Risky Biz News: Hackers hit Iranian steel industry
In other news: FSB officer detained for stealing crypto from a hacker; Russia tried to hack Ukraine's TV channels on NotPetya anniversary; and LockBit tests new ransoming strategies.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
A hacking group going by the name of Gonjeshke Darande [Predatory Sparrow (گنجشک درنده) in Farsi] has taken credit for a cyberattack that has hit the networks of three of Iran's largest steel companies—Hormozgan Steel, Khouzestan Steel, and Mobarakeh Steel.
The attack took place over the weekend and came to light on Monday when the hackers posted a video on Twitter of malfunctioning equipment.
#cyberattack against Iran's steel industry
— Gonjeshke Darande (@GonjeshkeDarand) 5:12 AM ∙ Jun 27, 2022
According to a report from the Associated Press, the video showed equipment from Khouzestan Steel, which had to halt operations as a result of the incident. The two other companies did not report any work stoppage as a result of the cyberattack.
In a series of tweets posted on Tuesday, researchers from security firm Check Point said they identified the malware used in the attack, which they named Chaplin, after the name of one of its files.
#BREAKING We found files related to the attack against the Steel Industry in Iran.
— Check Point Research (@_CPResearch_) 12:02 PM ∙ Jun 28, 2022
Initial analysis shows that the malware is connected to the attacks against Iran Railways last year, an attack that was thoroughly described in our previous research.
Here's what we know so far >>
Check Point said the malware appears to be a newer version of Meteor, the wiper used in a data-wiping attack against Iran's national railway system last summer. But unlike Meteor, Check Point said that Chaplin did not contain any data-wiping functionality.
Instead, the malware disconnected an infected computer from the local network, logged off the user, and then locked the user's screen with a message listing their past hacks and urging employees to call the phone number 64411 to prevent further attacks. The number is for the office of Supreme Leader Ayatollah Ali Khamenei and has been listed in the gang's previous hacks as a running gag.
Currently, it is unclear if the Chaplin malware had any modules that allowed it to interact with industrial equipment inside Khouzestan Steel's OT network.
Certfa Labs, an organization specialized in Iranian cyber operations, believes that images shared by the hackers on their Twitter account as "proof of access" suggest that they might have interacted with the plant's industrial equipment via another channel, namely via a control panel belonging to Irisa, a company that provides network services and industrial infrastructure to Iranian companies.
در تصویر دیگری که از سوی هکرها منتشر شده، پنل نرمافزاری متعلق به شرکت ایریسا رو میشه دید که این شرکت در حوزه اتوماسیون صنعتی فعالیت میکنه و مهمتر اینکه خدمات شبکه و زیرساخت صنعتی ارائه میده! بنابراین، بعید نیست خود این شرکت، یکی از سرمنشاءهای دسترسی هکرها بوده باشه.
— Certfa | سرتفا (@certfalab) 9:48 AM ∙ Jun 27, 2022
Certfa Labs says that this software is also used by many other Iranian steel companies, and not just the three hacked over the weekend and did not rule out that Gonjeshke Darande might still have access to other companies' networks as well. However, if they did, it is likely that the group would have used this access already, as in the past, they seemed to be focused on generating as much chaos and destruction as possible across Iran, and there would have been no reason to show restraint for this intrusion.
The group—also known as MeteorExpress or Indra—was also behind attacks on Iran's national railway system and gas stations. Another hacktivist group has also taken credit for attacks on Iran's state TV streams and the Evin political prison.
Breaches and hacks
Card skimming incident: Bank of the West, a US subsidiary of French banking giant BNP Paribas, disclosed on Monday a cybersecurity incident involving its ATM network. In a data breach notification letter filed with the California OAG, the bank said that it found skimming devices installed on some of its ATMs. An investigation subsequently discovered that the ATM skimming devices were active between November 2021 and April 2022 and allowed threat actors to steal payment card track data, including PIN numbers. "This stolen information may have been used to create fake debit cards and attempt cash withdrawals," the bank said.
Slovak Telekom: Slovak Telekom, the Slovak subsidiary of Deutsche Telekom, was hit by a cyber-attack over the weekend, the company confirmed in a Facebook message. The attack hit internal IT systems, causing downtime and interruptions for the telco's official website, mobile apps, and in-store and call center services.
