Risky Biz News: IR reports are not protected documents, multiple judges rule
In other news: US sanctions Chinese nationals behind proxy botnet; MediSecure asks for a government bailout; Check Point VPNs are under attack.

This newsletter is brought to you by SpecterOps, the experts in Attack Path Management. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Courts in three countries have now ruled that incident response and forensic reports are not protected legal documents and must be made available in other court cases or to authorities on request.
Legal precedents now exist in Australia, Canada, and the US.
In Australia, the precedent was in a class-action lawsuit related to the Optus September 2022 data breach. Optus argued that an incident response report it ordered from Deloitte was protected by client-attorney legal professional privilege. A federal court rejected the company's claim last November, and the company lost the appeal this week.
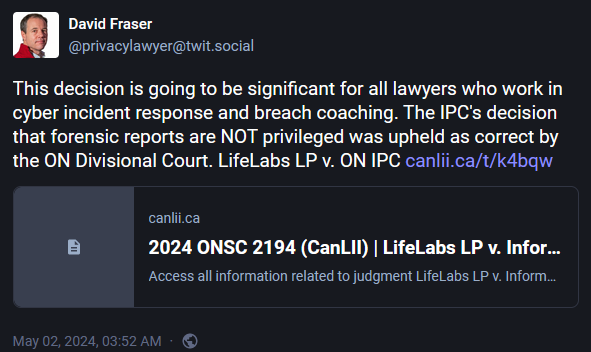
In Canada, the precedent was set in a case related to a data breach at private medical diagnostics company LifeLabs in 2019. Just like Optus, LifeLabs tried to argue that Canadian authorities did not have the right to publish details from its IR report because the document was subject to solicitor-client and litigation privilege. An Ontario divisional court disagreed with LifeLabs' classification.
In the US, the precedent is older and is related to the 2019 Capital One data breach. Back in May 2020, a judge ruled that plaintiffs in a class-action lawsuit were entitled to view a Mandiant IR report that Capital One commissioned after its breach. Just like in the other cases, Capital One tried to claim the report was a protected legal document under a business agreement.
The US ruling left the door open to have IR and forensics reports qualify for privilege when ordered directly by counsel—as explained by First Legal and law firm Stoel Rives.
"The court ruled that privilege did not apply to the forensic report because it was completed under the original retainer agreement, in which the bank directly engaged and paid Mandiant for their work. In order to ensure the report was protected, Capital One should have retained their law firm prior to the breach and instructed Mandiant to work at counsel's direction. This would have been sufficient to trigger attorney-client privilege and attorney work product doctrine."
Although this strategy seems to work in some cases, even this practice has been challenged recently, and the loophole of hiring your IR firm through your legal counsel may be closed soon.
Nevertheless, the 2020 Capital One ruling has had a major impact on the IR space. Shortly after the 2020 US decision was published, this newsletter's author heard from two cyber insurance providers that some companies were not only requesting IR reports via their counsels—to make sure client-attorney protected privilege applies—but were also going way above that.
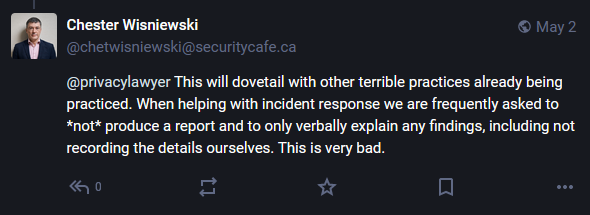
Breached companies began requesting that IR investigators not produce a report at all, instructing that all findings be delivered in oral form. All incident response communications were required to take place via IM clients that supported disappearing messages, and if an IR report needed to be put on paper, it had to contain the least information possible. The main purpose of all of this was to avoid leaving any paper trail that could be used in the discovery process of any possible class-action lawsuit.
My colleagues on the main Risky Business podcast also heard the same from different sources, and two years later, this now appears to be a standard practice, per Sophos CTO Chester Wisniewski.
Similar court rulings in other countries will most likely lead to widespread adoption of the "oral IR report" strategy across more geographical regions as companies try to bury their security failings.
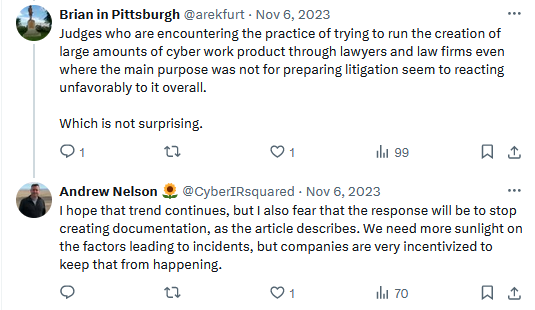
The trend of a regulatory crackdown and fines on hacked companies will also most likely exacerbate this trend going forward. As incident response consultant Andrew Nelson pointed out last year on Twitter, companies have no incentives to be candid about their breaches or share IR reports, as everything they get in return are fines, class-action lawsuits, scorn, and publish shaming.
