Risky Biz News: Iranian hackers sure love their social engineering
In other news: Rust gets a dedicated security team; Magento sites see supply chain attack; and WordPress sites targeted with a zero-day.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Three reports have been published over the past week on the recent activities of an Iranian cyber-espionage crew tracked under codenames such as Charming Kitten (Certfa Labs), APT42 (Mandiant), and TA453 (Proofpoint).
The common thread in all these reports is the group's dedication to the art of social engineering when going after their targets, something that is rarely seen among the arsenal of most other APT groups—maybe with the exception of some North Korean crews, and specifically those going after banks and cryptocurrency exchanges.
Sure, there is some sort of social engineering when an APT sends out a spear-phishing email to its target, don't get me wrong, but for the past half a decade, Charming Kitten constantly put that extra effort into engaging with its victims in an attempt to make sure they download malware infected files or visit a phishing site so account credentials can be compromised.
The group has cloned websites of legitimate security firms, posed as WSJ, CNN, NYT, and Deutsche-Welle journalists to trick victims into fake media interviews, and migrated to WhatsApp phishing before other APTs or security firms thought this could be a threat.
To target victims, the group either creates fictitious online personas or uses the accounts of previously compromised targets to go after their contacts, hoping from one victim to another.
But while other APT groups also do this, recent reports have pointed out the great lengths Charming Kitten operators are taking to build trust with their future victims.
For example, Certfa Labs said that Charming Kitten often tries to have "lengthy conversations with victims that can last for several days, and then trick them into clicking on malicious links at scheduled times." In its APT42 report last week, Mandiant researchers said they'd seen some of these trust-building conversations last, in some cases, even weeks.
In a report published yesterday, Proofpoint said that in some attacks they observed, the group has also used multiple fake personas "on a single email thread to convince targets of the legitimacy of the campaign," a technique one of the company's researchers described as "pretty convincing."
Some email conversations stop with the delivery of a malicious link, but others also escalate to phone calls, WhatsApp calls, and even Zoom video calls, all done to build rapport with their victims.
Certfa Labs said that while some APTs have periods of dormancy, Charming Kitten appears to run operations throughout the entire year.
The end goal varies on the target. Some are led to websites hosting malware under various pretenses and scenarios, while other victims are led to phishing sites that capture account credentials. Personas are also rotated based on the victim. Some personas are built from scratch, while others are based on real people.
As one researcher told me once in a phone call earlier this summer, if there's one APT that's getting close to the sophistication and dogged determination of BEC scammers, it's definitely this one.
PPS: Obligatory sharing of my TA453 attribution graphic. https://t.co/DTc5mMEmxU
— Josh aka Yoshi 🌻 (@ChicagoCyber) 9:57 AM ∙ Sep 13, 2022
Breaches and hacks
Philippine Airlines data breach: Philippine Airlines, the country's state-owned airline travel company, said this week that data of some of its past travelers has been stolen after a ransomware attack on Accelya, a third-party IT provider that PAL uses its frequent flyer program. PAL travelers who joined its frequent flyer program between 2015 to 2017, the company told CNN Philippines.
U-Haul data breach: Moving and rental space company U-Haul disclosed a security breach last week after the company said it found that hackers compromised a customer contract search tool and used it to access customers' names and driver's license information. This marks the company's second breach after a first one disclosed back in 2017 [PDF].
On July 12, 2022, we identified two unique passwords were compromised and used to access our customer contract search tool. We promptly changed the passwords and began an investigation. On August 1, 2022, our investigation determined some customer contracts were accessed between November 5, 2021, and April 5, 2022. After an in-depth analysis, on September 7, 2022, we identified the individuals whose information was involved.
Cisco data breach: After it disclosed a security breach last month on August 10, Cisco said in an update this week that the incident was the result of "an initial access broker (IAB) with ties to the UNC2447 cybercrime gang, Lapsus$ threat actor group, and Yanluowang ransomware operators." The company posted this update after the Yanluowang gang took credit for the attack and added Cisco-related data on its leak site.
