Risky Biz News: Is ransomware going after the Global South? Sure looks like it!
In other news: Another major Chinese user data leak; PAN bug abused in DDoS attacks; and SIDH broken for the third time.
This newsletter is brought to you by Airlock Digital, Proofpoint, RunZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
A report published last week by the British think tank the Royal United Services Institute (RUSI) argues that ransomware gangs have increased their targeting of the Global South—countries in Latin America, Asia, Africa, and Oceania.
RUSI analysts argue that ransomware gangs shifted their targeting over the past year following an acid response from US and European law enforcement agencies following a string of high-profile attacks that appear to have crossed a line and reached a point where the ransomware problem needed to be addressed.
This included arrests of ransomware affiliates and their money laundering partners, seizure of cryptocurrency funds linked to past ransom payments, financial sanctions against cryptocurrency platforms that aided blatant money laundering operations, and the creation of special task forces to hunt these gangs.
RUSI is not alone in reaching this conclusion, and other ransomware connaisseurs have also spotted this trend ever since last year, when, after operations orchestrated by US CyberCom and the FBI, ransomware crews appear to have (silently) decided to stop screwing around with major US targets and slowly shift to new hunting grounds.
Initially, there were slight spikes of new ransomware cases across Europe and Australia. This year, Latin America seems to have gotten more attention, according to reports from LeMag and Cyberscoop.
The reasons could be plenty, but RUSI argues that this may have something to do with the soft underbelly of most companies and government organizations across LatAm, most of which don't have the benefit of the same IT budgets seen with companies in Europe and North America.
In addition, RUSI analysts also point out that the focus on Global South countries may also be intentional and related to the current political climate—where payments to Russian cybercrime gangs may be subject to economic sanctions in North America and the EU, sanctions that are now hard to interpret even for the largest legal teams, mainly due to the complications that have arisen following Russia's invasion of Ukraine.
Insurers, lawyers, and negotiators may just not be in the mood to tempt faith and are most likely recommending that EU and US victims not pay ransoms to avoid any future complications, which makes perfect sense. However, RUSI says that the same may not be true for countries in other regions. Most of these countries have not even bothered to condemn Russia's invasion of Ukraine, let alone join any sanctions enforcement, so ransomware gangs are still free to roam like it's the Wild West, with nothing stopping them from blocking an entire country's activity with impunity.
Breaches and hacks
HanesBrand incident: Clothing manufacturer HanesBrands said in its quarterly report last week that a ransomware attack that took place earlier this year may end up costing the company almost $100 million in lost sales after the incident "limited its ability to fulfill customer orders for approximately three weeks."
Another Chinese hack: A hacker has claimed to have obtained the personal information of 48.5 million users of a COVID health code mobile app run by the city of Shanghai, Reuters reported. This would mark the second claim of a breach of a Shanghai agency over the past month after hackers also previously claimed to have leaked data from Shanghai's police department.
Smelly leak: Hackers leaked last week data from ShitExpress, a web service that lets you send a box of feces to other people. The hackers claim to have used a vulnerability in the site to obtain its full database, including private messages sent by users with their "gifts."
Seized crypto funds: Binance CEO Changpeng Zhao tweeted on Friday that his platform' seized $450,000 worth of cryptocurrency. The sum represents roughly 83% of funds stolen from Curve Finance on Monday, following a DNS attack that hijacked the platform's user frontend.
Binance froze/recovered $450k of the Curve stolen funds, representing 83%+ of the hack. We are working with LE to return the funds to the users. The hacker kept on sending the funds to Binance in different ways, thinking we can't catch it. 😂
— CZ 🔶 Binance (@cz_binance) 5:07 AM ∙ Aug 12, 2022
#SAFU
General tech and privacy
Google fined in Australia: Australia's competition watchdog fined Google on Friday A$60 million (US$42.7 million) for misleading users on the collection of their personal location data through their Android devices. The Australian Competition & Consumer Commission (ACCC) said that approximately 1.3 million Google account users in Australia might have been affected.
Government, politics, and policy
China's early access to security bugs: DHS Under Secretary for Policy Robert Silvers said during the Black Hat cybersecurity conference in Las Vegas last week that the Chinese government appears to use its software vulnerability disclosure rules to preview dangerous zero-day flaws before tech companies can deploy fixes, Cyberscoop reported. The new rules have been a subject of controversy since they were passed last year, as they appear to allow the Chinese government to punish security researchers who don't inform government agencies of dangerous bugs even before vendors.
FTC on surveillance vendors: The FTC said last week that it was starting procedures to crack down on commercial surveillance vendors. The agency is asking for feedback from the private industry on how to address the problem of "commercial surveillance," which is a term the agency uses for large-scale data aggregators, like ad platforms, and not necessarily to spyware product vendors like NSO Group. More here.
Cybercrime and threat intel
Zimbra mass exploitation: Security firm Volexity has published a report on a recent wave of attacks targeting Zimbra web apps. The attacks exploited a variation of CVE-2022-27295, an RCE formally patched earlier this year in March. While the initial vulnerability required that attackers possess valid admin credentials for an attack, Volexity said it found a variation where the admin password wasn't required. This new variation received the CVE-2022-37042 identifier and was patched at the end of July.
