Risky Biz News: Interpol arrests scammers linked to Nigerian "Air Lords" crime syndicate
In other news: Ransomware attack on Ghana's energy company results in power outages; new Pegasus cases surface in Indonesia and Mexico; and CISA to move to TLP 2.0 in November.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Interpol and South African officials detained last week two Nigerian nationals in Pretoria for their roles in a sprawling cybercrime campaign that stole more than $1.8 million from victims via online romance scams and business email compromise (BEC) operations.
Authorities did not release the names of the two suspects, but local media reported that the two are aged 39 and 42, respectively, and members of the Air Lords criminal syndicate.
Also known as the National Association of Airlords, Supreme Eiye Confraternity (SEC), or just Eiye, the group was established in 1963 as a student organization that slowly evolved into a secret cult and confraternity and eventually into a fully-fledged crime syndicate, currently mostly known for its involvement in sex trafficking and sex slavery across Africa and Europe.
An INTERPOL team is on the ground in South Africa🇿🇦 this week where two suspected organized crime members were arrested as part of a global operation against large-scale #FinancialCrime 💸
— INTERPOL (@INTERPOL_HQ) 2:55 PM ∙ Sep 30, 2022
The suspects are wanted for online scams that extracted $1.8 million from victims.
The arrests last week mark the first time Air Lords members were arrested on cybercrime-related charges.
Previously, past Interpol and FBI operations had gone after suspects linked to Black Axe, another Nigerian confraternity that devolved into a global crime syndicate.
While Black Axe members have been arrested for cybercrime activities as far back as 2015, international law enforcement started heavily concentrating on the group cybercrime "division" last year, with several crackdowns in September 2021, October 2021, April 2022, and May 2022.
In September 2021, Europol also detained 106 members of the Italian Neapolitan mafia for their roles in cybercrime-related operations, such as SIM swapping attacks, phishing, and vishing, showing a worrying trend where classic crime syndicates are slowly getting more and more involved with cybercrime activities.
While Nigerian threat actors have always been active in the online space since the 90s, with online romance and 419 scams being their area of expertise, a 2018 CrowdStrike report [PDF] warned that Nigerian groups were slowly moving into the BEC scam landscape and specifically gave an early warning regarding Black Axe, which, based on the recent arrests, seems to have been pretty accurate.
Breaches and hacks
Transit Swap crypto-heist: Decentralized cryptocurrency exchange platform Transit Swap lost $21 million / $23 million worth of funds after a hacker exploited a bug in its code on Saturday. The company confirmed the hack on Sunday and said they have "the hacker's IP, email address, and associated on-chain addresses," and are working to recover the funds. According to blockchain security firm SlowMist, the attacker appears to have returned 70% of the stolen funds already.
— Transit Swap | Transit Buy | NFT (@TransitFinance) 3:18 AM ∙ Oct 2, 2022
Whistleblower hacks: In a Twitter threat last week, Hindenburg Research, a research agency that exposed a fraud case inside Nikola Corp, said that critics and whistleblowers inside the company were targeted by hackers shortly after the company's wrongdoings were exposed back in 2020.
Trevor Milton, billionaire founder of $NKLA, is currently on trial for fraud.
— Hindenburg Research (@HindenburgRes) 6:45 PM ∙ Sep 29, 2022
Shortly after his hydrogen truck company was exposed, an army of hackers and spies started targeting his critics and whistleblowers.
Here's what happened & how we turned the tables.
(1/x)
ECG hack: For almost a week, Ghanaians have been unable to purchase any new power credits and have had electricity cut off to their homes after a threat actor hacked the Electricity Company of Ghana (ECG) and locked its servers, in what local experts are calling a suspected ransomware attack.
CBSA breach: Canada's privacy commissioner's office said that the data of 1.38 million Canadians were exposed after a security breach at one of the Canada Border Services Agency's contractors. The incident took place in 2019, targeted a US company used by the CBSA, and involved approximately 9,000 photos of licence plates collected from travellers entering Canada at the Cornwall, Ontario, border crossing.