Something's going on in Argentina: After the PLAY ransomware group encrypted the network of the Judiciary for the province of Córdoba last month, on Tuesday, the Judiciary for the city of Buenos Aires also disclosed that it suffered a major security incident that "compromised internal operating systems," which sure sounds like another ransomware attack.
FishPig security breach: Security firm SanSec said on Tuesday that it discovered that hackers breached the infrastructure of FishPig, a company that provides a security anti-bot plugin for Magento online stores, and inserted malware in its Magento 2 extension license and distribution server. The malware would backdoor Magento stores and then install the Rekoobe Linux malware strain. FishPig confirmed the incident in an announcement on its site, said they traced back the hack to August 6, and posted remediation advice for its customers.
General tech and privacy
US lawmakers warn Apple: Two Republican members of the US Senate intelligence committee have warned Apple against its plans to use chips manufactured in China (to replace South Korean and Japan-made components) for its upcoming iPhone 14 device, the Financial Times reported.
Retbleed fixes slow down performance: VMWare said it tested Linux kernel fixes for the Retbleed vulnerability and found computing and networking slowdowns of 70% and 30%, respectively.
Rust gets dedicated security team: The Rust Foundation, the nonprofit organization dedicated to supporting and sustaining the Rust programming language, announced it is establishing a dedicated security team.
New Windows update method: Microsoft said it developed a new update mechanism named Under Lock that allows it to update customers' Office and Microsoft 365 apps while a computer is locked or idle.
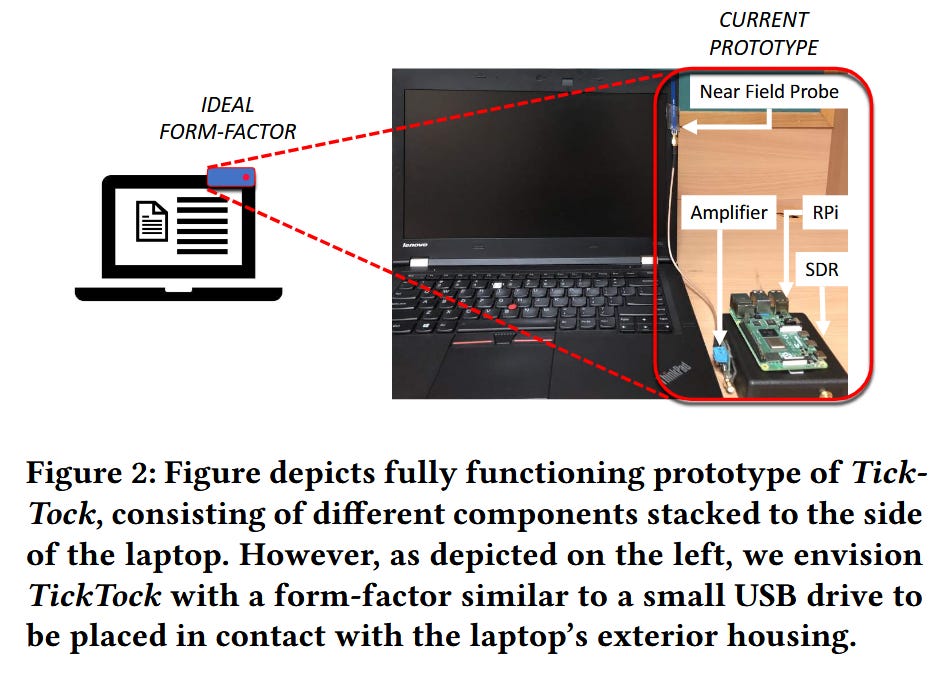
TickTock mic spying detection system: A team of academics have created a new device named TickTock that can detect when a device's microphone is secretly turned on by a threat actor or malware and used to spy on its owner.
While webcam attacks are somewhat defended with widely available commercial webcam privacy covers, unfortunately, there are no adequate solutions to thwart the attacks on mics despite recent industry efforts. As a first step towards defending against such attacks on laptop mics, we propose TickTock, a novel mic on/off status detection system. To achieve this, TickTock externally probes the electromagnetic (EM) emanations that stem from the connectors and cables of the laptop circuitry carrying mic clock signals. This is possible because the mic clock signals are only input during the mic recording state, causing resulting emanations.
