Risky Biz News: Google to delete accounts inactive for more than 2 years
In other news: EU passes cryptocurrency regulations; ransomware attack cripples one of Indonesia's largest banks; Zimbra servers targeted by new MalasLocker ransomware.

This newsletter is brought to you by Proofpoint. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. Apple podcasts users can click below:
Google says it plans to delete accounts that have been inactive for more than two years.
The company says that while the new policy has entered into effect this week, it will start mass-purging inactive accounts in December. This should give enough time for users to log in and reactivate older or backup accounts.
Google says it plans to first delete accounts that were created and never used again before moving to accounts that saw some activity.
Before deleting an account, Google will send multiple email notifications to that account's Gmail address and recovery email up to six months in advance.
Google VP of Product Management Ruth Kricheli says the company took this decision because an internal analysis showed that abandoned accounts are ten times more likely to use weak passwords or not have MFA enabled.
Kricheli says users can reactivate an account by logging in and performing one of the actions below:
- Reading or sending an email
- Using Google Drive
- Watching a YouTube video
- Downloading an app on the Google Play Store
- Using Google Search
- Using Sign in with Google to sign in to a third-party app or service
Google's announcement comes after Twitter announced a similar decision earlier this month.
The same criticism slung at Twitter also applies here too for Google. Families should look into keeping the accounts of loved ones who passed away active or at least download backups. This is especially important for Google Photos accounts that may still be hosting important memories that family members want to retrieve before Google nukes off its servers.
Breaches and hacks
ScanSource ransomware attack: Cloud service provider ScanSource says it was subject to a ransomware attack that has impacted the availability of some of its systems. The incident took place on Sunday, May 14. Affected services include customer portals, business operations, and its official website. The company says it's currently working to restore affected services.
Lacroix Group ransomware attack: French electronics manufacturer Lacroix Group has closed three of its factories this week to deal with the aftermath of a ransomware attack that took place over the weekend. Factories in France (Beaupréau), Germany (Willich), and Tunisia (Zriba) were shut down. While the company didn't know how much time the recovery process would take, it was optimistic it could resume production on May 22, next week. Lacroix says that the three factories accounted for 19% of its total sales last year. Despite this, the company says the incident is expected to have minimal impact as two of the factories were scheduled to operate for only three days this week anyway.
BSI ransomware attack: Bank Syariah Indonesia says it restored systems following a ransomware attack that hit its IT infrastructure at the start of the month. The incident caused major outages at BSI branches, its ATM network, and web and mobile banking services. BSI is one of Indonesia's largest banks, and the hack is considered the worst incident in the history of Indonesia's financial sector. The LockBit ransomware gang took credit for the intrusion and claimed to have spent more than two months in the bank's network. The bank says it's working with authorities to investigate and verify allegations that the personal data of more than 15 million of its customers was leaked online.
General tech and privacy
TailsOS adds LUKS2: The Tor Project has released version 5.13 of the TailsOS. The major change is that Tails now uses LUKS2 over LUKS1 for disk encryption.
Google privacy violations: Google is under investigation in the UK and EU (via Ireland) for breaking data privacy rules, including the GDPR, by holding to the personal data of job applications as far back as 2011. The investigation comes following a whistleblower's complaint. [Additional coverage in Fortune]
Zoom knew of Chinese censorship: According to a CyberScoop report, Zoom's top management knew that a part of the company's Chinese staff was working with the Chinese government to censor Zoom communications on sensitive topics, including Zoom's international userbase and not just China's internal market.
