Risky Biz News: Hardware backdoors found in Chinese key cards
In other news: US House wants TP-Link investigated as a national security threat; major RCE bug discovered in OpenBMC; OpenAI takes down Iranian influence op.

This newsletter is brought to you by enterprise browser maker Island. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

A security researcher has discovered secret hardware backdoors in RFID key cards manufactured by a major Chinese company.
The backdoors can allow threat actors to clone affected smart cards within minutes and access secure areas.
They impact smart cards manufactured by Chinese company Shanghai Fudan Microelectronics that were built using MIFARE Classic chips from NXP.
The chips have been on the market since 1994 and have been widely used over the past decades to create smart key cards and access badges in hotels, banks, government buildings, factories, and many other places.
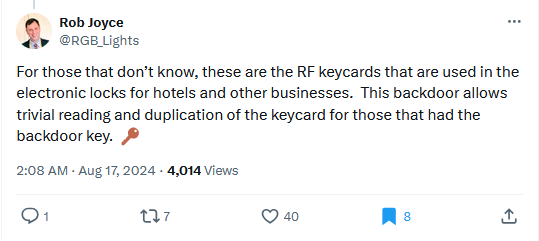
Because they've been on the market for so long, they also have not escaped the prying eyes of the cybersecurity community, which has found several ways to break their encryption and clone MIRAGE-based cards—such as the Darkside, Nested Authentication, Hardnested, or the Static Nested attacks.
Over the years, vendors have developed improved versions of their smart cards that shipped with various improvements designed to boost security and prevent some of the discovered attacks.
Two of the most popular card designs are the FM11RF08 and FM11RF08S variants—where the S stands for "Security improved version."
But in a paper published last week, Quarkslab's Philippe Teuwen says that while researching FM11RF08S cards, he found what proved to be a secret backdoor baked inside Fudan cards.
He discovered the backdoor while fuzzing the card's command sets and noticed that the card was answering to undocumented instructions on a specific range.
"Apparently, all FM11RF08S implement a backdoor authentication command with a unique key for the entire production. And we broke it."
For Fudan FM11RF08S cards, that key was A396EFA4E24F.
Taking his research further, he also found a similar universal backdoor authentication key for the older FM11RF08 cards, which was A31667A8CEC1.
This one also impacted many other Fudan card models, such as the FM11RF32 and FM1208-10. It also impacted card models from Infineon and NXP, suggesting these companies had likely licensed card technology from the Chinese company.
According to Teuwen, the backdoor seems to go back as far as 2007, meaning that many access key cards distributed over the past 17 years can likely be cloned with physical access within seconds.
As it was pointed out in a previous paragraph, RF access cards based on MIFARE Classic were already considered insecure for a long time, but that was due to design errors and not a backdoor. Attackers would still have to waste minutes and physical resources to crack and dump a card's data in order to clone access keys configured on it.
An intentional backdoor puts these cards into a whole new threat matrix cell.
Breaches, hacks, and security incidents
Unicoin hack: A threat actor has gained access to the Google Workspace of cryptocurrency platform Unicoin and changed the passwords of all of its employees. The intrusion took place on August 9 and Unicoin says it was able to remove the hacker from its systems four days later on the 13th. Following the hack, Unicoin says it also discovered additional incidents in its environment, such as hacked accounts for some managers and a contractor who was using a forged identity. The company says no customer funds were stolen following the breach. [Additional coverage in The Record]
Trackimo hack: A hacker going by the name of Maia Arson Crimew says they gained access to the backend of GPS tracker vendor Trackimo. Crimew says the company's backend tool, named the Trackimo Troubleshooter, was using a simple password that was easy to guess. The tool contained debug information from all of the company's GPS devices, including information like customer names, emails, passwords, GPS coordinates, battery levels, and uptime information. Trackimo secured the system after Crimew's report.
