Risky Biz News: Intel and Arm processors open themselves to timing attacks
In other news: FBI hacks Hive ransomware infrastructure; Yandex source code leaked online; Google disrupts major Chinese influence operation.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Modern Intel and Arm CPUs expose cryptographic data to timing attacks, Eric Biggers, a software engineer at Google on the Platform Encryption Team, has highlighted in a series of discussions on mailing lists for the past months.
Timing attacks against cryptography algorithms were discovered in the mid-90s and were proven practically at the start of the 2000s. Researchers proved that by measuring the time it takes for a CPU to process data, they could infer private information, such as an RSA private key. To prevent timing attacks, constant-time code capabilities were added to CPUs so the time needed to perform an operation would be relatively constant and independent from the value of the data handled inside the processor.
But Biggers says that for the past few years, both Intel and Arm have disabled by default features in their CPUs that enforce constant-time operations, namely DIT on Arm and DOITM on Intel.
Biggers says the upcoming 6.2 version of the Linux kernel will re-enable DIT inside Arm CPUs, but only for kernel-level code.
"Without any additional patches, userspace code will still get data-dependent timing by default," Biggers says, while no patch is currently scheduled to re-enable DOITM on Intel CPUs at all.
"Thus, as-is, it's not really possible to safely execute cryptographic algorithms on Linux systems that use an Intel processor with Ice Lake or later," Biggers says.
The issue appears to be a disaster waiting to happen, especially as more Arm and Intel CPUs are being shipped worldwide without what any cryptography expert would consider a must-have security feature.
"Constant-time code is super important in crypto to avoid timing attacks," Jean-Philippe Aumasson, cryptographer and co-founder & chief security officer at Taurus, a digital assets platform for the banking sector, told Risky Business News.
"It's definitely a potential major issue, but I've yet to see an attack PoC that could be exploited in real applications," Aumasson says.
Nevertheless, while attacks have not been spotted in the wild as of yet, research exploring timing attacks has continued over the past two decades, exploring new ways to carry them out. The latest example is new research published last year on a timing attack named Hertzbleed that can be carried out remotely and impacts all AMD and Intel CPUs on the market.
Breaches and hacks
Duolingo breach: A threat actor claims to have collected data on more than 2.6 million Duolingo users by exploiting an exposed application programming interface (API). The hacker is selling the data for $1,500 on a popular underground cybercrime forum. Duolingo said it is investigating the incident. [See coverage in The Record]
US federal agencies breached: The US Cybersecurity and Infrastructure Security Agency (CISA) says that two federal civilian agencies were hacked last year after employees were tricked into downloading legitimate remote access software onto their work computers. Despite gaining access to federal networks, the intruders didn't go after government data and instead focused on performing a refund scam to steal money from the employee's personal bank accounts. CISA says the intrusions appear to be part of a financially motivated phishing campaign that has been going on for months and was previously analyzed by cybersecurity firm SilentPush. The campaign uses various themes to trick victims into installing legitimate remote monitoring and management (RMM) software on their systems, through which the threat actors modify a victim's bank account statements to show extra funds that they want "refunded." CISA has a technical write-up on the whole thing.
South Korean intrusions: South Korea's cybersecurity agency says that a Chinese hacking group named the Cyber Security Team has launched cyberattacks against South Korean academic institutions. The hackers claimed to have breached more than 70 organizations around the Lunar New Year holiday that took place over the last weekend. The group says it plans to release more than 54 GB of data from the hacked institutions. KISA officials confirmed the attacks but said that only 12 educational institutions suffered breaches. [Additional coverage via the Yonhap News Agency]
Digg founder hacked: Digg founder and crypto enthusiast Kevin Rose has fallen victim to a phishing attack and signed a malicious transaction that has allowed a hacker to steal more than 40 NFTs. The stolen assets were worth $2 million on Wednesday, $1.4 million on early Thursday, and just $1 million by the afternoon. What a spectacularly stable financial ecosystem you have there, crypto-bros!