Maybe the best effort to counter this trend came from the UK ICO last year when the agency promised smaller fines for companies that cooperated with authorities—but this won't protect companies from ambulance chasers. [h/t Ravi Nayyar]
Breaches, hacks, and security incidents
CDEK ransomware attack: Russian package delivery service CDEK has suspended operations in the aftermath of a ransomware attack over the weekend. A threat actor named Head Mare took credit for encrypting the company's server on Monday. The group has been attacking Russian organizations since December of last year and is most likely one of the lesser-known pro-Ukrainian hacktivist groups. [Additional coverage in Vedomosti]
Mpact ransomware attack: Belgian ride-sharing service Mpact is dealing with a week-old outage of its mobile apps in the aftermath of a ransomware attack. The hack took place last week, on May 22, and the company is unclear if hackers stole any of its customers' data. The incident is affecting ride-sharing and carpooling services in over 80 cities across Belgium.
Sav-Rx ransomware attack: Pharmaceutics prescription service Sav-Rx is notifying over 2.8 million customers that their personal data was stolen in an October 2023 security breach. The company was the victim of a ransomware attack. Sav-Rx claims the ransomware gang has now destroyed the stolen data, which suggests it paid the ransom.
Christie's ransomware attack: The RansomHub group took credit for the ransomware attack that hit major auction house Christie's ahead of a major sale. [Additional coverage in Artnet]
MediSecure asks for govt bailout: Australian electronic prescription provider MediSecure has requested a government bailout in the aftermath of a recent ransomware attack. The company claimed it needed the money to help cover its operating costs since the attack. Sources told the ABC that the Australian government has declined MediSecure's request. According to the news outlet, this was the first time a private company filed for financial support following a cyber attack. MediSecure's request came on the same day a threat actor began selling its data on a dark web forum for $50,000. The data is believed to be authentic, and Australia's National Cyber Security Coordinator told Australians not go look for this data.
Google Search leaks: An anonymous source has leaked some of Google's internal documents on how its search engine works, and it's no wonder current search results are flooded with c**p since most of this knowledge has been known by black-hat SEO groups since the early 2010s.
Guacamaya Mexico leaks: A collection of files leaked by hacktivist group Guacamaya from Mexico's military intelligence reveals that most of the guns used by Mexican cartels are bought from US gun shops. [Additional coverage in USA Today]
Internet Archive DDoS attack: The Internet Archive, the organization behind the Wayback Machine, fell under a DDoS attack on Monday. Reasons unclear.
General tech and privacy
CPython ownership: The creator of the Python programming language, Guido van Rossum, has dropped ownership of the CPython core code interpreter. Code ownership is now being passed to Microsoft's Mark Shannon and one of the project's three initial members.
YouTube's war on ad blockers: In its latest phase of the war against ad blockers, Google is now forcing YouTube videos to automatically skip to the end if the user is using an ad blocker. [Additional coverage in 9to5Google]
OpenAI creates Safety Board: OpenAI has established a Safety and Security Committee to advise its leadership on critical safety and security decisions for OpenAI projects. The major infosec name on the committee is former NSA Director of Cybersecurity Rob Joyce, who will serve as a consultant.
Government, politics, and policy
Pegasus in Rwanda: The Rwandan government has deployed the NSO Group's Pegasus spyware against past political opponents, its own ministers, and even the family of a former presidential candidate. Reporters from Forbidden Stories discovered the attacks in a leaked list of phone numbers targeted with Pegasus spyware. According to the same reporters, Rwandan officials had access to Pegasus between 2017 and 2021, after which its contract was not extended.
Thailand launches Cyber Command unit: The Thai government has ordered the creation of a Cyber Command unit in its armed military forces. The new unit must be operational by October this year. The country's air force and navy already operate cyber warfare units. The government also plans to work with educational institutions to train between 300 and 500 skilled personnel annually. [Additional coverage in The Nation]
New NL NCSC head: The Dutch government has named Matthijs van Amelsfort as the next head of the country's cybersecurity agency, the NCSC. Van Amelsfort previously served as the head of the Dutch police's High Tech Crime Team.
