Risky Biz News: Iranian APT moonlights as access broker and ransomware helper
In other news: APT42 hunts regime traitors; France and the UAE hacked Durov's phone in 2017; APT29 suspected of using same exploits as spyware vendors NSO and Intellexa.

This newsletter is brought to you by Thinkst, the makers of the much-loved Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

An Iranian cyber contractor has been moonlighting as an initial access broker and providing support for ransomware gangs as a way to fill their personal coffers.
In a joint report published this week, CISA, the FBI, and the DOD's cybercrime division say that an Iranian group tracked as Pioneer Kitten (Fox Kitten, UNC757, Parisite, RUBIDIUM, Lemon Sandstorm) has created successful personas on the criminal underground where it sells access to the networks of hacked companies.
The group has operated using hacker names such as "Br0k3r" and "xplfinder" and has been observed selling access to affiliates for the AlphV, NoEscape, and RansomHouse ransomware operations.
If the affiliates are having a hard time encrypting a victim's network, members of the Iranian APT will also provide a helping hand in exchange for a percentage of a successful ransom.
Pioneer Kitten has been seen scanning and selling access to networks that have been hacked via older vulnerabilities, such as those in Citrix Netscaler gateways (CVE-2019-19781, CVE-2023-3519) and F5 BIG-IP load balancers (CVE-2022-1388), but also more recent exploits for Check Point secure gateways (CVE-2024-24919) and Palo Alto Networks PAN-OS and GlobalProtect VPN devices (CVE-2024-3400).
US officials say this part of the group's activity is separate from their main operation, which is to conduct cyber espionage and hack-and-leak ops for the Tehran regime.
One of the group's most visible efforts is Pay2Key, a fake ransomware that was deployed against Israeli targets in late 2020 with the sole purpose of locking systems but not providing a way to recover systems.
But while the Iranian regime seems to have involved Pioneer Kitten in a fake ransomware and data destructive operation, they do not appear to be aware of the group's side hustle.
US officials say the group "expressed concern" when the Iranian government began monitoring cryptocurrency linked with their IAB sales and ransomware attacks.
The report identifies the group as the employees of an Iranian company named Danesh Novin Sahand, which leaves some of their victims hopeful for official charges in the near future.
Breaches, hacks, and security incidents
France and UAE hacked Durov: Intelligence agencies from France and the UAE have hacked Pavel Durov's iPhone as part of a joint operation codenamed Purple Music. According to the Wall Street Journal, French officials were concerned about Islamic State's use of Telegram to recruit and plan attacks. The hack took place in 2017, a year before Durov met with French president Emanuel Macron. During the 2018 meeting, Macron met with Durov and invited him to move Telegram's headquarters to France.
Olympics ransomware attack: The Brain Cipher ransomware group has taken credit for a ransomware attack that disrupted Olympic venues during the recent Paris Olympics. The attack hit the Réunion des Musées Nationaux, an organization under the French Ministry of Culture that manages museums around Paris, including the Louvre. This is the group's second major disruption. It also hit Indonesia's national data center and crippled the activity of over 200 government organizations in June. [h/t Dominic Alvieri]
DICK's Sporting Goods cyberattack: US retail chain DICK's Sporting Goods has shut down email access to all employees in the aftermath of a security breach last week. The company has been using text messages and emails sent to personal employee inboxes to manage store activity until it recovers. DICK's has told the SEC the incident may have impacted systems that store confidential information. DICK's Sporting Goods is the largest sporting goods retail store chain in the US. [Additional coverage in Bleeping Computer]
Durex India leak: Congratulations to Durex's India division for exposing the personal data and orders of its customers. That's how you build your customer base. Who needs loyalty programs! [Additional coverage in TechCrunch]
No proof of CU hack last year: Sports technology platform says it found no evidence of unauthorized access to a video replay system used by the Colorado University football team. The statement comes after CU officials claimed last year that one of their opponents accessed practice videos ahead of one of their games. The Oregon football team won the game 42–6, which led Colorado to claim they've been hacked and file a complaint with Pac-12 officials. [Additional coverage in Front Office Sports]
Fota Park skimming incident: The Fota Wildlife Park in Cork says that hackers have stolen the payment card details of all customers who paid for tickets on its website between May 12, 2024, and August 27, 2024. [Additional coverage in RTE]
Steam DDoS attacks: The Steam gaming platform was the target of four waves of DDoS attacks over the past week. The attacks took place hours before Tencent's Black Myth: Wukong game broke a Steam record of most concurrent users. Chinese security firm QiAnXin says the attack disrupted Steam servers in 13 regions, but none of the waves lasted more than five hours. The attacks were most likely designed to prevent the game from breaking Steam's record. Black Myth: Wukong is China's most successful international game, with more than 10 million copies sold in the first week since its release.