Twitter sued by dissident's family: The sister of an imprisoned Saudi dissident has sued Twitter and the Saudi government. The lawsuit argues that Twitter broke the law by allowing one of its employees to access the dissident's personal information and then share it with Saudi intelligence agents. The information was used to arrest and imprison Abdulrahman al-Sadhan, a vocal critic of the Saudi regime. Al-Sadhan is currently facing a 20-year prison sentence for "supporting terrorism." A former Twitter employee was found guilty last year in a case where he was accused of taking bribes and acting as an agent for the Saudi government. [Additional coverage in Washington Post/non-paywall]
Easy Healthcare shared pregnancy data: The FTC has filed legal action against Easy Healthcare, the Illinois company behind the Premon fertility app. The agency says the company deceived users by sharing their sensitive personal information and ovulation and pregnancy information with third-party companies, such as AppsFlyer, Google, and even two China-based firms. The FTC has now asked a judge to bar the company from sharing any data unless it obtains its users' explicit consent.
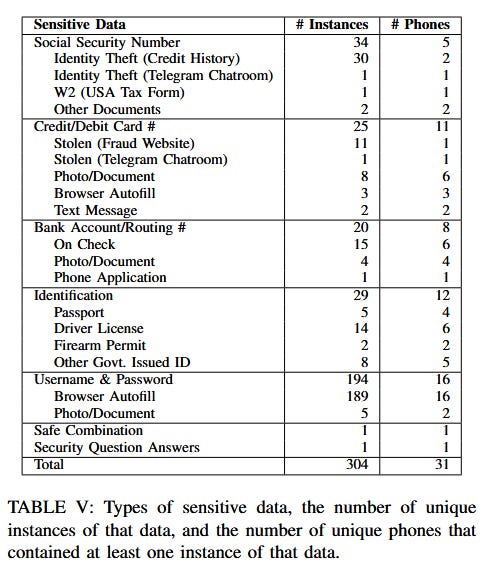
Police seized phones: Academics from the University of Maryland say that smartphones seized by US law enforcement that were not reclaimed by their original owners are being sold online without being wiped, exposing the data of their previous owners to possible crimes. Such devices are typically sold via PropertyRoom.com, an auction site specifically for selling police-seized inventory. Researchers say they were able to buy 228 smartphones off the site and extract data from most devices. This included emails, SMS messages, browser histories, bank and credit card information, Social Security numbers, and even sexually explicit photos and videos. Researchers say many of the phones either didn't have passwords or PINs, while some had easy-to-guess access codes, making their job easy. [Additional coverage in KrebsOnSecurity]
Government, politics, and policy
EU MiCA: The European Union passed a new legal framework this week designed to regulate the cryptocurrency market inside the EU. According to the MiCA (Markets in Crypto-Assets) framework, companies that want to trade crypto-assets in the EU must apply for a license and disclose information on the risks, costs, and charges that consumers face. Companies that mint crypto-assets will also be forced to reveal how much energy they use. But probably the most important MiCA requirement is that companies must take serious steps to combat money laundering via their platforms. This will be done by a mandatory KYC policy that will force crypto-trading platforms to obtain the names of their customers, including both sender and beneficiary, regardless of the size of the transfer.
CISA bills: The US House Homeland Security Committee has advanced two bills that give CISA new responsibilities in regard to open-source software and the government's cybersecurity workforce. According to HR 3286, CISA will be tasked with developing a framework to assess the risk of open-source software used by federal agencies, as well as engaging with the open source-community on security topics. According to HR 3208, CISA will also have to authority to train DHS employees to move from non-cyber to cybersecurity roles—as a way to boost the agency's cyber workforce. [Additional coverage in NextGov]
Montana bans TikTok everywhere: Governor Greg Gianforte has signed a bill into law that has officially banned [geofence bypass] the TikTok app across Montana. The law prohibits the company from operating in the state and requires app stores to block users in Montana from downloading TikTok. The law does not include penalties for users but allows authorities to fine app stores with $10,000/day if they fail to comply and remove the app. The law is not immediate and will go into effect on the first day of 2024. While other US states have banned the TikTok app on the devices of government employees, Montana becomes the first US state to issue a full-out ban on the app.
CIA on Telegram: The US Central Intelligence Agency has launched an official Telegram channel. This comes to complement the agency's Tor site.