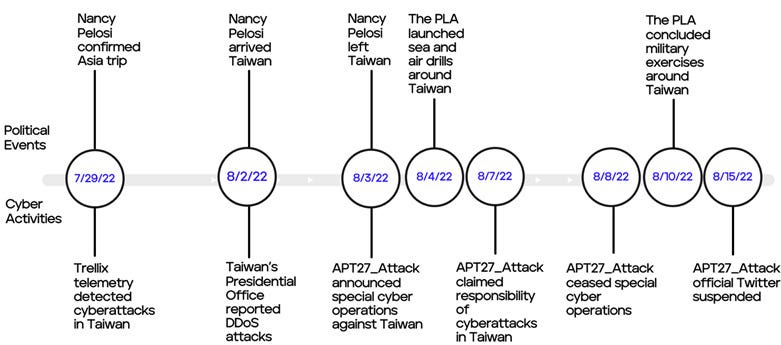
Pelosi's Taiwan visit and the cyberattacks: In a report last week, security firm Trellix linked several of the cyberattacks that hit Taiwanese government systems ahead of Nancy Pelosi's visit to several Chinese hacktivist groups—even the ones from a group claiming to be "APT27."
While the hacktivist group APT27_Attack claimed responsibility for these DDoS attacks, this hacktivist group is unlikely the same group as the APT27 espionage group known as Emissary Panda. The group's Twitter post claiming to be "APT27" is therefore a false flag, which successfully misled most major news agencies in their news reports.
General tech and privacy
US rep wins UN ITU election: US representative Doreen Bogdan-Martin was elected as the new head of the UN's International Telecommunication Union (ITU), a crucial agency that sets global standards for telecoms and tech infrastructure. Bogdan-Martin won 139 of the 175 possible votes, defeating Russia's representative and replacing China's Houlin Zhao, who has led the ITU for two consecutive terms since 2014. [Additional coverage in Politico Europe]
Microsoft rewrites SmartScreen technology: Microsoft said they rewrote the entire Windows Defender SmartScreen technology (Microsoft's SafeBrowsing analog) "to improve reliability, performance, and cross-platform portability" and detect phishing and malicious sites faster.
Government, politics, and policy
Pegasus in Indonesia: More than a dozen senior Indonesian government and military officials had iPhone devices targeted with spyware made by NSO Group. Reuters reported on Friday that Chief Economic Minister Airlangga Hartarto, senior military personnel, two regional diplomats, and advisers in Indonesia's defense and foreign affairs ministries were notified by Apple in November 2021 about the attacks, which allegedly involved the ForcedEntry exploit.
Pegasus in Mexico (again): In the meantime, R3D and Citizen Lab have published reports on new cases where the Pegasus spyware was used against Mexican journalists and human rights defenders. The spying incidents allegedly took place between 2019 and 2021, are believed to have been carried out under the guidance of government officials, and took place after Mexico's president assured the public the government would stop using the spyware after similar incidents were disclosed in 2017.
Russia sets up cybercrime-fighting agency: Russia's Ministry of Internal Affairs announced on Friday the creation of UBK, a new unit inside the ministry dedicated to fighting cybercrime.
Russia blocks Soundcloud: Roskomnadzor, Russia's telecommunications watchdog, blocked access to music streaming platform Soundcloud, most likely related to the platform hosting podcasts discussing Russia's invasion of Ukraine. According to Podcasts.ru, Soundcloud's mobile app is still working, and only the main web portal appears to have been blocked.
CISA to move to TLP 2.0: The US Cybersecurity and Infrastructure Security Agency said it plans to migrate to the new TLP 2.0 protocol in November this year.
Sponsor section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
Cybercrime and threat intel
Phisher arrested in Germany: German police said last week that they detained a 24-year-old man for stealing €4 million from personal bank accounts. Authorities said the suspect gained access to the accounts after phishing the account owners, including for the TAN (transaction) codes needed to exfil funds.
REF2731: Elastic's security team has published a report on REF2731, a malware campaign that deploys the PARALLAX loader to install the Netwire RAT.
