Risky Biz News: Google TAG says it tracks 30 surveillance vendors
In other news: NSA says leave PowerShell on; CISA wants a cybersecurity hotline; and five EU states used NSO spyware.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
There are three tech companies today that have a unique and comprehensive view of people's online lives. These are Apple, Google, and Microsoft, all of which are behind today's top operating systems, as well as some of the Internet's most popular online services.
For Google, the signals it acquires from Gmail, Drive, Chrome, and Android allow the company remarkable insight into today's threat landscape. For example, Google can see what types of threats are hitting your Android devices and your email inbox, even if those threats target other operating systems where Google doesn't have great visibility into.
Over the years, Google has dedicated significant efforts and funds to boosting its security teams to take advantage of this unique position, and, once in a while, the company makes a statement that reveals the scope of a particular problem or topic.
One of those days was yesterday. In a blog post on Thursday, the Google Threat Analysis Group (TAG), the Google security team that tracks advanced threats, revealed that they are aware of and currently tracking more than 30 organizations selling surveillance capabilities to government-backed threat actors.
This quite large number highlights that while the public's attention has been captured by a few vendors like Hacking Team, Gamma Group, NSO Group, and Candiru, there are far more entities that engage in similar operations in an industry that has been loosely regulated over the past decade.
The latest Google TAG report adds new information about RCS Lab, an Italian company that used to be a reseller for the old HackingTeam, but has now moved into creating and selling its own tools.
The company was at the center of a first report last week when mobile security firm Lookout published an analysis of Hermit, a piece of Android malware packed with different exploits, which Lookout said it initially found being deployed in Kazahstan in April this year. Further sleuthing also found the same malware being deployed in Syria, and in Italy, in both 2019 and 2021, as part of law enforcement anti-corruption investigations, according to documents released by the Italian government.
Google TAG's report effectively confirms Lookout's findings and adds more depth, especially on the Hermit's malware use inside Italy, where Google said that the entity which deployed the malware appears to have worked with local ISPs to disable the target's mobile connection before sending an SMS message telling the victim to install an ISP-themed mobile app to restore their connection.
Furthermore, Google also confirmed that RCS Lab also has iOS exploits in their arsenal, namely CVE-2021-30983 (aka Clicked2), which Google's Project Zero team analyzed in a different blog post here, and which Apple patched last December. But this was just one of the six iOS exploits RCS Labs had packed into the malicious iOS app.
Now, Google says that while everyone has been fixated on taking down NSO Group, other vendors have been slowly growing in the Israeli company's shadow.
"[T]he commercial spyware industry is thriving and growing at a significant rate," Google TAG's Benoit Sevens and Clement Lecigne said. "This trend should be concerning to all Internet users. "
These vendors are enabling the proliferation of dangerous hacking tools and arming governments that would not be able to develop these capabilities in-house. While use of surveillance technologies may be legal under national or international laws, they are often found to be used by governments for purposes antithetical to democratic values: targeting dissidents, journalists, human rights workers and opposition party politicians.
Aside from these concerns, there are other reasons why this industry presents a risk to the Internet. While vulnerability research is an important contributor to online safety when that research is used to improve the security of products, vendors stockpiling zero-day vulnerabilities in secret poses a severe risk to the Internet especially if the vendor gets compromised. This has happened to multiple spyware vendors over the past ten years, raising the specter that their stockpiles can be released publicly without warning.
Breaches and hacks
Carnival Cruise settlement: US cruise line Carnival Cruise has agreed to pay $1.25 million in a multi-state settlement over its 2019 data breach. The money will be divided between 46 states and residents impacted by the incident, according to multiple state OAG officials.
CS:GO skin heist: A hacker has stolen more than $2 million worth of Counter-Strike: Global Offensive skins from a collector's private Steam inventory, including seven rare and highly-prized AWP Dragon Lore skins, considered some of the most expensive skins that CS:GO players can own. The hack is currently considered the largest theft in the game's history. [Coverage in PCGamesN]
$2,000,000+ in CS:GO skins have been hacked and stolen (some items getting moved/sold as we speak)
— ohnePixel (@ohnePixel) 4:37 PM ∙ Jun 21, 2022
this is the most expensive inventory all-time, containing the most legendary items in CS:GO history (7x souvenir dragon lores, no-star karambit, #1 blue gems)
@CSGO @Steam
General tech and privacy
New Instagram feature: Meta announced on Thursday that they are testing a new way for users to verify their age on the platform. "If someone attempts to edit their date of birth on Instagram from under the age of 18 to 18 or over, we'll require them to verify their age using one of three options: upload their ID, record a video selfie or ask mutual friends to verify their age," the company said.