NATO CCDCOE expands: The NATO Cooperative Cyber Defence Centre of Excellence expanded its ranks this week with four new members. Iceland, Ireland, Japan, and Ukraine have now formally joined the organization and will now cooperate with NATO members and several non-member countries to share cyber defense intelligence.
New Pegasus case: French media reports that officials have found traces of the Pegasus spyware on a device belonging to Florence Parly, the served as the French Minister of the Armed Forces from 2017 to 2022.
China blocks "fake news sites": The Cyberspace Administration of China has removed more than 835,000 online posts and shut down more than 107,000 accounts and websites peddling "fake news." The crackdown started in April and targeted accounts that used AI tools to generate reports that imitated legitimate news agencies. Officials say the fake news reports were designed to attract attention, "arouse the emotions of netizens," and drive traffic to specific websites.
Sponsor section
Proofpoint, this week's sponsor, has recently published the 2023 edition of Voice of the CISO, a yearly report featuring insights and experiences from more than 1,600 CISOs from around the world. The report covers recent threat actor trends, insights into better defenses, and the latest dynamics in board-CISO relations.
Cybercrime and threat intel
Betting and fantasy sites hacker charged: The US DOJ has unsealed charges against an 18-year-old from Wisconsin for hacking and selling access to accounts on fantasy sports and betting websites. Officials say Joseph Garrison used a technique called credential stuffing to gain access to approximately 60,000 accounts. Garrison and co-conspirators stole at least $600,000 from some of the compromised accounts. The attacks took place last year, and the FBI identified and raided Garrison's home in February of this year. Officials say they found more than 40 million username and password pairs and more than 700 configuration files that could be used to launch credential-stuffing attacks against different websites. Evidence retrieved from Garrison's phone also included conversations with co-conspirators on how to execute the credential stuffing attacks and how to sell access or steal funds from the accounts. While not officially confirmed, Garrison is believed to be the person behind credential stuffing attacks that hit sites like DraftKings and FanDuel last year.
Skynet Market founder pleads guilty: An Illinois man pleaded guilty to selling payment card information on the dark web. Authorities say Michael D. Mihalo founded and operated a dark web carding site named Skynet Market. Through the site and through profiles on other sites like AlphaBay Market, Wall Street Market, and Hansa Market, Mihalo and his partners sold the credit and debit card numbers of tens of thousands of US citizens.
Russian sentenced to prison for pro-Ukraine DDoS: A Russian court has sentenced IT specialist Yevgeny Kotikov to three years in prison for participating in a DDoS attack against Russian websites organized by pro-Ukraine hacktivists. The DDoS attack took place in February 2022, shortly after Russia's invasion of Ukraine, and targeted the website of the Russian Defense Ministry. Kotikov was also ordered to pay an 800,000 rubles ($10,000) fine.
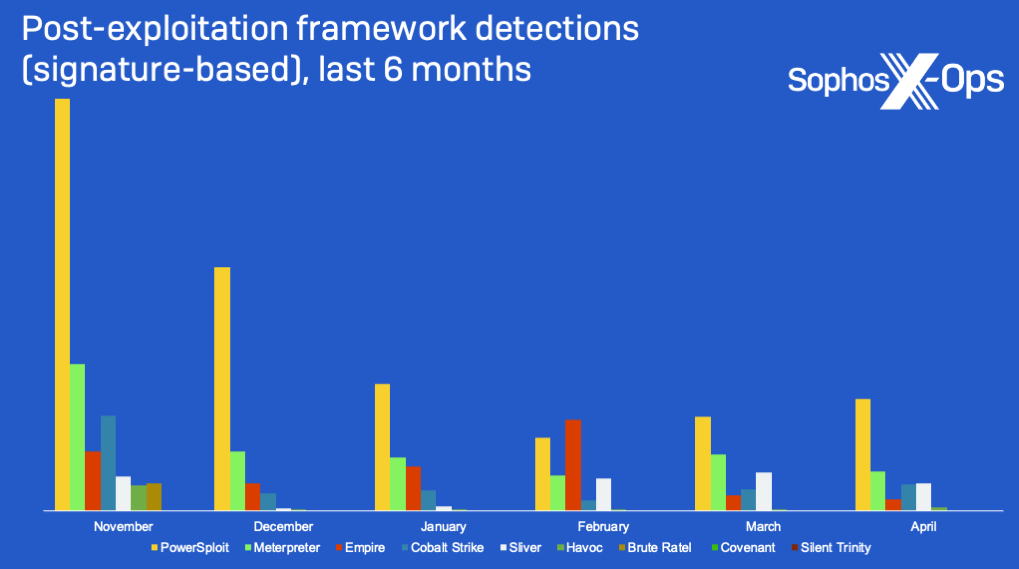
Attack framework detections: PowerSploit has been the most popular post-exploitation framework with threat actors over the last six months, according to data gathered by cybersecurity firm Sophos. Meterpreter and Empire were runners up in the second and third spots, while Cobalt Strike and Brute Ratel detections were low, suggesting they are primarily the go-to tools for targeted intrusions where stealth is crucial.