CoinSwitch sues WazirX over hack: Indian cryptocurrency exchange CoinSwitch has filed a lawsuit against fellow Indian exchange WazirX to recover funds stolen from its WazirX accounts. Hackers stole over $230 million from WazirX in July. CoinSwitch is trying to recover $9.65 million it had in its WazirX account. WazirX announced a controversial plan to distribute the loss from the hack across all accounts instead of covering it from its reserve, as most crypto-heists are usually covered in the industry. [Additional coverage in TechCrunch]
General tech and privacy
Microsoft donates MONO: Microsoft has donated the MONO Project to the WineHQ organization.
CrowdStrike outage financial impact: CrowdStrike expects to lose around $60 million in net new annual recurring revenue and subscription revenue in the aftermath of its technical outage. The company says it's trying to keep customers from leaving through various discounts. CrowdStrike CEO George Kurtz denied rumors that the company was losing customers to rivals. Both SentinelOne and Palo Alto Networks claimed they have been fielding calls from CrowdStrike customers over the past weeks. [Additional coverage in CybersecurityDive]
Yelp sues Google: Yelp has filed an antitrust lawsuit against Google, alleging the company has a monopoly over the search market, which it has abused to promote its own review business.
France formally charges Durov: French prosecutors have charged Pavel Durov on Wednesday with enabling criminal activity on the Telegram platform. Charges include aiding and abetting criminal offenses on the platform, such as illicit transactions, drug trafficking, CSAM, and online fraud. He was also charged with refusing to pass information to authorities in criminal investigations and providing cryptographic services to criminals. Durov was released on €5 million bail and must check in at a police station twice a week. Authorities have seized his passports, and he is forbidden from leaving France. NBC News reports that Telegram completely ignored requests from three child safety groups to work on removing CSAM from the platform. [Additional coverage in Politico Europe]
Government, politics, and policy
California Senate passes AI bill: The California Senate has passed a bill (SB 1047) to regulate the development and use of AI models. If it passes the House and is signed into law by California Governor Gavin Newsom, it would become the first AI safety law passed in the US. [Additional coverage in Axios]
AU Cyber Advisory Board: The Australian government is planning to establish a cyber advisory board with members of the private sector. Officials say the board will include large providers that already support the government's cybersecurity operations. The new board is being established under Australia's Cyber Security Strategy, passed at the end of last year. [Additional coverage in InnovationAus] [h/t Ravo Nayyar]
EU launches Telegram investigation: The EU is investigating Telegram for misrepresenting the total number of EU users in order to fall under the 45 million threshold that would make the company liable under the EU Digital Services Act. Telegram said in February, it had only 41 million EU users. The EU announced its investigation a day after Durov was detained in France. [Additional coverage in the Financial Times]
Indonesia mulls Telegram and Bigo bans: The Indonesian government is considering blocking live streaming app Bigo Live and instant messaging platform Telegram for hosting pornography and online gambling content. Officials say they've warned both platforms in the past, but their responses were deemed "inadequate." The government's decision comes weeks after it imposed a similar ban on search engine DuckDuckGo. [Additional coverage in the Jakarta Globe]
Dutch NAFIN outage: The Dutch government says that a software error caused a major day-long outage of NAFIN, a crucial IT system managed by the Dutch Defense Ministry. The system is integrated across multiple government services and has caused cascading and sprawling second-hand outages all over the Netherlands on Wednesday. It caused air traffic to shut down at some airports, impacted Coast Guard operations, took down the country's passport service, and took down the government's DigiID service.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Haroon Meer, Founder and CEO at Thinkst, about the company's evolution over the past 15 years, its focus on hacker-like internal culture, and the UK NCSC's new deception network.

Cybercrime and threat intel
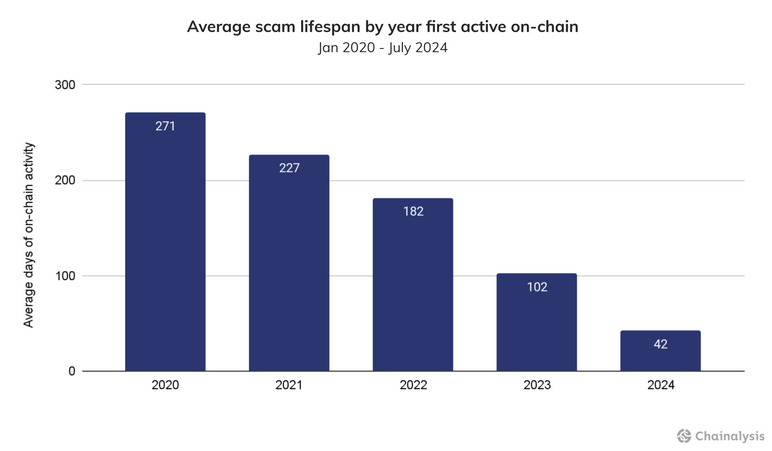
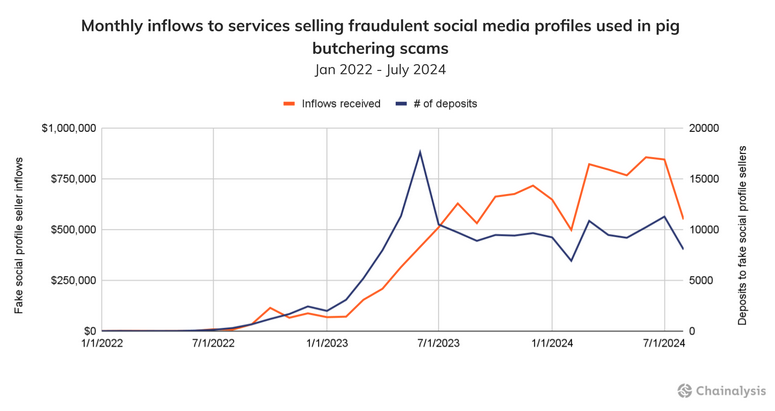
KK Park 2024 earnings: One of Myanmar's largest online scam compounds has made over $100 million worth of crypto-assets in the first half of the year alone. Blockchain tracking company Chainalysis says KK Park has adapted to the increased pressure from law enforcement agencies and is now running shorter scam campaigns to compensate for potential disruptions. KK Park's tactics are a representation of a general trend in the pig-butchering scene, where the lifespan of a scam operation has gone down from 271 days in 2020 to only 42 days this year.
