Risky Biz News: IoT cybersecurity labeling scheme coming to the US in 2024
In other news: Cytrox and Intellexa sanctioned in the US; typos keep sending military emails to Mali domains; and a new Citrix zero-day exploited in the wild.
This newsletter is brought to you by asset inventory and network visibility company runZero. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Spotify:
The White House and the FCC have announced a voluntary cybersecurity labeling program for internet-connected devices sold in the US.
The program will roll out in 2024 and is named the US Cyber Trust Mark.
It will take the form of a shield logo applied to routers and IoT devices sold through US retailers. The logo will be applied to devices that meet a set of basic cybersecurity criteria, such as devices using unique and strong default passwords, can receive security updates, protect user data, and restrict access to their management interfaces.
The White House hopes the Cyber Trust Mark will be as successful as the Energy Star labeling program pioneered by the EPA and Department of Energy and will help consumers select and buy IoT devices that are secure out-of-the-box.
Device manufacturers and US retailers such as Amazon, Best Buy, Google, LG, Logitech, and Samsung have announced their participation in the program and plan to ship and sell devices that will have a Cyber Trust Mark if they meet the program's basic criteria.
The White House has tasked the FCC and NIST to produce these criteria, and NIST is expected to deliver a set of security requirements for consumer-grade routers by the end of the year—based on which the Cyber Trust Mark shield can be applied to a device.
Similarly, the Department of Energy has also started working on cybersecurity labeling requirements for smart meters and power inverters.
The White House started working on the program in October 2022, and the plan is to roll out cybersecurity requirements for other types of products and eventually cover most of the IoT and smart device space.
As devices receive the right to bear the Cyber Trust Mark shield logo, the risk of scammers and vendors illegally applying it to their products also grows.
The White House says it also tasked the FCC to create a national registry of certified devices that consumers can easily check online. The FCC will also work with the DOJ to establish oversight and enforcement safeguards and go after anyone misusing the Cyber Trust Mark logo to mislead consumers.
Similar IoT cybersecurity labeling schemes already exist in Germany, Singapore, the UK, and Finland—and Australia and the EU are working on theirs as well.
Breaches, hacks, and security incidents
VT customer leak: A file containing a list of more than 5,600 VirusTotal customers has leaked online. The leak contains the names and email addresses of account owners. Some accounts appear to be registered and used by representatives of various government and intelligence agencies from countries such as Germany, the US, the UK, Taiwan, and the Netherlands. [Additional coverage in Spiegel]
Dating apps leak: Security researcher Jeremiah Fowler has discovered a database server exposed on the internet without a password that contained more than 2.3 million records from three mobile dating applications. The leak is as sensitive as it gets, containing everything from names and emails to passwords and even sexually explicit images. Fowler says most of the exposed data appears to have originated from an app named 419 Dating – Chat & Flirt. A smaller subset of information appears to be from two other apps named Meet You (Enjoy Social App) and Speed Dating App For American (MyCircle Network Corp).
"Some of these images were NSFW (not safe for work) and contained sexually explicit images. I saw close up pictures of body parts and those with the users' faces. These identifiable images combined with names and emails could be a potential risk to the user."
Amazon in-van footage leak: Surveillance footage from Amazon delivery vans is being posted online, suggesting the company's video surveillance platform was either hacked or is leaking footage online. [Additional coverage in Motherboard]
Kronos ransomware lawsuit: UKG, the company behind the Kronos payroll management service, has agreed to pay $6 million to settle a class-action lawsuit filed in the aftermath of a ransomware attack that hit its cloud system back in December 2021. [Additional coverage in CybersecurityDive]
TOMRA cyberattack: TOMRA, one of the world's largest recyclers, has been hit by an "extensive cyberattack" that has impacted some of the company's IT systems. TOMRA says the attack took place early on Sunday, July 16, and they immediately took steps to isolate the affected systems. This sure sounds like ransomware, even if the company has not confirmed it. Big corps like TOMRA don't just isolate entire systems because they found some infostealer or downloader on their network.