Syniverse hack impacted Vodafone: Technology news site The Stack reported on Monday that the mysterious "supplier" whose hack put Vodafone's network in danger in an incident mentioned in the company's annual report might be a company called Syniverse, a company that manages routing and international roaming between different mobile networks. The company disclosed in October 2021 that it was hacked in an incident that took place in 2016 and went undetected for years.
Attack on Ukrainian TV channels: Ukraine's Security Service said they blocked "Russian special services" from hacking into the networks of the Ukrainian TV channels that participated in a national telethon held on Monday, on Ukraine's Constitution Day. According to the SSU, the attackers tried to access live video streams, live news feeds, and the computers of TV network employees.
Apetito attack: A cyberattack that has hit German frozen foods supplier Apetito is apparently also impacting food deliveries in the UK as well.
OAG California leak: The California OAG launched a new firearms portal this week, but the website was misconfigured and leaked the personal data of more than 2,800 Californians who own a concealed carry permit, according to The Reload.
Government, politics, and policy
Russia's Project Nemesis: Elise Thomas, a researcher for the Institute of Strategic Dialogue, has published a report on Russia's tactics of doxxing members of the Ukrainian military. The operators of this campaign claim to be a group of patriotic Russian hackers engaging in a volunteer effort they have dubbed Project Nemesis.
Hacker-for-hire scene is changing but booming: A report from MIT Technology's Patrick Howell O'Neill looks at the changing landscape of the surveillance and hacker-for-hire sector, which, despite sanctions imposed on Candiru, NSO Group, CSIS, and Positive Technologies, appears to be thriving. While some companies have gone under, more are taking their place. In addition, O'Neill also reports that governments from states like Saudi Arabia, Bahrain, Qatar, and Singapore are also building up local companies, following in the UAE's work with DarkMatter.
CISA guidance on Exchange Online: CISA published guidance on Tuesday and urged government agencies and private sector companies that rely on Exchange Online email servers to switch and update their authentication flows from legacy protocols to modern alternatives by October 1, 2022.
Cybercrime and threat intel
FBI warning on deepfakes: The FBI's Internet Crime Complaint Center has published a security advisory warning that some threat actors are using stolen personal data and deepfake technology to pose as legitimate persons and apply for remote work positions in companies. If they get hired, the threat actors use these positions to steal financial data, intellectual property, or other corporate data from the victim company.
Glubteba and AWM Proxy connection: Infosec investigative reporter Brian Krebs alleges that Dmitry Starovikov, one of the two Russians sued by Google for operating the Glupteba malware botnet, is also behind AWM Proxy, a website that rents access to proxy servers (actually computers infected malware).
Ransomware site doxxing: Cisco Talos said it was able to identify and link ransomware dark web domains to clear web servers and IP addresses by matching TLS cert serial numbers between them. Identified ransomware groups include DarkAngels, Snatch, Quantum, and Nokoyawa.
Hive decryptor: KISA, South Korea's cybersecurity agency, has released a free decrypter for the Hive ransomware. The decrypter only works with versions 1 through 4 of the Hive ransomware, but not the latest v5. The decrypter was released on Tuesday after KISA sponsored academic research into finding encryption flaws in the Hive code last year.
@campuscodi KISA is planning to upload the English version file on the NoMoreRansom site soon
— Seungjoo Kim (김승주) (@skim71) 11:14 PM ∙ Jun 28, 2022
@campuscodi Hive's TOR network blog and chats page are the slickest looking of all the groups, but their encryption scheme for their locker is complete trash. They go through all this work of hiding the key, but then re-use the one time pad! Version 5+ will be broken soon.
— 🎸 paul 🎹 (@paul_eubanks) 12:57 PM ∙ Jun 28, 2022
Harditem decryptor: On the same note, security firm Avast also released a free decryptor for the Harditem ransomware as well.
We briefly looked at the "Harditem" ransomware, discovered by @pcrisk and found that it's a decryptable variant of Prometheus/Thanos. Avast decryptor updated:
— Avast Threat Labs (@AvastThreatLabs) 12:04 PM ∙ Jun 27, 2022
NetWalker affiliate: Sebastien Vachon-Desjardins, a former employee of the Canadian government who later transitioned into an affiliate for the NetWalker ransomware gang, has pleaded guilty in a case filed by US authorities for attacks against US hospitals. Vachon-Desjardins was detained in January 2021, received a seven-year-old prison sentence from Canadian authorities in February 2022, and was extradited to the US to face similar charges in March.