US govt RPKI adoption: The White House National Cyber Director Harry Coker has pledged that half of the IP addresses used by US federal agencies will be secured against BGP hijacks. Coker says government agencies are working to adopt Resource Public Key Infrastructure, or RPKI, for their internet infrastructure. The security of the BGP protocol and internet routing has become a recent priority for the US government and the FCC.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Justin Kohler, VP of the Bloodhound team at SpectreOps about 'attack paths', the ways that malicious actors maneuver through Active Directory to elevate their privileges. They discuss how and why they arise and what you can do about them.

Cybercrime and threat intel
US sanctions 911 S5 botnet: The US government has sanctioned three Chinese nationals for running a residential proxy botnet known as 911 S5. Officials say the trio compromised user devices to deploy their proxy malware and route malicious traffic. Treasury officials say they also linked the 911 S5 service to a series of bomb threats made throughout the US in July 2022. The 911 S5 service shut down the same month after hackers breached the service and leaked user data. Security firm Spur claims the service attempted to rebrand and relaunch as CloudRouter.
Scattered Spider membership: The FBI estimates that the Scattered Spider cybercrime group has almost 1,000 members. Speaking at a security conference last week, the FBI described the group as "very, very large" and claimed that many of the group's members don't know each other. According to CyberScoop, the group originates from an online community known as The Com.
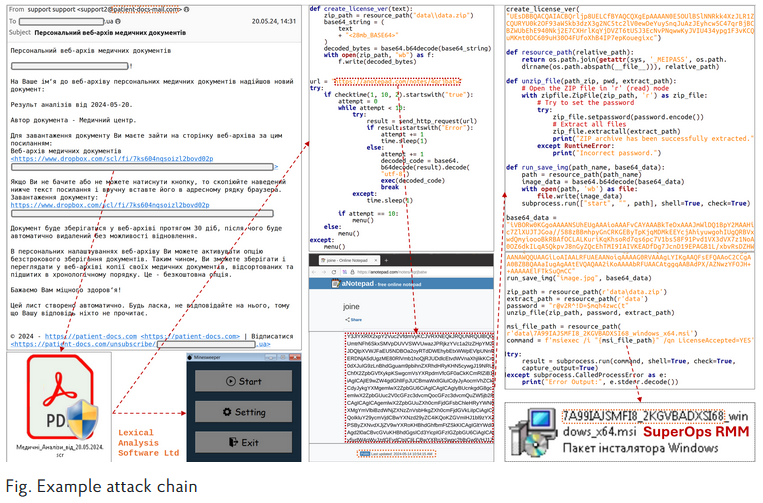
UAC-0188: Ukraine's CERT has discovered a malware delivery campaign that targets Ukrainian organizations. The final payload is a legitimate version of the SuperOps RMM remote management software, which the attackers use to access infected systems. CERT-UA linked the attacks to a group it tracks as UAC-0188. The group was also seen attacking European and US financial organizations.
Attacks on Check Point VPNs: Security firm Check Point has detected attacks against the VPN feature of its security appliances. The attacks took place over the past weeks and targeted its R80 and R81 devices. Check Point says the attackers compromised old VPN accounts that did not have 2FA enabled. The company has released a hotfix to block customers from logging into their VPNs with accounts that don't use a second authentication factor.
TXZ campaign: ISC Sans researchers have spotted a malspam campaign delivering malware hidden inside TXZ files, archives compiled with the now-notorious XZ file archiving utility.
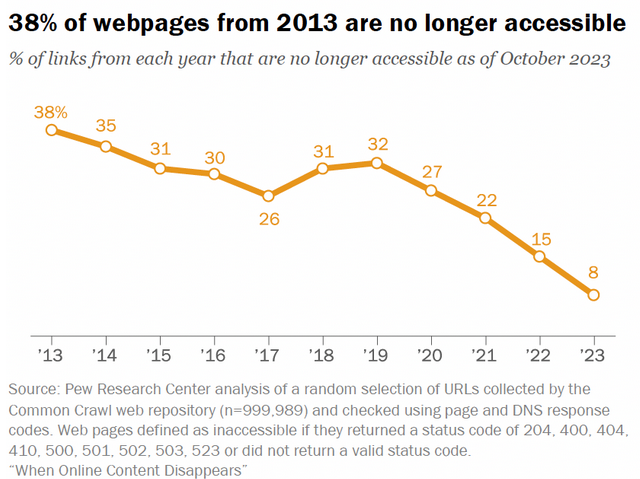
Threat/trend reports: Kaspersky and Pew Research have recently published reports covering infosec industry threats and trends.
