Risky Biz News: Google throws out GlobalTrust certs
In other news: Spyware vendor pcTattletale hacked; South Africa suspends child maintenance payments after hack; Russian IAB charged in the US.

This newsletter is brought to you by SpecterOps, the experts in Attack Path Management. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Google is removing GlobalTrust TLS certificates from the Chrome browser's certificate root store.
The ban will apply to any new certificate issued by GlobalTrust after June 30 this year.
Chrome will continue to trust older/existing GlobalTrust certificates, and websites using them will work as before.
Google says e-commerce monitoring GmbH, the Austrian company behind the GlobalTrust brand, had several issues over the past years and failed to follow incident reporting requirements (e.g., [1],[2],[3],[4],[5],[6],[7],[8]).
[Of note, Mozilla has a planned maintenance on the day this newsletter goes live, so the links may not work on that day.]
Browser makers like Google, Mozilla, Microsoft, and Apple expect that certificate authorities (CAs) like GlobalTrust follow a long list of requirements when running their service and when suffering any kind of technical error or security breach.
Since the ban does not distrust older GlobalTrust certificates, this appears to be the case of a punitive measure against a misbehaving CA, with Google losing trust in the company and choosing to air it on the safe side.
Google will enforce the ban retroactively on all Chrome versions down to v124 thanks to a new feature the company added to the browser that allows it to manage its root store based on certificate SCTs (issue dates).
The other browser makers have not announced a similar decision, but Mozilla seems to be very well aware of the CA's shady history.
Breaches, hacks, and security incidents
pcTattletale hacked: A hacker has defaced the website of spyware app pcTattletale and leaked the company's source code and internal data. The incident took place on Friday, a day after security researcher Eric Daigle published details about a vulnerability in the company's app. The leaked data does not contain screenshots from victims but does contain database dumps, the app's source code, and its server root contents. According to Maia Arson Crimew, the company's website appears to have been backdoored since December 2011. Amazon took down pcTattletale's AWS account several hours after the hack. pcTattletale joins a list of over a dozen hacked spyware vendors.
ABN Amro hack: Dutch bank ABN Amro says hackers accessed some of its customer data following a ransomware attack on one of its third-party contractors. The incident impacted AddComm, a customer support company serving the bank's Dutch market. ABN believes hackers stole client names and contact information and warned customers to be wary of possible phishing and scam attempts.
Kakao breach fine: South Korea's privacy watchdog has fined instant messaging service Kakao over 15 billion won ($11 million) for a recent security breach. The incident took place in 2023 after the data of more than 65,000 Kakao users was leaked online. The fine is more than twice the highest recorded the agency has ever imposed. Kakao says it will appeal the fine, claiming the leaked data did not contain any personal details. [Additional coverage in Yonhap News]
South Korea defense hacks: South Korea's military and police forces have launched a joint investigation into the hacking of defense officials' personal email accounts. [Additional coverage in Yonhap News]
South Africa suspends child maintenance payments: South Africa's development agency has suspended child maintenance payments in the aftermath of a cyberattack last week. The Department of Justice and Constitutional Development says it took down the electronic payment system for third-party funds after several attempts to compromise the system. Officials are currently investigating the attacks and urged families to visit their nearest court for in-person payments. [h/t DataBreaches.net]
Cencora breach: US pharmaceutical company Cencora is notifying individuals who had their data stolen in a security breach earlier this year. The hack exposed patient names, postal addresses, dates of birth, health diagnoses, and medication details. The breach impacted customers at Cencora and other drug companies that work with the company. More than half a million users are believed to have their data stolen. [Additional coverage in TechCrunch]
Optus breach: The Australian Communications and Media Authority (ACMA) plans to prosecute Optus for its 2022 security breach. The Australian telco suffered a data breach in September of 2022 that affected up to 10 million current and former customers, amounting to almost a third of Australia's population. ACMA claims Optus failed to protect its customers' personal information. ACMA previously fined Optus $1.5 million in March for another security lapse that exposed the data of its 200,000 mobile customers (supplied under the Coles Mobile and Catch Connect brands) between January 2021 and September 2023.