Hotel-themed malvertising campaign: Security firm Confiant has discovered a network of fake travel websites that lure visitors into handing over their payment card details and charging expensive fees for fake reservations at real-world hotels. Confiant says the threat actor is using expensive search engine ads to drive traffic to their sites, with their ads being centered around gaining authority on the "reservations" keyword. Based on telemetry, Confiant believes that more than 55,000 victims land on the malicious sites each month. Researchers say the group appears to be using a call center in India to secure reservations, with an average payout of $800 per victim.
DarkCrystal RAT campaign: Equinix security researcher William Thomas has details on a campaign using a boobytrapped desktop authenticator app to infect users with the DarkCrystal RAT.
TurkoRat on npm: ReversingLabs has found two malicious npm packages that installed TurkoRat, an open-source infostealer. Researchers say the two npm libraries were live for almost two months on npm before being detected.
FleeceGPT: Sophos has discovered five scammy ChatGPT-related apps on Apple and Google's app stores that fall under the category of a "fleeceware" app that scams users out of funds using large payments and trial fees.
ZIP domains abuse: Two weeks after ZIP domains became available for registration, Netcraft reports the first cases of phishing gangs abusing them for active campaigns.
New Leak Wolf group: Russian cybersecurity firm BI.ZONE has published a report on a threat actor named Leak Wolf. The group started operations in April 2022 and appears to be the latest in a long line of pro-Ukrainian hacktivist operations. BI.ZONE says the group breaks into company networks without relying on malware and typically leaks stolen data via its Telegram channel. The group is very active and has already leaked data for more than 40 Russian companies this year alone.
MalasLocker targets Zimbra servers: A new ransomware gang named MalasLocker is hacking, stealing email inboxes, and then encrypting Zimbra servers. The attacks started at the end of March and are still ongoing. The group has turned some heads because it is not requesting ransoms from hacked companies. Instead, the gang asks victims to make a donation to a non-profit charity that they "approve of" for a victim to receive a decryption key. The MalasLocker data leak site currently holds the stolen data of three companies and the Zimbra configuration of 169 other victims.
New Abyss RaaS: Security researchers have spotted a new Ransomware-as-a-Service operation named Abyss. The gang began operations in March of this year and has already listed 15 victims on its dark web leak site. Their latest entry is L3Harris, one of the major US defense contractors.
Malware technical reports
QakBot infrastructure: Team Cymru has published a look at QakBot command-and-control servers. The researchers found that the majority of Qakbot bot C&C servers are likely compromised hosts that were purchased from a third party. Based on the company's data, most of these compromised hosts are located in India. In addition, Team Cymru has also identified three upstream C&C servers that appear to be located in Russia.
GuLoader: ANY.RUN researchers have a write-up on how to deobfuscate GuLoader with Ghidra.
Sotdas: Qualys has a report on a new version of Sotdas, an IoT malware strain typically used to build DDoS botnets. Now, with cryptomining capabilities.