Promises2Kids ransomware attack: After hitting Synnovis and crippling NHS operations and blood donations for months in the UK, the Qilin ransomware group has claimed an attack on Promises2Kids, a non-profit involved in child fostering in South California. Where's a Tomahawk missile when you need one! [h/t PogoWasRight]
Change Healthcare ransomware attack: TechCrunch's Zack Whittaker has published a timeline of the ransomware attack that hit Change Healthcare earlier this year.
FlightAware leak: Flight tracking service FlightAware has confirmed a security breach that exposed the data of all its customers. The company blamed the incident on a misconfigured server. The exposed data included all user data, ranging from real names and emails to passwords and billing information. [Additional coverage in LoyaltyLobby]
NPD leak: Troy Hunt and Brian Krebs have published some in-depth looks at the massive trove of data hacked and leaked from data broker National Public Data. Per Krebs, the data was stolen in December of last year by a hacker known as SXUL and then sold and re-sold several times before it was leaked for free on hacking forums last month. Per Hunt, the data contains over 3 billion records with data on more than 133 million individuals. NPD has also confirmed the hack itself.
Monobank DDoS attack: A two-day-long DDoS attack has taken down Monobank, Ukraine's largest direct bank. [Additional coverage in the Kyiv Independent]
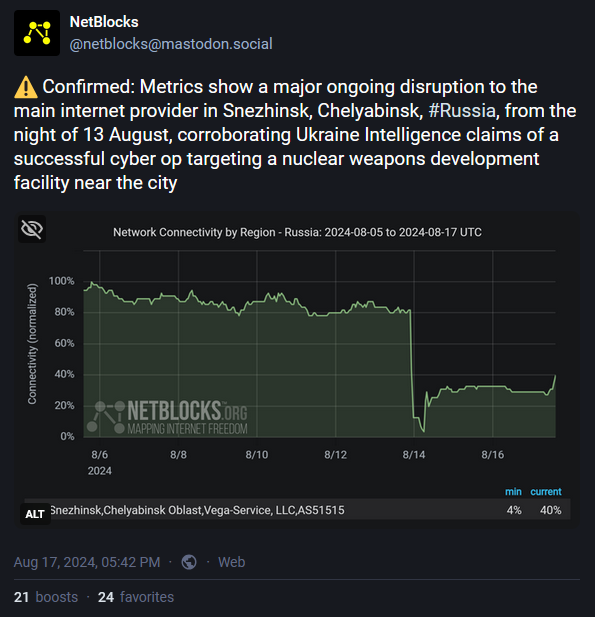
Vega hack: Ukraine's military intelligence agency GUR says it conducted an offensive cyber operation against a Russian organization involved in Russia's nuclear weapons program. The agency says the attack was conducted together with a hacktivist group named the BO Team and targeted the All-Russian Scientific Research Institute of Technical Physics (VNIITF) in Snezhinsk, Chelyabinsk. The GUR says it stole data on the institute's employees, nuclear plant, and sanctions evasion tactics. Officials say they also wiped 10 servers and more than 1,100 switches from Vega, the institute's internet service provider. According to NetBlocks, the attack also left a large part of the Snezhinsk city without internet access. Snezhinsk is one of Russia's ten infamous "nuclear cities"—cities dedicated to nuclear research that had no formal name and were not listed on any map.
General tech and privacy
Twitter pulls out of Brazil: Twitter has closed its Brazil offices after the company refused to comply with a judge's order to remove abusive content from its network. [Additional coverage in Reuters]
TikTok algorithm study: A study from the Network Contagion Research Institute (NCRI) at Rutgers has found that users are more likely to have a pro-CCP view on sensitive China topics the more time they spend on TikTok. The NCRI credits this to the large influx of pro-CCP creators on the platform. It's an interesting study of TikTok's algorithm that doesn't shine well on the company.
Google Search monopoly in action: Google will delist websites from its search index if they block the company's AI scraping bot. [Additional coverage in Bloomberg]
Keep ad blockers on Chrome: There's a trick to keep uBlock Origin and the old (efficient) ad blockers working in Chrome one extra year after the Manifest V2 deadline this fall.
