Risky Biz News: Iranian hacktivists breach president's office, leak sensitive files
In other news: RAIDForums user database leaks online; Greece end-year exams disrupted by huge DDoS attack; US to launch satellite hacking sandbox into space.
This newsletter is brought to you by Nucleus Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
An Iranian hacktivist group calling itself "Uprising till Overthrow" has breached the Iranian President's Office and has leaked a large collection of classified documents.
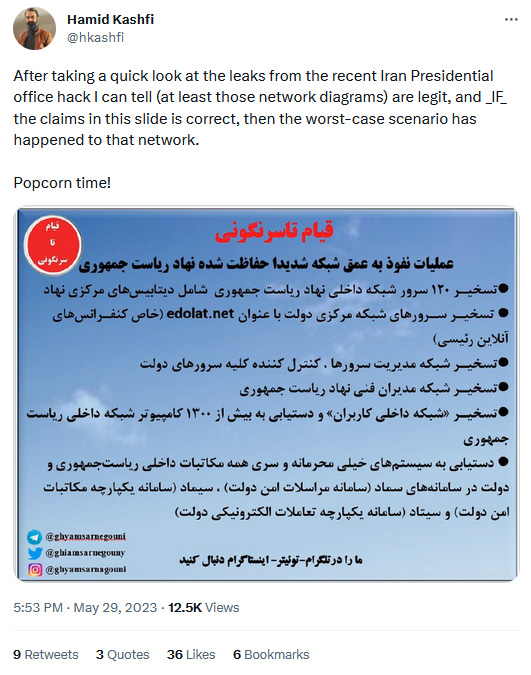
According to a press release posted on the website of exiled opposition party MEK, the group claims to have taken control of more than 120 servers and over 1,300 computers inside the President's Office internal network.
The group claims to have had full control over the entire network, to the point they were able to decrypt classified material and encrypted communications from the past several years.
Stolen files allegedly include documents pertaining to national and international policy, official communications with the IRGC, plans for official trips abroad, building designs for government sites, maps of IT infrastructure, lists of officials' phone numbers, and even the names of official government security and protection teams.
While not all documents appear to have been leaked, several sources have confirmed their authenticity, such as Iran International and Hamid Kashfi.
The "Uprising till Overthrow" hacktivist group—sometimes also mentioned as "Rise to Overthrow" or "GhyamSarnegouni"—began operations last year.
Its first major hack involved hacking and shutting down more than 5,000 Iranian government cameras and 140 government websites in June 2022.
The group made a bigger splash earlier this month when they hacked, defaced, and leaked data from Iran's Ministry of Foreign Affairs.
Despite the media coverage, Iranian officials have not released any statement regarding the recent breach. They previously denied the MoFA hack.
Just like in the MoFA incidents, "Uprising till Overthrow" also defaced the website of the Iranian President's Office with messages in support of the MEK.
Breaches and hacks
Internet Archive incident: The maintainers of the Internet Archive say their public OCR service has been hit by a coordinated attack. The attack bombarded the service with tens of thousands of requests "from 64 virtual hosts on Amazon's AWS services." The attack brought down the Internet Archive for about an hour. Maintainers say that as soon as they blocked the attacking IPs, another 64 other IP addresses started bombarding the service within a few hours. Speaking on Mastodon, an Internet Archive member says the attack appears to have been just "overstated exuberance" and not malicious in nature.
Crimean ISP cyberattack: Russian internet service provider Miranda Media says the massive internet outages across the Crimean peninsula and occupied Ukrainian territories across the weekend were caused by a cyberattack. The attack caused a full loss of service for all customers. The company did not reveal the exact nature of the incident.
Greece edu platform DDoS: A large-scale DDoS attack has disrupted the end-of-year high school exams in Greece for a second consecutive day. The Greek Ministry of Education says the high school examination platform saw attacks both on Monday and Tuesday, in what officials called "the most significant attack ever made on a Greek public government organization." Officials say that despite the attack, they were able to send out and complete exams, although not after they left students waiting in classrooms for their subjects for hours.
