Risky Biz News: HackerOne discloses malicious insider incident, and nobody's surprised
In other news: Dutch university makes a profit from ransomware refund; Israel govt seizes victim's server for investigation; another DNS hijack in crypto-scam-world.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Three years ago, a Romanian vulnerability researcher accused employees of the HackerOne bug bounty platform of accessing bug reports he filed on the platform, taking his findings, and using them to file similar reports at other companies on the same platform—effectively stealing future profits.
At the time, the researcher did not provide any proof for his accusations, but once he went public, other researchers told similar tales. Nobody posted any proof, but everyone was telling the same story—of how HackerOne moderators would often mark and close a report as "informative," claiming a vulnerability had no significant impact on a company, but once the researchers tried to submit the same "unique" bug against other HackerOne programs, their reports would be marked as "duplicates," suggesting someone else had already filed a similar report before them.
Although no evidence that HackerOne employees were stealing bug reports for their own profits was ever posted, the rumors persisted throughout the years, mainly because everyone likes a good conspiracy theory.
But it's not a theory anymore. In a report published late Friday, just ahead of the July 4th extended weekend, and hoping the incident would not get extended media coverage, HackerOne disclosed the first incident of a rogue employee stealing a researcher's bug report.
Recounting the events following an internal investigation, HackerOne said that, on June 22, one of the companies that runs a bug bounty program on its platform complained that they received a vulnerability report through a separate channel that was similar to a bug submitted via its HackerOne program.
HackerOne's customer said they took note of the report because the person who submitted this bug used "intimidating language," in what's most likely coded language and lawyer-speak for a suspected extortion attempt.
When HackerOne tried to dismiss the customer's complaint with the classic excuse that "bug collissions and duplicates" can happen in the infosec industry, the customer "expressed skepticism that this was a genuine collision and provided detailed reasoning."
To HackerOne's credit, once the company was convinced of the customer's valid complaint, it took less than a day to identify the rogue employee, block his access to HackerOne systems, and remotely lock their laptop.
HackerOne also said it reviewed the employee's entire activity log from their two and a half months of employment and linked his identity to a second HackerOne account, which was used to collect bounty payments for bug reports the employee stole from other researchers.
The employee was fired on Thursday, and HackerOne said it has not decided if it would refer the case to law enforcement just yet.
In total, HackerOne said their former employee received payments from seven other companies, but this number could be larger, and asked companies to come forward if they received any communications from a researcher named "rzlr," their former employee's secondary sock-puppet account name.
Breaches and hacks
Ransom payment back for a profit: The Maastricht University in the Netherlands will receive the ransomware payment they paid to hackers in 2019 back and with a profit. The university paid €200,000 in Bitcoin to the hacker three years ago, and they will receive their Bitcoin back after Dutch authorities tracked down the payment to a money launderer in Ukraine, who was detained last year. The positive side is that the Bitcoin is now worth €500,000, which the university said it plans to put in a fund meant to help struggling students, according to Dutch newspaper de Volkskrant [non-paywalled version in NOS].
Sharp Boys leak: An Iranian hacking group named Sharp Boys has leaked the personal information of more than 300,000 Israeli citizens who signed up on travel agency websites. Leaked data includes ID numbers, addresses, and even payment card details. According to the Jerusalem Post, data from more than 20 websites was leaked, including hotel4u.co.il, hotels.co.il, isrotel.com, minihotel.co.il, trivago.co.il, and danhotels.com. According to the Times of Israel, all websites were operated by a company named Gol Tours LTD, and Israeli officials took a never-before-seen step of seizing all the company's servers to have better access and investigate the intrusion.