Windows Sandbox updates: Microsoft is adding new features to its Windows Sandbox technology, such as runtime clipboard redirection, audio/video input control, and the ability to share folders with the host at runtime.
Government, politics, and policy
House asks for investigation into Chinese WiFi routers: The US House Committee on CCP has asked the Commerce Department to investigate Chinese WiFi router maker TP-Link. Officials say the proliferation of the company's routers in the US is creating a potential national security risk. The Committee says the high number of vulnerabilities in TP-Link products could allow state-sponsored hackers to easily breach US infrastructure. Officials also cited China's draconian national security laws that could also force TP-Link to hand over data on US citizens to the Chinese state. The Committee's warning comes after CISA and many cybersecurity firms warned that Chinese state-sponsored hackers are using botnets made of home routers to hide operations against US and Western targets.
Ransomware incidents during the election: The FBI published a public service announcement last week reiterating that even if there are disruptions to the US election infrastructure during the voting period this fall, the vote itself is safe and will take place regardless.
"Any successful ransomware attack on election infrastructure tracked by FBI and CISA has remained localized and successfully managed with minimal disruption to election operations and no impact on the security and accuracy of ballot casting or tabulation processes or systems."
BKA's legal powers: Writing for Binding Hook, ECCRI researcher Jakob Bund looks at how Germany's BKA has re-interpreted the search-and-seize local legislation to find a way to go after cybercrime infrastructure.
UK Cyber Resilience Audit: The UK NCSC is working on a scheme called the Cyber Resilience Audit that will let private organizations join regulatory and certification bodies and receive the ability to conduct independent Cyber Assessment Framework (CAF)-based audits on behalf of the UK government.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Brian A. Coleman, Senior Director at Pfizer for Insider Risk, Information Security, Digital Forensics Expert. Brian goes over all the Island features that have made the browser a favorite tool to secure older corporate apps, either by blocking insecure features or adding logging capabilities where they didn't exist.

Cybercrime and threat intel
Extortionist charged: US officials have charged a New Jersey man with hacking and extorting his employer at the end of last year. According to court documents, Daniel Rhyne abused his position as core infrastructure engineer to create a secret virtual machine on his company's network. Rhyne allegedly used this VM to run automated scripts that changed the passwords of employee accounts, deleted backups, and shut down his employer's servers. He then used a new email account to demand a $750,000 ransom to be paid within a week. The FBI says it tracked the attack to Rhyne after they linked the hidden VM to one of his laptops. [h/t CourtWatch]