Pizza chain phishing campaigns: BforeAI has uncovered a sophisticated phishing campaign targeting well-known international pizza restaurant chains. Targeted brands include Domino's Pizza, PizzaPizza, Little Caesars Pizza, Blaze Pizza, 241 Pizza, Panago Pizza, Boston Pizza, and others.
ASD phishing campaign: The ASD's ACSC has sent out a security alert about a phishing campaign using the agency's logo and name.
Mysterious phishing campaign: GuidePoint Security has identified a sophisticated campaign that uses a combination of social engineering and phishing portals to collect login credentials and one-time passcodes for users of Cisco VPN products. Researchers say the campaign has targeted over 130 US organizations in various industry verticals.
SLOW#TEMPEST phishing campaign: Securonix has published a report on SLOW#TEMPEST, a phishing campaign that targets Chinese-speaking users with Cobalt Strike and Mimikatz payloads.
Atlassian cryptomining campaign: Trend Micro looks at how threat actors are abusing CVE-2023-22527 for recent cryptomining campaigns. This was patched in January this year.
New CosmicSting attacks: SanSec looks at new attacks against Adobe Commerce and Magento sites via the CosmicSting vulnerability that are now deploying a new type of backdoor.
GenAI campaigns: Netcraft researchers analyze various phishing and scam sites that are now using GenAI to improve their lures and content.
Congratulations, AI folks! You've now managed to remove the spelling mistakes from phishing sites! That's quite impressive!
Link shortener campaigns: Google's Mandiant division looks at how link shorteners are currently being used in various malware and phishing operations by both cybercrime and APT groups.
Stolen check landscape: Recorded Future has published a report on the check fraud market. Probably the first report on this topic I've seen in a while now.
"Approximately 50% of stolen check images are posted within eight days of theft, emphasizing the speed at which stolen information circulates among cybercriminals. This quick turnaround time demands equally swift responses from affected parties to mitigate potential damages."
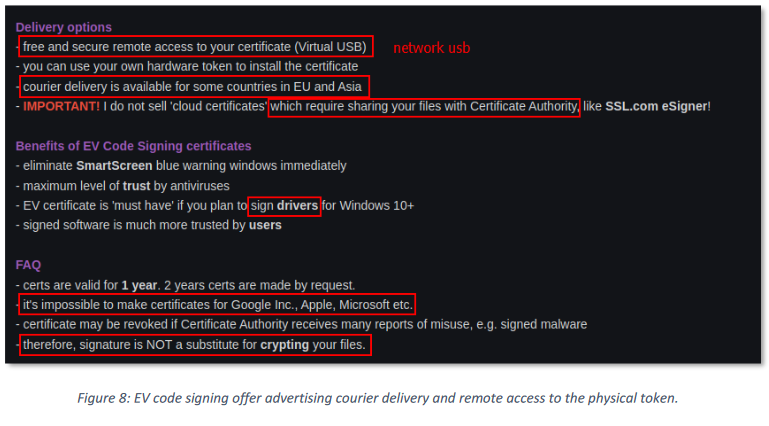
EV Code Signature Market: Intrinsec has published a report looking at the underground market that sells extended validation (EV) code-signing certificates to criminal groups.
France-v-Telegram on cybercrime forums: Threat intel firms Intel471 and KELA have published reports looking at how cybercriminals have reacted (or panicked) after learning of Durov's arrest in France.
"Some users of cybercrime/drugs supply services are taking precautions communicating with these services, with several pausing their activities on the Telegram platform. The services suppliers are concerned about the security of their operations, particularly those who have stored sensitive information on Telegram, recognizing that this could expose them to significant risks if authorities gain access."
Telegram DDoSaaS: FalconFeeds looks at the DDoS-as-a-Service business that has flourished on Telegram.
