Risky Biz News: Internal chats for Yanluowang ransomware gang leaked; reveal members are Russian, not Chinese
In other news: FinCEN say $1.2 billion in ransomware payments in 2021; FTC settles with Chegg for 4 data breaches in 5 years; OpenSSL vulnerabilities are bad, but not internet-ending.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The internal chat logs of the Yanluowang ransomware gang were leaked online on Halloween, revealing the group's core members, details about how they build their code, and how they deal with victims.
But more than anything, the leak reveals that despite their name and repeated claims that the gang consists of Chinese nationals, all internal chats are in "some of the most perfect Russian"—as one threat intel analyst described it to RiskyBizNews on Tuesday.
The leak appears to be the aftermath of a serious hack. Not only did the intruder gain control over the gang's internal Matrix chat server, but they also compromised Yanluowang's dark web "leak site."
They used the leak site—which is heavily monitored by law enforcement and infosec firms—to announce the hack, posting a new blog post on Monday with links to their Telegram and Twitch accounts, where links to the leaked chat logs had been posted.
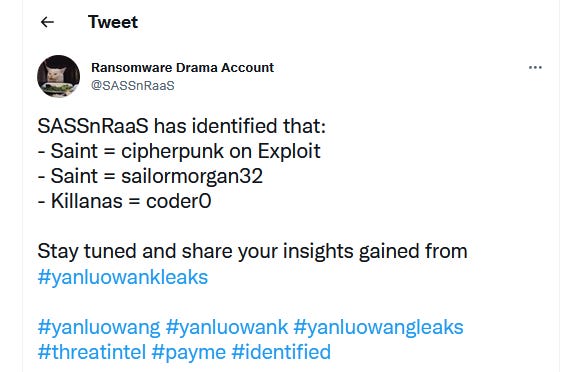
The leaked chat logs reveal several things. The first is the names of core members in charge of the Yanluowang RaaS and their identities on cybercrime forums.
The second is that the Yanluowang ransomware gang began operations in October 2021, which is around the same time Broadcom's Symantec first reported on their activities.
Third is that the gang and its members are really bad at coding, which now explains why Kaspersky researchers were able to find a vulnerability in its encryption algorithm and release a free decrypter back in April. And if that wasn't bad enough, the leaker also shared a screenshot allegedly containing the ransomware's decryption routine source code.
At the time of this newsletter, there are several theories about who the leaker is, ranging from the classics: "disgruntled former member" to "a security researcher gone rogue." The wildest theory is that the leaker is Cisco's security team, acting as payback for Yanluowang breaching its network and attempting to extort the company earlier this year. [We actually wish it was Cisco, tbh. Get slammed, ransomware gangs!!! How do you like them apples!?! etc. etc. etc.]
Nevertheless, as it happened to the Conti Leaks earlier this year, this leak effectively means the end of the Yanluowang operation, as no one in the cybercrime underground would be willing to work with the group after they've been so thoroughly hacked. OpSec is extremely important for cybercrime operators, and nobody will sign up for a RaaS that may be crawling with spooks and infosec teams on its servers.
Breaches and hacks
Dropbox phishing incident: File-sharing and file synchronization service Dropbox disclosed a minor security breach on Tuesday, revealing that a threat actor managed to compromise one of its employees through a phishing attack and gained access to one of its GitHub accounts. Dropbox said the intruder did not gain access to its core infrastructure where the files, personal data, and financial information of its users was being stored. However, Dropbox said the attackers did have access to repositories that stored API keys used by its developers and "a few thousand names and email addresses belonging to Dropbox employees, current and past customers, sales leads, and vendors."
AU DOD security incident: ForceNet, a company that provides a communications platform for the Australian military, suffered a ransomware attack last week. Responding to an ABC inquiry, officials from the Australian Department of Defense said there was no evidence to suggest that the personal data of current and former DOD personnel was stolen in the incident.
FTC settles with Chegg: The US Federal Trade Commission sued and reached a settlement with ed-tech company Chegg for its repeated failure to secure its platform and for suffering four security breaches over the span of the last five years. The proposed FTC settlement requires Chegg to limit the data it collects from users, offer users access to the data the company collected about them, honor data deletion requests, and implement multi-factor authentication for both customers and employees.
Air NZ cred-stuffing attack: Air New Zealand said that several customer accounts were compromised following a credentials-stuffing attack the airline faced last week. [Additional coverage in Stuff]
General tech and privacy
Cisco disables Meraki networks in Russia: US networking equipment vendor Cisco allegedly disabled WiFi networks managed through its Meraki service in Russia. According to multiple online reports, the company failed to give customers any warning and just renamed all networks in Russia as "12345-Sanctions."