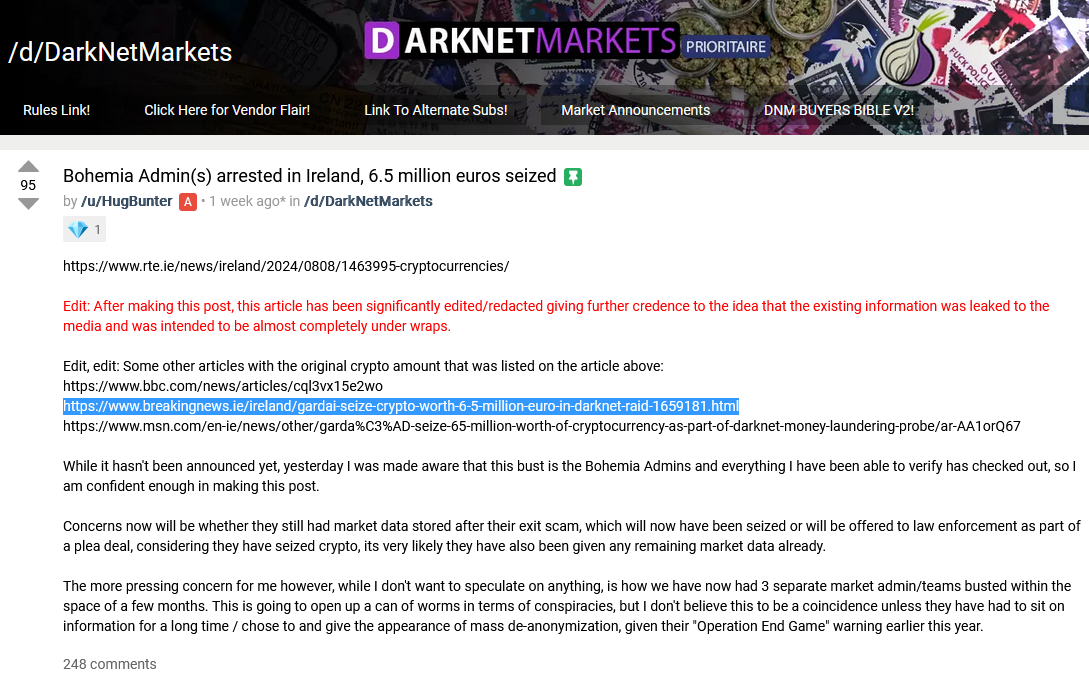
Bohemia Market admin arrested: Irish authorities have arrested a Dublin man for allegedly running the Bohemia dark web marketplace. 23-year-old Kevin Daniel Andrei has been charged with three counts of money laundering related to dark web sales. Authorities seized €6.5 million worth of cryptocurrency and two luxury cars during the arrest. Officials didn't link Andrei to any specific dark web markets, but a post on the Dread underground forum identified Andrei as the admin of the Bohemia Market, a dark web marketplace that has been operating since 2021. [Additional coverage in the BBC and BreakingNews.ie] [h/t vxdb]
Google-cloning malvertiser: Malwarebytes researchers have discovered a malvertising campaign that created malicious ads and web pages trying to pass as official Google products. The entire campaign is ridiculous and shows the inadequate level of vetting that takes place on Google's Ads platform since a threat actor ran thousands of ads mimicking Google's own brands.
Token theft attacks at MSFT: And something we missed back in June—Microsoft says it detected 147,000 token replay attacks on its platform last year, a 111% increase year-over-year over the previous year. Despite the large number, the incidents represented fewer than 5% of all identity compromises. [h/t Tal Be'ery]
DPRK crypto workers: A blockchain investigator known as ZachXBT has discovered an underground network of North Korean software developers working on dozens of cryptocurrency projects. The cell operates out of Asia and is believed to generate between $300,000 to $500,000 per month. ZachXBT has traced at least 21 workers to over 25 cryptocurrency projects. He says he found the network while helping a company recover $1.3 million worth of stolen funds. [Additional coverage in CoinTelegraph]
US seizes StreamEast domain: The US DHS has seized one of the three domains used by StreamEast, a website known for hosting sports-related pirate streams. [h/t vxdb]

Malware technical reports
Mad Liberator ransomware: Sophos has published a technical report on Mad Liberator, a new RaaS platform that launched this summer.
"Ransomware groups rise and fall constantly, and Mad Liberator may prove to be a significant new player, or just another flash in the pan. However, the social-engineering tactics the group used in the case described above are noteworthy – but they are not unique."
Brain Cipher ransomware: Group-IB looks at the Brain Cipher ransomware operation, the group that made quite the name for itself after hacking Indonesia's national data center and crippling the activity of 200+ government organizations. According to Group-IB, the group appears to be a rebrand of older ransomware operations known as RebornRansomware, EstateRansomware, and SenSayQ.
Dolphin Loader: eSentire researcher Ann Pham (RussianPanda) has published a report looking at a new MaaS that launched in July named Dolphin Loader.
D3F@ck Loader: eSentire looks at D3F@ck, another MaaS that launched this year and provides a malware-loading service similar to the aforementioned Dolphin.