Odessa breach (maybe): US authorities are investigating a security incident in the city of Odessa, Texas. Officials say that an unidentified threat actor has accessed numerous city computer networks several times over the past month using the accounts of former Odessa City Attorney Natasha Brooks, which were not deactivated after she was fired. The intruder is believed to have accessed information from the Odessa Police Department and the GovQA public requests platform and exfiltrated hundreds of emails to a remote account. Brooks is currently fighting her firing as a "breach of contract and race discrimination." At this point, it's unclear if Brooks re-accessed her accounts or if city officials are making this up. There is some serious drama going on here. [Additional coverage in OA Online]
General tech and privacy
Meta fined in Norway: Norway's privacy watchdog Datatilsynet has banned Meta from running behavioral advertising on Facebook and Instagram unless the company obtains specific consent from Norwegian users to process their personal data. The agency plans to fine Meta one million crowns ($100,000) per day starting August 4 for the next three months unless the company takes action. The Datatilsynet plans to take its decision to the European Data Protection Board (EDPB) in the hopes of making the fine permanent and maybe enforced across the entirety of the EU.
Wikipedia joins Mastodon: The Wikimedia Foundation has joined and launched its own Mastodon instance—in case you were looking for a safe server to join.
Chrome 115: Google Chrome v115 has started rolling out to users. The major feature included in this version is Google's new Privacy Sandbox ad-targeting technology.
Government, politics, and policy
US sanctions Cytrox and Intellexa: The US government has sanctioned Cytrox and Intellexa, two EU-based spyware vendors whose Predator hacking tool has been abused to spy on Greek journalists and politicians. Four legal entities associated with the two companies have been added to the US Department of Commerce entity export list. Presence on the Entity List prohibits any US organization or individual from doing business with Cytrox and Intellexa without specific approval from the US government. Cytrox and Intellexa join NSO Group, Candiru, Positive Technologies, and CSIS, four other spyware makers and exploit vendors that were added to the list in November 2021. NSO's inclusion on the Entity List in 2021 is believed to have effectively destroyed the company's business.
Top US cyber official denied post: The White House does not plan to nominate Kemba Walden to serve as permanent National Cyber Director. Walden has been occupying the position in a temporary designation since Chris Inglis left the post in February of this year. Reporting in US media claims the White House believes Walden's personal debt would make it difficult to push her nomination through Congress, despite receiving glaring endorsements from both parties and her predecessor. In Walden's place, the Biden administration plans to nominate retired Navy, CIA, and NSA officer Harry Coker. [Additional coverage in Reuters]
Typo sends military emails to Mali domains: A Dutch internet expert warns that thousands of Pentagon emails are being sent to Mali domains by accident every day because users are mistyping the .mil domain as .ml. The problem was identified by Johannes Zuurbier, A Dutch IT expert who used to manage the .ml domain on behalf of Freenom for over a decade until this week when the domain went back to Mali officials. Zuurbier says the Russian-allied Mali government will now be able to collect missent emails and data-mine them to gain access to sensitive data, such as passwords for US government systems, diplomatic documents, and travel details of US military personnel. [Additional coverage in The Financial Times/non-paywall]
Cyber Flag 2023: The Cyber Flag yearly virtual exercise will take place next week. Hosted by US CyberCommand, this year's edition will host cyber units from the Five Eyes alliance (US, UK, Canada, Australia, and New Zealand) but also South Korea. The role of the exercise is to bolster defense and information sharing.
5G network slicing guidance: CISA and the NSA have released additional guidance on the topic of 5G network slicing. The new paper comes to complete a guide the two agencies initially released back in December 2022.
CISA cloud security tools: Over the past few months, CISA has been releasing a bunch of cloud security and review tools. It has now released a dedicated page to host links to all, so you won't have to go around sifting and getting lost in their GitHub repo.
Sponsor section
This week's sponsor is RunZero. In this Risky Business News sponsor interview, Tom Uren talks to RunZero CEO Chris Kirsch about how the company has evolved from offering an active scanning product to one that can now discover assets on OT and cloud environments using both active and passive scanning approaches:
Cybercrime and threat intel
BEC scammer sentenced: A Nigerian man named Olalekan Jacob Ponle has been sentenced to eight years in prison in the US for his role in BEC attacks that stole more than $8 million from victims.