Yandex source code leaks: Some of the source code of Yandex, a Russian search engine and IT software giant, was leaked on the Breached cybercrime forum. The leak appears to be authentic, according to different sources. Yandex said the source code was leaked by a former employee. The code contains the source for most major Yandex services, such as Search, Maps, Taxi, Mail, Market, Travel, Cloud, Pay, and many more. Several hardcoded credentials for various cloud servers were also exposed in the leak. All leaked files are dated February 24, 2022, the date of Russia's invasion of Ukraine.
ADS-B Exchange attacks: ADS-B Exchange, the website that tracks international flights and the service behind the Elon Musk Tracker, has been the target of DDoS attacks this week.
General tech and privacy
US sues Google for ad market monopoly: The US Department of Justice has filed an antitrust lawsuit against Google for abusing its position in the online advertising market. The DOJ says Google has amassed a monopoly and is seeking the breakup of the company's online ad business. Officials said Google had used anticompetitive, exclusionary, and unlawful actions to eliminate or severely diminish competitors and make huge profits for itself.
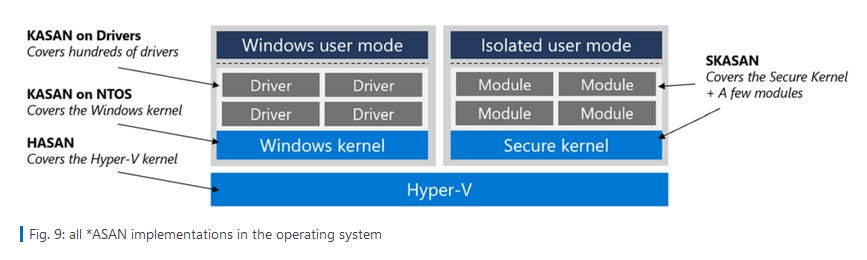
Kernel sanitizers in Windows: Microsoft has published a description for its KASAN, SKASAN, and HASAN kernel sanitizer modules that are currently shipping with Windows 11 installations. Kernel sanitizers are used to detect memory errors for kernel components running on Windows 11.
Government, politics, and policy
Killnet DDoS attacks (yawn): Following Germany's decision to deliver Leopard 2 tanks to Ukraine, disguised intelligence operation "hacktivist group" Killnet launched DDoS attacks against German government websites and called it a great victory on their Telegram channel. Nobody cares about two-hour outages, Killnet. Give it a rest! Also, it's never Russia until Russia denies it.
CISA K12 resource: CISA has published a report to help K-12 institutions assess and protect their networks against cybersecurity threats.
NIST AI guidance: US NIST released its AI Risk Management Framework along with a companion playbook, explainer video, and an AI RMF Roadmap for organizations looking into working with AI toolsets.
Poland's Artemis: CERT-PL has published details about Artemis, a system that scans the Polish internet for common vulnerabilities and configuration errors and then notifies resource owners. So far, since January 2 this year, the system has scanned close to 2000 domains and subdomains of local governments and identified hundreds of websites running outdated software.
