Risky Biz News: Google Search and Ads have a major malware problem
In other news: LockBit gang leader is a big drama queen; Magento store owners f*** around and find out; AMD security patch disables CPU cores.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Don't get me wrong. I know that it's somewhat common knowledge to many people that Google search results or the ads that are intermingled with the results can often lead to malware or phishing sites. This has been a de-facto threat vector for anyone surfing the internet for the past two decades.
This way of delivering malware is often referred to as "SEO poisoning" or "SERP poisoning," where SEO stands for search engine optimization and SERP stands for search engine results page.
Over the years, several cybercrime operations have made SEO/SERP poisoning their preferred way of delivering their malware. Typically, it would be the gangs specialized in cryptomining which often preferred this method, usually by hiding their payloads in pirated software or software license cracks.
SERP/SEO poisoning was happening, but it wasn't everyone's go-to method for their operations. That honor has always gone to email-based delivery channels. Spear-phishing, mass-phishing, and malspam have dominated infosec reports over the past decade, and for good reasons. Email security standards sucked, email security solutions were simplistic, and email spam delivery was cheap.
But that tide is slowly shifting, and since late 2021, a trend has been emerging in the cybercrime ecosystem, with many operations dipping their toes back into SEO/SERP poisoning as a distribution tactic, either a replacement or a companion for classic email channels.
Throughout 2022 and early 2023, we've had Gootkit/Gootloader, IcedID, BatLoader, PrivateLoader, NullMixer, FakeCrack, RedLine Stealer, Rhadamanthys Stealer, Vidar Stealer, Yellow Cockatoo, VagusRAT, MasquerAds, and loads loads more testing or fully embracing SEO/SERP poisoning for their operations.
More on this from Patrick Schläpfer, a malware analyst at HP Wolf Security, who will also have a report out on Wednesday on another new SEO/SERP poisoning, this time distributing the Vidar Stealer via websites mimicking Audacity, Microsoft Teams, Discord, and Adobe, all promoted through Google ads.
"Since November 2022, we've seen a surge of malware distributed through malicious search engine adverts, rather than traditional spam, with multiple threat actors currently using this technique. Attackers are imitating the websites of popular software projects to trick victims into infecting their computers and buying search engine adverts to drive traffic there. The fake domains closely resemble the legitimate ones, making it difficult to recognize the adverts as malicious. For example, we found 92 domains typosquatting popular software products likely used to distribute IcedID, suggesting a growing focus on this delivery mechanism among threat actors."
The sudden rise in SEO/SERP poisoning attacks also caught the eye of the FBI's IC3 division, which put out an alert [PDF] trying to warn consumers of the rising threat.
There are many reasons why SEO/SERP is back. Many have been discussed in this thread. Yes, email security products are much more advanced now. Yes, running an SEO/SERP poisoning campaign is much cheaper than renting a spam botnet and expensive coders to make sure your malspam dodges email filters. Yes, online advertising companies (including Google itself) have fewer security checks to pass than a properly configured modern email security gateway. Yes, the proliferation of ad-blocking technologies has forced many ad companies to lower their standards and close their eyes to obvious malicious behavior. Yes, online ads can be used to target only a particular set of users with your malware, something that email was never accurate at.
These operations are back in bulk. If you're a malware researcher, it's hard not to see an obvious shift in malware distribution trends these days.