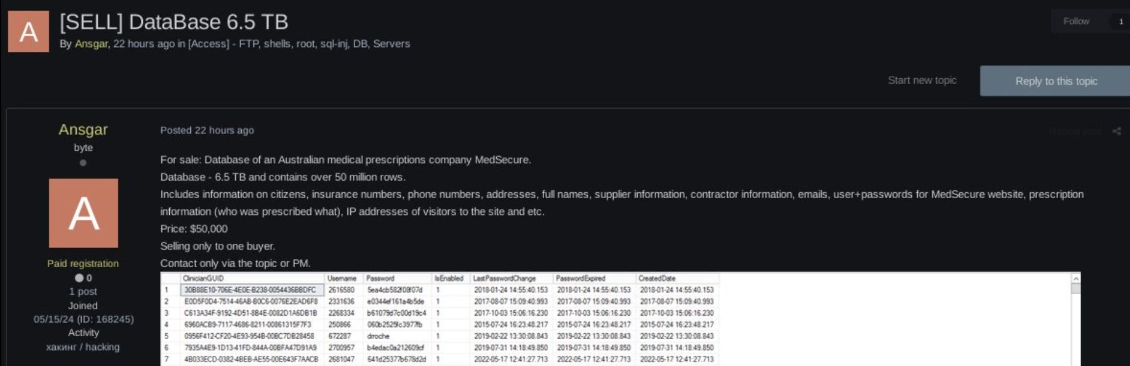
MediSecure data leak: A threat actor is selling data stolen from Aussie healthcare provider MediSecure on a dark web forum named Exploit. According to an analysis by threat intel analyst CyberKnow, the threat actor is "highly likely" to have access to the real MediSecure data.
General tech and privacy
ICQ shuts down: Russian instant messaging service ICQ will shut down on June 26, the company announced via a message on its website.
TLS Trust Expressions: Google engineers have proposed a new IETF standard named TLS Trust Expressions that introduces a new TLS extension/mechanism to servers to deploy multiple certificates and transparently select between them. This enables a multi-certificate deployment model, for a more agile and flexible PKI that can better meet security requirements.
Firefox and Manifest V3: Mozilla has published a timeline of its Manifest V3 implementation, which, among other things, will bring in more revokable permissions.
Windows 11 24H2: Microsoft will remove Cortana, WordPad, and Tips from Windows 11 with its 24H2 fall release. Instead, everyone will get saddled up with the company's next-gen useless AI disaster Copilot.
Android 15: Google has published a blog post with some of the security features expected to arrive with Android 15 later this fall. The major features include the addition of private spaces (a separate space on their device where they can keep sensitive apps away from prying eyes, under an additional layer of authentication) and improved background activity protections (so background apps can't bring apps to the foreground and abuse user interaction).
Game cheating case: In a landmark case, a US judge ruled that a cheating software vendor violated the copyright of Bungie, the maker of the Destiny game. Since US courts work on precedence, this will allow even more companies to go after wallhack and cheat software vendors plaguing their games. Unfortunately, this will likely impact legitimate gaming modders as well. [Additional coverage in PC Gamer]
Stadium privacy: Privacy International has raised a sign of alarm about the increasing use of facial recognition in sports stadiums around the world. I, for once, do not agree with this one.
Meta could care less about disinformation: Meta's WhatsApp disinformation tiplines established to allow Indian users to report fake news have either not kept up with tips or have failed to go and verify reports; in the latest example of Meta's failure and disinterest in stopping disinformation campaigns. The company laid off its disinformation team last year, shuttered another tool this year, and is currently under investigation in the EU for failing to detect even the most obvious of Russian disinfo campaigns. [Additional coverage in Rest of World]
Government, politics, and policy
FHA new cybersecurity reporting requirements: The US Federal Housing Administration (FHA) has published new cybersecurity reporting requirements [PDF]. According to the new rules, FHA-approved lenders must report cybersecurity incidents to the US Department of Housing and Urban Development within 12 hours of detecting a breach. Mortgage companies have already criticized the new rules for the super strict reporting timeline, which leaves little room for evidence collection or legal consultations. [Additional coverage in the HousingWire]
Zambia hunt forward: US CyberCommand has confirmed it recently carried out a hunt-forward mission in the African country of Zambia. The mission took place last year and lasted for three months. According to The Record, the Zambia mission was one of the 22 hunt-forward missions CyberCom carried out last year.
Trump and Ulbricht: For some weird reason, US presidential candidate Donald Trump said he wants to pardon Silk Road founder Ross Ulbricht. [Additional coverage in CoinDesk]
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Justin Kohler, VP of the Bloodhound team at SpectreOps about ‘attack paths’, the ways that malicious actors maneuver through Active Directory to elevate their privileges. They discuss how and why they arise and what you can do about them.