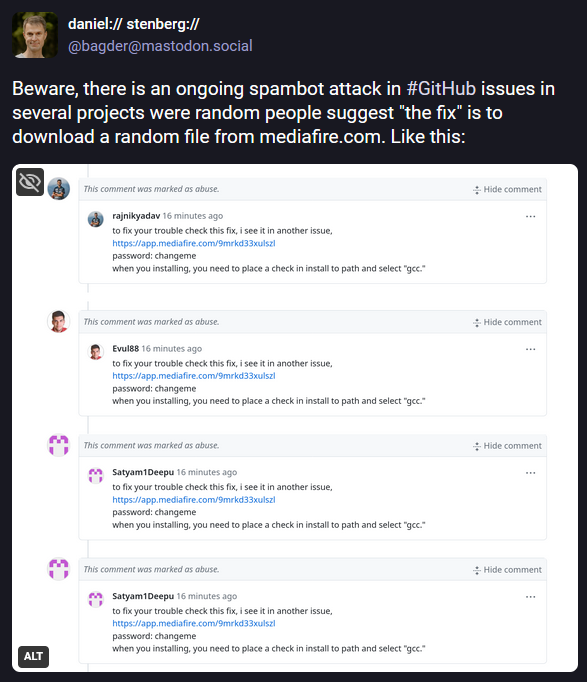
GitHub hit by new spam wave: A threat actor is spamming the issue trackers of GitHub projects with malicious links hosting malware. The campaign started this week and appears to be using a network of fake GitHub profiles to post the links on random projects. DevSecOps company Socket says the campaign has spammed thousands of GitHub issues in just a few hours. Repository admins have closed most of the issues but more than 800 still remain open. The spam contains links to MediaFire-hosted files containing a version of the LummaC2 infostealer.
Malware technical reports
7777 Botnet: Bitsight has published a report on the 7777, or Quad7, an IoT botnet known for its low and slow brute-force attacks on Microsoft 365 accounts. Similar reports are available from Sekoia and Team Cymru.
Unknown Python stealer: OALABS has published a report on an unknown Python infostealer.
Snake Keylogger: Fortinet's security team has published a report on the Snake Keylogger (404 Keylogger, KrakenKeylogger).
Latrodectus: Netskope has published a report on Latrodectus, a MaaS that appears to be the next iteration of the IcedID operation.
BlackByte ransomware: Cisco Talos says the BlackByte ransomware group is far more active than its public leak site may imply. The group has posted only 20-to-30% of victims on their leak site compared to the number of successful intrusions Talos has identified in telemetry data. Talos credited BlackByte's latest proficiency to its use of a new ESXi exploit (CVE-2024-37085). The BlackByte operation is believed to be one of the groups that separated from the larger Conti group in 2022.
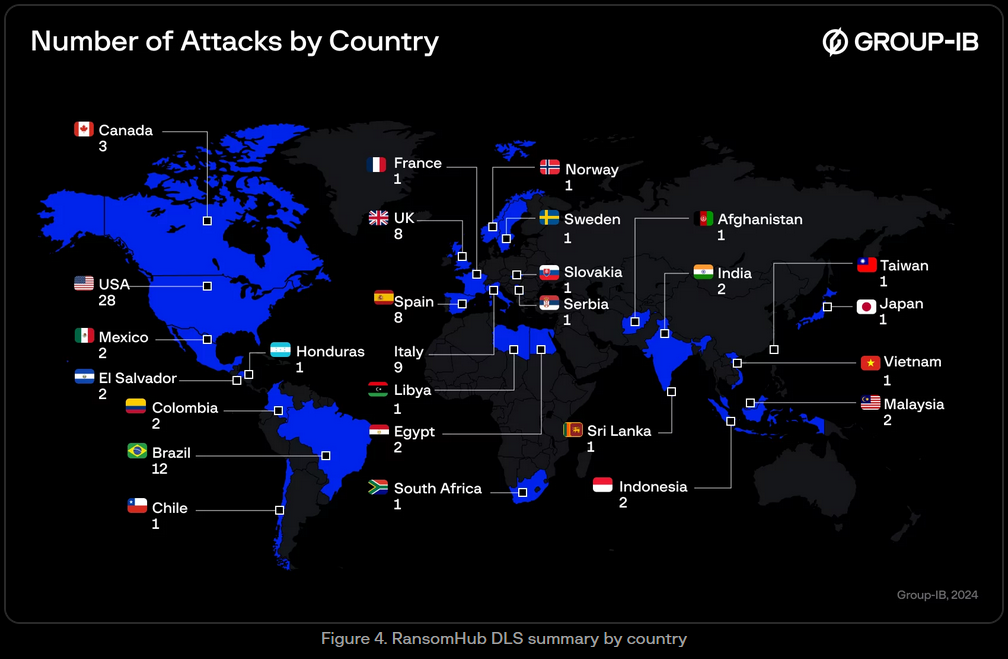
RansomHub ransomware: CISA, the FBI, the HHS, and MS-ISAC have published a technical report on the RansomHub ransomware. According to the report, since its inception in February 2024, RansomHub encrypted and exfiltrated data from at least 210 victims. Group-IB has also published a report on the same gang a day before.