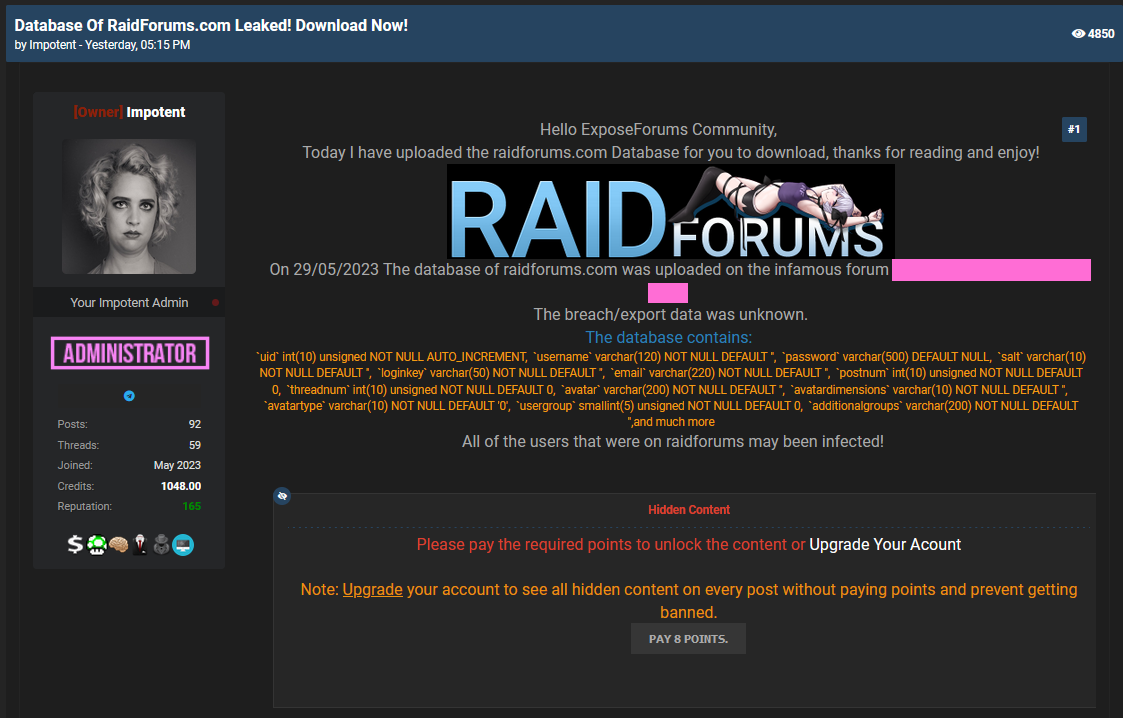
RAIDForums database leaks: A copy of the RAIDForums user database has been leaked online on a newly launched cybercrime forum named Exposed. The leak confirms rumors that swirled in underground circles that the forum might have been hacked in previous years. The leaked files contain account details for users who registered on the site between March 2015 and September 2020. Details on more than 478,000 user accounts are included. Law enforcement seized the original RAIDForums and detained its administrator in April 2022. After its shutdown, a new forum named BreachForums (or Breahed) became the go-to place for data traders and database leakers. After BreachForums was also seized earlier this year, Exposed now seems to have become the new meeting place for the data trading community. According to reports, the site's new admins appear to have already made more than $4,500 just from selling forum awards and tiers over the past ten days since its launch. Around half of that amount was earned following the leak of the RAIDForum database.
General tech and privacy
Mullvad VPN drops port-forwarding after abuse: Mullvad has dropped support for port-forwarding, a feature that allows remote users to access computers hidden by its VPN service. The company says some of its users abused the feature to host "undesirable content and malicious services" on their personal computers and then make them available on the internet hidden behind its VPN's IP addresses. Mullvad says it was contacted numerous times by law enforcement about the abuse. Its VPN service performance was also affected by the abuse after some of its IP addresses got blocked by some service providers. The company has removed the ability to add new port-forwards, and all existing port-forwarding setups will be shut down on July 1, 2023.