Chrome 103 is out: Google has released v103 of its Chrome web browser this week. While the usual security fixes and dev/API-related changes shipped with this release, there were also loads of new features that went live for the Chrome for iOS release. Among the most important new feature was the news that Google's Enhanced Safe Browsing feature is now available for iPhone users, something that has been available for all the other Chrome users since last year.
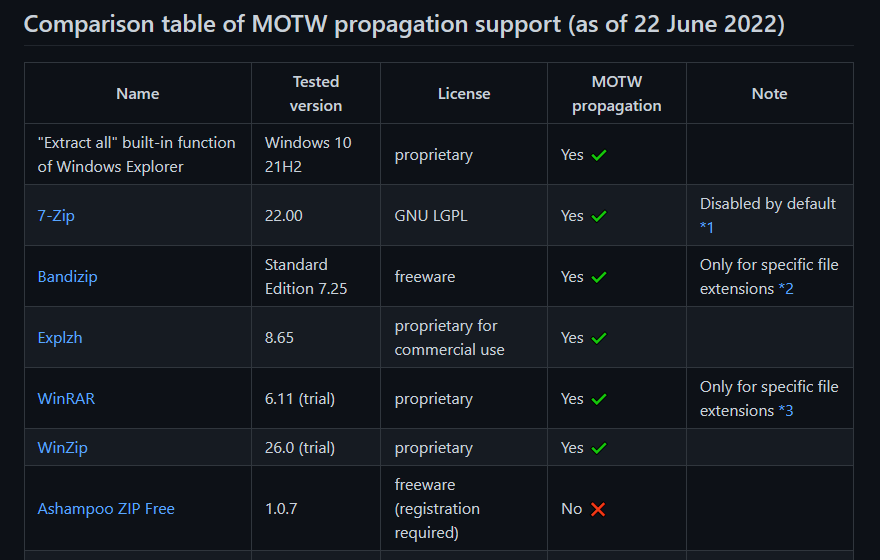
7-Zip now supports MotW: 7-Zip v22, released last week, supports Mark-of-the-Web, a Windows security feature that has been long requested by security firms and antivirus makers. 7-Zip now becomes the fifth major file archiving software on Windows to support this feature, after WinRAR, WinZip, Eplzh, and Bandizip. [Coverage in Bleeping Computer]
Government, politics, and policy
NSA and allies on PowerShell: Cybersecurity authorities from the US, the UK, and New Zealand have released a joint security advisory on the proper configuration and monitoring of PowerShell on Windows systems. A surprise to many, the three agencies didn't universally recommend removing or disabling PowerShell entirely, as there are benefits to having it enabled on a local network. The US NSA, the UK NCSC, and the NZ GCSB said that their recommendations "will help defenders detect and prevent abuse by malicious cyber actors, while enabling legitimate use by administrators and defenders."
CISA wants a cybersecurity hotline: Members of the CISA Cybersecurity Advisory Committee proposed the creation of an emergency "311" cybersecurity call line for incidents affecting small and medium-sized businesses, The Record reported on Wednesday. The idea has received positive feedback and approval on social media, although there is a fear the hotline will turn into a tech support line if not implemented correctly. Details about how this will work are still unclear, though.
Long CISA onboarding: The same CISA Cybersecurity Advisory Committee also recommended that the agency cut its onboarding process for new employees from the current 198 days to 90 days, Federal News Network reported. "The process is lengthy and difficult to navigate both internally and externally, and therefore places CISA at a tremendous disadvantage relative to private sector employers for this critical and highly sought-after talent pool," the report [PDF] states.
