Google deps.dev API: Google launched an API for deps.dev, a database of security metadata, including dependencies, licenses, advisories, and other critical health and security signals for more than 50 million open-source package versions.
Misinformation superspreaders: A report found that Twitter Blue accounts are some of the platform's biggest spreaders of misinformation.
Dumb Nintendo stuff: Nintendo's notoriously dumb lawyers have gone on another copyright takedown spree. This one is particularly silly because they're taking down gameplay from their own games, even if their own ToS allow players to put it online.
Patreon double standards: There are reports that Patreon is suspending Ukrainian accounts raising funds for their military but not doing the same for Russians. Another platform that considers genocide is more important than the ability to defend yourself in the case of an invasion.
New LinkedIn verification scheme: Microsoft has announced that companies can now verify their employeeS' LinkedIn accounts using Microsoft's Entra cloud identity and access solution. The feature might be useful in stemming some scenarios where scammers pose as employees of a certain company when approaching their targets. It's a nice gesture, but it will probably not stop anyone. Such a feature works when it's broadly available and not limited to Entra accounts.
"With a few taps on their phone, members can get their digital employee ID from their organization and choose to share it on LinkedIn. After they send the credential, a Workplace verification [badge] will be displayed on their profile."
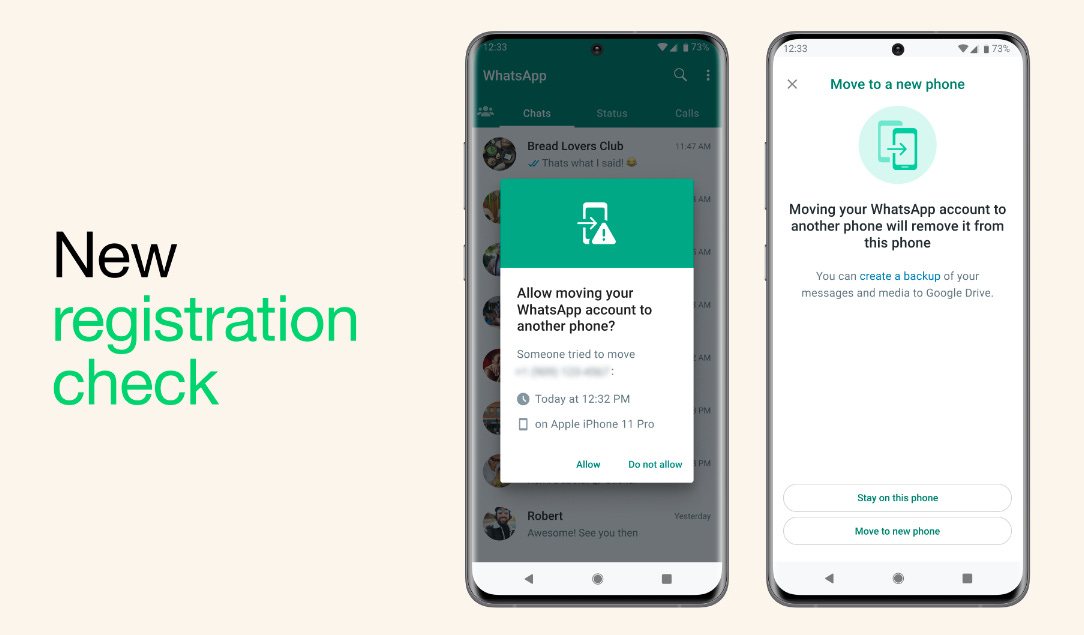
New WhatsApp security features: Meta has rolled out three new security features for its WhatsApp instant messaging service. The first is named Account Protect and is meant to prevent threat actors from moving a user's account to a new device. The second is named Device Verification and is meant to prevent malware on a device from interacting with the WhatsApp install and online services. The third is named Automatic Security Codes and is a new cryptographic system meant to ensure that encrypted chats remain encrypted and safe to use.
Government, politics, and policy
Secure by design guidance: CISA, the FBI, the NSA, and cybersecurity agencies from Australia, Canada, Germany, Netherlands, New Zealand, and the UK published a joint statement and guidance asking software vendors to release future products that are secure-by-design and secure-by-default. The guidance was described as the first of its kind. It urges software makers to include secure defaults in their products, prioritize security as a critical element of product development, and release accurate and complete vulnerability advisories.
17th critical infrastructure sector: The Cyberspace Solarium Commission has recommended that US space systems should be considered a critical infrastructure sector. If approved by White House officials, space would become the US' 17th critical infrastructure sector.