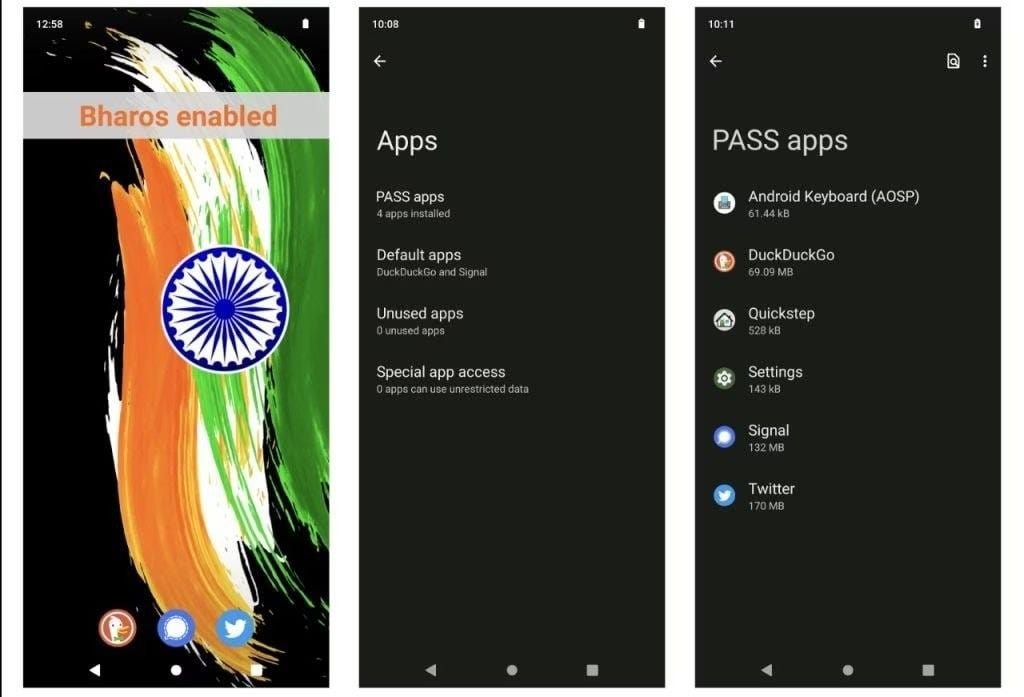
India launches BharOS: The Indian government has demoed the first version of its homegrown mobile operating system, a project called BharOS. The operating system was developed by the Indian Institute of Technology in Madras with funding from the Ministry of Education and the Ministry of Telecommunications and Information Technology. Under the hood, BharOS is a modified version of Android that comes with no preloaded apps, doesn't track and share user data, and supports private app stores. Officials said the OS was designed for the Indian government and private sector as an alternative to Android and iOS. At a press conference, officials also claimed the OS is incapable of running malware, but we'll see about that when the OS is formally released. Usually, these types of braggadocio claims don't tend to live up to reality.
Sponsor section
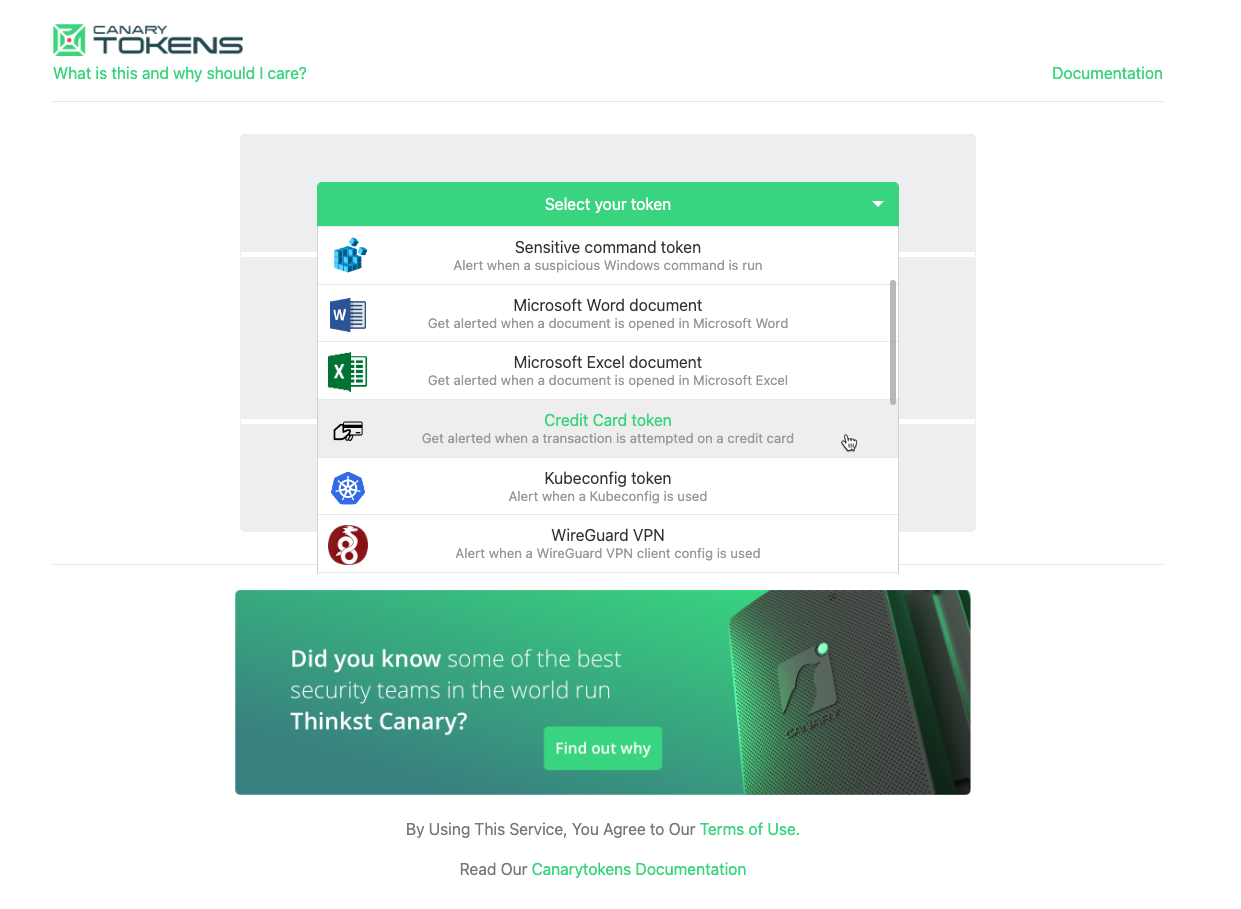
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. The company has recently released a new type of canary token that's basically a real and valid payment card number. Companies can store the token in one of their systems, and Thinkst will alert them when the card (token) is used somewhere in the real world; alerts that companies can use to investigate possible breaches of their financial data storage systems.
Cybercrime and threat intel