Ailurophile Stealer: G Data researchers look at Ailurophile, a new infostealer spotted being distributed in the wild.
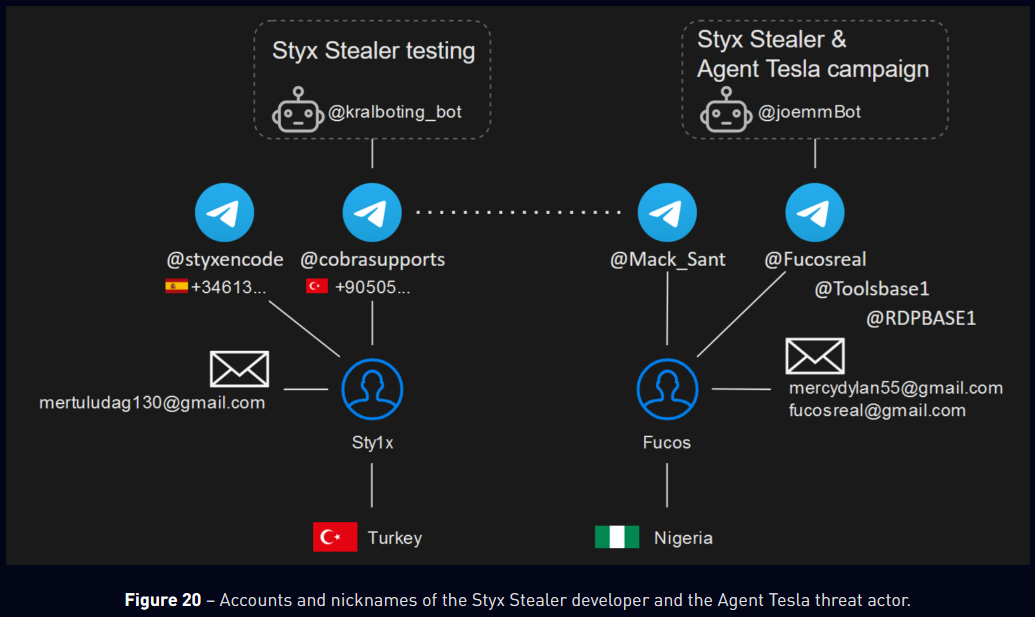
Styx Stealer: Security firm Check Point has discovered a major operational security fail in the new Styx Stealer malware that allowed its researchers to track down and unmask its author. Check Point says the developer infected their own computer, which allowed it to link the stealer to a Turkish hacker known as Sty1x. Data from Sty1x's PC included details about its personal identity but also contact information for 54 of the Styx Stealer buyers. This allowed Check Point to track down one of today's major spammers known as FucosReal to an individual in Nigeria.
Sponsor Section
Learn more about choosing the best enterprise browser for your organization. Dive into features, top vendors, and what to consider when researching.
APTs, cyber-espionage, and info-ops
Bitter: StrikeReady has published a report looking at the files it found in an open directory linked to Bitter APT operations.
BlueNoroff's TodoSwift: Kandji has published a report looking at TodoSwift, a new macOS malware strain part of the arsenal of DPRK APT group BlueNoroff.