Intel considers dropping 16/32-bit compatibility: Chipmaker Intel is considering dropping legacy support for the old 16 and 32-bit modes from its upcoming lines of CPUs. Intel says the old modes are only used for booting up operating systems and placing them in 64-bit modes and rarely anything else. The new 64-bit mode-only architecture is currently referred to as x86S (S for simplification).
MINIX OS is dead: Several people have noticed this before, but there's been no new development on the MINIX open-source operating system since 2014, when its creator, Andy Tanenbaum, retired from VU University.
Venezuela's troll farms: The BBC has a profile on a Venezuelan working in the country's troll farms, getting paid to tweet state propaganda.
"Every day, Venezuela's ministry of communications tweets a "hashtag of the day," which is repeated not only by elected officials' accounts and state sympathisers but also by "digital troops" like Rafael, who are paid to share propaganda."
Government, politics, and policy
New spyware for Israeli police: Israel's police force has licensed new spyware named Echo, made by Israeli cyber intelligence company Rayzone. The new tool includes functionality to allow investigators to locate a suspect, their movement path, and the apps installed on their device. The new acquisition is already causing a stir. According to the Calcalist, Israeli police purchased the tool without approval from the Israel Attorney General's Office, against a recommendation made by the Ministry of Justice. The Ministry of Justice investigated the Israeli police force last year for its use of the NSO Group's Pegasus in incidents that targeted activists, business figures, reporters, and politicians.
Moonlighter: The US government is set to launch into space a new nano-satellite named Moonlighter that will serve as a satellite hacking sandbox. Once deployed, Moonlighter will allow cyber security professionals to perform cyber experiments on a satellite that is in space rather than test satellite workbenches that are set up in special laboratories. The project was developed by the ISS National Laboratory, US Space Systems Command, and the Air Force Research Laboratory. Moonlighter is also scheduled to be part of Hack-A-Sat 4, a hacking contest organized by the US government. Moonlighter is to be deployed in space with the SpaceX CRS-28 rocket, targeted for launch on June 3, 2023.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Patrick Garrity, VP of Marketing and security researcher at Nucleus Security, on how the company has been tapping into CISA's KEV database for insights on vulnerability management and prioritization.
Cybercrime and threat intel
Professionalization of cybercrime: Back in April, Trend Micro published a report on the professionalization and specialization of the cybercrime landscape. On the heels of that report, WithSecure has a deeper dive into the topic, showing how the underground cybercrime ecosystem has slowly adapted to provide highly specialized services, an evolution from the old 2010s when each cybercrime ecosystem was trying to provide all-out offerings. Now, you have groups dedicated to crafting exploits, gangs specialized in initial access, people specialized in expanding that initial access, ransomware gangs, MaaS platforms, money mule services, and so on. Many of these services are then offered to one another, with groups supporting each other's operations.
Black Market Pesos Exchange: Europol has shut down a money laundering network that was going by the name of the Black Market Pesos Exchange. The network seemed to cater to drug cartels exclusively.
In The Cyber arsenal: A Swiss company is developing and selling hacking tools to governments in the Middle East, Africa, and Asia. Named In The Cyber, the company is known for acquiring Italian spyware maker HackingTeam in 2019, which it renamed to MementoLabs. New tools developed under this new umbrella include TEX, or Tactical EXecutor, a toolkit that can be plugged into any Windows system and provide investigators with admin access, even if the storage has been encrypted with BitLocker. Other products include MoniTOR, a tool that can partially deanonymize Tor traffic, and PrevenTer, a tool for phone call speech recognition and call transcription. [Additional coverage in the Neue Zurcher Zeitung]
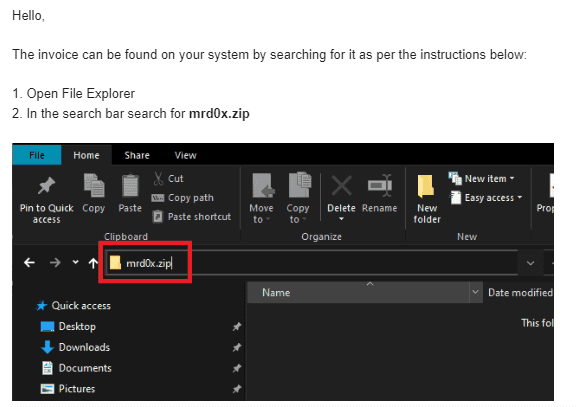
ZIP domains woes: Pen-tester mr.d0x documents a new way to abuse Google's newly announced .zip domains.