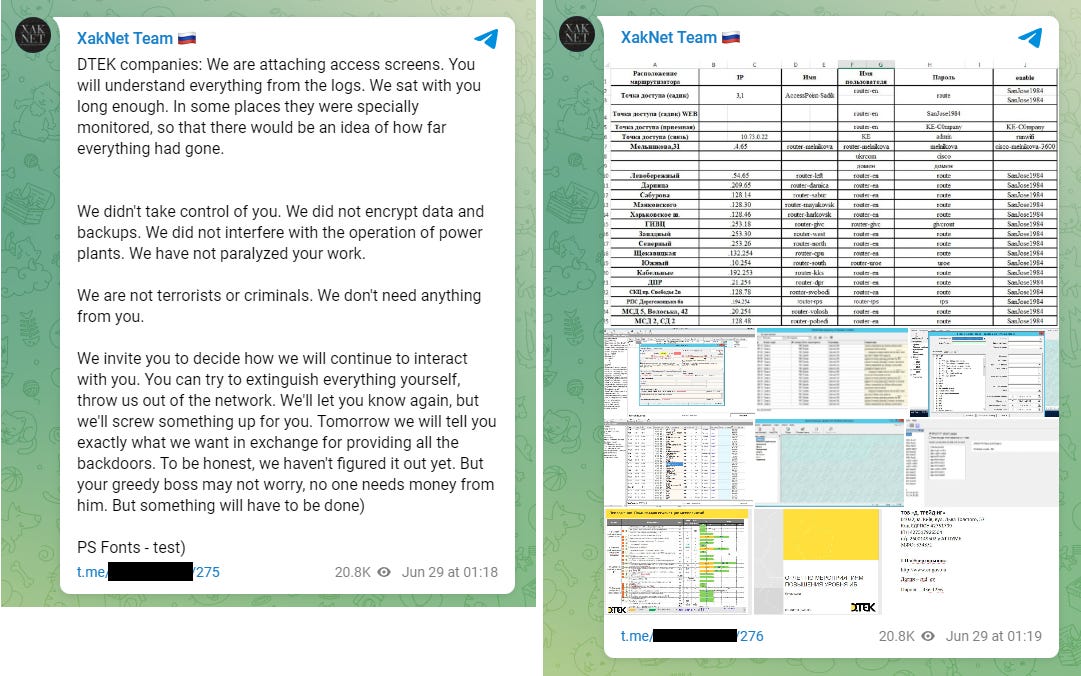
DTEK hack: Ukrainian officials said that Russian hackers and their military forces appear to have coordinated once again this past week. Victor Zhora, head of Ukraine's SSSCIP security agency, said that Russian hackers hit the network of Ukrainian power grid DTEK at the same time that Russian missiles hit the company's thermal power plant in Kryvyi Rih. DTEK has also formally confirmed the incident in a statement. On Russia's side, the DTEK hack was claimed by XakNet, a pro-Russian hacktivist group that many security experts say operates on the instructions of Russian intelligence services.
DNS hijack incident: Ankr, a company that provides server infrastructure for blockchain companies, disclosed a security breach on Friday, revealing that a threat actor social-engineered a Gandi employee to take control over some of its servers. The company said the attacker modified two nameservers in order to redirect traffic from two RPC servers to malicious versions. These two servers handled traffic for Polygon and the Fantom Foundation, two organizations that specialize in Ethereum-based infrastructure. Both companies confirmed the RPC infrastructure hijack but did not provide any details about the impact on their customers.
Public RPC gateway provided by Ankr for Polygon (polygon-rpc.com) and Fantom (rpc.ftm.tools) were comprised via DNS hijack earlier today.
— Mudit Gupta (@Mudit__Gupta) 12:00 PM ∙ Jul 1, 2022
Polygon and Fantom foundation have no control over services provided by others.
Use Alchemy or others while this is fixed.
General tech and privacy
China to invest in its own OS: A group of ten Chinese tech companies have agreed to help Kylinsoft build a new project named openKylin, meant to help improve the open-source development of Kylin, China's national operating system. The move comes as western software companies, such as Microsoft and Apple, are pulling out of Russia and creating technical issues for the Russian government, which, just like China, is incredibly dependent on US-made operating systems.
Azure AD now supports temporary passcodes: Microsoft has formally launched a new feature called Temporary Access Pass for Azure AD. The feature allows Azure AD servers to issue time-limited passcodes to a company's employees. These passcodes can be used by employees to register new accounts or reset accounts where they lost access. Microsoft said the feature should be used by companies that have migrated their employees to passwordless setups where employees use hardware security keys, authenticator apps, or biometrics to access their accounts and need a temporary way to let users register or reset access to accounts.
Government, politics, and policy
Israel accuses Iran of hacking UN org in Lebanon: Israel's defense minister accused the Iranian government and its Lebanese proxy Hezbollah of attempting to hack the UN peace-keeping force that sits on the border between Israel and Lebanon.
Israel to investigate Iran steel industry attack: The Israeli Defense Ministry said it would start an internal investigation after several Israeli media companies reported that Israel's cyber units were likely behind the cyber-attacks that crippled at least one Iranian steel plant last week. Officials said the hack and its attribution to Israel are in contradiction with its "ambiguity policy."
DOJ sues to stop possible BAH SIGINT monopoly: The US Department of Justice filed a lawsuit last week to stop Booz Allen Hamilton's acquisition of EverWatch. The DOJ believes that if the acquisition goes through, BAH will establish a monopoly and become the sole viable bidder in NSA defense contracts for signals intelligence modeling and simulation services (also known as MASON contracts).