Montana bans TikTok: The US state legislature of Montana has passed a bill banning the use of the TikTok application on all personal devices across the state, effectively becoming the first US state to issue a full-out ban on the app. The bill passed with a 54-43 vote. The bill was sent to Gov. Greg Gianforte's office to be signed into law. Gianforte can veto the bill and refuse to sign it, and his intentions are still unclear.
NATO Locked Shields 2023: The NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) will host this week Locked Shields 2023, a cyber defense exercise where teams of cybersecurity experts defend networks from attacks that simulate real-world adversaries. This year's edition includes more than 3,000 participants from 38 nations, marking the largest Locked Shields edition to date.
China accuses the US of spying: Chinese government officials have accused the US of "jeopardizing" global cybersecurity by its internet monitoring and espionage operations. The statement references five past and very public incidents, such as the Snowden and Shadow Brokers leaks. If the statement says anything, it's that the Chinese government may have no clue what the US may be doing right now in terms of cyber espionage. Beijing officials have made similar accusations over the past months but have not provided any insight into new operations, constantly chewing on decade-old leaks and incidents.
India's new fact-checking unit: The Indian government has updated its 2021 IT laws to add a clause requiring online platforms such as Meta and Twitter to take down information that has not been "fact-checked" by an Indian government body. Government officials say the amendment is meant to fight online misinformation. Some government officials, press freedom advocates, and tech experts have called it an attempt to "censor journalism." They say this new "fact-checking" mechanism does not include judicial oversight, an appeal process, nor does it specify which government body will decide what information is false or true.
New GCHQ Director: Anne Keast-Butler has been named as the new Director of the GCHQ, the UK's national intelligence agency. Keast-Butler has been named as the new Director of the GCHQ, the UK's national intelligence agency. Keast-Butler will succeed Sir Jeremy Fleming, who announced in January his decision to step down after six years in the role. She previously served as Deputy Director General for the MI5 before she was named the GCHQ's 17th and first female Director.
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
Cybercrime and threat intel
Dutch police warn RaidForums users: Dutch police sent thousands of emails, hundreds of letters, and made a dozen calls to Dutch citizens who had accounts on RaidForums, a cybercrime forum that was taken down in April of last year. Authorities didn't file any charges but said they only wanted to remind users they were no longer anonymous and may risk serious repercussions if they continue illegal activities.
Online investment fraud gang dismantled: Europol announced the arrest of five suspects who were part of a gang that ran a massive online investment fraud scheme that stole more than €89 million from more than 33,000 victims across the world. The suspects were detained in Germany. Fifteen locations were also raided and searched across Bulgaria, Romania, and Israel, including five illegal call centers.
Sextortion assistance scams: The FBI warns the general public that some companies that offer "assistance" services for sextortion victims are taking advantage of victims. The Bureau says it received reports of companies falsely claiming to work with law enforcement officials and charging exorbitant fees in the tune of thousands of US dollars.
DDoS attacks on NATO countries: Netscout reports seeing a significant increase in DDoS attacks targeting NATO countries following Russia's invasion of Ukraine.
Cloudflare DDoS trends report: In its 2023 Q1 threats report, Cloudflare noted a rise in the use of VPS servers to host DDoS attack infrastructure compared to the use of IoT botnets. Cloudflare noted that some of these VPS-based DDoS botnets are launching attacks up to 5,000 times larger than what they typically see from classic IoT botnets.
Malware delivery on Google Play: Kaspersky says it is seeing ads in underground forums where malware authors are advertising services to deploy malware inside Google Play-approved Android apps. Access to "Android malware loader" services are being advertised for typically $5,000.
Attacks on tax firms: Sophos has details on a threat actor targeting tax firms with the GuLoader malware. Since it's also tax season, other campaigns leveraging tax-related schemes are also underway, per Microsoft and Fortinet.
Swatting-as-a-service: Motherboard has a report on Torswats, a new swatting-as-a-service sold on Telegram and which uses synthesized voices to place calls at police stations across the US.
BlackLotus guidance: Microsoft published guidance on how to investigate, detect, and deal with BlackLotus UEFI bootkit infections.
Malvertising campaign using Weebly sites: Malwarebytes has a report on a malvertising campaign abusing Google Search ads to redirect users to various scam sites hosted on Weebly servers. The campaign uses various non-standard targeting, such as cooking and weather topics, but also classic tech support and software download themes.
MSMQ exposure: IoT search engine Censys says there are more than 465,000 Windows systems connected online that are exposing their MSMQ (Microsoft Messaging Queuing) service and could be exploited via the recently patched CVE-2023-21554 RCE vulnerability.