Dutch hacker detained for selling Austrian citizens' data: Austrian police announced that a hacker who was selling the data of more than 9 million Austrians in 2020 on an underground hacking forum was detained by Dutch authorities in November of last year. Officials said the suspect was a member of the now-defunct RaidForum, where he used the nickname "DataBox" to sell hacked data from a variety of victims. Dutch officials are also investigating the suspect for "dozens of other illegal activities on the Internet."
Dutch cybercriminals detained: Dutch authorities have arrested a 22-year-old man and a 20-year-old woman from the municipality of Westerkwartier on fraud charges. Dutch police say the duo called victims posing as bank employees, convinced them to install the AnyDesk remote access software, and later accessed their bank accounts. Officials say the duo stole more than €150,000 from their victims.
RSOCKS admin pleads guilty: Denis Emelyantsev, a Russian national and the administrator of the RSOCKS proxy-for-hire service, has pleaded guilty in a US court. Emelyantsev was detained while on vacation in Bulgaria in May 2022, two weeks before authorities orchestrated a takedown of his botnet. He was extradited to the US late last year.
ShinyHunters suspect extradited to the US: Moroccan officials have extradited Sebastien Raoult, a French national, to the US to face charges in a hacking investigation. Raoult was detained last year on suspicion of being part of the ShinyHunters hacking group. He was arraigned in court on Thursday. Indictment available via the DOJ press release, here.
