Risky Biz News: Greece tries to downplay its spyware scandal
In other news: Cuba ransomware gang claims Montenegro attack; Hacktivists release Lukashenko's passport scan as NFT; and Google launches bug bounty program for its FOSS projects.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Things are heating up between the EU and Greece in relation to a recent spyware scandal where the Athens government stands accused of using spyware to keep tabs on a political rival and a member of the EU Parliament.
In late July, Nikos Androulakis, a member of the EU Parliament and the president of Greece's second-largest opposition party (PASOK), filed a complaint with the country's Prosecutor's Office of the Supreme Court, claiming that his device had been infected with Predator, a commercial spyware product developed and sold by North Macedonian company Cytrox.
Androulakis said he learned of the attack on his device in June this year after he contacted a new cybersecurity unit of the EU Parliament founded earlier this year and tasked with checking the devices of EU officials for commercial spyware products.
Within a week, his revelations and the subsequent investigation tracked the attacks to an operation of the Greek national intelligence service, the EYP, and triggered the resignation of EYP Director Panagiotis Kontoleon.
Current leaks from an ongoing Greece parliamentary investigation also indicate the ruling Athens government may have also had a hand in the use of the Predator spyware against local finance journalist Thanasis Koukakis, who was notified of an infection on his device in March this year by CitizenLab.
You are a journalist in Greece and require technical support for secure phones and communication systems or want to check your systems for malware like Pegasus? Please reach out to us on info@flokinet.is
— FlokiNET (@FlokiNETehf) 3:44 PM ∙ Aug 30, 2022
Since the scandal has picked up steam in Greece, ruling officials, and especially Prime Minister Kyriakos Mitsotakis, whom Androulakis accused directly of ordering and orchestrating the surveillance operation, have been trying to downplay the incident as much as possible. Mitsotakis and his party have accused journalists Alexander Clapp and Nektaria Stamouli of working for the Greek opposition parties after they wrote scathing articles about government corruption and the degradation of press freedom in Greece in the New York Times and Politico Europe, respectively.
Response to allegations by #Greece’s govt spokesman @POLITICOEurope @JamilAnderlini
— Nektaria Stamouli (@nstamouli) 9:10 AM ∙ Aug 25, 2022
As of last week, Mitsotakis and his office switched to the narrative that it's actually "foreign forces are attempting to destabilize the nation" and not his government's abuse of power.
With pressure mounting from their own parliamentary investigation and the EU's newly established PEGA—a committee to investigate the use of Pegasus and equivalent surveillance spyware across Europe—the current Greek ruling regime has taken to attacking the EU itself.
In a letter sent to PEGA, Greece's representative to the EU has called the government's use of the Predator spyware a case of "national security" and called into question the competence of the European Union to investigate a government for internal matters.
As Politico Europe pointed out in a report yesterday, Greece's stance echoes similar responses from Hungarian, Polish, and Spanish officials, governments that have also been caught deploying spyware against journalists and political opponents.
But in a scathing reply on Twitter, Sophie in 't Veld, a Dutch MP and member of the EU's PEGA, contradicted Greece's stance calling the current unchecked use of spyware a threat to democracy and the rule of law across Europe, a condition mandated and regulated by EU conventions. It appears that the EU has stopped accepting the blanket excuse of "national security" when the constant victims of spyware across EU member states continue to be opposition parties and reporters investigating government corruption.
Slight correction to @vrailas: the spyware scandal is very much European competence. That is why @Europarl_EN @EP_PegaInquiry is investigating. Apart from violating EU laws, ao #GDPR, MEPs and @EU_Commission officials were targeted. And natl gvts are part of the Council.
— Sophie in 't Veld (@SophieintVeld) 5:31 PM ∙ Aug 24, 2022
In the meantime, the same PEGA is also going after Europol and its representatives for ignoring and refusing to investigate the abusive use of spyware across Europe. [More in this paywalled Politico Europe article]
It is rather embarrassing how brave and diligent journalists have uncovered continent-wide attacks on cybersecurity with the illegitimate use of spyware, while @Europol claims not to have been aware of anything. And not it knows, but refuses to investigate. #BigFatFail
— Sophie in 't Veld (@SophieintVeld) 9:04 AM ∙ Aug 30, 2022
The @Europol deputy director claims that Europol serves the member states and can only operate with the consent of the governments. So even if governments are corrupt or involved in criminal activity, @Europol will loyally serve them?