Mekotio: CyFirma has published an analysis of Mekotio, a banking trojan widely used to target banks across LATAM.
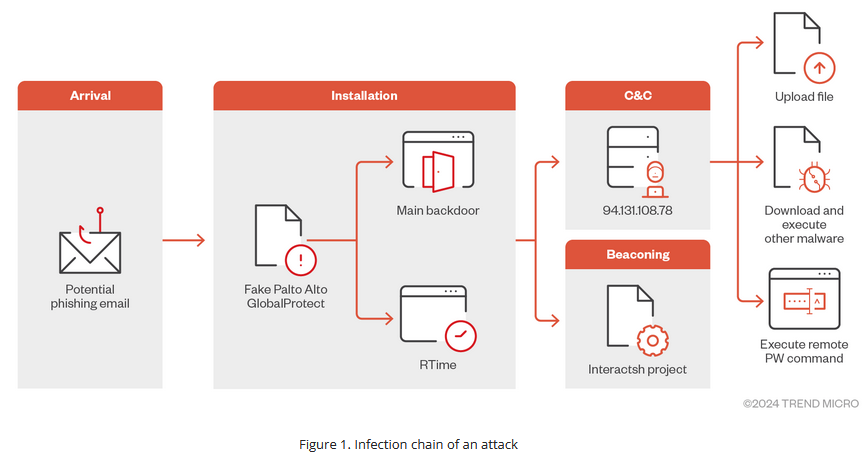
GlobalProtect malware: A mysterious threat actor is targeting users in the Middle East with malware disguised as a Palo Alto GlobalProtect setup utility. Security firm Trend Micro says the malware is sophisticated and can execute remote PowerShell commands, download and exfiltrate files, and bypass security sandbox solutions. Trend Micro has not attributed the campaign to any known group. The campaign is similar to attacks by pro-Palestinian hacktivist group Handala that used fake F5 security updates and CrowdStrike outage lure to deploy data wipers against Israeli organizations—although this time, the final payload is a lot more advanced.
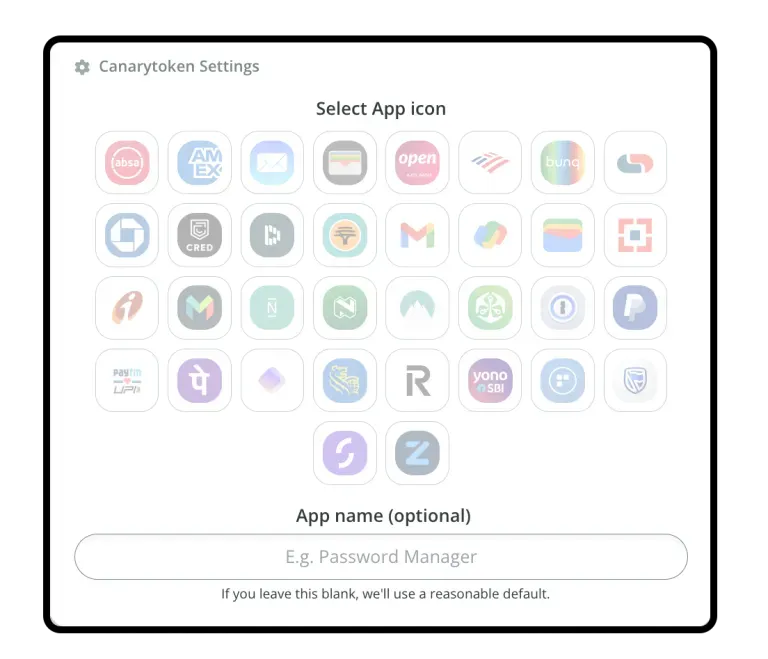
Sponsor Section
Thinkst launched earlier this month a new fake mobile app Canarytoken for your smartphone. The token can be configured to look like any app you want and alert security teams when it is opened—an indication the employer's device was either infected with malware looking for juicy stuff or fell into the hands of an unauthorized third party (also looking for juicy stuff).
