Risky Biz News: Hackers blamed for false air raid sirens in Israel
In other news: New DFSCoerce NTLM relay attack; new OT:ICEFALL vulnerabilities; and Jacuzzi's backend gets popped.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Air raid sirens went off in the Israeli cities of Jerusalem and Eilat on Sunday, June 19, for at least 50 minutes following what government officials have described as a "cyber incident."
On Monday, the Israel National Cyber Directorate (INCD) confirmed the incident but said the alarms came from public address systems managed by local authorities and not the ones managed by the Israeli Defense Forces Home Front Command.
As a result, the agency asked local authorities to review the security posture of their air raid and public address systems by changing default passwords, enabling two-factor authentication, and restricting access to the management interfaces only to trusted IP addresses.
אזעקה צבע אדום, בשכונת נווה יעקב בירושלים
— 🌏News (@kisis007) 3:48 PM ∙ Jun 19, 2022
ככ״ה תקלה.
While several Israel-based security firms suggested the attack was carried out by Iranian hackers, government officials told the Jerusalem Post that it is still uncertain who was behind the intrusion.
Everyone seems to have rushed to attribute the incident to Iranian hackers in light of similar intrusions Iranian-linked groups orchestrated in the spring and summer of 2020 against Israeli water and wastewater management systems.
This is not the first time that hackers breach an air raid and public address system to sound false alarms. In previous years, hackers have also set off tornado sirens in Dallas (2017), DeSoto and Lancaster (2019), and Bastille also published research named SirenJack on how emergency alert systems manufactured by ATI Systems could be abused to set off false alarms.
Breaches and hacks
Flagstar Bank: Flagstar Bank, one of the largest banks in the US, disclosed a security incident during which a threat actor gained unauthorized access to the personal data of more than 1.5 million customers. The hack took place on December 3-4, last year, and was discovered on June 2, 2022, the bank said.
General tech and privacy
Windows updates problems: The Microsoft June 2022 Patch Tuesday security updates released last week have broken quite a few things. For starters, WiFi hotspot functionality on all versions of Windows is broken on Arm devices. Second, VPN, RDP, and RRAS connections are also broken for all Windows Server users since last week. Third, sign-ins into Azure Active Directory and Microsoft 365 services on Arm devices also broke last week because of the same updates, but the company has at least released a fix for these issues on Monday.
Meta lawsuit: Facebook's parent company Meta was sued on Friday for allegedly collecting private medical data from users visiting healthcare and hospital websites. The lawsuit was filed a day after The Markup exposed that many US hospitals were using the Facebook Pixel analytics tracker on their sites and unknowingly sending visitors' details to Meta's servers.
Mullvad removes subscriptions: Mullvad, one of today's biggest VPN providers, has removed the ability for customers to purchase monthly subscriptions (recurring payments via PayPal or payment cards). The company justified its decision as a privacy-protection feature as this process would entail mandatory logging of user details. Users can still purchase VPN servers via one-time payments, as this process requires less data stored about its users.
Acrobat Reader blocks security tools: Minerva Labs researchers said they discovered that the Adobe Acrobat Reader app is blocking at least 30 security tools from injecting their code into its process to perform their duties and scan PDF files for malicious content. The decision, while most likely done for performance and stability reasons, will most likely end up exposing its users to malicious code embedded in any PDF files. Over the past year, there have been several zero-days discovered in the Adobe Acrobat Reader app, which begs the question of why Adobe is sabotaging apps that are trying to protect its users.
Apple to bypass CAPTCHAs: Apple is adding a new feature in iOS 16 and macOS this fall, called Private Access Tokens, that will allow users to identify themselves as real users on websites and bypass modern CAPTCHA fields. Apple said the private access tokens would be generated based on a user's device identifier and Apple ID account, but that servers would not be able to track a user's identity using them. Cloudflare and Fastly have already announced support for Private Access Tokens, according to MacRumors.
Government, politics, and policy
OpSec mistakes expose Putin's fortune: Investigators from the OCCRP have used a little-known email domain to link together various real estate properties owned by shell companies supposedly linked to Russian President Vladimir Putin. "These companies have a variety of owners, including wealthy bankers and oligarchs—but also the children of Putin's friends and even his alleged mistress," the OCCRP said.