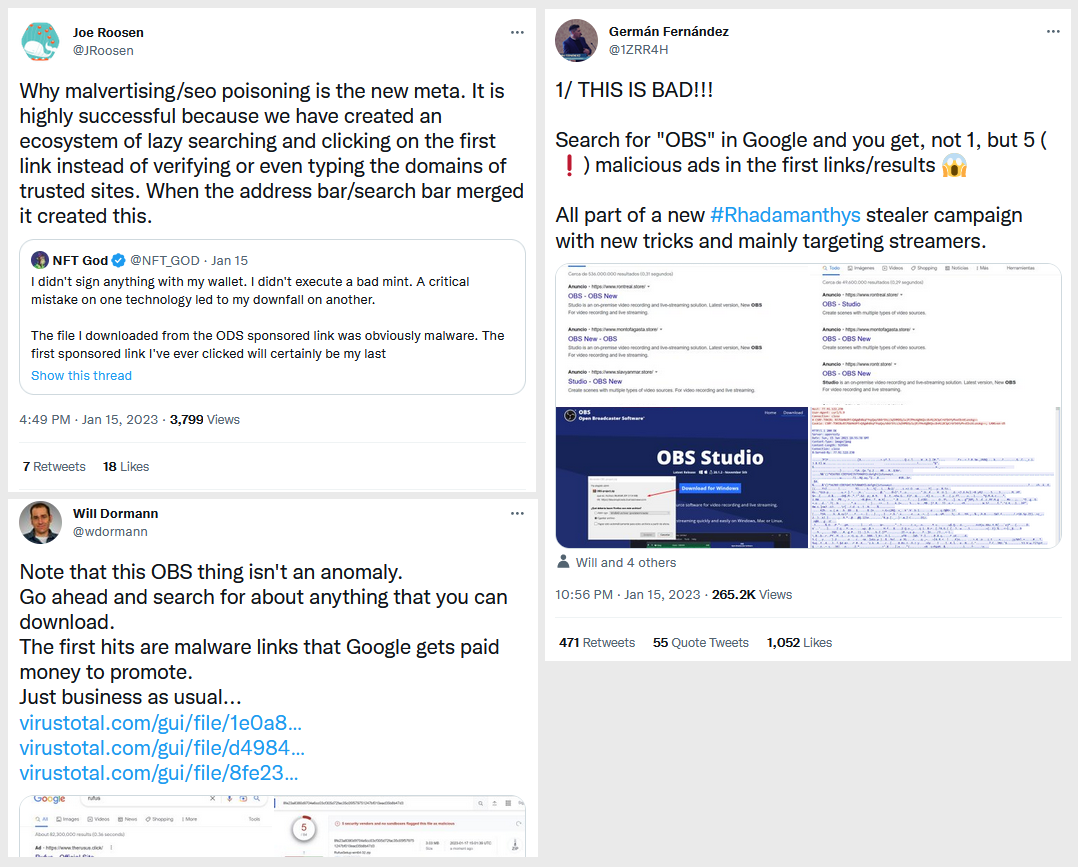
Primarily because of its dominance in both online search and ads, Google hosts most of these campaigns.
The most annoying part of all of this is that Google's support and security teams appear to have been caught on the back foot and are completely unprepared for what's currently going on. Both security researchers and companies who had their brands abused say they've found it difficult to get Google to act and remove the malicious content from search results, a situation that invites more abuse for the foreseeable future.
Breaches and hacks
Hacked Harmony funds move: North Korean hackers have moved and laundered more than $63.5 million worth of Ether from funds stolen in June last year from the Harmony bridge platform. The stolen funds were laundered and then deposited in accounts at cryptocurrency platforms Binance, Huobi, and OKX. Binance and Huobi froze a small portion of the funds, but the bulk is still under the hackers' control. The hack is believed to have been carried out by the Lazarus Group, a group of government-backed North Korean hackers.
DNV ransomware attack: Norwegian IT company DNV has confirmed that the cybersecurity incident that forced it to shut down its ShipManager smart fleet management platform last week was—just as everyone suspected—a ransomware attack. The company says the incident impacted 70 of its 300 customers and that ShipManager was down for only 1,000 vessels of the total 7,000 ships that are managed via the software. DNV says it's still working to restore servers and that vessels can still use their onboard ShipManager software in offline mode.
Grafana Labs incident: Grafana Labs says it was impacted by CircleCI's recent security incident and that two of its GPG keys were exposed via their CircleCI integration, keys they have now changed.
"Following a thorough review, we have not identified any signs of suspicious activity and we believe, with a high level of confidence, that none of our systems or code are or have been at risk of compromise."
Government, politics, and policy
Iran's new mobile surveillance system: CitizenLab researchers have received documents that detailed the Iranian government's efforts between 2018 and 2021 to implement state-controlled surveillance capabilities inside the networks of local mobile operators, including capabilities that would allow the government full access to backend systems. This allegedly includes access to billing systems, SIM management, and traffic, call, and SMS history. CitizenLab said this system was being built using technology acquired from foreign companies, such as Russian company PROTEI, UK-based Telinsol, and Canadian company PortaOne. CitizenLab says it's unclear if this system has been built or deployed.
"The CRA's Legal Intercept system uses APIs to integrate directly into mobile service providers' operational systems, including acquiring detailed data on service ordering, service fulfillment, and billing history stored in the service provider data warehouse. Any new, termination, or change request for a user's SIM card must be validated by the CRA, using the API from the mobile provider to request approval from the CRA prior to enacting the change."