APTs, cyber-espionage, and info-ops
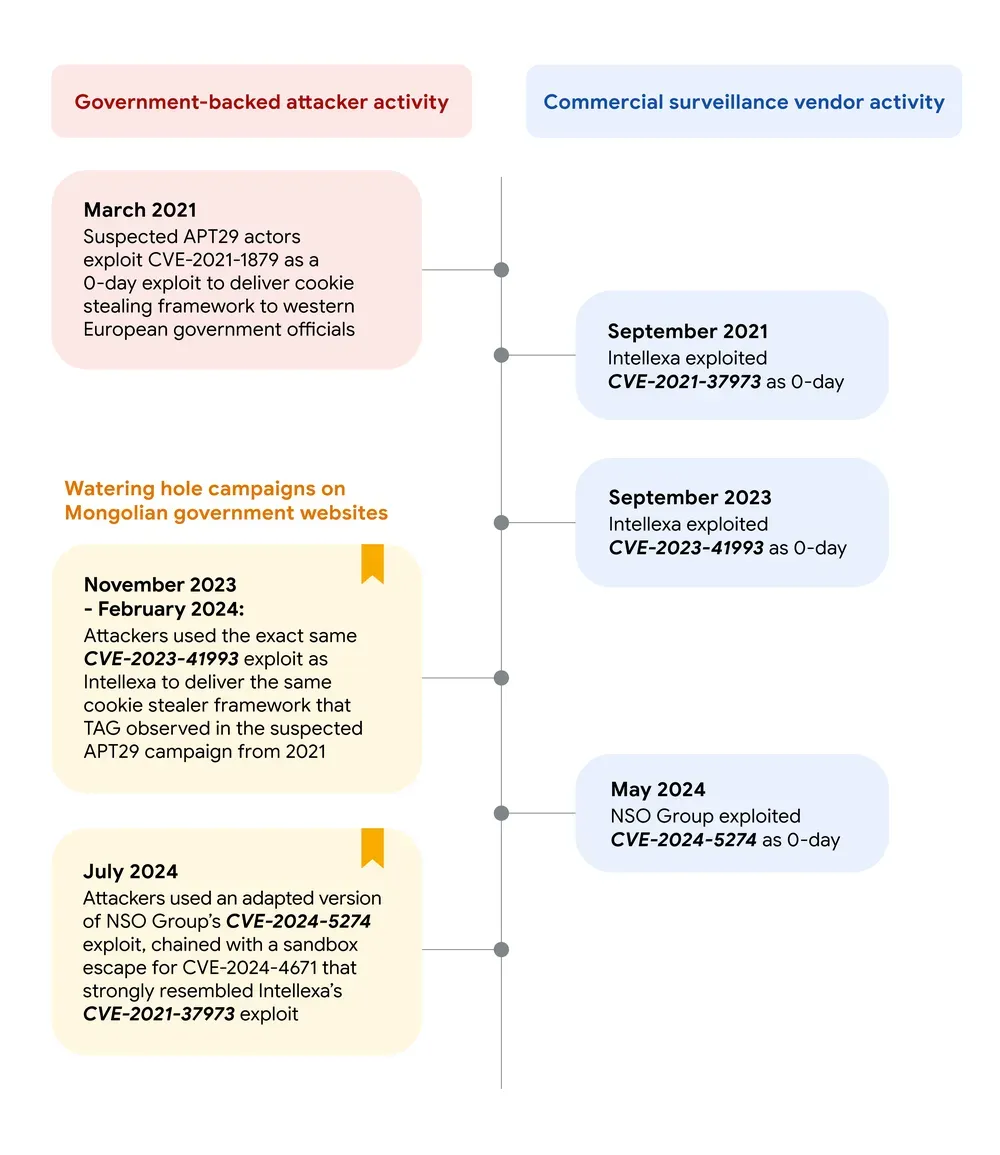
APT29 uses exploits similar to NSO&Intellexa: Russian cyber-espionage group APT29 has been spotted using multiple exploits in the wild that are "identical or strikingly similar" to exploits previously used by spyware vendors such as Intellexa or the NSO Group. Google says it found the APT29 exploits used in watering-hole attacks on Mongolian government websites between November 2023 and July this year. The exploits were for n-day vulnerabilities in iOS WebKit and Chrome for Android and were most likely used to infect the phones of Mongolian government workers. Google says it does not know how APT29 acquired the exploits from NSO and Intelleaxa.
APT activity inside Russia: Rostelecom's Solar security team has published a report covering APT activity targeting Russian entities in the first half of the year.
Disinformation in India: A Bellingcat investigation looks at how Indian disinformation sites are making bank via Google Ads.
APT-C-60's WPS zero-day: A suspected South Korean APT group has been exploiting a zero-day vulnerability (CVE-2024-7262) in the WPS Office for Windows client. The attacks appear to have been taking place since at least February this year and targeted multiple East Asian countries. Slovak security firm ESET discovered the zero-day and worked with the vendor to release a patch. The company linked the operation to a South Korean APT tracked as APT-C-60.
DPRK on npm: Phylum has published a report looking at a recent surge of North Korean activity trying to infect npm users with malware.
Kimsuky's BabyShark: South Korean security firm Hauri has published a report on Kimsuky's BabyShark malware.