Hackers arrested in Azerbaijan: Azerbaijan officials have detained three men suspected of hacking a major local food corporation. Officials say the trio tried to sell the company's stolen data for $35,000. [Additional coverage in Sputnik Azerbaijan]
Russian bot form dismantled: Ukraine's Cyber Police has dismantled a bot farm operating in Western Ukraine that published Russian propaganda and disinformation about the war in Ukraine. Officials seized more than 250 GSM gateways and 150,000 SIM cards that were used to register accounts on social media across different mobile operators. Ukrainian police believe more than 100 people were involved in running the bot farm.
RedCurl attack: The RedCurl cybercrime group [1, 2] has allegedly breached a major Russian bank. According to Russian security firm FACCT, the group breached the bank's network by one of its contractors after its phishing attacks against the bank's employees failed.
Malicious PyPI package: Sonatype researchers have discovered a malicious Python library named "feur" that was available through the official PyPI portal and tried to infect Windows users with the NullRAT infostealer.
La_Citrix self-dox: An initial-access broker named La_Citrix has infected his own system with an infostealer and accidentally sold his own personal data on underground forums, allowing security firm HudsonRock to identify their real-world identity.
Soup crypto-scammer: Blockchain investigator ZachXBT claims that a threat actor named "Soup" has stolen more than $1 million worth of crypto-assets by luring victims into joining a malicious Discord server. ZachXBT claims the threat actor is a Canadian man named "Dan," who laundered the funds using Roblox in-game items.
WebAPK phishing: Google's WebAPK technology can be used for phishing attacks, per a CSIRT KNF report.
FBI tech support scam warning: The FBI warns about the rise in tech support scams that target the elderly and ask victims to send cash to the scammers through shipping companies. This is a change from the usual modus operandi where scammers ask victims for bank transfers, cryptocurrencies, or gift cards.
Email extortions: A Barracuda investigation found that roughly the same 100 Bitcoin addresses appeared in 80% of emails analyzed from a sample of 300,000 extortion emails detected by the company over a one-year period. The company says the limited number of observed Bitcoin addresses suggests that only a handful of attackers are most likely behind most of these campaigns, which should make it easy for law enforcement to deanonymize and disrupt operations.
"We conclude that attackers are somewhat lazy in obfuscating their identity and, in the vast majority of cases, seem to use the same bitcoin address for these scams. Once again, this leaves us somewhat optimistic because it leaves the possibility that this relatively small number of bitcoin addresses (and attackers) can be tracked down by law enforcement."
Malware technical reports
Sardonic backdoor: Broadcom's Symantec has a report out on Sardonic, a backdoor used by the Syssphinx (FIN8) group to deploy the Noberus (BlackCat) ransomware.
VoidRAT: SecurityScorecard's Vlad Pasca has a breakdown of VoidRAT, a fork of the open-source Quasar RAT.
Danabot: Version 3 of the Danabot malware has been spotted in the wild. According to Flashpoint, the malware is being advertised on underground forums as DBot v.3.
LOBSHOT: OALABS has published IOCs on LOBSHOT, a new malware strain distributed via malicious Google ads.
NoEscape ransomware: A new ransomware operation named NoEscape is believed to be a new incarnation of the old Avaddon ransomware group. Avaddon shut down operations in 2021 and released decryption keys for all victims after US and Australian authorities started focusing on its activities. The new NoEscape operation launched in June 2023 and appears to be using a decrypter almost identical to the one used by Avaddon in the past. Just like most ransomware operations today, the NoEscape group has encrypters for Windows, Linux, and VMware ESXi, and primarily targets enterprise systems.
Sponsor Demo
RunZero is one of this newsletter's main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network, including OT devices in critical environments. To learn more, please check out this runZero product demo below:
APTs and cyber-espionage
APT28: EclecticIQ researchers have published a report linking the recent attacks against RoundCube email servers and the Zimbra collaboration platform to the same attacker. Researchers say attackers have breached RoundCube and Zimbra servers in order to execute phishing campaigns targeted at government entities in Ukraine, but also Spain, Indonesia, and France. The operation has been active since January 2023, and RecordedFuture and CERT-Ukraine previously linked it to GRU's APT28 group.
Vulnerabilities, security research, and bug bounty
Pwn2Own Toronto 2023: Rules for the Pwn2Own Toronto 2023 hacking contest are now live. Up for hacking will be smartphones, printers, SOHO routers, smart speakers, NAS devices, surveillance systems, and home automation systems. The contest is scheduled for late October this year.