US spy agencies prepared to loosen hiring rules: US intelligence agencies will soon be given the green light to hire IT experts that have smoked or consumed marijuana products in the past, something that has been prohibited until now, the WSJ reported. The measure, approved unanimously by the Senate Intelligence Committee on Wednesday, comes as the CIA, NSA, and other cybersecurity agencies have been struggling to find IT talent as many are disqualified out of the blocks because they consumed marijuana in previous months or in previous stages of their life. As marijuana has become legal in 19 US states and the District of Columbia, this new loosened hiring policy was a long time coming, although active marijuana consumption during government employment is still prohibited.
US bill on privacy and data transfers: A bipartisan group of US senators has proposed a new bill this week that would ban the sale or transfer of private information belonging to US citizens to foreign countries considered a national security risk, such as China or Russia. The new bill is named the Protecting Americans' Data from Foreign Surveillance Act and was sponsored by Senator Ron Wyden (D-Ore), Senator Cynthia Lummis (R-Wyo), Senator Sheldon Whitehouse (D-RI), Senator Marco Rubio (R-Fla), and Senator Bill Hagerty (R-Tenn).
More NSO Group drama in Europe: A lawyer from Israeli spyware vendor NSO Group told EU officials this week that at least five EU member countries have bought the company’s hacking tools. The executive, NSO Group's General Counsel Chaim Gelfand, was answering questions at a European Parliament committee looking into the use of spyware in Europe. Gelfand did not provide the names of the countries and promised to get back to EU officials with an official number of member states who used its tools.
Lithuania DDoS alert: The Lithuanian National Cyber Security Center has issued an alert about an increase in DDoS attacks targeting local websites. According to the agency, most of the DDoS attacks are directed against public authorities, transport, and financial sectors, and the attacks have caused temporary disruptions to services. The attacks came as pro-Russian hacktivist groups announced plans to launch DDoS attacks against Lithuanian websites after the country said it wouldn't allow trains carrying Russian sanctioned goods to pass through its territory to Russia's Kaliningrad enclave.
Other LT🇱🇹 targets by another group
— SwitHak (👁) (@SwitHak) 9:15 PM ∙ Jun 21, 2022
Spotted first by @Cyberknow20
Source
↘️
Cybercrime and threat intel
Conti infrastructure goes down: After news that the Conti gang was preparing to disband into smaller operations last month, Conti infrastructure has finally gone down for good, confirming earlier reporting.
🌐 After 28 days without any new victims, most of Conti #Ransomware infrastructure is down 🚨
— DarkFeed (@ido_cohen2) 8:24 AM ∙ Jun 22, 2022
This is the end? or a new start? 🧐
#Conti
IT Army of Ukraine: Cyber defense researcher Stefan Soesanto has published a comprehensive report [PDF] on the activities of the IT Army of Ukraine; the hacktivist group put together with duct tape by the Ukrainian government shortly after Russia's invasion. The report deals with how the group selects its targets, gathers data for future operations, how members coordinate, and tools used for the attacks. [Additional coverage in Cyberscoop]
Vulnerabilities used by ransomware gangs: Tenable has a report out on the ransomware ecosystem. The report includes a list of 78 vulnerabilities exploited by ransomware groups for their attacks.
Search Marquis: Broadcom's Symantec team is reporting a rise in instances of Search Marquis, a browser hijacking malware strain that targets macOS users.
@Apple Safari is often hijacked by Search Marquis, so when one clicks on a hot link in an email message it does not go to that linked url page, but to a blank Search Marquis search box. Hard to get rid of too.
— kppotatoes (@kppotatoes) 1:00 AM ∙ Jun 15, 2022
VMWare warning: CISA and the US Coast Guard Cyber Command said in an advisory on Thursday that VMWare Horizon and VMWare Unified Access Gateway (UAG) are still being actively attacked using the old Log4Shell vulnerability disclosed last year. CISA said attacks had been spotted from cybercrime and state-backed groups alike. The warning also comes as Cisco Talos issued a similar warning earlier this week about the AvosLocker ransomware gang using Log4Shell to compromise VMWare UAG systems.
Scalping bots hit Israeli government sites: In a report on Thursday, security firm Akamai said that it detected several scalping bots targeting MyVisit, the appointment scheduling platform used by many Israeli government offices. Akamai says that these bots have been filling government appointment slots at various agencies and then reselling the slots on the dark market for a profit, with some slots going as much as $100.