Suspected APT32/OceanLotus campaign: Huntress has published a report on a suspected APT32/OceanLotus campaign that targeted Vietnamese human rights defenders. Ah, the enemies of all legitimate democratic states! The despicable human rights orgs! </s>
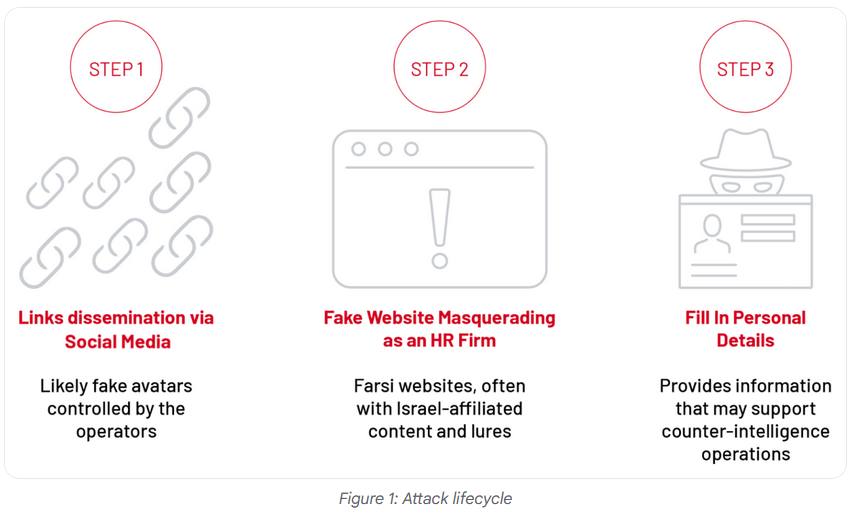
APT42 hunts regime traitors: Iran's APT42 cyber-espionage group is behind a long-lasting counter-intelligence campaign designed to identify traitors and collaborators inside Iran and its allies. Google says the campaign has been active since 2017 and used over 35 fake recruiting websites designed to lure Iranians and others to work for Mossad or other Israeli organizations. The campaign used Google Ads and social media accounts to target intelligence and military veterans inside Iran, the Assad regime, and Hezbollah. APT42's role appears to be to identify individuals who might betray Iran and pass down their details to Iran's other agencies. APT42 was previously linked to a cyber unit inside the Intelligence Organization of the Islamic Revolutionary Guard Corps (IRGC-IO).
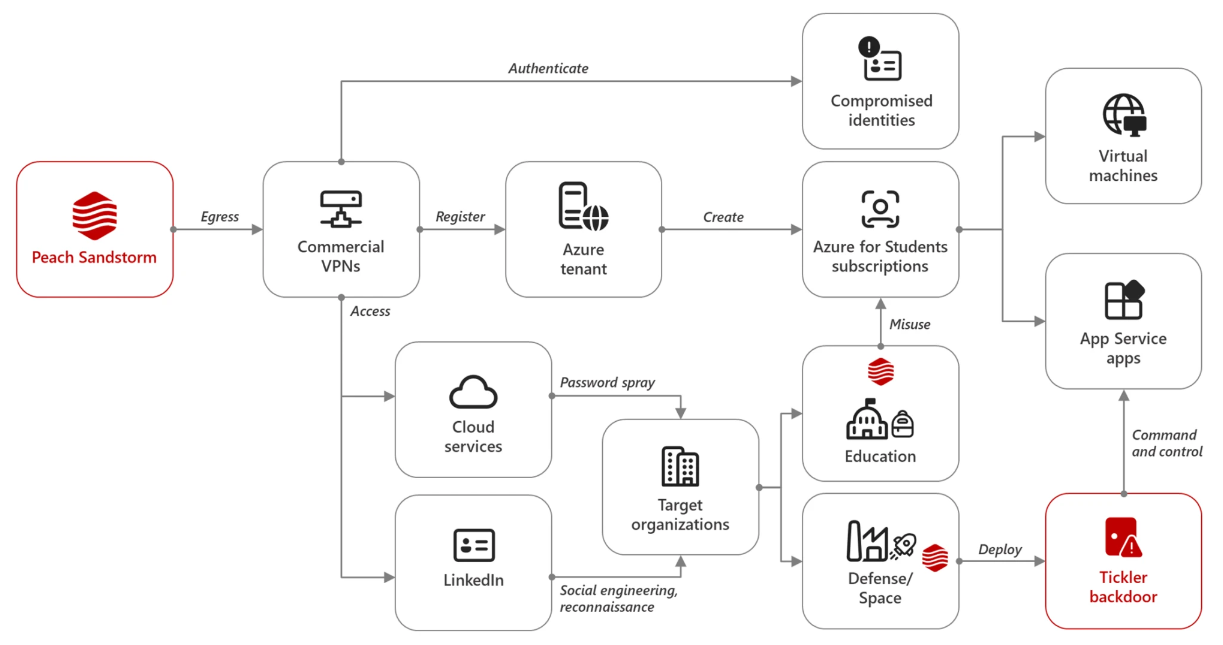
APT33's Tickler: Microsoft says that it spotted an Iranian APT group it tracks as Peach Sandstorm (APT33) deploy a new backdoor named Tickler in attacks against a wide range of targets around the globe. Targets included companies in the satellite, communications equipment, and oil and gas field, but also federal and state government sectors in the United States and the United Arab Emirates. The first Tickler infections date back to April this year.
Vulnerabilities, security research, and bug bounty
Cisco security updates: Cisco has released six security advisories for various products.
Fortra security update: Fortra has released security updates for its GoAnywhere and FileCatalyst products. [h/t ScreamingGoat]
JetBrains security update: JetBrains has released a security update for its TeamCity CI/CD server.