New Chrome pop-up system coming: Google Chrome is getting a new built-in Pop-up API soon, and knowing how much tech support scammers like their annoying pop-ups and browser-in-browser attacks, this might be a new attack surface that security professionals might want to get acquainted with.
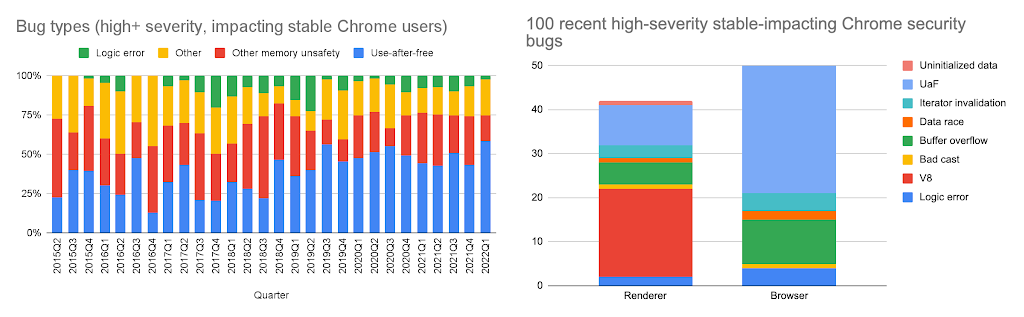
MiraclePtr: Google published on Tuesday more details about MiraclePtr, an internal initiative at the company to rewrite parts of the Chrome codebase and add extra protections against Use-after-Free (UaF) memory corruption vulnerabilities, which currently account for the largest portion of Chrome security flaws.
Government, politics, and policy
Mudge's Senate hearing: Twitter's former head of security gave a testimony to the Senate Judiciary Committee on Tuesday, which you can (re)watch here. The hearing didn't reveal anything new/major on top of what Mudge already wrote in his whistleblower letter last month... except maybe something about a possible Chinese spy working for the company.
Disinformation Senate hearing: In the meantime, another Senate hearing is scheduled for Wednesday, with the Homeland Security committee expected to grill execs from Meta, Twitter, and TikTok on social media disinformation campaigns. [Additional coverage in Cyberscoop]
New FBI PIN: The US FBI published a new private industry alert [PDF] this week, warning and urging hospitals and healthcare organizations to update their medical devices with recent security updates.
Research on China's RMSV: The Atlantic Council has published new research this week that looks at how the RMSV is impacting the global state of software security. The RMSV—Regulations on the Management of Security Vulnerabilities—is a law passed by the Chinese government in July 2021 that regulates the software vulnerability disclosure process inside China, and among its clauses includes a mandate that all issues must be reported to the government first, before to the software vendors. The conclusions of this research are:
- Harmonize vulnerability disclosure across the US and allies
- Improve the quality and consistency of support of vulnerability discovery tools
- Track vulnerability disclosure patterns and invest against gaps
Sponsor section
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. Last week, the company launched a new product called Sensitive Command Canarytoken, a simple canary token that sends an alert every time any command you choose as "sensitive" or "malicious" is executed on your host.
Cybercrime and threat intel
Sentencing delay explanation: As Dissent from DataBreaches.net points out here, the delay in sentencing Vasile Mereacre and Brandon Glover, the two hackers who extorted Uber in 2016, appears to be related to their cooperation in the case against Joe Sullivan, the former Uber CISO. Mereacre and Glover pleaded guilty back in 2019, yet, after three years, they have not received their official sentence. Mereacre testified in Sullivan's case this week.
Crypto money launderer arrested: Dutch police said on Tuesday that they arrested a 39-year-old man from the village of Veenendaal on charges of money laundering cryptocurrency worth tens of millions of euros. Authorities said the laundered funds were initially stolen using a malicious software update purporting to be from the open-source Electrum wallet. Two such incidents took place in 2018 and 2020, when the Electrum app was abused to deliver malicious updates, but threat actors have also hosted their own boobytrapped Electrum wallet updates in incidents that didn't involve the Electrum infrastructure itself, so it's hard to tell what happened here, especially since Dutch police didn't share too many case-specific details.