Myanmar surveillance: Israeli company Cognyte sold interception spyware to a Myanmar state-backed telecommunications firm a month before the nation's February 2021 military coup. The deal is currently being investigated by Israeli prosecutors, as defense exports to Myanmar were banned back in 2017. [Additional coverage in Reuters]
Hacked data flooding UK courts: The Bureau of Investigative Journalism has a report out on how many cases in UK courts revolve around data and evidence obtained with the help of hacker-for-hire services.
"The case has included allegations that a former Metropolitan Police officer hired Indian hackers and that lawyers from a top City firm held a secret 'perjury school' in the Swiss Alps to prepare false witness testimonies about how they got hold of illegally obtained information."
FBI looking at Chinese-made cranes: The 2023 National Defense Authorization Act (NDAA) that was passed by Congress in December includes a somewhat strange provision that mandates four government bodies to conduct a cybersecurity assessment of foreign cranes operating in US ports. The study, which needs to be conducted by the Maritime Administrator, Homeland Security, the Pentagon, and the Cybersecurity and Infrastructure Security Agency, must be completed by late December 2023 and submitted to the Senate Commerce and Armed Services committees and House Transportation and Armed Services committees. [Coverage in CSO Online, non-paywalled link here]
Ukraine report on Russian conflict and use of cyber: A joint report authored by the Ukrainian Economic Security Council, Ukraine's State Service of Special Communications and Information Protection (SSSCIP), the Strategic Communications Office of the Secretariat of the Commander-in-Chief of the Armed Forces of Ukraine, and experts from the TRUMAN Agency has found "a clear connection between cyberattacks, conventional attacks and information attacks" carried out by Russia during the past year, attacks that correlate with Russia's concept of hybrid warfare. Ukrainian officials echo the conclusion of three Microsoft reports from last year [April, June, and December], which also claimed there was some sort of coordination between Russian kinetic military operations and its cyber operations. Ukrainian officials claim that while coordination is widespread, it is not an absolute constant rule across Russia's operations.
"Cyberattacks are entirely consistent with Russia's overall military strategy. Moreover, cyber-attacks are often coordinated with other attacks: conventional attacks on the battlefield and information-psychological and propaganda operations. This effect was demonstrated in the autumn and winter of 2022, when, after a series of cyberattacks on the energy sector, Russia launched several waves of missile attacks on energy infrastructure. While simultaneously launching a propaganda campaign to shift responsibility for the consequences (power outages) to Ukrainian state authorities, local governments, or large Ukrainian businesses."
Sponsor section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year, in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
Cybercrime and threat intel
Phisher detained in Ukraine: Ukraine's Cyber Police has detained two suspects who orchestrated phishing campaigns aimed at stealing banking credentials. Officials said the two suspects sold the data on Telegram channels and on the dark web. The two suspects were identified as a 21-year-old native of the Mykolaiv region and his roommate.
Mallox interview: Threat intelligence analyst Marco A. De Felice has published an interview with the operators of the Mallox ransomware, also known across time as TargetCompany and Fargo. The gang claims to have infected "thousands" of victims since they began operations in June 2021.
LockBitSupp profile: Threat intelligence company Analyst1 has spent a year undercover interacting with the LockBit ransomware gang and its alleged leader, an individual who goes online as LockBitSupp. The LockBit gang began operations in 2019 and has dominated 2022, becoming the largest and most active ransomware group after the downfall of several rivals in late 2021. However, despite their success last year, Analyst1 researcher Jon DiMaggio says that the gang's leader is slowly chipping away at the gang's own reputation and antagonizing a large portion of the cybercrime underground through aggressive comments and smear campaigns against other rivals. DiMaggio says that even if LockBitSupp has disagreements, they still maintain a direct line of communication with their competitors, showing that in at least some topics, the major ransomware cartels like to discuss and coordinate responses and operations. These and many other more are in the company's extensive report (and the must-read infosec report of the week) on the LockBit gang.
2022 payment card fraud landscape: Recorded Future has published its yearly report on the payment card fraud landscape and says that during 2022 more than 59.4 million compromised payment card records were posted for sale across dark web carding shops. Recorded Future says the number is down from the 96 million payment card records that were posted for sale a year before, in 2021. In addition, the company says it also tracked more than 1,500 domains used for malicious Magecart scripts planted on more than 9,200 online stores.