Malware technical reports
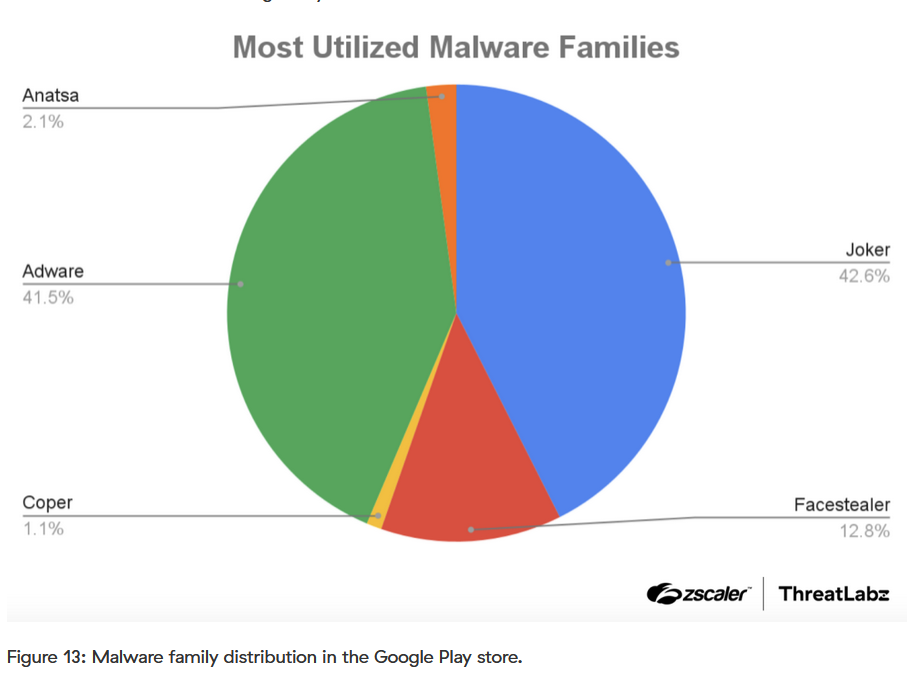
Anatsa on the Play Store: Threat actors have managed to slip apps infected with the Anatsa (TeaBot) banking trojan on the official Google Play Store. Security firm Zscaler has found PDF and QR code readers that act as loaders to deploy the Anatsa malware on user devices. Once installed, the app shows fake login screens to capture a user's e-banking credentials. According to Zscaler data, Anatsa accounts for 2.1% of all malware strains found on the official Play Store.
Kiteshield Packer: Chinese security firm QiAnXin has published a report on Kiteshield, an open-source packer for Linux ELF binaries that is currently abused in the wild by multiple threat actors targeting Linux infrastructure.
"Kiteshield wraps ELF binaries with multiple layers of encryption and injects them with loader code that decrypts, maps, and executes the packed binary entirely in userspace. A ptrace-based runtime engine ensures that only functions in the current call stack are decrypted at any given time and additionally implements a variety of anti-debugging techniques in order to make packed binaries as hard to reverse-engineer as possible. Both single and multithreaded binaries are supported."
Rebirth botnet: Cloud security firm Sysdig documents Rebirth, a DDoS service catering to the gaming community, and especially to Call of Duty Warzone players.
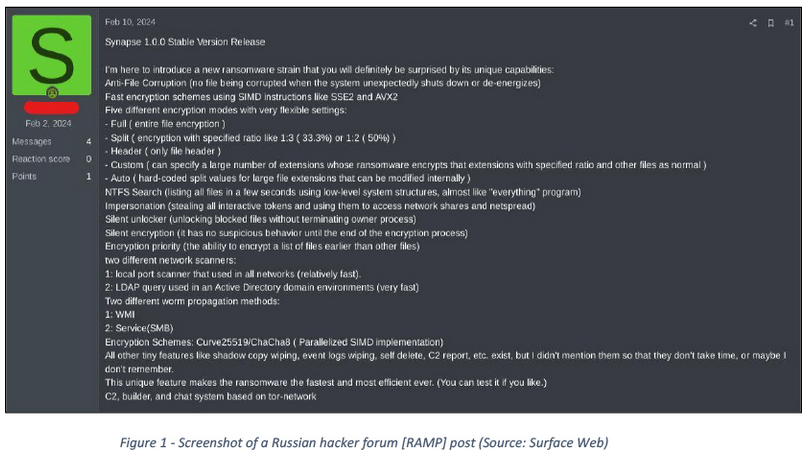
Synapse ransomware: Security researchers have discovered a new Ransomware-as-a-Service advertised on underground hacking forums since February this year. The new ransomware is named Synapse, and it contains code that spares Iranian systems from encryption. According to security firm CyFirma, earlier this year, the Synapse group released a demo video to prove they built the fastest file-encrypting ransomware to date.