New cybersecurity bills signed into law: US President Joe Biden signed two cybersecurity-related bills into law this week—namely the State and Local Government Cybersecurity Act and the Federal Rotational Cyber Workforce Program Act. According to The Record, the former will allow CISA to offer state and local governments help to upgrade digital security tools and procedures, while the latter establishes a rotational cyber workforce development program across several government agencies in an effort to compete with the usually more lucrative private sector.
Germany Green Party hacked: The German Green party said that a cyberattack hit its IT systems and impacted email accounts belonging to Annalena Baerbock and Robert Habeck, ministers in the German government. Other party officials, such as Omid Nouripour and Ricarda Lang, also had emails forwarded to external servers, Der Spiegel reported last week.
No VPN fines in Russia: Russian government officials said that while they legally banned the use of VPN services inside Russia to bypass local restrictions on accessing banned foreign websites, they are not currently planning to impose fines for any offenses to this rule.
IT experts returning to Russia: Maksut Shadayev, head of the Ministry of Digital Development, told RBC TV on Monday that Russian IT experts who fled the country after its invasion of Ukraine are now returning home. Shadayev said that the "cancel culture," and the wariness of western companies when it came to hiring Russian specialists because of fears of "spying" played a crucial role in many IT specialists returning back to Russia.
Cybercrime and threat intel
AvosLocker: Cisco Talos said that it linked recent infections with the AvosLocker ransomware to hacked VMWare Unified Access Gateways that were not patched for the Log4Shell vulnerability.
Magecart attacks: Malwarebytes has reported that Magecart (web skimmer) attacks taking place in the browser (client-side) have gone down but are more covert now, as some groups appear to have re-focused operations on carrying out server-side attacks (undetectable via classic AV solutions) or have shifted operations towards going after cryptocurrency users.
LinkedIn fraud on the rise: LinkedIn has published advice on how to spot investment and financial fraud on its platform. The company's warning comes as an FBI agent told CNBC last week that cryptocurrency investment schemes have been running rampant on the platform.
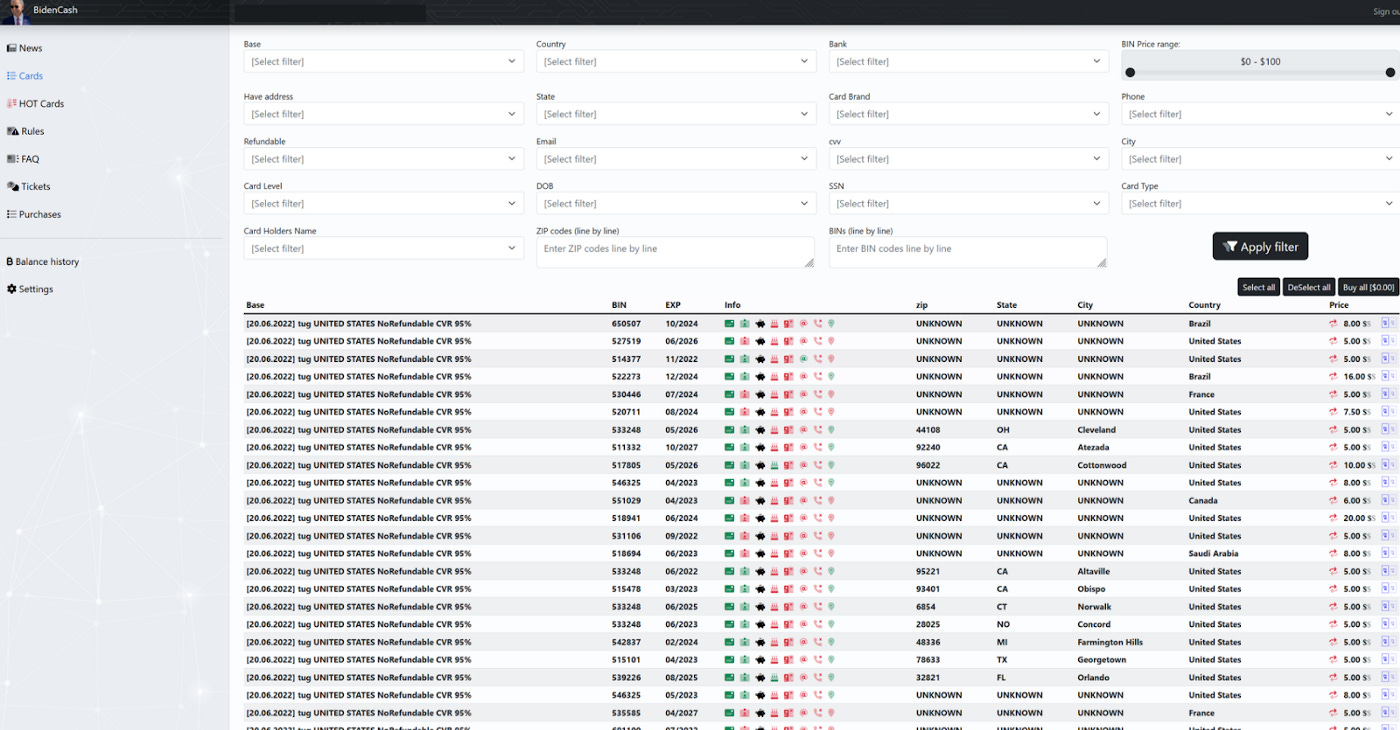
BidenCash: A new carding portal named BidenCash is making its presence felt on the cybercrime underground, allowing fraudsters to purchase stolen payment card data on the cheap. Discovered by Italian security firm D3Lab, the store launched earlier this year, and the company believes it sells data acquired through web skimming attacks. According to S2W, the portal claims to sell the data of 7.9 million payment cards from all over the world.