Package repos attacks: DevSecOps company Sonatype says it tracked 422 malicious packages uploaded on the npm repository in the month of December 2022 and 58 similar packages uploaded on the PyPI portal. Most of the packages leveraged typosquatting or dependency confusion to infect their targets and focused on data exfiltration—with a few exceptions here and there.
GitHub Codebases abuse: Just like any respectable cloud service, the new GitHub Codebases IDE can be abused for malware delivery. Congratulations!
Magento store owners being stupid: SanSec is reporting that owners of Magento and Adobe Commerce stores have bypassed a recent security patch and re-exposed their stores to attacks. The incidents refer to a Magento security update from February 2022 for a vulnerability tracked as CVE-2022-24086. The vulnerability allows threat actors to place "malicious" orders on unpatched stores that abuse the store's emailing template feature to take over the store. Attacks exploiting this vulnerability began at scale in November 2022. Almost a year later, Sansec is now reporting that some Magento store owners have applied the patch, which disabled the store emailing feature, but later manually re-enabled the email template feature, which then led to their stores getting hacked.
"Sansec discovered that several vendors and agencies are actively bypassing this security fix, and some patched stores actually got hacked."
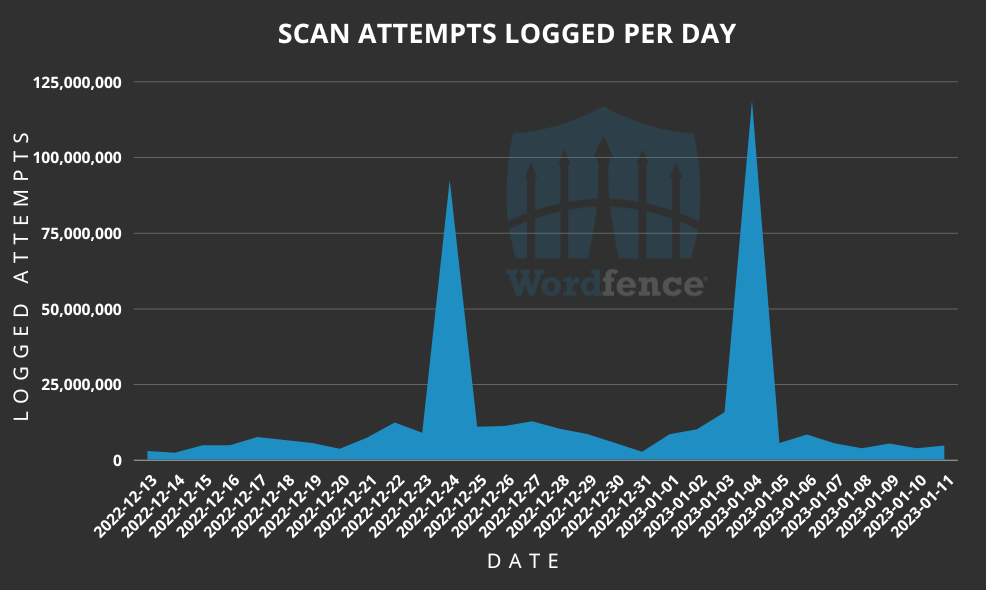
WordPress attacks: Wordfence says it recorded spikes in attacks targeting WordPress sites over the Christmas and New Year holidays, with attackers trying to compromise WordPress sites using exploits for "ancient" vulnerabilities. The activities spikes were very noticeable, and Wordfence says these spikes aren't uncommon because "systems are not as closely monitored" during holidays. Final payloads included common web shells, typically used to take control over hacked websites.
Malware technical reports
Free decrypter: Avast has released a free decrypter for the BianLian ransomware after its researchers identified a flaw in the malware's encryption routine. The ransomware was first spotted in August 2022 and was used primarily in targeted attacks against enterprises. Not to be confused with the Android dropper from 2018, which is a totally different thing.
MobaXtermPersonal backdoor: The HashRun security team has published a technical write-up on the MobaXtermPersonal malware. Not to be confused with the MobaXterm Linux app.
APTs and cyber-espionage
Earth Bogle: Trend Micro researchers have discovered a threat actor using geo-political lures to target individuals and organizations in the Middle East and Africa. Delivery is via email spear-phishing, and the final payload is njRAT. Trend Micro has named this campaign Earth Bogle but has not linked it to any known APT as of yet.