Risky Business Demo
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
APTs and cyber-espionage
APT28: Cybersecurity firm Sekoia says it observed Russia's APT28 group hack and abuse Ubiquiti routers to host phishing infrastructure. The phishing pages were capable of bypassing 2FA and targeted UKR.NET, a popular webmail service used by Ukrainian civilians. Sekoia says it found at least five hacked Ubiquiti routers hosting a malicious Python script they linked to APT28. The same routers also contained an SSH rootkit, but researchers couldn't tell if this was installed by APT28 or another threat actor.
SideWinder: Group-IB and Bridewell have published a joint report exposing new infrastructure operated by the SideWinder APT group. Uncovered infrastructure includes domains and 55 IP addresses that researchers say the group could use in future attacks. The identified phishing domains mimic various organizations in the news, government, telecommunications, and financial sectors.
Kimsuky AlphaSeed: S2W has discovered AlphaSeed, a Go-version of AppleSeed, a malware strain typically used by the Kimsuky APT. AlphaSeed works as an infostealer and can take screenshots of infected hosts, perform keylogging, and steal files. S2W says the malware was coded to receive and execute commands via emails received from a Naver email account.
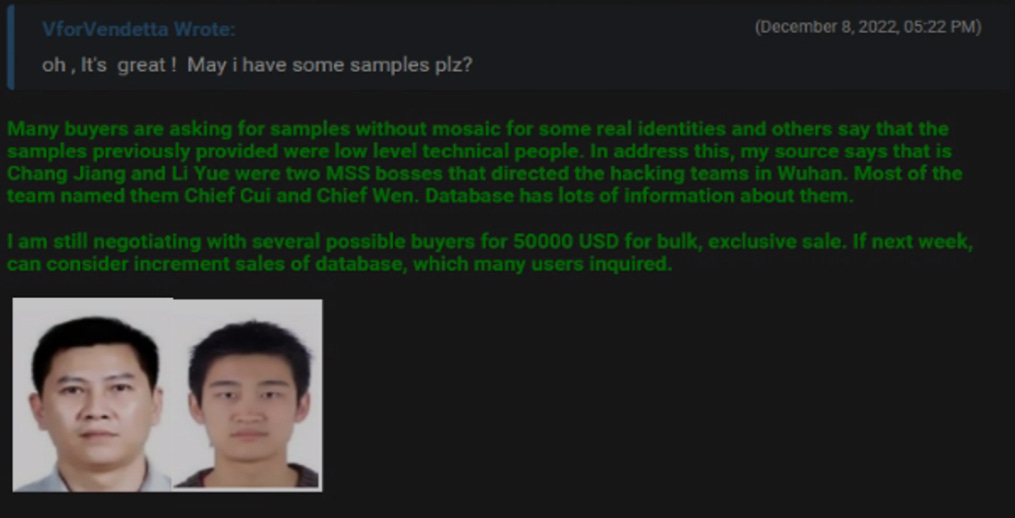
Intrusion Truth exposé final part: APT-doxing group Intrusion Truth has published its last article in its APT31 exposé, linking several employees of front-company Wuhan Xiaoruizhi to the Chinese Ministry of State Security. The group has asked the infosec community to sift through the files they leaked and make similar connections to APT31 (a challenge accepted by some). Previous articles in the series are here: 1, 2, 3, 4, 5.
Vulnerabilities and bug bounty
New Google VRP: Google has updated its Android VRP to grant researchers an extra $15,000 for bug reports that contain in-depth information, a PoC, and a root cause analysis of the reported vulnerability, information that Google says helps its engineers fix issues faster. In addition, Google says it will no longer issue CVEs for Android vulnerabilities that are rated medium and below. CVEs will continue to be assigned for Android bugs rated as high and critical severity.
Top 10 vulns of 2022: Snyk published the Top 10 most common code vulnerabilities it found across the JavaScript, Java, Python, Go, PHP, Ruby, and C# ecosystems last year. We won't list the entire Top 10 here, but #1 went to Directory Traversal.