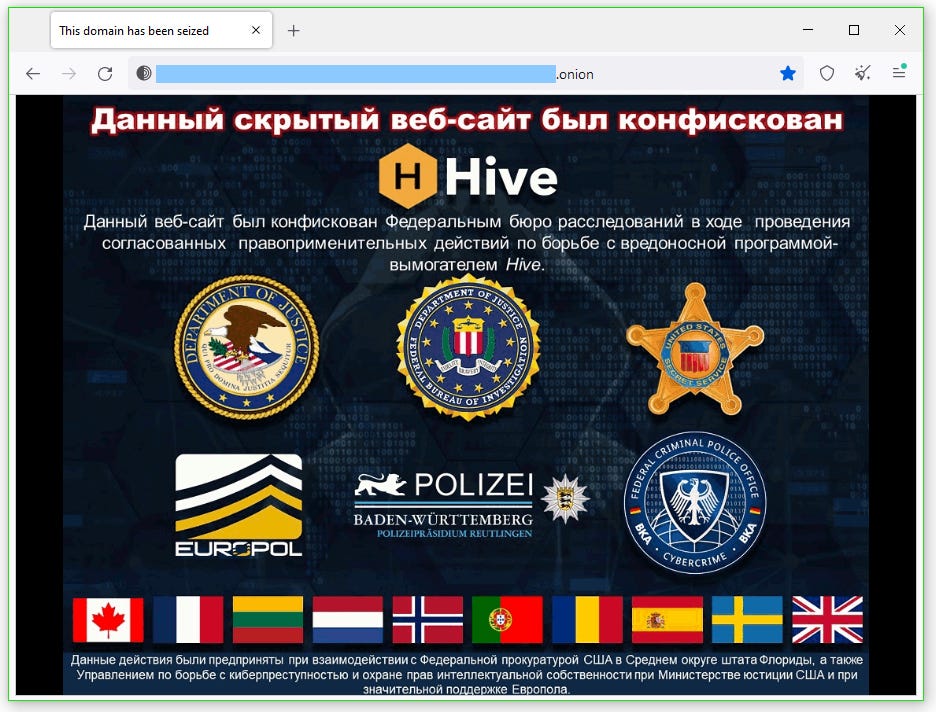
Hive ransomware seizure: Law enforcement agencies from the US and EU have seized servers and websites operated by the Hive ransomware gang. The US Department of Justice says the FBI secretly breached the Hive gang's infrastructure in July 2022, from where agents retrieved more than 1,300 decryption keys over the past seven months. Of these, the FBI distributed 1,000 decryption keys to past Hive victims but also shared in real-time more than 300 new decryption keys to companies that had computers encrypted in ongoing Hive attacks last year. Officials say they prevented ransomware payments estimated at roughly $130 million, but they also notified many other companies when their networks were breached, even before Hive and its affiliates had a chance to deploy their ransomware and encrypt their data. Since June 2021, when the Hive gang launched its operation, the group is believed to have made more than $100 million from ransom payments. (h/t Dominic Alvieri)
Criminal money laundering: Blockchain analysis company Chainalysis says that 67.9% of the $23.8 billion worth of cryptocurrency linked to illicit addresses last year has passed and been laundered through one of five major cryptocurrency exchanges. In an exclusive with Wired, Chainalysis declined to name the five exchanges.
npm spam: A threat actor going by the name of Zalastax has uploaded more than 20,000 JavaScript libraries to the npm package repository. None of the scripts contain malicious code, but the sheer volume of the automated attack has flooded the repository with garbage content. Mend security researchers Tamir Ben Ari and Tom Abai say they reached out to the individual behind the attack, who said the package spam was a "silly project with no purpose and done out of curiosity."
Black hat SEO botnet: Sucuri has a write-up on a botnet specialized in hacking WordPress sites and then using them to improve the SEO/SERP ranking of malicious sites or redirect traffic to phishing and malware-laden websites. The botnet appears to hold thousands of infected sites under its grasp.
Kronos in Mexico: In a security alert this week, IBM's X-Force team said it saw new attacks with the Kronos banking trojan targeting Mexican users.