PAN bug exploited in the wild: Palo Alto Networks said last week that threat actors are using a recently discovered denial of service (DoS) bug to execute DDoS attacks by reflecting and amplifying traffic off PAN firewall devices. Palo Alto Networks said the attack doesn't crash the firewall, but it allows attackers to abuse the device's bandwidth and resources for DDoS attacks on third parties. The company promised patches for August 15, 2022.
Tornado Cash dev arrested: Dutch authorities said they detained a developer of the Tornado Cash crypto-mixing service last week. The arrest comes days after the US Treasury Department sanctioned the service for helping cybercriminals launder illicitly obtained funds. The suspect's name has not been released, according to Dutch privacy laws.
Malicious Python libraries: Kaspersky security researcher Leonid Bezvershenko found two malicious Python libraries uploaded on the official PyPI portal last week. The two packages (ultrarequests and pyquest) would download malware (W4SP Stealer) on a developer's system specialized in exfiltrating browser cookies, Discord tokens, and crypto wallet files.
We have just discovered two malicious PyPi packages masquerading as HTTP libraries: ‘ultrarequests’ and ‘pyquest’. The description of these packages is taken from the ‘requests’ package. The malicious code is in the class ‘HTTPError’ (‘exceptions[.]py’ file) [1/3]
— Leonid Bezvershenko (@bzvr_) 7:14 PM ∙ Aug 11, 2022
On top of this, Sonatype also discovered a third malicious package, named secretslib, that covertly runs an in-memory cryptominer on Linux systems.
New stealer on sale: A new information stealer named RAPOGLIFF is currently being advertised on underground cybercrime forums.
⚠️RAPOGLIFF #Crypto #Stealer is on #Sale ⚠️
— Daily Dark Web (@DailyDarkWeb) 6:50 AM ∙ Aug 13, 2022
A stealer is a #Trojan that gathers information from a system. The most common stealers are those that collect login #information, like usernames and passwords, and then send the data to another system via email or over a network.
Malware technical reports
SOVA: Mobile security firm Cleafy has published a report on the fourth iteration (v4) of the SOVA Android banking trojan.
Zeppelin ransomware: CISA published a malware report last week on the Zeppelin ransomware. The report gives a chilling warning to organizations that the Zeppelin gang may encrypt their files multiple times, which would also require multiple ransomware payments as a result or lead to permanent data loss if any of the keys are lost, incorrect, or mishandled.
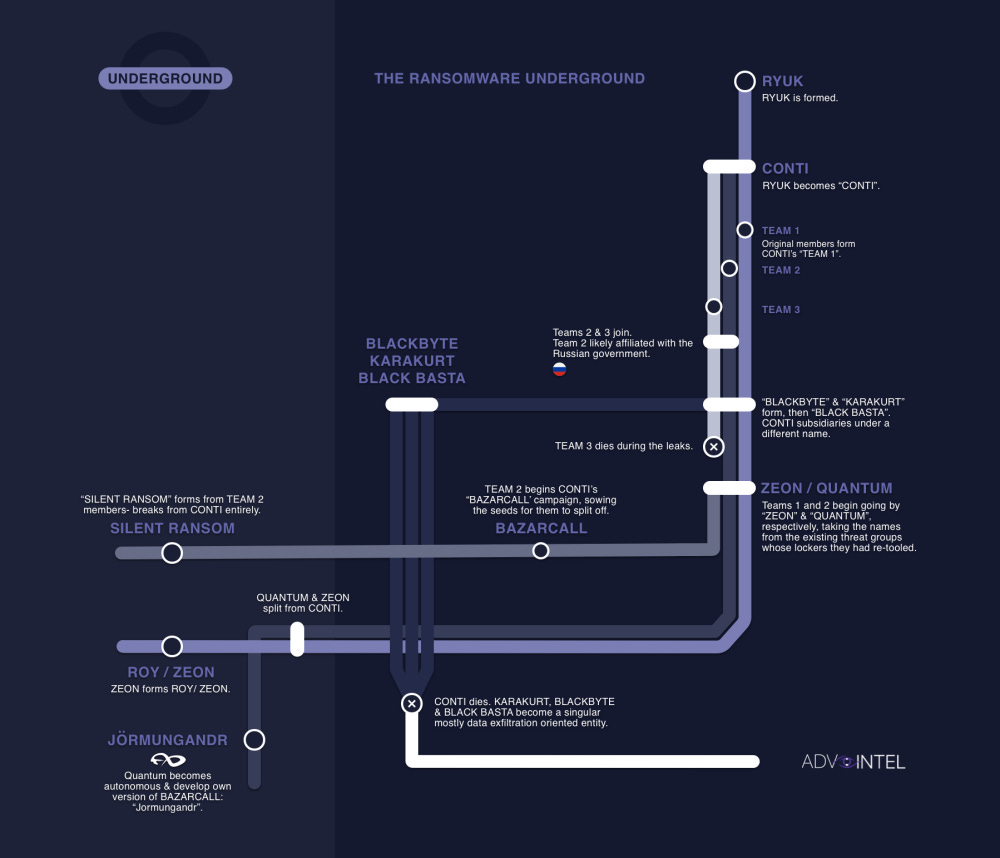
BazarCall: AdvIntel has published a breakdown of the BazarCall malware operation, first spotted being used in the wild last year. Per AdvIntel, some of the groups using BazarCall also include former members of the Conti ransomware operation.