µC/OS audit: Cisco Talos has published the results of how it created a fuzzer and looked for vulnerabilities in the µC/OS open-source ICS protocol.
Jenkins RCE write-up: Conviso has published a technical analysis of CVE-2024-43044, an RCE bug in the Jenkins automation server that was patched at the start of the month.
WP plugin flaws: Security firm Project Black has found 14 vulnerabilities in WordPress plugins just by downloading their code and scanning it with Semgrep static analyzer for common misconfigurations.
PR-Agent vulnerability: Kudelski Security has published details about multiple vulnerabilities in PR-Agent, an AI-powered tool to automate pull requests. The vulnerabilities can be used to leak GitHub repository secrets, trigger secret GitHub workflows, and more.
3CX phone vulnerabilities: Security firm Praetorian has discovered a local privilege escalation and authenticated arbitrary file read vulnerability (CVE-2024-25085) in the 3CX Phone Management System.
AVTECH zero-day: IoT botnets have exploited a secret zero-day in AVTECH CCTV cameras to take over devices and launch DDoS attacks since at least December of last year. The zero-day exploits a command injection bug (CVE-2024-7029) in a feature that lets admins adjust the brightness of AVTECH cameras. Akamai says it notified AVTECH about the zero-day and the attacks earlier this year, but the company has not responded or released a patch. Akamai says proof-of-concept code for the zero-day has been available online since 2019 but went under the radar until the end of last year when IoT botnets started adopting the code. CISA told organizations earlier this month to put their AVTECH cameras behind a firewall to prevent the cameras from getting hacked.
Maltese party calls for end of white hats' investigation: The Malta Nationalist Party has called on the government to stop an investigation into four young security researchers. The four students were arrested and had their equipment seized after reporting a vulnerability and requesting a bug bounty reward from a local mobile app maker. The party's call to end the investigation comes after the app maker itself had requested the same last year. FreeHour says it initially misunderstood the report as an extortion attempt and reported the incident to police. The company tried to withdraw its report, but a criminal case was already underway. Both FreeHour and the National Party are now calling on the government to change its policy on cybersecurity and security research. [Additional coverage in Malta Today] [h/t DataBreaches.net]
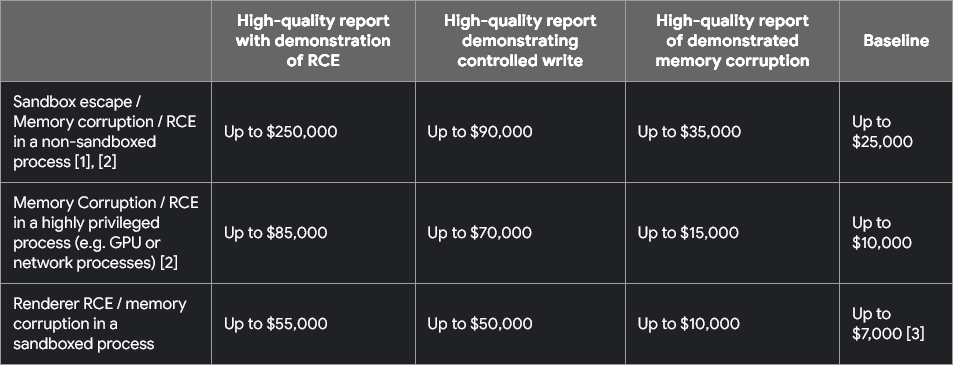
Google increases Chrome VRP rewards: Google has increased some of the payouts for its Chrome bug bounty platform. Payouts for some bug classes have been increased up to five times the old rates as exploitation of memory corruption bugs has now become harder. Researchers can earn up to $250,000 for a remote code execution exploit in a Chrome non-sandboxed environment. The increased payouts put the Chrome VRP on the same level in terms of rewards with the Android and Google Cloud bug bounty programs.
Infosec industry
New LinkedIn CISO: LinkedIn has hired former Twitter chief security information officer Lea Kissner as its new CISO. Kissner replaces Geoff Belknap, who moved into a secret security role at LinkedIn's parent company Microsoft. Kissner has worked in privacy and security role since 2018. [Additional coverage in SecurityWeek]
New tool—SeamlessPass: Security firm Malcrove has open-sourced SeamlessPass, a tool leveraging Kerberos tickets to get Microsoft 365 access tokens from organizations using the Seamless SSO service.
KCon 2024 talks: Slides from KnownSec's KCon 2024 security conference, which took place this week, are now available on GitHub. The slides are mostly in Chinese. This was the conference's 13th edition.
Threat/trend reports: Abnormal Security, Chainalysis, Immunefi, Recorded Future, and Rostelecom have recently published reports covering infosec industry threats and trends.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss the opportunities in phishing and why it is both easy and difficult.
In this podcast, Tom Uren and Patrick Gray discuss an Australian government effort to bridge the gap between online and real identity across the whole economy. It addresses a real need, but Tom doesn't think it will go smoothly.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!