Cybercrime and threat intel
IAB charged: The US Justice Department has charged a 31-year-old Russian national for working as an initial access broker. Authorities say that between 2019 and 2024, Evgeniy Doroshenko sold access to hacked networks on dark web forums. Doroshenko operated under the hacker name of Flanker and is believed to be located in Astrakhan, Russia.
Coinbase phisher pleads guilty: An Indian national has pleaded guilty to participating in a phishing operation that stole over $37 million from Coinbase users. Chirag Tomar was part of a larger group that set up fake Coinbase Pro login pages, lured victims to the sites, and then emptied their accounts. Authorities say Tomar used the stolen funds to pay for a lavish lifestyle, expensive products, and trips abroad. Tomar was detained at the Atlanta airport in December of last year.
Israeli hacker-for-hire case: Earlier this month, UK authorities detained an Israeli man at the Heathrow airport for allegedly conducting a cyber-espionage campaign on behalf of an American PR firm. He was released by UK authorities after a major blunder, but new reporting suggests his client was Washington public affairs firm DCI Group.
Smiling Hacker case: French authorities have re-brought their case against Algerian hacker Hamza Bendelladj, known as the Smiling Hacker, for launching ransomware attacks against French organizations. The initial case was dismissed due to legal technicalities, but French prosecutors have managed to have a new case scheduled in front of a judge in January of next year. Officials are accusing Bendelladj of writing and distributing the PyLocky ransomware while in prison in the US (for his role in the SpyEye banking trojan). It's unsure if the trial will even take place next year as Bendelladj is scheduled to be released from his US prison in July, and there's no talk yet of any extradition request. [Additional coverage in ZDNet.fr]
Neculiti brothers: Infosec reporter Brian Krebs has picked up and expanded on a Correctiv report covering the Neculiti brothers, Ivan and Juri, two Moldavian nationals behind several shady web hosting companies. Their companies have provided hosting to Russia's disinformation campaigns and many of the pro-Kremlin faketivist groups launching DDoS attacks against websites in Western democracies.
Unsafe Rust: The Rust Foundation says that 20% of all Rust packages (crates) use the "unsafe" keyword to run unsafe code and expose their code to attacks. Rust developers say that most of the unsafe keyword usage is related to the loading of non-Rust language code or libraries, such as C or C++. The package with the most uses of the unsafe keyword is the Windows crate, which allows Rust developers to call into various Windows APIs.
LLMs in cyberattacks: The Netherlands' cybersecurity agency has published a report on how LLMs could potentially be used in cyber operations.
Malicious AV sites: Security firm Trellix goes over a malware delivery campaign using websites that impersonate well known antivirus companies.
New npm malware: Fourteen malicious npm packages were discovered last week. Check out GitHub's security advisory portal for additional details.
Threat/trend reports: DataTribe and NBIP have recently published reports covering infosec industry threats and trends.
Malware technical reports
MITRE hack malware: MITRE has published a three-part series that looks at its security breach from earlier this year. In its last part, published last week, MITRE looks at the group's malware—the BRICKSTORM backdoor and the BEEFLUSH web shell.
Sponsor Section
Justin Kohler, VP of Product at SpecterOps, shows how BloodHound Enterprise can be used to find and fix Active Directory (mis)configurations that could let attackers easily own your entire enterprise.
APTs, cyber-espionage, and info-ops
Shedding Zmiy: Rostelecom's security team has discovered a new APT group attacking Russian government agencies and their contractors. Named Shedding Zmiy, the group has links to the old Cobalt cybercrime operation. Rostelecom says the group switched from financial crimes to espionage in late 2022. The Russian telco describes Shedding Zmiy as one of the most active and professional APT groups currently targeting Russia.
Hellhounds: Russian security firm Positive Technologies has published more details about an APT it tracks as Hellhounds, which the company first spotted last year. PT says the group has been active since 2021, operates the Decoy Dog malware, and has made at least 48 confirmed victims inside Russia.