"Several people pointed out on Twitter that the Windows File Explorer search bar is a good delivery vector. If the user searches for mrd0x[.]zip and it doesn't exist on the machine, it will automatically open it up in the browser. This is perfect for this scenario since the user would be expecting to see a ZIP file. An example of a phishing email that could be sent to an unsuspecting target."
Malware technical reports
SpinOk: Russian cybersecurity firm Dr.Web has discovered a malicious Android SDK that contains spyware-like features that can steal local files, replace clipboard content, and even collect sensor data from an infected device. The SDK is currently advertised under the guise of being a marketing toolkit that can show ads inside Android applications. So far, the SDK has been seen in 101 Android apps uploaded to the official Google Play Store. The apps have been downloaded more than 421 million times. Dr.Web says it notified Google of its findings, and app makers were told to remove the SDK from their code.
CryptoClippy: The CryptoClippy clipboard-hijacking malware is slowly evolving into a banking trojan, according to cybersecurity firm Intezer. The malware was first spotted in April 2023 by PAN's Unit42. At the time, the malware contained functionality to infect a Windows system and silently replace cryptocurrency addresses in the OS clipboard. Intezer says it has discovered a new CryptoClippy version that can now also collect and exfiltrate information about payment apps commonly used in Brazil.
Akira ransomware: K7 and Antiy published reports on the new Akira ransomware. So far, their leak site has listed 17 victims since its launch at the end of April. K7 says the ransomware's code uses portions of the leaked Conti source code.
Kraken: Malware researcher Igal Lytzki has published a two-part series on the Kraken infostealer.
AsyncRAT: OALABS takes a look at an AsyncRAT sample and its AMSI bypass technique.
DogeRAT: CloudSEK researchers have an analysis on DogeRAT, a new open-source remote access trojan targeting Android devices.
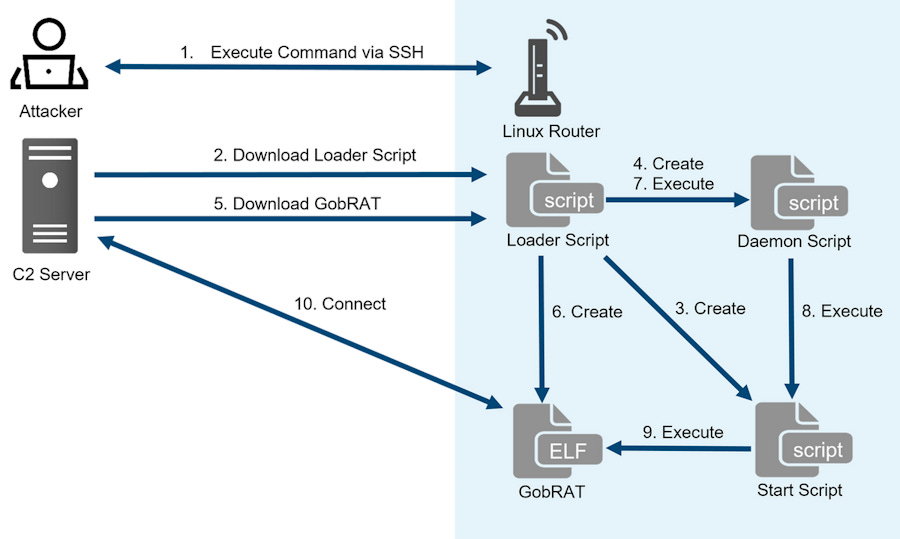
GobRAT: JPCERT/CC has published an analysis of GobRAT, a new Go-based Linux malware that was deployed on routers in Japan in a series of attacks in February this year.