Government, politics, and policy
UK NCSC annual review: The UK GCHQ National Cyber Security Centre has published its annual cybersecurity year-in-review report. To cut the chase short, here are the main takeaways:
- In 2022, the NCSC managed the response to hundreds of incidents, 63 of which were nationally significant.
- In 2022, 18 ransomware incidents required a nationally coordinated response.
- The most significant threat facing citizens and small businesses continued to be from cybercrime, such as phishing, hacking of social media accounts remained an issue.
- The Chinese Government's cyber capabilities continued to develop. Beijing's activity has become ever more sophisticated, with the state increasingly targeting third-party technology and service supply chains, as well as exploiting software vulnerabilities.
New CISA guidance: The US Cybersecurity Infrastructure and Security Agency has released guidance urging organizations and federal agencies to roll out phishing-resistant multi-factor authentication (MFA) [PDF] and number-matching protections if they use mobile push-notification-based MFA [PDF].
Spyware inquiry: The EU's PEGA commission will visit Cyprus and Greece this week to investigate the use of spyware by the local governments.
Ransomware summit: The White House is hosting this week the second edition of the International Counter Ransomware Summit, a two-day event where members from more than three-dozen countries and a dozen private sector companies will be discussing ways to address the current threat posed by ransomware gangs. [Additional coverage in the AP and a recorded live stream of the conference is embedded below.]
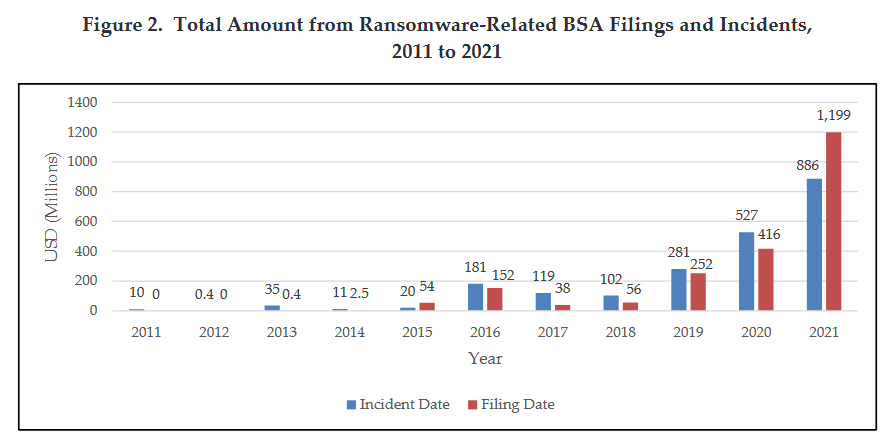
US Treasury ransomware stats: On the day of the International Counter Ransomware Summit, the Financial Crimes Enforcement Network (FinCEN) unit, part of the US Treasury Department, published statistics [PDF] on ransomware-related events reported by banks and other financial institutions through Bank Secrecy Act (BSA). FinCEN said that in 2021, filings related to suspected ransomware payment "substantially increased from 2020," amassing to almost $1.2 billion. The agency estimates that roughly 75% of these payments were made to ransomware gangs located in Russia.
Sponsor section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year, in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
Cybercrime and threat intel
Vastaamo hacker: Finnish authorities have "arrested in absentia" and issued a European arrest warrant in the name of a 25-year-old Finnish citizen on suspicion of orchestrating the hack of the Vastaamo Psychotherapy Center. The Vastaamo incident, considered one of the worst in the country's history, took place in 2018 when a hacker stole the personal medical records of the clinic's patients and attempted to extort the healthcare provider. To put pressure on the company, the hacker leaked some of the medical files on the dark web. When that failed, the hacker sent smaller ransom demands to more than 30,000 of the clinic's patients, asking for €200 and threatening to publish their medical records. (via DataBreaches.net)
PayPal bug exploited: Forcepoint researchers said they identified a bug in the PayPal service that allows phishing gangs to send legitimate PayPal invoices for non-existent products/services. The company says that PayPal has yet to respond to its report.
Phishing kit stats: In its quarterly DNS threat report, Akamai researchers said they tracked 299 unique phishing toolkits being used in attacks in the wild in the third quarter of 2022. In addition, the company also reported that 14% of customer devices contacted a malicious domain and that DNS-over-TLS adoption rose by 40% from the previous quarter.