APTs and cyber-espionage
Iron Tiger: Trend Micro and Sekoia published reports last week on the recent shenanigans of the Iron Tiger APT (also known as Emissary Panda, APT27, Bronze Union, and Luckymouse). The report details a supply chain attack on a chat application named MiMi, through which the group delivered versions of the HyperBro backdoor to infected users.
We noticed Iron Tiger controlling the servers hosting the app installers of MiMi, suggesting a supply chain attack. Further investigation showed that MiMi chat installers have been compromised to download and install HyperBro samples for the Windows platform and rshell samples for the Mac OS platform. While this was not the first time the technique was used, this latest development shows Iron Tiger's interest in compromising victims using the three major platforms: Windows, Linux, and macOS.
Armageddon IOCs: CERT Ukraine has published new IOCs from recent attacks carried out by Russia's Armageddon APT.
Vulnerabilities and bug bounty
Ethereum blockchain attack: A new academic paper published this month presents a new attack on the Ethereum blockchain's consensus mechanism that could be used by rogue miners to obtain higher mining rewards compared to the standard protocol. The research team, comprised of academics from the Hebrew University in Israel, described their work as "the first case of a confirmed consensus-level manipulation performed on a major cryptocurrency."
SIDH broken again: The (supposedly) quantum-resistant SIDH key exchange algorithm has been broken again, less than two weeks from the first and then the second attack against it.
Probably correct Break of SIDH in basically 1 page
— Pratyush Mishra (@zkproofs) 4:04 AM ∙ Aug 11, 2022
😨
Browser-powered desync attacks: In new research presented at BlackHat and DEF CON, PortSwigger's James Kettle detailed a new technique named browser-powered desync attacks. The new technique, in layman terms, desyncs a website's frontend from a user's browser and then uses the same browser to launch and relay attacks on other websites. Kettle said he successfully tested the technique to attack sites like the Amazon web store, the Akamai CDN, and multiple web VPNs.
Windows Server service tampering vulnerability: Akamai researcher Ben Barnea has published a detailed write-up of CVE-2022-30216, a vulnerability that can be used to tamper with Windows 11 and Windows Server services. In practice, the bug can be used to run code remotely on the domain controller and even modify a server's certificate mapping and therefore perform server spoofing. The bug was patched in Microsoft's July 2022 security updates.
Bootloader bugs: Eclypsium researchers have published details about three vulnerabilities impacting the firmware of booatloaders from Eurosoft (CVE-2022-34301), New Horizon Datasys (CVE-2022-34302), and CryptoPro Secure Disk for BitLocker (CVE-2022-34303). The details were also presented at DEF CON, and the vulnerability can be used to bypass the UEFI Secure Boot security feature and execute unsigned code during the boot process.
macOS security issue: Computest security researcher Thijs Alkemade has published details about CVE-2021-30873, an AppKit vulnerability that Apple patched last year and which can be abused on older macOS systems to elevate an attacker's permissions. The vulnerability resided in "saved state," a macOS feature that can re-open apps in their last state before a reboot.
Realtek SDK bug: Two security researchers—Octavio Gianatiempo & Octavio Galland—published more details about CVE-2022-27255, a stack-based buffer overflow vulnerability that impacts the Realtek SDK for the company's eCOS real-time OS, used across a wide variety of Realtek devices and white-labeled products built on Realtek SOCs. Patches for this were released back in March [PDF]. According to ISC SANS, "this vulnerability will likely affect routers the most, but some IoT devices built around Realtek's SDK may also be affected." The details were also presented at DEF CON.
Not-so-smart smart stuff: Trellix researchers presented their findings at the Black Hat security conference last week on a series of vulnerabilities in Lenel building control systems and access control panels, which they said could be used to unlock doors for facilities protected by these systems—which also apparently include US government buildings.
Infosec industry
ACSC compliance: Microsoft has published a set of Intune policies to help organizations comply with the Australian Cyber Security Centre's (ACSC) Windows 10 Hardening Guidance.
New tool—Threatest: Datadog's security team has open-sourced a new tool named Threatest, a Go-based framework for testing threat detection rules. Per Datadog, "Threatest allows you to detonate an attack technique, and verify that the alert you expect was generated in your favorite security platform."
New tool—BlueHound: Security firm Zero Networks has open-sourced a new tool called BlueHound. According to the company, the tool can be used to scan internal IT systems for information about user permissions, network access, and unpatched vulnerabilities and then reveal the paths attackers would take if they ever managed to breach the network.