Sunlogin exploitation: South Korean security firm ASEC says it spotted a threat actor exploiting RCEs in Sunlogin, a Chinese remote access software suite, to gain access to corporate networks and deploy Gh0stRAT or cryptomining malware. [Later update: The original write-up is now also available in English]
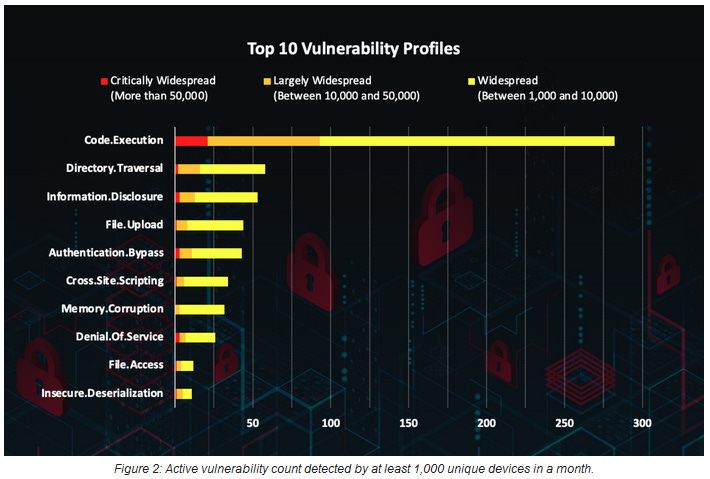
Fortinet threat report: Fortinet published its yearly exploitation report for the past year. The company noticed several vulnerability exploitation "outbreaks" last year and said the vast majority of exploit attempts it spotted last year tried to go after "code execution" vulnerabilities.
Malware technical reports
Black Basta ransomware: Quadrant Security has a technical analysis on the Black Basta ransomware, which the company said it recently dealt with after it hit one of its customers, a large, regional energy outfit based in the southeastern United States.
PY#RATION: Securonix researchers have put out a report on PY#RATION, a new Python-based remote access trojan that has been spotted distributed in the wild since August last year.
CryptBot: ANY.RUN has a breakdown of CryptBot, an infostealer that has been active since 2019.
Mimic ransomware: Trend Micro researchers have published a technical report on the new Mimic ransomware, which appears to be abusing Everything APIs for improved encryption speed. Everything is a Windows filename search engine developed by Voidtools that offers quick searching and real-time updates for minimal resource usage. Trend Micro said it first observed this ransomware in the wild in June 2022 and that the ransomware has targeted both Russian and English-speaking users.
APTs and cyber-espionage
TA444: Cybersecurity firm Proofpoint says that a North Korean APT group it tracks as TA444 has been closely following the cybercrime landscape and has often implemented the latest malware distribution methods as soon as run-of-the-mill operations would adopt them. Throughout the past year, Proofpoint says it has seen TA444 abuse tricks such as Office files with malicious remote templates, LNK shortcut files, ISO and MSI files, compressed HTML code, and virtual hard drives to install malware on their targets' systems. All of these are techniques that were popularized by financially-motivated cybercrime groups, but TA444 was quick to borrow from their arsenals. This behavior goes against the grain when it comes to the threat landscape, as it's usually the low-level cybercrime groups that adopt techniques from the more advanced APT operations. Proofpoint says TA444 activity overlaps with public activity called APT38, Bluenoroff, and Stardust Chollima and that the group is very likely tasked with generating revenue for the North Korean government.
Abraham's Ax: Last year in November, a new hacktivist group named Abraham's Ax appeared online, claiming to operate on behalf of the Lebanese Hezbollah group. The group leaked data and phone conversations from Saudi Arabian officials in response to the country's increasing diplomatic relations with Israel. But in a report this week, Secureworks says they found ties between this group and Moses' Staff, an anti-Israeli and pro-Palestinian hacktivist group that has been linked to the Iranian government. Secureworks says that both groups appear to be operated by an Iranian threat actor the company is tracking as COBALT SAPLING.
PlugX variant: Palo Alto Network's Unit42 says it discovered a version of PlugX that can infect and spread via USB devices. PlugX is remote access trojan that was developed and initially used by Chinese cyber-espionage groups but has since leaked and been adopted by many Chinese threat actors as well.
"This PlugX malware also hides actor files in a USB device using a novel technique that works even on the most recent Windows operating systems (OS) at the time of writing this post. This means the malicious files can only be viewed on a Unix-like (*nix) OS or by mounting the USB device in a forensic tool."