— Sophie in 't Veld (@SophieintVeld) 8:48 AM ∙ Aug 30, 2022
The new powers of @Europol are not a pick-and-chose menu. They have been granted with a view to protection EU citizens. Refusal to use these powers, is dereliction of duty plain and simple.
— Sophie in 't Veld (@SophieintVeld) 9:20 AM ∙ Aug 30, 2022
Breaches and hacks
Lexington BEC loss: The city of Lexington, Kentucky, lost $4 million to a BEC scam after an employee sent the funds to a scammer. The funds represented federal housing assistance intended for the Community Action Council. City officials said they managed to freeze the scammer's bank account, but reporting on the incident was unclear if officials managed to recover the stolen funds.
Another Chinese data leak: TechCrunch reported on Tuesday that Xinai Electronics based, a Chinese security camera vendor, has left exposed online a database that contained more than 800 million records with information such as facial and license plate scans. The database was exposed for months and was secured in mid-August after a security researcher and TechCrunch reached out to the company.
Belarusian passports as NFTs: Hacktivist group Belarusian Cyber-Partisans claimed on Tuesday to have obtained copies of passports for the entire country and have released an NFT collection (now-delisted) with passport scans for the country's president and other high-ranking government officials.
🧵1/3🔥For the 1st time in human history a #hacktivist collective obtained passport info of the ALL country's citizens. Now we're offering you an opportunity to become a part of this history 😎. Get a unique digital version of #lukashenka passport as #NFT opensea.io/collection/cpa…
— Belarusian Cyber-Partisans (@cpartisans) 3:42 PM ∙ Aug 30, 2022
General tech and privacy
FTC sues Kochava: The US Federal Trade Commission has filed a lawsuit this week against Kochava, an Idaho-based data broker, for allegedly selling the precise geolocation information of Americans, including data related to visits to healthcare providers, such as specialized hospitals and abortion clinics. Kochava sued the FTC earlier this month after the US agency inquired into its data handling practices. In a statement to the WSJ, Kochava called the FTC's current investigation "manipulative" and "based on completely false pretenses."
DeFi platform accidentally closes itself: In this newsletter "LOL of the week" story, cryptocurrency platform OptiFi said it accidentally closed its platform by accident following a programming blunder when it used a "close" command in its smart contract that actually did its job and closed the smart contract. The result was that the platform permanently locked nearly $661,000 worth of user cryptocurrency funds, which it promised to return in about two weeks while it restores some of the affected services.
First ad blocker running on Manifest V3: Ad-blocking software vendor AdGuard published what it called the "world's first ad blocker built on Manifest V3," which is Google's new platform for building Chrome extensions. Since it was announced, Manifest V3 has been criticized for being too restrictive and removing features that are typically used by ad-blockers and security extensions, a move that Google has categorized as taking steps to secure Chrome users but what tech experts have called a move to protect Google's advertising empire.
Government, politics, and policy
Cuba ransomware hits Montenegro: The operators of the Cuba ransomware took credit on Tuesday for the cyberattack that crippled the activities of the Montenegro government. Cuba claiming the attack comes to contradict a statement from Montenegro government officials last week, who said the attack was carried out by "Russian services." France's ANSSI security agency has been involved in the small Balkan state's response to the attack.
Russia using leaked hacked data to go after critics: The Russian government has used a database of Navalny supporters that was leaked online in April 2021 to make a first arrest—a man named Andrey Zayakin, who works as an independent journalist and who previously reported on academic plagiarism committed by Russian politicians. The database contained the names of people who donated to the Anti-Corruption Foundation (FBK), a political group created by jailed opposition leader Alexey Navalny. The FBK blamed the incident on an FSB informant who infiltrated their ranks, and while Russian police have used the leaked data to harass some donors in the past, as threat intel firm Flashpoint points out, this marks the first time they detained some using its contents.