FSB officer detained for stealing from a hacker: TASS reported last week that Russian authorities detained an FSB officer on charges of stealing cryptocurrency from a hacker. The suspect, named Dmitry Demin, a lieutenant colonel for the FSB's Samara regional unit, was accused of stealing cryptocurrency funds during a search of a hacker's home in the city of Syzran last year. The FSB officer was detained from a complaint filed by the hacker himself, who estimated the losses at "several million rubles."
FB Messenger chatbot campaign: Security firm TrustWave said it detected a Facebook credentials phishing campaign that abused Facebook's own Messenger chatbot technology to interact and dupe victims.
CISA KEV update: CISA has updated its KEV database with eight new vulnerabilities that are being exploited in the wild. This includes five new Apple bugs, a Mitel zero-day, a Chrome browser bug initially patched in May, and the PwnKit Linux vulnerability.
More LockBit 3.0 updates: After releasing v3.0 of their malware and launching a bug bounty platform over the weekend, the operators of the LockBit ransomware also appear to have made some changes to their dark web leak site. The group is now offering victims the possibility to buy and destroy their own data from the LockBit gang's servers.
🌐 The new website (Version 3.0) of Lockbit #Ransomware team allows anyone to extend the timer by 24 hours, destroy all data from the website, or download all data right away to maximize the ransom money for each victim 💸
— DarkFeed (@ido_cohen2) 7:48 PM ∙ Jun 27, 2022
Next level hacking group 🥷
#Lockbit
While this is a novel addition to ransomware leak sites, LockBit hasn't stopped here. In addition, the group now also provides victims with the ability to extend the ransom payment timer and delay the publication of their files—an option that many victims may be willing to pay while they prolong negotiations or gather the actual payment. In addition, Emsisoft's Brett Callow says that in recent LockBit attacks, the gang appears to be testing a new strategy where they gradually reduce the ransom demand as time passes, hoping that at one point, a victim that would have had no interest in paying might see the economic advantage in recovering their original files or stolen data at a lower price.
I suspect we'll see more a/b tests in the coming weeks/months as ransomware actors attempt to respond to changing market conditions. As-is, their conversion rates are down and there's more 'risk' in the risk reward ratio. 5/5
— Brett Callow (@BrettCallow) 6:24 PM ∙ Jun 27, 2022
Malware technical reports
Revive banking trojan: Mobile security firm Cleafy has published a report on a new Android banking trojan strain named Revive that appears to currently target Spanish banks.
AlphV/BlackCat: AdvIntel has published a technical breakdown of the AlphV/BlackCat ransomware, one of the first-ever written in the Rust programming language.
Racoon Stealer's return: After we featured two weeks ago a report from S2W about the return of the Racoon Stealer malware, the team from Sekoia managed to get their hands on and analyze one of these new Racoon Stealer 2.0 versions.
AstraLocker 2.0: ReversingLabs has published a report on AstraLocker, a ransomware strain built on the leaked Babuk source code, first spotted in February 2021. The report covers v2.0 of AstraLocker, first seen in March this year.
GlowSand: Security firm InQuest has a report detailing some of the recent malware samples "aimed at Ukraine and neighboring countries."
Bumblebee: Broadcom's Symantec team has a write-up out on the Bumblebee malware loader.
APTs and cyber-espionage
New ShadowPad infections: Kaspersky's ICS CERT team said they uncovered a suspected Chinese APT group that has launched attacks and has compromised the network of a telecommunications company in Pakistan. Kaspersky said it discovered the breach last year, in October, and one particular detail that stood out about the incident was that the threat actor also infected systems part of the telco company's building automation systems. A follow-up in-depth investigation into the APT group's operations also discovered other intrusions at organizations in the industrial and telecommunications sectors in both Pakistan and Afghanistan and a logistics and transport organization (a port) in Malaysia. Kaspersky said the APT group appears to have relied on exploiting Microsoft Exchange email server vulnerabilities to deploy the ShadowPad backdoor on infected networks.