IAB quarterly report: In its quarterly report for Q3 2022 [PDF], threat intel firm KELA said it observed initial access brokers selling access to more than 570 corporate networks over the past quarter, with a cumulative requested price of around $4 million.
"The average price for access was around USD 2800 and the median price — USD 1350. In Q3 actors offered more expensive listings since the total number of listings remained almost the same. On average, there were around 190 access listings in each month of Q3, lightly higher than in Q2."
Azov wiper: Several security researchers have spotted a new destructive data-wiping malware strain being deployed on computers across the world in limited numbers over the past few days. According to current evidence, the malware is deployed on computers that have been previously infected with the SmokeLoader malware. Once deployed, the malware wipes user files and leaves a ransom note behind, trying to pose as an attack by the Azov ransomware. The ransom note claims the ransomware was developed by Polish malware researcher Aleksandra "hasherezade" Doniec in an attempt to bring attention to Russia's invasion of Ukraine, which is obviously a ruse meant to disguise its true origin and destructive actions.
To whomever it concerns: I am NOT in any ways affiliated with Azov (or any other #ransomware). It’s a common practice among cyber criminals to try to frame security researchers.
— hasherezade (@hasherezade) 10:42 AM ∙ Oct 30, 2022
Malware technical reports
New malware from the same app dev: Malwarebytes researchers said they found four Android applications developed by the "Mobile apps Group" that were infected with versions of the HiddenAds malware. The finding is significant because Malwarebytes said the same developer published similar apps in the past, infected with an older version of the HiddenAds malware, but his account wasn't banned, allowing them to publish new apps in the meantime.
Pegasus spyware: Part three of a technical analysis of the Pegasus spyware is now live. Parts one and two are here.
APTs and cyber-espionage
APT10: Kaspersky published two reports on Monday on LODEINFO, a backdoor part of the arsenal of the APT10 Chinese cyber-espionage group.
APT trends report: Kaspersky has also published its quarterly APT threat and trends report, widely regarded as one of the most comprehensive in the industry. Now, for the first time, in a video version as well.
Vulnerabilities and bug bounty
OpenSSL bug not a big deal: The OpenSSL project published a security update on Tuesday to fix two vulnerabilities tracked as CVE-2022-3786 and CVE-2022-3602, touted last week as the first "critical"-level vulnerabilities the project was patching in the last six years. But as the OpenSSL project explained in a blog post, the vulnerabilities were not as dangerous as everyone was led to believe last week, and the two had their severity rating downgraded to "high." While not as widespread as initially feared, users are still advised to patch both issues. For defenders, the Dutch NCSC maintains a list of software vulnerable to this vulnerability, and researcher Marcus Hutchins published scripts for scanning your network/software and checking to see if it's affected.
Apache Batik vulnerability: Details and a PoC are available for an SSRF-to-RCE vulnerability in Apache Batik, a Java library for working with SVG images. The vulnerability is tracked as CVE-2022-40146.
Checkmk vulnerabilities: SonarSource researchers have published details on several vulnerabilities in Checkmk, a tool and service for IT infrastructure monitoring.
CosMiss vulnerability: Microsoft rolled out fixes for an authentication bypass vulnerability in Jupyter Notebooks for Azure Cosmos DB, reported by Orca Security. The company calls the vulnerability CosMiss. Microsoft said no customers were impacted by this vulnerability, and no action is required from them to apply the patch.
Impersonate attack: Orange's SensePost team published details about a new way to compromise Windows domains by abusing access tokens. The token exploit mechanism does not rely on LSASS, meaning it can bypass many EDR solutions. The code for this attack is available on GitHub.
Infosec industry
TLP 2.0 enters into effect: CISA has begun formally using the new TLP 2.0 protocol, announced earlier this year.
No Hat 2022 videos: Talks from the No Hat 2022 security conference, which took place two weeks ago, are available on YouTube.
Some very sad news: Vitali Kremez, the CEO of AdvIntel, has been reported missing at sea following a scuba diving trip on Sunday. A US Coast Guard search is still underway.
#SearchAndRescue @USCG crews are searching for 36-year-old Vitali Kremez, last seen wearing a black wetsuit and scuba tank while diving near #HollywoodBeach, Florida.
— USCGSoutheast (@USCGSoutheast) 8:39 PM ∙ Oct 30, 2022
Anyone with information is asked to call Sector Miami at (305) 535-4472.