MikroTik zero-day: Latvian network equipment vendor MikroTik has failed to patch a zero-day vulnerability that was used at the Pwn2Own hacking contest last December. The vulnerability impacts the company's routers. It allows an attacker on the same network to execute remote code with root privileges on the router without needing to authenticate. Pwn2Own organizer ZDI says it reported the issue to MikroTik on the day of the contest but has not received any update for the past six months.
VMWare vulnerabilities: STAR Labs researcher Nguyễn Hoàng Thạch published details on two VMWare vulnerabilities (CVE-2023-20869/20870) they used during the Pwn2Own hacking contest last December. Both bugs were patched in April 2023.
Netgear vulnerabilities: NCC Group researchers have found seven vulnerabilities in Netgear routers.
"Overall, the security posture of custom binaries built by NETGEAR contained many vulnerabilities, largely due to the widespread usage of insecure C functions such as strcpy, strcat, sprintf, or from off-by-one errors. However, the majority of the binaries on the NETGEAR router were compiled with many protections in place, including stack canaries, non-executable stack (NX), position-independent code (PIE) and address layout randomization (ASLR) enabled. These protections made many of the vulnerabilities identified difficult to exploit on their own."
AWS/GCP account takeover: Rezonate researchers have found that misconfigured OpenID (OIDC) GitHub Actions can be used to hijack AWS and GCP accounts. The organization says that based on its scans, the same misconfigurations exist in dozens of GitHub public repositories that use a GitHub OIDC provider to connect AWS or GCP accounts.
WAGO RCE: ONEKEY says it found a vulnerability in multiple WAGO products that can be used by an unauthenticated attacker to execute code remotely on the devices. Vulnerable products include Wago industrial automation controllers and touch panels. The company has released security updates.
Chrome RCE: Exodus researchers have published a technical write-up on a V8 RCE affecting older versions of Chrome and Edge (~April 2021).
New Fortinet zero-day PoC: BishopFox researchers have released a new PoC for CVE-2022-42475, a zero-day discovered in Fortinet firewalls last fall.
Apple security updates: Apple has released security updates for the vast majority of its products. The updates fix multiple vulnerabilities, including three zero-days that have been exploited in the wild. All three zero-days impact WebKit, the engine at the heart of Apple's Safari browser. One zero-day allows an attacker to escape the browser's security sandbox, while the other two can be used to execute malicious code via "maliciously crafted web content." The zero-days are tracked as CVE-2023-28204, CVE-2023-32373, and CVE-2023-32409.
Cisco security updates: Cisco has released ten security updates for various products. One is rated critical.
Jenkins security updates: The Jenkins project has published a security advisory warning about vulnerabilities in 22 plugins.
Chrome security update: There's also a security update for Chrome 113.
WordPress security update: And there's one for WordPress too.
Infosec industry
BSides SF 2023 videos: Talks from the BSides San Francisco 2023 security conference, which took place earlier this month, are available on YouTube.
Chris Inglis joins Securonix: Former National Cyber Director Chris Inglis has joined cybersecurity firm Securonix as a member of its newly-announced Strategic Advisory Board.
New Lacework CISO: Lacework has appointed Lea Kissner as its new CISO. Kissner previously worked as Twitter CISO before the whole Musk implosion.
Acquisition news: IBM has acquired Polar Security, a provider of cloud and SaaS security solutions, for $60 million.
Pwnie Awards nominations: Members of the infosec community can now nominate their favorite research and researchers for this year's Pwnie Awards ceremony, to be held in Vegas this August.
Mental health in infosec: As part of Mental Health Awareness Week, Virtually Informed has published a report on the current state of mental health in the cybersecurity industry.
RIP Security Fix: The Washington Post appears to have purged some of its old blogs. Sadly, this also included Security Fix, the OG Brian Krebs blog, before he went solo on KrebsOnSecurity.