Fines for hacked companies: The Russian government's plan to fine companies who suffer security breaches continues to go ahead, and according to a report from RBC, the government is considering imposing turnover-based fines for companies who leak the data of at least 10,000 users, with fines set to go higher the bigger the leak is.
White House classified meeting with aviation execs: Cyberscoop reported that the Biden administration plans to hold a classified briefing on cyber-threats next month, in September, with executives from the aviation industry. Similar meetings have also been secretly taking place over the past months with execs from various industry verticals and trade groups, such as with transportation officials in early August.
Sponsor section
RunZero (formerly Rumble Network Discovery) is one of this newsletter's four main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network. To learn more, please check out this runZero product demo below:
Cybercrime and threat intel
Malicious Chrome extensions: McAfee researchers said they identified and helped take down five Google Chrome extensions hosted on the official Web Store that had been downloaded and installed by more than 1.4 million users. The extensions offered to allow users to watch Netflix shows together, find website coupons, and take screenshots, but McAfee said the extensions tracked users' web activity and then secretly inserted affiliate IDs in users' web cookies so their creators could earn a profit.
FBI warning on DeFi attacks: The FBI's IC3 division has issued a public statement announcement on the rise in attacks targeting cryptocurrency DeFi platforms, attacks that have been steadily rising in recent years and which are currently accounting for most of the cryptocurrency losses recorded on the market.
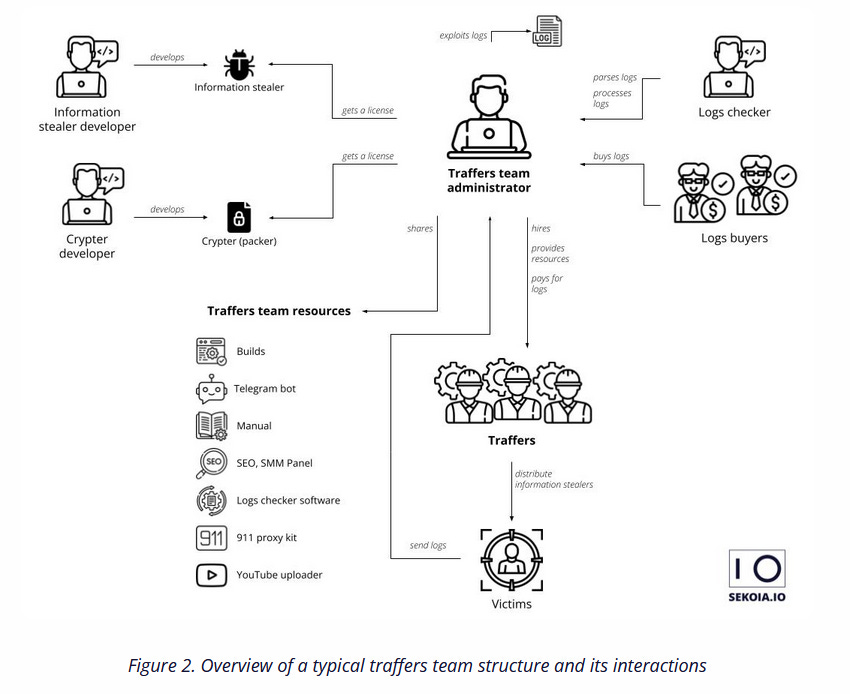
Traffers report: Security firm Sekoia has published a report this week on "traffers," a sub-category of the cybercrime underground specialized in running botnets of infected websites that redirect unsuspecting users to malicious pages serving malvertising or malware.
Malware technical reports
PureCrypter: Qihoo 360 Netlab researchers published a report on PureCrypter, a C#-based malware loader strain that has been for sale on underground forums. According to the company, the malware has been observed distributing a variety of malware strains, including Formbook, SnakeKeylogger, AgentTesla, Redline, AsyncRAT, and others.