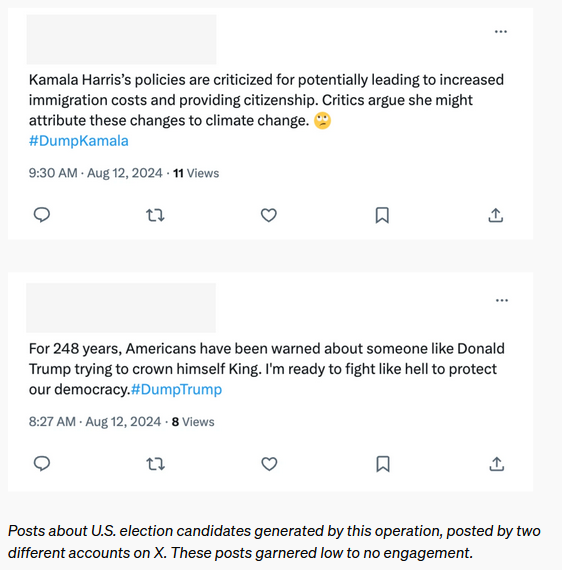
OpenAI disrupts Iranian info-op: OpenAI has taken down multiple ChatGPT accounts used by an Iranian threat actor as part of an influence operation targeted at the upcoming US presidential election. The accounts were used to generate news articles and social media posts to support both the Harris and Trump camps. OpenAI linked the accounts to a threat actor known as Storm-2035. It is one of the four groups highlighted in a recent Microsoft report [PDF] about Iran's efforts to sway the US elections. Besides the US election, the group also posted content about the Israel-Palestine war, the Paris Olympics, Scottish independence, and Venezuelan politics.
Vulnerabilities, security research, and bug bounty
GlobalPlatform API vulnerability: A team of academics has discovered a series of design weaknesses in the GlobalPlatform Internal Core, an API that provides compatibility between different Trusted Execution Environments (TTEs). These weaknesses can be used to exploit memory bugs via Trusted Applications (TAs) and take control of the underlying TTEs. The research team said they found 14 vulnerabilities using a special tool they created, 10 of which are still in the process of being patched. All in all, the vulnerabilities affect mobile devices currently in use by billions of users.
NetSuite vulnerabilities: AppOmni researchers have identified a misconfiguration in NetSuite's SuiteCommerce platform that can leak sensitive data.
MSI SMM vulnerability: A security researcher has found a critical vulnerability (CVE-2024-36877) in MSI's System Management Mode (SMM) driver that can allow threat actors to execute code and install bootkits on affected systems. A write-up and PoC are now available after MSI has patched the issue in June.
OpenBMC vulnerability: Tetrel Security has discovered a critical vulnerability in OpenBMC, an open-source firmware for baseboard management controllers. Tracked as CVE-2024-41660, the vulnerability resides in the Service Location Protocol server that is preinstalled with all OpenBMC images. Tetrel says a memory corruption bug in the SLP server allows remote unauthenticated attackers to run malicious code on internet- or network-accessible BMCs. The attack is simple to execute and only requires sending malicious SLP packets to a BMC's port 427. The vulnerability received a severity rating of 9.8/10 and was patched at the end of July.
Infosec industry
New tool—AWS Mine: ScaleSec's Steven Smiley has released AWS Mine, a honey token manager for AWS infrastructure.
New tool—SCCMSecrets: Synatcktiv has open-sourced SCCMSecrets, a tool for exploiting SCCM policies distribution for credentials harvesting, initial access, and lateral movement.
New tool—Ransomware Tool Matrix: Equinix researcher William Thomas has released the Ransomware Tool Matrix, a repository with information on what tools each ransomware gang or extortionist gang uses in attacks.
New project—OxA11C: SentinelOne and Intezer have co-launched a new project named OxA11C aimed at bringing infosec people together to create better ways to reverse engineer Rust-based malware.
Take Command videos: Talks from Take Command, a cybersecurity summit from AWS and Rapid7 that took place in May, are now available on the conference's website.
Black Hat and DEF CON recap: Infosec news outlet The Readable has probably the best, longest, and most accurate recap of the recently concluded Black Hat and DEF CON security conferences.
Threat/trend reports: Legit Security, Ox Security, and ProtectAI have recently published reports covering infosec industry threats and trends.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss what it would mean to be in a golden age of OSINT and whether we are in one.
In this discussion, Tom Uren and Patrick Gray talk about a US government policy initiative to cover cyber insurance gaps while also improving security across the economy. Lofty goals, but Tom wonders if it is a difficult way to address security gaps.
The Risky Business team has recently started publishing video versions of our podcasts. Below is the main weekly show, with Pat and Adam at the wheel!