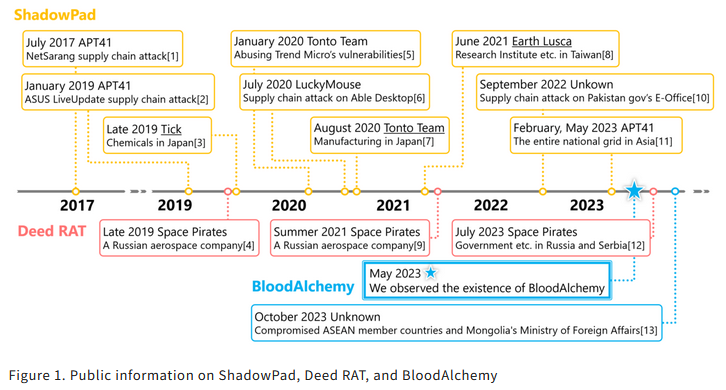
BLOODALCHEMY: ITOCHU says the new BLOODALCHEMY malware is an evolved version of Deed RAT—itself a successor of ShadowPad. The malware was spotted in the wild for the first time last year by Elastic's security team. Elastic spotted the malware on the network of a Foreign Affairs Ministry from a member of the Association of Southeast Asian Nations (ASEAN)—so very likely, a Chinese APT op.
Vulnerabilities, security research, and bug bounty
Chrome zero-day, again: Google has released an update for its Chrome browser to fix a zero-day (CVE-2024-5274) exploited in the wild. The zero-day is a vulnerability in Chrome's V8 JavaScript engine, and was discovered by one of Google's internal security teams. This is the fourth Chrome zero-day Google patched this month and the eighth this year.
MikroTik vulnerability: DEVCORE researchers have (finally) published a technical write-up on CVE-2023-32154, a MikroTik vulnerability they used at the Pwn2Own hacking contest in 2022, which they won. The vulnerability is an RCE in MikroTik routers that impacts all RouterOS-based devices released since 2015.
ILIAS LMS vulnerability: ERNW researchers have found a remote code execution vulnerability in the ILIAS LMS application. The vulnerability is actually an exploit chain between a PHP filter bypass (CVE-2024-33529) and an XSS (CVE-2024-33528).
Replicate vulnerabilities: Cloud security firm Wiz has discovered a vulnerability in the Replicate AI platform that could have allowed a malicious LLM model to access sensitive data from other customers hosting on the same infrastructure. In the aftermath of this research, Wiz released PEACH, a step-by-step framework we developed for modeling and improving SaaS and PaaS tenant isolation.
Windows 10 EoP: Synacktiv researcher Guillaume André has published a write-up on CVE-2024-26238, an elevation of privilege vulnerability he found in the Windows 10 PLUGScheduler scheduled task. Microsoft patched the bug in this month's Patch Tuesday.
Telesquare PoC: Security researcher Valentin Lobstein has published a PoC for CVE-2024-29269, an RCE in Telesquare routers.
Confluence PoC: Security researcher Huong Kieu has published a PoC for CVE-2024-21683, an RCE in Atlassian Confluence servers that was patched last week. [h/t Screaming Goat]
Jenkins security updates: The Jenkins project has released security updates to fix vulnerabilities in three of its plugins.
Microsoft honeypot: In a blog post last month, Microsoft confirmed that the code.microsoft.com subdomain had been a long-running honeypot. The blog post has some interesting stats from the subdomain, now formally retired. [h/t Dave Wilburn]
WhatsApp vulnerability: ZenGo CTO Tal Be'ery has found an issue in WhatsApp that allows attackers to fingerprint a user's devices if the target has their account connected to multiple devices. Meta declined to patch the reported issue.
"Simply put, users expect their chats’ history to be the same across all devices. However, we show that a rogue client can send different messages to the same user’s different devices and it has some obvious (and some less obvious) security implications."
Infosec industry
Acquisition news: Bug bounty platform Bugcrowd has acquired Informer, a provider of attack surface management (ASM) and continuous penetration testing.
New tool—Intune Assignment Checker: Security researcher Ugur Koc has released Intune Assignment Checker, a tool that scans and provides a detailed overview of assigned Intune Configuration Profiles, Compliance Policies, and Applications for user, groups, and devices.
New tool—Tor-DDoS: Enkidu6 is maintaining a list of IP addresses known to launch attacks on Tor relays/nodes.
New tool—Nimfilt: ESET has open-sourced a new tool named Nimfilt that can be used to analyze Nim (malware) binaries.
New tool—Cranim: The NCC Group has open-sourced a tool called Cranim that can be used to visualize and render cryptographic concepts.
New tool—Sudo for Windows: Microsoft is working on Sudo for Windows. It works like the Linux original, allowing users to run elevated commands directly from unelevated terminals.
Google urges abandoning phishing tests: Google has urged that companies abandon phishing tests and instead adopt what it calls phishing fire drills (aka phishing training).
Risky Business Podcasts
In this edition of Between Three Nerds, Tom Uren and The Grugq talk to Elena Grossfeld about the strategic culture of Russian intelligence organizations.