RSocks gang: Brian Krebs has published an exposé on the people running the RSocks rent-a-proxy service, seized by the FBI and US DOJ earlier this week.
Malware technical reports
Emotet update: The Emotet malware has returned to deploying an SMB spreader module to allow it to move laterally across an infected network.
Conti report: Group-IB has a report on the activities of the Conti ransomware cartel based on their leaked chats. The research dives deep into the history and major milestones of one of the most aggressive and organized ransomware operations, which, according to Group-IB, has hit at least 850 organizations across the world.
SUAVEEYEFUL: Greek security researcher Anastasios Pingios has published an analysis of SUAVEEYEFUL, a CGI software implant for FreeBSD and Linux. The malware was developed by the Equation Group (believed to be the US NSA) and was used to spy on the email traffic of the Chinese MFA and the Japanese Waseda Research University in the early 2000s. The implant's existence was revealed during the ShadowBrokers leak in 2017. The leaked version targeted MiraPoint email products specifically.
APTs and cyber-espionage
Chinese APT: Check Point has published a report on a Chinese APT, which they believe has possible ties to the Tropic Trooper (KeyBoy) threat actor. The CP report focuses on the group's new malware strain, named Nimbda, a malware loader coded in the Nim programming language, as well as a new variant of the Yahoyah trojan, focused on collecting information about local wireless networks.
Calisto: Sekoia has a report out on Calisto—the Russian threat actor that Google TAG tracks as Cold River—and which has been targeting Western NGOs, think tanks, and the defense sector. Sekoia reports on this group's use of Evilginx, a tool that allows it to set up reverse proxies on phishing pages to intercept authentication cookies and bypass 2FA.
Bronze Riverside and Bronze Starlight: Cybersecurity firm Secureworks said in a report on Thursday that two Chinese APT groups—Bronze Riverside and Bronze Starlight—have been engaging in a coordinated campaign to steal intellectual property from their victims and then deploying ransomware as a cover-up for their intrusions. Bronze Riverside, also known as APT41, has been focused on Japanese companies, in particular.
Lyceum: ClearSky said it discovered new malware associated with the Iranian SiameseKitten (Lyceum) group. The malware is dropped by a PDF file claiming to contain info about drone strikes conducted in Iran. It installs a reverse shell, and ClearSky says the malware is signed using a fake Microsoft certificate that is also used by a variety of other Iranian groups, such as Phosphorus.
Russia's cyber operations: Microsoft has published an updated version of its report [PDF] describing Russia's cyber operations since its invasion of Ukraine. The report—an update to a previous version released in April—details destructive cyberattacks within Ukraine, network penetration and espionage outside Ukraine, and cyber influence operations targeting people around the world.
Russian government agencies linked by Microsoft to influence operations
— Catalin Cimpanu (@campuscodi) 4:01 PM ∙ Jun 22, 2022
Vulnerabilities and bug bounty
MEGA-awry: The MEGA file-sharing service has released fixes this week for a set of vulnerabilities that could have allowed threat actors to decrypt customer files. The issues, named MEGA-awry, were discovered by academics from ETH Zurich and are bugs in the company's various encryption algorithms, which MEGA uses to encrypt customer files before syncing them to its servers. In a blog post on Wednesday, MEGA said it was not aware of any user accounts being compromised by this attack.
Infosec industry
Chain-bench: Cloud security firm Aqua Security has open-sourced a supply chain auditing tool named Chain-bench.
Ukraine DDoS protection: Radware has announced that it will provide pro-bono DDoS mitigation services to the Ukrainian government.
FLOSS v2.0: Mandiant has released v2 of FLOSS, a tool the company's analysts have used to deobfuscate strings found inside malware binaries.
Some in-house news: This week, Risky Business Media launched a third podcast under the Risky Business brand. Named Seriously Risky Business, this is a weekly show discussing the topics of our eponymous newsletter, and will be hosted by Patrick Gray and Tom Uren. You can listen to the first episode here. New episodes will be available via the same RSS feed of the Risky Business News podcast, the audio version of this newsletter. The main Risky Business podcast, presented by Patrick and Adam, remains available via its separate RSS feed.