DOJ goals for ransomware attacks: The US Department of Justice said in a strategic planning document published on Friday that it wants to increase the percentage of reported ransomware incidents it handles by 65% by September 2023. In addition, the department also wants to increase the number of seizures and forfeitures following a ransomware investigation by another 10%. [Additional coverage in The Record]
State Department bounty for election interference: The US State Department announced last week rewards of up to $10 million for any information leading to the identification of any person who works with or for a foreign government for the purpose of interfering with US elections through "illegal cyber activities." The bounty is being offered as the US is readying to go into the midterm elections later this fall. This is also the second time that the US State Department has offered such a bounty after it offered a similar $10 million reward in 2020, ahead of the presidential elections held in that year.
Cybercrime and threat intel
IT Army revelations: Stefan Soesanto, a cyber defense researcher from Switzerland and an expert in the activities of the IT Army of Ukraine [his PDF report here] said on Friday that ITAU members have admitted for the first time that they used a DDoS campaign against one of their targets as a distraction for a data exfiltration operation. The target was Russia's e-procurement resource platform Roseltorg.
New pro-Russian hacktivist group: A new pro-Russian hacktivist group calling itself DeaDNet has taken credit for the wave of DDoS attacks that have hit Norway over the past week. The group now joins the ranks of similar hacktivist groups like KillNet and XakNet, although it's unclear if they are just a front for Russian intelligence services, like the previous two.
Another new pro-russian hacktivist group. They have been conducting #ddos ops against #Norway with other groups.
— CyberKnow (@Cyberknow20) 9:54 AM ∙ Jul 2, 2022
#cybersecurity #infosec #RussianUkrainianWar #UkraineRussiaWar
New YDIO group: The former DarkLulz hacking group has rebranded as Your Data Is Ours (YDIO) and announced a series of coordinated attacks against companies located in BRICS countries (Brazil, Russia, India, China, and South Africa).
🌐 The #LulzArmy / #DarkLulz hacking team rebranded in "Your Data Is Ours" (#YDIO) on July 1st.
— Cyber, etc... (@cyber_etc) 11:37 AM ∙ Jul 3, 2022
They launched #OpBRICS against the 5 major emerging economies : Brazil, Russia, India, China and South Africa.
So far, they don't refer to the Anonymous collective.
Via @OurDatas
LockBit and Darkside connection: Emsisoft CTO Fabian Wosar says that large chunks of the LockBit 3.0 source code appears to have been copied from the now-defunct Darkside and BlackMatter ransomware strains. One of the theories why we're seeing this older code re-used in LockBit 3.0 is below:
@campuscodi There was an unconfirmed rumour that after we pwned BlackMatter for 8 weeks, they fired their dev team and hired new devs to redo everything, resulting in AlphV/BlackCat. So purely based on that, it would seem reasonable that LB hired the old BlackMatter/Darkside devs.
— Fabian Wosar (@fwosar) 9:16 PM ∙ Jul 3, 2022
Dark web trends shifts: After authorities seized several dark web marketplaces earlier this year, activity on carding marketplaces and underground forums saw a spike, according to a joint report from Agari and PhishLabs.
Raspberry Robin continues to spread: Microsoft told customers in a security alert last week to bolster their defenses against the Raspberry Robin malware, as the company has found infections with this new threat on the networks of hundreds of customers. Discovered by Red Canary last year, Raspberry Robin is a Windows worm that spreads through USB devices and often uses hacked QNAP NAS devices as command-and-control servers.
Malware technical reports
SolidBit and CryptOn: Researchers from the S2W Talon team have spotted two cybercrime groups using branding similar LockBit, a well-known and successful ransomware operation. The first is named SolidBit, and while its code appears to be based on the Yashma ransomware, its logo and payment site mimick LockBit's style. The second is named CryptOn, and while it has not been confirmed to be an actual ransomware operation, its leak site is almost identical to the one used by LockBit.
Vulnerabilities and bug bounty
Bind9 vulnerabilities: An internet scan carried out by researchers from security firm SpiderSilk found that more than 315,000 DNS servers are vulnerable to a vulnerability in the BIND9 DNS server software tracked as CVE-2021-25220. Disclosed earlier this year in March, the vulnerability can be used to poison the cache of DNS servers and propagate bad DNS responses across its clients.
DFSCoerce micro-patches: Security firm ACROS has released a micro-patch for the DFSCoerce vulnerability, which Microsoft said it wouldn't fix. Mitja Kolsek, co-founder and CEO of ACROS Security, told Risky Biz News that his company now has micro-patches for all four major NTLM relay attacks disclosed over the past year that Microsoft classified as "won't-fix" issues. This includes RemotePotato0, PetitPotam, PrinterBug/SpoolSample, and DFSCoerce.