Malware technical reports
PlutoCrypt: Malware researcher Igal Lytzki has published an analysis of PlutoCrypt, a new variant of the JokerCrypt ransomware.
Legion: Cado Security and Permiso published an analysis of Legion, a Python-based toolkit meant for hacking into servers and collecting credentials for various cloud services. The tool is currently advertised on Telegram and appears to be a variant or related to a toolkit named AndroxGh0st. Researchers suspect the tool is being used to harvest server access that can later be abused for spam or sold for access.

Goldoson: McAfee has discovered Goldoson, a malicious software library that made its way into more than 60 legitimate Android applications. The library contains features that allow it to secretly collect lists of locally installed applications, a history of Wi-Fi and Bluetooth devices information, and nearby GPS locations. McAfee says apps were the library was used were downloaded more than 100 million times.
Balada Injector: Sucuri researchers say they've been tracking a gigantic malware campaign that has compromised more than one million WordPress sites since 2017. Sucuri says the threat actors are using vulnerabilities in WordPress themes and plugins to infect underlying Linux servers with a backdoor named Balada.
Mexals cryptojacker: Akamai says the Mexals cryptojacking gang appears to have returned with new attacks targeting servers with improperly secured SSH services. Akamai says it observed new attacks from the gang since October 2022. The gang also tried to rebrand as Diicot, the name of the Romanian anti-terrorism and organized crime agency. Akamai and Bitdefender believe the threat actor behind this malware is a Romanian speaker.
Zaraza: Uptycs has a report on the new Zaraza infostealer.
Aurora Stealer: Security researcher Mohamed Adel has a report on the Aurora Stealer, an infostealer written in the Go programming language.
RedLine Stealer: Huntress Labs malware researcher Matthew Brennan published a technical analysis of the RedLine Stealer.
Vare: CyberArk researchers have discovered a new infostealer named Vare that is currently being used to target other malware authors. Malware operators are typically targeted using social engineering tactics via Discord. Vare itself also uses Discord as its backbone, as both a CDN and C&C infrastructure. CyberArk says Vare is still in early development but has linked the malware to a new group called "Kurdistan 4455" based out of southern Turkey.
Karakurt returns: Chinese security firm QiAnXin has a report on the return of Karakurt, the data extortion division of the old Conti gang.
SarinLocker ransomware: CyFirma has published a report on the new SarinLocker ransomware—operated by the FusionCore group.
RagnarLocker ransomware: Sygnia published a technical analysis of the new RagnarLocker ransomware strain.
Kadavro ransomware: Fortinet has an analysis of the new Kadavro ransomware they've been seeing distributed in the wild disguised as a Tor Browser installer.
LockBit ransomware: French security firm Glimps has published a technical analysis of Lockbit's new version, known as LockBit Green.
Vice Society ransomware: PAN's Unit42 has a breakdown of a typical Vice Society ransomware attack.
Trigona ransomware: Zscaler has analyzed Trigona, a ransomware written in Delphi that has been active since June 2022. Researchers have also released a Python-based tool to extract and decrypt Trigona configurations.
RTM Locker: Trellix researchers have discovered a new RaaS platform named Read The Manual, or RTM Locker.
Quasar Chaos: OALabs has published IOCs on Quasar Chaos, a combination between the Chaos ransomware and the Quasar open-source RAT.
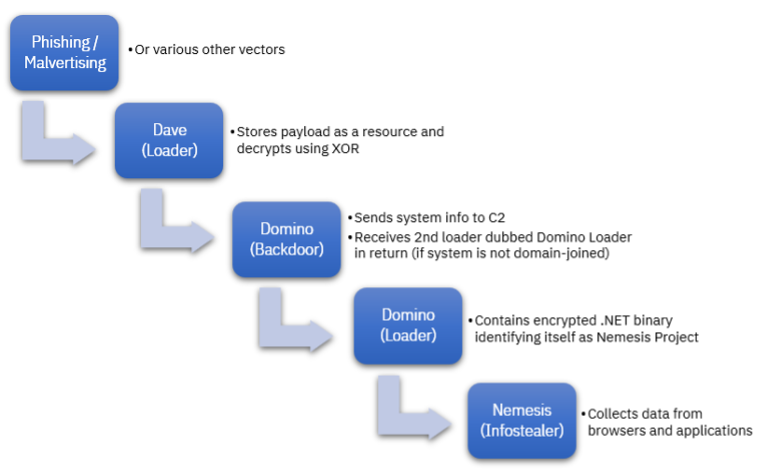
Domino backdoor: IBM's X-Force security team has been tracking since February 2023 a new malware campaign that infects victims with the Dave Loader malware in order to later drop a new malware strain codenamed the Domino backdoor and then the Project Nemesis infostealer. What IBM found interesting about this campaign is that former members of the Trickbot/Conti gang (Dave Loader) appear to now be cooperating with the FIN7 gang (Domino).