DragonBridge: Mandiant said that a Chinese threat actor they are tracking as DragonBridge unsuccessfully tried to mobilize public protests against an Australian mining company that was set to build a processing plant for rare minerals in Texas on behalf of the US government. Mandiant said the group was attempting to defend China's dominance in the rare earth minerals market in this particular campaign, but that the group had also been linked to past influence campaigns going as far back as 2019, where they also criticized the Biden's administration handling of the COVID-19 pandemic and helped amplify claims made by Russian influence operations that the US was operating biological weapons labs in Ukraine. The report's publication and the campaign's audacity even got an official response from the Pentagon. [Additional coverage in Cyberscoop]
Evilnum: Zscaler has published a report on the recent activities of the Evilnum APT, first spotted two years ago. While initially the group has targeted the fintech sector, Zscaler said that in attacks that took place in March, they went after inter-governmental organizations that deal with migration services.
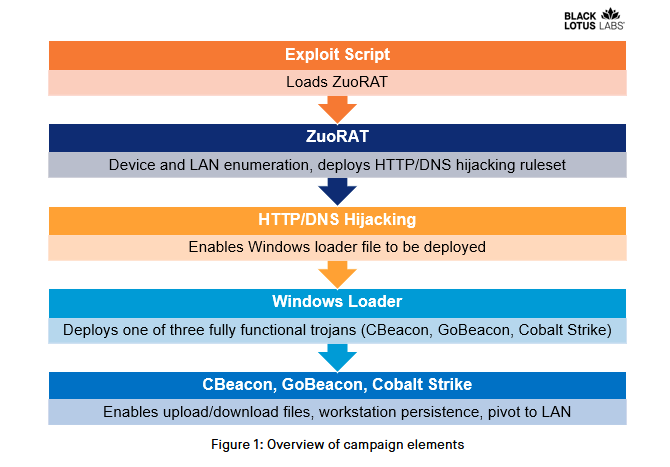
ZuoRAT: Lumen's Black Lotus Labs published a report on Tuesday on ZuoRAT, a new remote access trojan that they found installed on SOHO routers. Researchers said the malware was designed to allow attackers to pivot into local networks and even hijack HTTP and DNS traffic passing through the router. Lumen said it observed ZuoRAT telemetry and traffic coming from ASUS, Cisco, DrayTek, and NETGEAR routers in Europe and North America. The company said it believes the malware may be the work of a nation-state attacker.
Vulnerabilities and bug bounty
New crypto vulnerability: Tens of cryptography libraries have misimplemented the Ed25519 digital signature algorithm, according to Konstantinos Chalkias, a cryptographer at MystenLabs and Meta's former lead cryptographer. Chalkias said these libraries are exposing one of the Ed25519 private APIs, which can allow an attacker to extract private cryptographic keys from applications using the affected libraries, such as cryptocurrency wallets, web servers, or encryption apps. Chalkias discovered the issue earlier this month, and his initial list of 26 libraries has now been expanded to 40 entries with the help of the open-source community. Only one of the current 40 affected libraries has rolled out a patch at the time of writing. [Additional coverage in PortSwigger]
Open CVDB: Wiz launched today the Open Cloud Vulnerability & Security Issue Database, a public database of vulnerabilities in cloud services. The Open CVDB service tracks security flaws in platforms such as AWS, Azure, and the GCP.
FabricScape: Palo Alto Networks has published a technical write-up on FabricScape, a vulnerability in Azure Service Fabric that could be used to escape customer containers running on Linux-based Azure hosts. Microsoft said it rolled out patches earlier this month to all its systems.
NAA phantom credentials: The team at SpecterOps has research out on how network access accounts (NAAs) used by the Windows System Center Configuration Manager (SCCM) may leave artifacts like credential blobs on disk, exposing networks to attacks. The research team recommends removing NAA accounts from AD servers and transitioning to Enhanced HTTP.
Infosec industry
GitHub security update: GitHub announced on Monday that its security advisory database will now also include security alerts about vulnerabilities and supply chain attacks in Erlang and Elixir packages. Currently, the GitHub Advisory Database shows security alerts for Composer (PHP), Go, Maven (Java), npm (JavaScript), NuGet (.NET), pip (Python), RubyGems (Ruby), and Rust.