Risky Business Demo
Nucleus Security's COO Scott Kuffer shows Risky Business podcast host Patrick Gray their vulnerability management platform. It ingests scan outputs from a number of vulnerability identification tools, normalizes that information, and then allows vulnerability management teams to do things like assign responsibility for certain types of bugs to the correct people.
APTs and cyber-espionage
Bitter's ORPCBackdoor: Chinese security firm KNOW Chuangyu has a report on ORPCBackdoor, a new malware strain used in recent campaigns by the Bitter APT.
Patchwork's EyeShell: The same company also published a report on EyeShell, a new Windows backdoor strain seen in attacks carried out by the Patchwork APT group.
LookBack's FlowCloud: NTT Security has published a report on FlowCloud, a backdoor used by the LookBack (TA410) APT group. While the malware has been used for quite some time now and has been deployed via phishing campaigns and vulnerability exploitation, NTT researchers say they've seen recent attacks where the malware was also dropped on Japanese networks via USB memory sticks.
SmokeLoader campaign: CERT-UA says UAC-0006, a financially-motivated threat actor, is targeting Ukrainian organizations with malspam emails that infect victims with the SmokeLoader malware. A similar campaign took place in early May as well. CERT-UA says the previous campaign successfully infected roughly 1,100 computers.
Void Rabisu and RomCom's evolution: A financially motivated threat actor known as Void Rabisu (Tropical Scorpius) has significantly changed its mode of operation since October 2022. The group is known for operating the Cuba ransomware and the RomCom backdoor, which it offers under a malware-as-a-service model. Trend Micro says that since October 2022, the RomCom has been used in a series of geopolitically motivated attacks linked to the Ukrainian conflict. The security firm says it has seen RomCom in campaigns targeting the Ukrainian government and military, but also organizations outside Ukraine that were linked to the conflict. This includes a local government that provides help to Ukrainian refugees, a parliament member of a European country, a European defense company, and various IT service providers in Europe and the US. Trend Micro's report confirms similar findings by BlackBerry's security team, which assessed the cybercrime group was now working for the Russian government.
Operation Red Deer: Perception Point researchers analyze a recent malspam campaign deploying the 3losh RAT they have linked to the Aggah group. Several waves of this campaign were spotted, all targeting Israel.
Vulnerabilities and bug bounty
macOS "Migraine" vulnerability: Microsoft security researchers have discovered a new macOS vulnerability. Named Migraine (CVE-2023-32369), the vulnerability can allow an attacker with root access to bypass System Integrity Protection (SIP) and modify protected parts of the OS. Apple patched the Migraine bug in security updates released earlier this month.
Sudo vulnerability: Synacktiv researchers Matthieu Barjole and Victor Cutillas have discovered two vulnerabilities (CVE-2023-28486 and CVE-2023-28487) in the Linux Sudo utility. The vulnerabilities can be used to inject terminal control characters that alter output when being viewed.
Pydio vulnerabilities: RedTeam Pentesting has found three vulnerabilities impacting Pydio Cells, an open-source file-sharing and synchronization software that runs on the user's own server or in the cloud. This includes unauthorized role assignments, cross-site scripting via file download, and a classic server-side request forgery issue.
PrinterLogic vulnerabilities: A team of security researchers has discovered a collection of 18 security flaws in the PrinterLogic enterprise print management software. The vulnerabilities are quite serious, and they include an authentication bypass, an SQL injection, and several password and sensitive information leaks. Some of the reported issues have received fixes, although not all.
Faronics vulnerabilities: NCC Group researchers have discovered 11 vulnerabilities in Faronics Insight, an on-premise educational and class management software platform. Uncovered vulnerabilities include several RCEs, a security feature bypass, and a teacher credentials leak. Patches have rolled out earlier this month.
Infosec industry
OffensiveCon 2023 videos: Talks from the OffensiveCon 2023 security conference, which took place two weeks ago, are now available on YouTube.
New tool—Scraping Kit: Security firm Lares has open-sourced a new tool named Scraping Kit that can scrape services for keywords useful for the initial enumeration of Domain Controllers.