Sponsor Section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year, in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
APTs and cyber-espionage
DoNot APT: CyFirma researchers have published a report on recent DoNot APT campaigns targeting individuals in South Asia using Android malware.
Lazarus DeathNote campaign: Kaspersky has a report on a Lazarus campaign they've been tracking under the DeathNote codename, taking place since late 2019.
APT-C-28: Qihoo 360 researchers have published a report on the APT-C-28 (ScarCruft, Konni) cyber-espionage group and its recent operations targeting South Korea.
3CX incidents: 3CX has published an initial incident response report for its recent supply chain compromise. We now have names for the malware used in the attacks: TAXHAUL (Windows loader), COLDCAT (Windows downloader), and SIMPLESEA (macOS backdoor).
Transparent Tribe APT: SentinelOne published a report analyzing Transparent Tribe APT campaigns distributing the Crimson RAT.
Iranian destructive attacks: Microsoft says the DarkBit ransomware operation is a front for Iranian cyber espionage group MuddyWater (Mercury), a hacking unit inside Iran's Ministry of Intelligence and Security. The company says DarkBit is typically deployed on cloud or on-premises systems previously compromised by the MuddyWater gang by a seemingly independent sub-group it tracks as DEV-1084. Microsoft believes MuddyWater handing off access to DEV-1084 is the group's attempt to disguise intelligence collection as a mundane ransomware intrusion.
APT28 leader identified: Ukrainian hacktivist group Cyber Resistance claims to have identified and hacked the email account of a Russian GRU officer they believe is the leader of the Russian military's infamous APT28 hacking unit. The officer has been identified as Lieutenant Colonel Sergey Alexandrovich Morgachev. Morgachev's connection to APT28 has been widely known since 2018, when the US Justice Department charged him for the 2016 DNC hack. No previous reporting described Morgachev as APT28's leader.
Russian coffee shop espionage: Russian hackers are taking over private security cameras across Ukraine coffee shops and other private businesses, according to Rob Joyce, Director of Cybersecurity at the National Security Agency. Joyce says the purpose of the hacks is to collect intelligence on aid convoys passing through Ukraine's territory. The full Joyce CSIS interview is embedded below and the part of Russian security camera hacking is at the 29 minute mark.
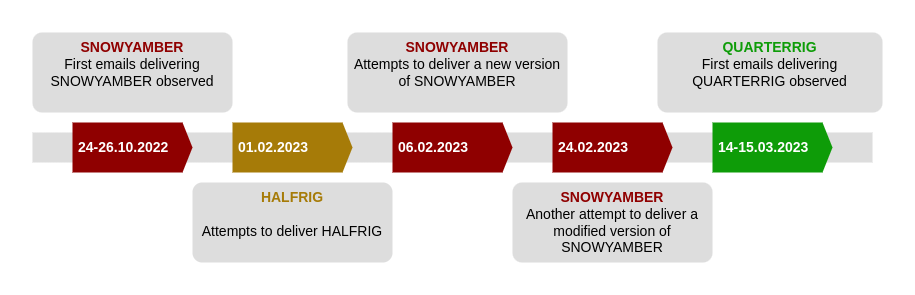
Russian cyber-espionage: Poland's CERT team and its Military Counterintelligence Service have issued a security advisory about a widespread espionage campaign linked to Russian intelligence services. Officials say the campaign has been underway since October 2022 and has targeted NATO member states, EU states, and, to a lesser extent, African countries. Polish officials linked the campaign to the Russian SVR and its APT29 hacking unit and published reports on three new malware strains used in the attacks—identified as SNOWYAMBER [PDF], HALFRIG [PDF], and QUARTERRIG [PDF].
Vulnerabilities and bug bounty
Patch Tuesday: Last week was also the April 2023 Patch Tuesday. We had security updates being released by Adobe, Apple, Microsoft, Mozilla Firefox, Google Chrome, Google Cloud, Fortinet, Hikvision, Jenkins, and SAP. The Android project and Cisco released security updates last week as well. This month, Microsoft patched 115 vulnerabilities, including a zero-day (CVE-2023-28252) abused in attacks by the Nokoyawa ransomware gang. Two zero-days were also patched in iOS and macOS (CVE-2023-28205 and CVE-2023-28206) and one in Chrome (CVE-2023-2033). According to Google TAG head Shane Huntley, the three zero-days were used by two different surveillance vendors.