Kasablanka: Chinese security firm QiAnXin has published a report on recent attacks carried out by the Kasablanka APT. The attacks cover a campaign that took place between September and December 2022, attacks that targeted Russian government organizations.
Vulnerabilities and bug bounty
Hack the Pentagon 3.0: The Department of Defense is preparing to hold the third edition of its Hack the Pentagon bug bounty program. The first edition was held in 2016, while the second took place in 2018. The government is now asking bug bounty platforms to sign up and host the new edition. HackerOne, Bugcrowd, and Synack previously hosted the two previous editions, according to NextGov.
AMD vulnerabilities: Chipmaker AMD has released firmware updates to fix a set of vulnerabilities found in the secure components of its CPU models. The vulnerabilities impact components like the AMD Secure Processor (ASP) and the AMD System Management Unit (SMU) and can allow threat actors to compromise the boot process and hijack operating systems. AMD says the vulnerabilities were found following a security audit. Tens of AMD CPU models were found vulnerable, including many of the company's high-end models. The firmware patches were delivered as updates to AGESA, an AMD library included in a motherboard's BIOS code. Unfortunately, the update appears to be causing issues on some CPU models, with users reporting that the update has disabled some of their CPU cores, effectively reducing their CPU's processing power.
Firefox 109: ...is out, including fixes for several security bugs. This release's main feature is the rollout of the new Manifest V3 extensions system, which Mozilla claims won't hinder the performance of ad blockers in its browser, unlike what happened on Chromium-based browsers.
CVE-2022-47966 (Zoho): Security firm Horizon3 plans to release proof-of-concept code for CVE-2022-47966, a pre-authentication remote code execution in the Zoho ManageEngine server. Zoho released a patch for this vulnerability last October.
CVE-2023-0179 (Linux): Italian security researcher Davide Ornaghi has published details about a buffer overflow vulnerability within the Linux Netfilter subsystem. A PoC is scheduled to be published on GitHub in the coming days, per the researcher.
"The exploitation could allow the leakage of both stack and heap addresses and, potentially, a Local Privilege Escalation to the root user via arbitrary code execution."
Sophos zero-day exposure: Security firm VulnCheck says that 99% of all internet-connected Sophos firewalls have still not been updated to address a zero-day that was fixed last September, tracked as CVE-2022-3236. Even Worse, VulnCheck says that roughly 4,000 out of more than 78,000 internet-connected Sophos firewalls are also too old to be patched for the same zero-day, meaning thousands of systems will remain exposed to attacks. VulnCheck says the only thing that appears to be keeping these systems safe is the lack of a public exploit that would very likely trigger a wave of mass-exploitation.
AWS CloudTrail bypass: Cloud security firm Datadog says it found a bypass in the AWS CloudTrail security tool that could be abused to bypass its API monitoring capabilities. AWS fixed the issue last October.
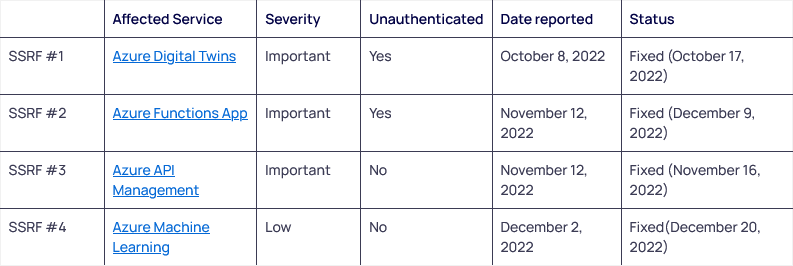
Azure SSRF vulnerabilities: Orca Security researchers have found Server Side Request Forgery (SSRF) vulnerabilities that impact four Azure cloud services, namely Azure API Management, Azure Functions, Azure Machine Learning, and Azure Digital Twins. Two of the vulnerabilities can be exploited without needing to authenticate, and the issues can be exploited to scan cloud networks for exposed systems. Microsoft fixed all issues.
Infosec industry
Some career advice: G Data malware analyst Karsten Hahn breaks down the stupid myth that you have to write and open-source malware to be a good malware analyst. TL;DR: Don't. The two are not even remotely connected, and it will most likely hurt you when trying to get a better job.
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