FSB officer pleads guilty: Dmitry Demin, a lieutenant colonel for the FSB's Samara regional unit, pleaded guilty this week to stealing bitcoins worth 187.4 million rubles from a hacker who was under investigation in the city of Syzran earlier this year.
From Conti to Quantum/BlackCat: New research published by Advanced Intelligence claims that after the disbandment of the Conti ransomware operation, infections with the Emotet botnet switched to serving as initial access points for Quantum and BlackCat ransomware strains. Previously, before Conti's shutdown in June this year, the botnet served the Conti gang and its previous incarnation as Ryuk exclusively.
The things people do for money these days: Last week, the operators of the LockBit ransomware gang said they would pay $1,000 to anyone who would get a tattoo of their logo. A week later, the gang closed this program after roughly 20 people took up the gang on its offer.
In total, about 20 people made LockBit's tattoos. Accordingly, LockBit spent about $20,000. This value is inaccurate because some people may have privately contacted LockBit. I have uploaded all participants, wallets, and media to the GitHub repository: github.com/3xp0rt/LockBit…
— 3xp0rt (@3xp0rtblog) 7:44 AM ∙ Sep 12, 2022
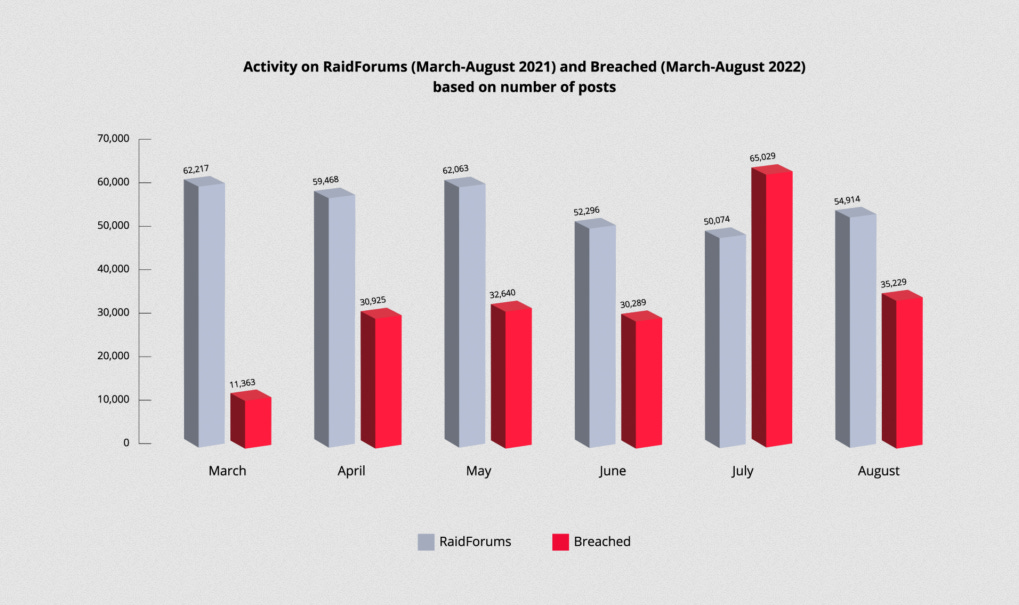
Analysis of the Breached forum: Threat intelligence outfit KELA published a deep dive this week on the rise of Breached, the cybercrime forum that has replaced the now-seized RaidForums as the main point of data leaks in the cybercrime underground. The forum currently has 82,000 registered users, rivaling Raid's former size.
Malware technical reports
OriginLogger: PAN's Unit42 has a report out on OriginLogger, a new keylogger malware that is being advertised in underground circles as AgentTesla's successor.
PrivateLoader: OALabs researchers have published TTPs and other useful information about the PrivateLoader malware operation. This comes to add to previous reports published earlier this year by Intel471, Zscaler, and Walmart's security team.
Lorenz ransomware: A report from Arctic Wolf Labs details how the Lorenz ransomware gang used a vulnerability in Mitel MiVoice Connect telephony servers to gain access to corporate networks for ransom operations.