WooCommerce Payments exploitation: Threat actors are exploiting a recently disclosed vulnerability (CVE-2023-28121) in the WooCommerce Payments plugin to take over WordPress sites. According to website firewall provider Wordfence, attacks began last week and peaked on Saturday when more than 157,000 sites were hit. The plugin is installed on more than 500,000 sites, all of which are online stores.
Adobe ColdFusion exploitation: Threat actors are exploiting two Adobe ColdFusion vulnerabilities to install web shells on servers that are not running up-to-date patches. The unidentified attackers appear to be exploiting an incorrectly patched (for CVE-2023-29298) and an accidentally disclosed vulnerability (CVE-2023-29303 derived from a CVE-2023-29300 write-up). According to Rapid7, the attacker is using the two vulnerabilities chained together to install webshells on ColdFusion servers. Adobe released security updates on Tuesday and Friday last week to address the vulnerabilities. Installing the Friday, July 14 patches, should stop the ongoing attacks for the time being.
Citrix exploitation: Networking equipment vendor Citrix has released security patches to fix a zero-day vulnerability (CVE-2023-3519) targeting its ADC and NetScaler gateway devices. The zero-day is described as an unauthenticated remote code execution. Besides the zero-day, the updates also address two other vulnerabilities. Citrix credited security firm Resillion for discovering the three vulnerabilities and the ongoing attacks.
Jira exploitation: Also in exploitation news, a threat actor is also scanning for Jira instances and attempting to exploit two vulnerabilities (CVE-2023-26255 and CVE-2023-26256) in servers that run the "Stagil navigation for Jira – Menus & Themes" plugin. SANS ISC reports a huge spike in scans targeting the plugin.
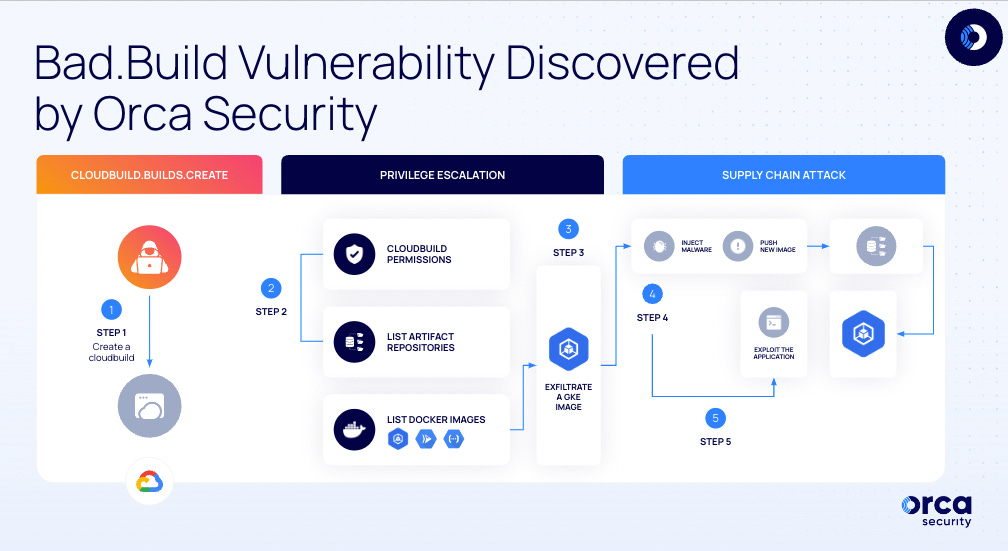
Bad.Build vulnerability: Orca Security has discovered a design flaw in the Google Cloud build service that can allow attackers to impersonate the service and gain unauthorized access to code repositories and images hosted in its Artifact Registry. Orca says the issue could have been exploited to insert malicious code into legitimate repositories or project images and mount supply chain attacks against Google Cloud customers. Google has issued a partial fix for the issue—nicknamed Bad.Build—in June. According to Orca, Bad.Build attacks are still possible even after the partial fix.
Infosec industry
Industrial protocols: Orange's cybersecurity team has put together a GitHub repo with a large collection of tutorials and breakdowns of common industrial protocols, such as DICOM, ICCP, SLMP, and others.
Risky Business Podcasts
In this podcast, Patrick Gray and Tom Uren talk about Citizen Lab's analysis of WeChat's behavior and its privacy policy.