Diavol comeback: Walmart's security team said last week that they saw new attacks using the Diavol ransomware, developed by a former TrickBot member Alla Witte, who is currently in custody.
Phishing with Chromium's Application Mode: Vulnerability researcher and pen-tester mr.d0x has published technical research showing how the Application Mode (--app command line flag) in Chromium-based browsers like Google Chrome and Microsoft Edge can be used to create realistic desktop phishing applications.
CISA KEV update: CISA has updated its KEV database with three new vulnerabilities that are being exploited in the wild. This includes the two zero-days in Microsoft Exchange servers disclosed last week (CVE-2022-41040 and CVE-2022-41082) and a vulnerability in Atlassian Bitbucket servers (CVE-2022-36804).
Malware technical reports
BlueSky ransomware: Italian security firm YOROI has published a technical breakdown of the BlueSky ransomware. First spotted in the wild in May this year, the ransomware is believed to be operated by a Russian national from Krasnodar, according to a previous report from CloudSEK.
DJVU ransomware: BlueBerry's security team published last week an analysis of the ever-evolving DJVU (STOP) ransomware. According to BlackBerry researchers, in recent campaigns, DJVU was often seen deployed after the victim was initially compromised with the RedLine infostealer.
APTs and cyber-espionage
Comm100 supply chain attack: CrowdStrike said on Friday that it detected that a suspected Chinese threat actor compromised the infrastructure of Comm100, a Canadian company that provides customer support chat applications, and has modified one of its installers to deliver malware to its customers' networks. The security vendor said the compromise was short-lived and only lasted from September 27 through September 29, when its security team detected malware being delivered through the platform.
The trojanized file was identified at organizations in the industrial, healthcare, technology, manufacturing, insurance and telecommunications sectors in North America and Europe.
Lazarus campaign in NE/BE: ESET published a report on Friday about an Amazon-themed spear-phishing campaign carried out by the Lazarus North Korean APT against targets in Belgium and the Netherlands during the fall of 2021. Confirmed targets of these attacks include an employee of an aerospace company in the Netherlands and a political journalist in Belgium. Lazarus used their tried-and-tested BYOVD (Bring Your Own Vulnerable Driver) technique to elevate privileges on the attacked machine and install the BLINDINGCAN backdoor. In this case, ESET said Lazarus exploited a vulnerability in a Dell driver.
ShadowPad intrusion: NCC Group researchers have a write-up on a Chinese APT intrusion that began with the exploitation of a WSO2 device via CVE-2022-29464 and ended with the deployment of the ShadowPad backdoor and data exfil.
WindShift APT: macOS malware connaisseur Patrick Wardle has analyzed WindTape, a second-stage macOS backdoor used by the WindShift APT.
Vulnerabilities and bug bounty
Exchange zero-days: After a report from Vietnamese security firm GTSC, Microsoft formally confirmed the existence of two new Exchange zero-days on Friday. The OS maker released mitigations, assigned CVE-2022-41040 and CVE-2022-41082 to the two vulnerabilities but did not provide a timeline for any security patches yet.
Poisoning Akamai's entire CDN cache: Italian security researchers Jacopo Tediosi and Francesco Mariani discovered a technique that would allow them to poison the cache of all websites running on Akamai's CDN. While Akamai didn't have a bug bounty program, the two researchers said they made roughly $50,000 by reporting the issue to many of Akamai's customers.
Infosec industry
Zscaler buys ShiftRight: Security firm Zscaler has acquired ShiftRight, a company specializing in security workflow automation services. The acquisition was announced in June—for $25.6 million—and closed last week.
New tool—AzTokenFinder: Security researcher @HackmichNet released last week a tool called AzTokenFinder that can find and extract Azure tokens from other processes, like PowerShell, Excel, Word, and others.
BSides San Francisco 2022 videos: Talks from the BSides San Francisco 2022 security conference, which took place in June this year, are available on YouTube.
Google TAG history: Google has put together a nice video on how the TAG team came to be.