@campuscodi Well done @AWNetworks we saw Lorenz using Mitel servers for IA in April last year (before the CVE date) but to much evidence had been wiped to be able to confirm exploitation. Nice work and good details in the report.
— PeterM🌻 (@AltShiftPrtScn) 5:27 PM ∙ Sep 13, 2022
Emotet: The DFIR Report team published a report this week on how a system initially compromised with the Emotet malware was eventually used to escalate access and gain control over the local network's domain controller.
Great threat intel from a network that was pwned & used to mass email Emotet payloads. Tradecraft includes lateral movement via MSI using PSExec, persistence via Run Key/Atera/SplashTop, gained SYSTEM on the DC.
— Kyle Hanslovan (@KyleHanslovan) 4:15 PM ∙ Sep 12, 2022
Support @TheDFIRReport with a donation 🥹
thedfirreport.com/2022/09/12/dea…
APTs and cyber-espionage
ShadowPad attacks: The Symantec Threat Hunter team, part of Broadcom Software, published a report on Tuesday on an APT campaign that targeted a range of government and state-owned organizations in a number of Asian countries with the ShadowPad remote access trojan, an APT malware strain historically associated with Chinese threat actors.
Vulnerabilities and bug bounty
Patch Tuesday update train: Since yesterday was the September Patch Tuesday, we had security updates being released by Adobe, Microsoft, SAP, and others. The Microsoft updates also addressed an actively exploited zero-day tracked as CVE-2022-37969, an EoP vulnerability in the Windows Common Log File System Driver that was spotted exploited in attacks by several security firms, such as Crowdstrike, Zscaler, Mandiant, and DBAPPSecurity. Apple also released security updates a day earlier, on Monday, as part of the iOS 16 rollout.
Azure PTA vulnerabilities: Secureworks researchers published new research that demonstrates a proof-of-concept exploit of flaws found in Microsoft's Azure Active Directory Pass-Through Authentication (PTA) method. Exploitation of these flaws enables threat actors to log in using invalid passwords, gather credentials, perform remote denial of service (DoS) attacks, and maintain persistence for years. Exploitation can't be detected by the target organization.
You know how letting an attacker steal AD FS token-signing certificates is bad?
— Brian in Pittsburgh (@arekfurt) 1:20 PM ∙ Sep 13, 2022
As it turns out, letting them steal AAD-to-AD Pass-Through Authentication agent certificates isn't great either.
Tesla NFC relay attack: Researchers from IOActive have published details about a new NFC relay attack that can unlock and start Tesla Model Y cars within seconds. Technical details are available in this PDF file, while press coverage for the layman is available in The Verge.
WP plugin zero-day: Wordfence researchers said they identified a series of attacks against WordPress sites using a zero-day vulnerability (CVE-2022-3180) in the WPGateway plugin. Wordfence says the vulnerability allows unauthenticated attackers to insert a malicious administrator on vulnerable websites.
Cryptography attacks via the UI: An academic paper recently looked at the possibility of exploiting the UI options of the Wolfram Mathematica software to manipulate cryptographers into introducing faults in their algorithms.
The attack takes advantage of the fact that the very rich user interface allows displaying formulae in invisible color or in font size zero. This allows to render some code portions invisible when opened using the tool. We implement a classical fault attack thanks to this deceptive mechanism but other cryptographic or non-cryptographic attacks (e.g. formatting the victim's disk or installing rootkits) can be easily conducted using identical techniques. This underlines the importance of creating malware detection software for symbolic computation tools. Such protections do not exist as of today.
Infosec industry
New tool—CloudFox: Security firm BishopFox has open-sourced on Tuesday a new security tool named CloudFox that can find exploitable attack paths in cloud infrastructure.
New free service—Grafana Incident: Grafana Labs launched yesterday a new service called Grafana Incident, an incident response management capability, which will be available even in the company's cloud product free tier.
Google closes Mandiant acquisition: After passing regulatory inspection, Google has formally closed its $5.4 billion acquisition of security firm Mandiant this week. Mandiant will continue to operate under its own brand but will do it under Google Cloud's leadership.
NortonLifeLock closes Avast merger: Similarly, in corporate news, NortonLifeLock and Avast also completed their $8.1 billion merger, announced last year in August.