Domain registration scanning done right: A report [PDF] published on Tuesday by the Digital Citizens Alliance has discovered that several top domain registrars are allowing customers to register domains that appear to be intended for criminal use. This includes domains registered with names suggesting the sale of malware strains, stolen card data, opioids, untraceable guns, and fake COVID-19 cures and cards. Among the companies that are failing to police their new domain registrations, the report listed NameCheap, GoDaddy, and Network Solution.
Phishing gang detained in the Netherlands: Europol announced on Tuesday that Dutch police detained a phishing gang at the request of Belgian authorities. According to Dutch officials, the gang engaged in email, SMS, and WhatsApp spam that redirected users to e-banking phishing sites. Dutch police said the suspects are men between the ages of 25 and 36 from Amsterdam, Almere, Rotterdam, and Spijkenisse and a 25-year-old woman from Deventer. Europol said the suspects were very prolific and are believed to have stolen millions of euros from victims. Another phisher was also detained in the Netherlands at the request of Belgium police last week—in the city of IJmuiden—but it's unclear if he's a member of the same gang.
Rise of LNK malware: McAfee has published a report on the recent rise in the use of malicious LNK shortcut files as attachments in malspam campaigns, a rise that coincided with Microsoft taking steps to block the execution of VBA macro scripts, commonly used for malware distribution in the past.
Yo revisando algunos .LNK 🤓
— Germán Fernández (@1ZRR4H) 8:55 PM ∙ Jun 20, 2022
Malware technical reports
Matanbuchus: The Matanbuchus malware loader is currently seeing a huge rise in usage. The malware was first offered as a crimeware-as-a-service in February 2021 for the measly price of $4,000. Palo Alto Networks now has a technical report on this rising threat.
This is the ad for Matanbuchus, a malware loader currently advertised for $4k on forums to other cybercrime gangs
— Catalin Cimpanu (@campuscodi) 5:35 PM ∙ Mar 6, 2021
APTs and cyber-espionage
ToddyCat: Kaspersky has published a report on a new APT group they named ToddyCat. The security firm said the group has been active since December 2020 and has targeted high-profile entities in Europe and Asia. ToddyCat's arsenal is comprised of the Samurai and Ninja backdoors, and while the group initially targeted Microsoft Exchange email servers, since September 2021, Kaspersky said the group has also gone after Windows desktops.