ModernLoader: Cisco Talos researchers have published a report on a malware campaign that took place earlier this year, between March and June, and targeted users in Eastern Europe, in regions such as Bulgaria, Poland, Hungary, and Russia. The campaign used hacked websites to deliver various malware strains, such as DcRAT, Redline Stealer, and SystemBC, with the final payload, often being the ModernLoader remote access trojan and various Monero cryptominers.
ChromeLoader: CyberGeeks' Exousus published a technical breakdown of the ChromeLoader browser hijacker.
Nitrokod cryptominer: Check Point researchers have published details about a malware operation that uses legitimately-looking Windows desktop apps to install a cryptominer on users' devices. The malware has been promoted and made available via multiple software download aggregators and has managed to avoid detection by sleeping up to a month before starting any cryptocurrency mining on users' devices. Check Point named the malware Nitrokod after the name of its developer, believed to be located in Turkey.
Pegasus breakdown: Security researcher Vlas Pasca published this week a breakdown of the Pegasus for Android spyware toolkit. The write-up is the first part of a three-part series "because of the code's complexity and length."
APTs and cyber-espionage
TA423/RedLadon (aka APT40, Leviathan): Proofpoint and PwC researchers said they identified a suspected Chinese cyber-espionage operation active from April 2022 through June, delivering the ScanBox exploitation framework to targets who visit a malicious domain posing as an Australian news website. The targets and focus of this TA423/Red Ladon operation were Australian domestic organizations, as well as entities involved with offshore energy exploration in the South China Sea.
I am beyond excited to drop new research today with my coauthor @cyberoverdrive on TA423/RedLadon (aka Leviathan). It’s rare for @threatinsight to partner with others but Sveva and @PwC Global Threat Intelligence Team are among the rarest talents. 1/3🧵
— Digital_Monet (@aRtAGGI) 9:55 AM ∙ Aug 30, 2022
proofpoint.com/us/blog/threat…
Vulnerabilities and bug bounty
Google OSS VRP: Google launched on Tuesday a new bug bounty program—named the Open Source Software Vulnerability Rewards Program (OSS VRP)—to reward security researchers for reporting vulnerabilities in Google's open source projects, such as the Go programming language, the Angular JavaScript framework, the Bazel build system, the Fuchsia operating system, and the Protocol Buffers (Protobuf) networking libraries. Rewards vary from $101 to $31,337. Android has its own separate VRP—that's why it's not included here.
Pip vulnerability: Security firm Checkmarx said that it found a hidden and unexpected behavior in the pip package install utility for the Python programming language that will run the "setup.py" file even when developers download packages to their storage via the "pip download" command instead of directly installing them via "pip install." Checkmarx considers this a vulnerability because developers use this command to analyze Python code for vulnerabilities and malicious code and do not expect the setup.py script to run in this instance. Researchers pointed out that this was first reported to the pip team back in 2014 but has yet to be addressed.
WordPress security updates: The WordPress team released v6.0.2 of the CMS with security fixes, including for XSS and SQLi vulnerabilities.
Bootkit for Windows Sandbox: Security researchers Duncan Ogilvie and Miles Goodings said they created what appears to be the first bootkit that can infect the Windows Sandbox. The code's on GitHub.
A nice run-through for disabling PatchGuard, DSE, and getting a bootkit to run in Windows Sandbox.
— Daax Rynd (@daax_rynd) 6:54 PM ∙ Aug 30, 2022
Infosec industry
x33fcon videos: Talks from the x33fcon Europe 2022 security conference, which took place last week, are now available on YouTube.
Fall Pwn2Own hacking contest: The ZDI team published the upcoming program, targets, and rules for the Fall Pwn2Own 2022 hacking contest. This year's edition will take place in Toronto, Canada, and researchers will be able to take a swing at hacking smart devices, such as smartphones, wireless routers, printers, home automation hubs, smart speakers, and NAS devices.
New tool—GarbageMan: WithSecure (formerly F-Secure) has open-sourced GarbageMan, a collection of tools designed for .NET malware analysis.