Azure Storage vulnerabilities: Orca Security discovered a way to abuse Microsoft Storage Accounts by manipulating Azure Functions to steal access tokens of higher privileged identities, move laterally inside organizations, access critical business assets, and execute remote code.
CVE-2023-28879 (Ghostscript): Almond researchers published details on CVE-2023-28879, an RCE in the Ghostscript PostScript processing engine.
Google internal network RCE: Giraffe Security says it managed to successfully execute a dependency confusion attack that compromised 50+ computers inside Google's internal network.
Linux Spectre protections fail: The Linux kernel team has fixed a bug where its Spectre protections were failing to load for userspace apps that were trying to load that particular security feature.
Security researchers detained: Malta's police force is investigating four students who found and reported a vulnerability in FreeHour, a software application used by local universities and their students. According to the Times of Malta, the students reported the vulnerability to the app maker last October, gave it three months to fix it, and requested a bug bounty for their efforts. In a blog post, FreeHour says it misunderstood the initial report and thought it was an extortion attempt and reported it to authorities. The company says it eventually learned the students had "no malicious intent," but by that point, a criminal case was underway, where they had no further say. The four were eventually arrested, had their houses searched, computer equipment seized, and now risk up to four years in prison.
Infosec industry
ShmooCon 2023 videos: Talks from the ShmooCon 2023 security conference, which took place in late January, are now available on the Internet Archive.
Botconf 2023 videos: Talks from the Botconf 2023 security conference, which took place last week, are now available on YouTube.
AI Incident Database: Prof. Emily M. Bender launched a public database of AI-related/caused security and privacy incidents.
Okta detection logic: Okta's security team published earlier this month its internal threat detection logic. The company's thinking is that other companies could benefit from the work they put into detecting threats against Okta users. SIEM maker Splunk has already integrated Okta's detection rules into its product.
"Over the past few months, Okta's Defensive Cyber Operations team has shared bespoke detection logic with security analytics/SIEM providers, requesting the logic be baked into their content libraries' out of the box.' The first of those discussions has already borne fruit with Splunk, the security analytics platform chosen most often by Okta customers."
New tool—ChainLoop: Chainloop, an open-source software supply chain control plane, has gone open-source.
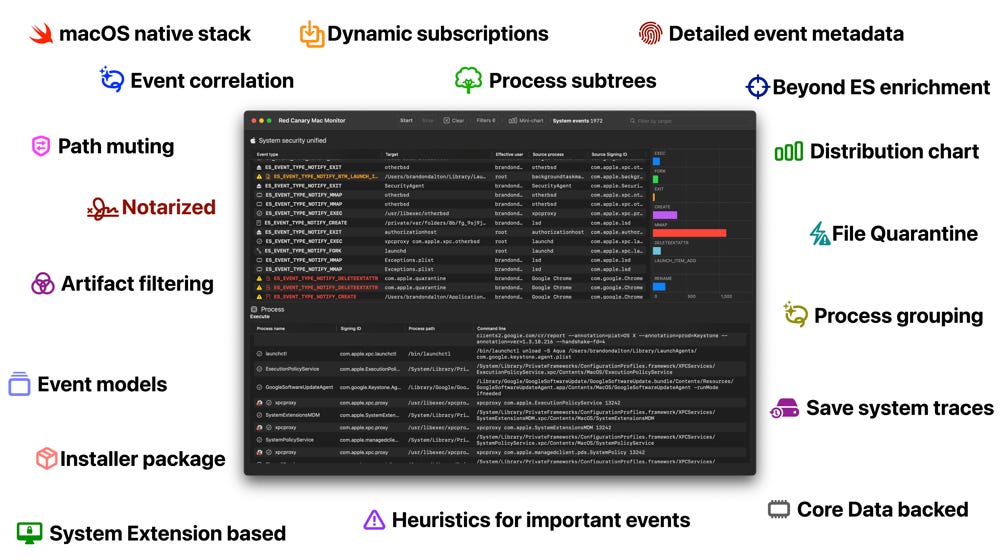
New tool—Red Canary Mac Monitor: Security firm Red Canary has open-sourced a new tool named Mac Monitor. The tool collects and enriches system events, displaying them graphically with an expansive feature set designed to reduce noise. It was designed for macOS security research.