NCSC cyber-espionage warning: The UK's National Cyber Security Centre has issued a warning over spear-phishing campaigns carried out by threat actors based in Russia and Iran. Groups like the Russia-based SEABORGIUM (Callisto Group/TA446/COLD RIVER/TAG-53) and Iran-based TA453 (APT42/Charming Kitten/Yellow Garuda/ITG18) targeted UK organizations in 2022, and operations are still ongoing. The NCSC says targets at risk include academia, NGOs, think tanks, defense and government organizations, as well as politicians, journalists, and activists. In a technical document, the NCSC says these operations are not your typical delivery of malicious documents via email. Instead, the threat actors contact victims via benign topics, establish a personal rapport, and only after they've earned the victim's trust try to lure them to phishing sites or into installing malicious apps.
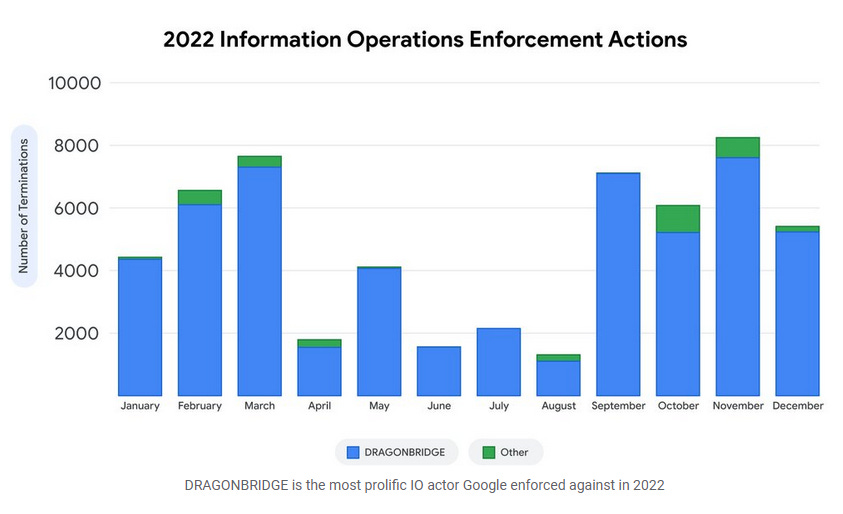
Chinese influence op DragonBridge: Google said it has taken down more than 50,000 accounts on YouTube, Blogger, and AdSense, linked to a Chinese influence operation the company calls DRAGONBRIDGE. Also known as "Spamouflage Dragon," the group has been active since 2020 and has also operated influence bot networks on Twitter and Facebook as well. Since 2020, Google said it removed more than 100,000 accounts from its networks and that in 2022, DRAGONBRIDGE was by far the largest influence operations (IO) threat group. However, despite this, most of their accounts had almost no real engagement from real users.
"Despite their scale and profuse content production, DRAGONBRIDGE achieved practically no organic engagement from real viewers — in 2022, the majority of DRAGONBRIDGE channels had 0 subscribers when Google disrupted them, and over 80% of DRAGONBRIDGE videos had fewer than 100 views. Engagement for DRAGONBRIDGE's blogs on Blogger was also low, with nearly 95% receiving 10 or fewer views for blogs terminated in December."
Vulnerabilities and bug bounty
CVE-2022-34689 (Windows Crypto API): Akamai researchers have published a write-up and a PoC for CVE-2022-34689, a vulnerability in the Windows CryptoAPI that can be exploited in offline mode to spoof x.509 certificates and allow threat actors to authenticate or sign code as their target. The vulnerability was found and reported to Microsoft last year by the US NSA and UK NCSC and was patched in the October 2022 Patch Tuesday.
Exchange exploits: Bitdefender researchers have a summary of the recent exploits and attacks against Microsoft Exchange email servers, such as ProxyShell, ProxyNotShell, and OWASSRF.
MyBB RCE: Positive Technologies have a write-up on two MyBB vulnerabilities that can be chained to achieve RCE and take over MyBB <= 1.8.31 forums.
Infosec industry
New tool—containerdbg: Google has open-sourced a new tool called containerdbg, an all-in-one command-line tool to help debug Kubernetes containers with common issues that arise when moving to containers as part of legacy application modernization.
Tenable fund: Vulnerability management platform Tenable has announced a $25 million fund to invest in early startups launching in the vulnerability exposure and management space.
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