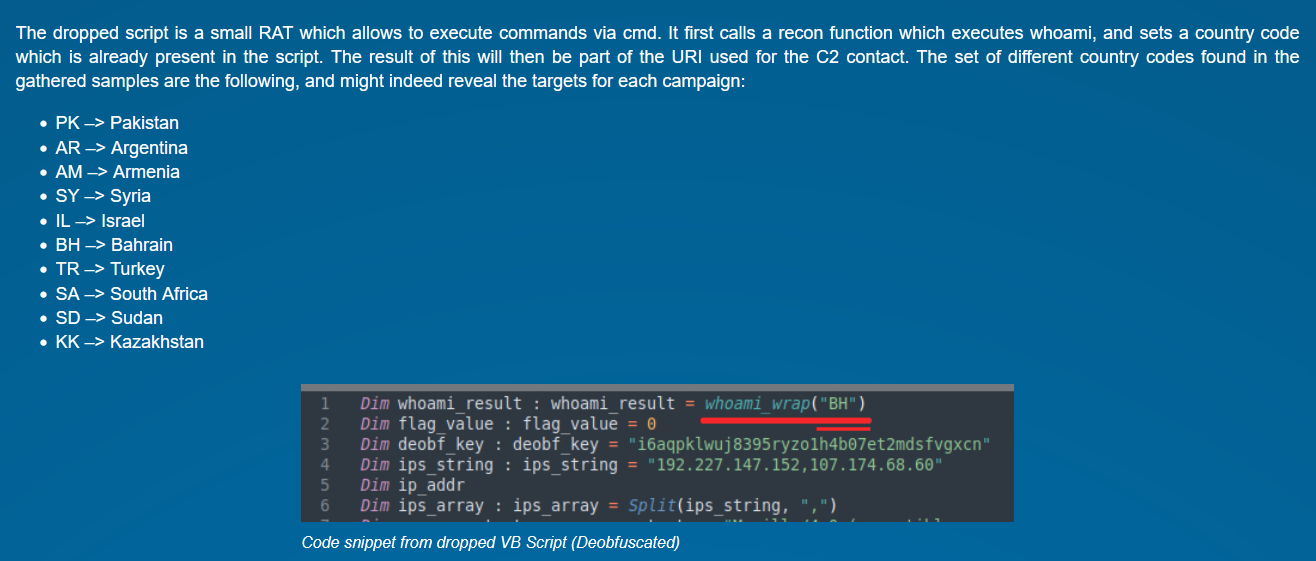
MuddyWater: Lab52 has a report out on the recent MuddyWater APT campaigns observed in the wild, including a C&C server OpSec mistake that exposed which countries the Iranian group was targeting.
Vulnerabilities and bug bounty
DFSCoerce NTLM Relay attack: A security researcher named Filip Dragovic has published details and proof-of-concept code for a new NTLM relay attack that he named DFSCoerce. The attack abuses the Microsoft Distributed File System (MS-DFSNM) protocol, a public key infrastructure (PKI) service that is used to authenticate users, services, and devices, to hijack a local Windows domain. DFSCoerce is part of a class of NTLM relay attacks that abuse various Windows protocols to trick domain controllers into authenticating a malicious NTLM relay, granting the attacker access to admin privileges and control of the entire domain. Microsoft published details and mitigations for this class of attacks last year. [More coverage here.]
Yep, this works. Just like the attack chain starting with PetitPotam works.
— Will Dormann (@wdormann) 2:39 PM ∙ Jun 20, 2022
You all already knew that if you didn't already apply the PetitPotam mitigations from last August the entire attack chain still works today as it was originally described, right?
kb.cert.org/vuls/id/405600
Jacuzzi smart hot tub hack: Security researcher Eaton Zveare said he found severe security flaws in the backend infrastructure used by Jacuzzi for its line of smart hot tubs. In a blog post on Monday, the researcher said he was able to hack this backend, known as the SmartTub network, and was able to view details for all the company's smart tub owners. The company appears to have secured the backend network but has ignored and shun the researcher and has not notified its customers about the accidental access to their private details.
OT:ICEFALL: Forescout published a new report on Tuesday about 56 vulnerabilities the company calls OT:ICEFALL. The vulnerabilities impact 26 models of OT equipment from 10 different vendors, including Honeywell, Motorola, Siemens, and others.
Blockchain research: Security firm Trail of Bits has published a report on the common vulnerabilities found in blockchain technologies. The research found that while blockchain cryptography might be secure, other issues plague blockchain technologies, such as network topology (60% of Bitcoin traffic goes through just three ISPs), software centrality (entities can decide to hard-fork projects at will), software lag (21% of Bitcoin node servers use outdated software), the use of unencrypted traffic, and more. Trail of Bits said it conducted this research at the request of the US Defense Advanced Research Projects Agency (DARPA). Its findings have also been summarized in this 20-minute podcast.
Scroll-to-Text attacks: There's a way to steal text from private pages a user might access using the new Scroll-to-Text Fragment feature, but I wouldn't worry that much as this is a very very very targeted attack method.
Infosec industry
GitHub coding standards support: GitHub said on Monday that its service can now scan user code for compliance with the AUTOSAR C++ and CERT C++ coding standards, a requirement of the ISO 26262 Part 6 compliance process.