Sponsor Section
Justin Kohler, VP of Product at SpecterOps, shows how BloodHound Enterprise can be used to find and fix Active Directory (mis)configurations that could let attackers easily own your entire enterprise.
APTs, cyber-espionage, and info-ops
Sapphire Werewolf: Russian security firm BI.ZONE has published a report on Sapphire Werewolf, a threat actor that has hit more than 300 Russian organizations since March this year. The group has often used Russian government documents as lures, and the final payload has been a version of the Amethyst stealer.
Blind Eagle: Lab52 says it spotted a spear-phishing campaign this month aimed at the Colombian Attorney General's Office. The company linked the campaign to a suspected Latin American APT known as Blind Eagle (APT-C-36).
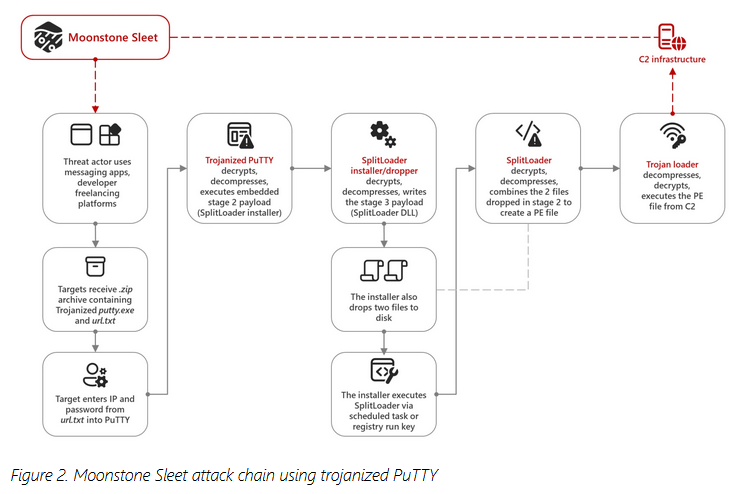
Moonstone Sleet: Microsoft's security team has discovered a new APT group named Moonstone Sleet (formerly Storm-1789) engaging in both cyber-espionage and revenue generation for the North Korean regime. Microsoft says it spotted the group when it splintered from the Diamond Sleet cluster last year and deployed its own infrastructure and attacks. Since then, the group has set up multiple fake companies to engage with potential targets in the blockchain and AI field and has used trojanized software and fake job lures to infect targets with malware. The group has also launched attacks with the FakePenny ransomware, and its members have sought employment at legitimate companies.
Vulnerabilities, security research, and bug bounty
Apple PoC: Security researcher Wang Tielen has published a PoC for CVE-2024-27842, a vulnerability patched this month by Apple that allows macOS apps to run arbitrary code with kernel privileges.
FortiSIEM PoC: Security firm Horizon3 has published a write-up and PoC on CVE-2024-23108, a command injection vulnerability in FortiSIEM appliances. The vulnerability has a rating of 10/10 and was patched last October. A write-up and PoC for a bug from the same patch is also available.
Glibc/PHP RCE: Ambionics researcher Charles Fol has published a write-up and PoC on a Glibc vulnerability (CVE-2024-2961) that can be used for remote code execution attacks on PHP-based applications and websites.
ManageEngine vulnerabilities: Security firm Shelltrail has published a three-part write-up [1, 2, 3] on two vulnerabilities (CVE-2024-36036 & CVE-2024-36037) in ManageEngine ADAudit Plus, a product used for real-time monitoring of Active Directory, Windows file servers, and Windows configuration change auditing.
Citrix security updates: Citrix has released a security update to patch a vulnerability in its Workspace app for Mac. [h/t Screaming Goat]
TP-Link Archer RCE: Security firm ONEKEY has discovered a major vulnerability in a TP-Link router model popular with the gaming community. Tracked as CVE-2024-5035, the vulnerability impacts TP-Link Archer routers and allows threat actors to run commands on the router with root privileges. The vulnerability has a severity rating of 10/10 and can be exploited remotely and without authentication. TP-Link has released firmware patches for affected router models at the end of last week.
Infosec industry
Tool update—ScoutSuite: The NCC Group has updated its cloud auditing tool ScoutSuite with support for Digital Ocean.
OBTS 2023: Talks from the Objective by the Sea 2023 security conference, which took place last October, are available on YouTube.
SecureWV 2023: Talks from the SecureWV 2023 security conference, which took place in October last year, are available on YouTube.
MCSC 2024: Talks from the Munich Cyber Security Conference 2024 security conference, which took place in February, are available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the role of the state in tackling ransomware, why action has been slow and ineffective, and what it will take to truly change the situation.




