Risky Biz News: Google disrupts CryptBot malware operation
In other news: Clop ransomware gang behind PaperCut attacks; Tencent software updates delivered APT malware on selected devices; AT&T email accounts hijacked for crypto-heists.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Google has disrupted the operations of CryptBot, an infostealer that has infected more than 670,000 computers across the world over the past year.
The company's legal team has filed civil lawsuits against several Pakistani nationals it believes are currently operating server infrastructure that is distributing the malware.
First spotted in 2019, CryptBot has been primarily distributed via websites advertising software cracks, pirated content, and (contaminated) updates for major software products—including Google products such as Google Chrome and Google Earth Pro.
A New York court granted Google a temporary restraining order that will allow it to take down current and future domains that are linked to CryptBot infrastructure and used to distribute the malware.
Google argued that CryptBot operators were not only impersonating its software brands to infect users, but the malware itself was also stealing the personal data of Google users.
According to technical reports[1, 2, 3, 4, 5] published in previous years, CryptBot can steal sensitive information from infected computers, such as browser-stored credentials, browser authentication cookies, browser-stored payment card details, cryptocurrency wallet information, and screenshots of the infected system.
This data is collected from infected hosts, packed into a ZIP, and uploaded to the CryptBot operator's command and control server. From there, the stolen data often makes its way to underground marketplaces like Genesis, where it is put up for sale.
In a 2021 report, Mandiant said it saw CryptBot-stolen data being leveraged in intrusions by APT29, a cyber-espionage unit inside Russia's Foreign Intelligence Service, also known as the SVR.
Google's legal action against CryptBot marks the company's second such action after the company also used its lawyer squad to disrupt the operations of the Glupteba botnet last year.
Breaches and hacks
AT&T cryptocurrency hacks: A hacker group is exploiting an API vulnerability in AT&T's system to gain access to customer email addresses in order to hijack cryptocurrency exchange accounts. AT&T has confirmed the attacks. The company told TechCrunch the API vulnerability allowed the hackers to generate "secure mail keys" that granted access to any user email without needing to know the account's password. TechCrunch's source claims the hackers have used their access to steal between $15 and $20 million—although this could not be independently confirmed at the time of writing.
Merlin crypto-heist: A hacker has stolen more than $1.82 million worth of cryptocurrency assets from decentralized exchange (DEX) Merlin. The attack took place during the company's three-day event sale of the new MAGE token and after it also touted a recent security audit claiming no security flaws were found in its platform. [Aditional coverage in CoinDesk]
General tech and privacy
Windows 10 EoS: Microsoft says that Windows 10 version 22H2, which was released in October of last year, will be the last major version of the Windows 10 operating system. With the announcement, this means the official End-of-Support (EoS) date for Windows 10 is now officially set for October 14, 2025. After that date, Microsoft will stop delivering monthly security updates.
ChromeOS adds new security features: Google has announced new security features for its ChromeOS operating system. The new features include support for a Verified Boot mechanism, an on-by-default policy to block the execution of any untrusted executables, and a settings section from where users can manage access to their device camera and microphone. In addition, ChromeOS also includes a DLP feature known as ChromeOS Data Controls, through which system administrators can block actions that can lead to data theft, such as printing, screen-sharing, copy-pasting, and screen-capturing capabilities.
Fastly launches a CA: Something that we missed in February was that CDN provider Fastly launched its own in-house certificate authority. Named Certainly, the new CA will issue certificates to Fastly's own customers so they won't depend on a third-party service. The novel thing is that all Certainly certificates will have a maximum 30-day, the shortest default in the CA industry (by a long mile).
More SHA-1 deprecations: Google will deprecate support for SHA-1 signatures during the TLS handshake. The Chrome browser maker says this "removes the ability for a future attacker to exploit some sort of collision in SHA1 to impersonate a server."
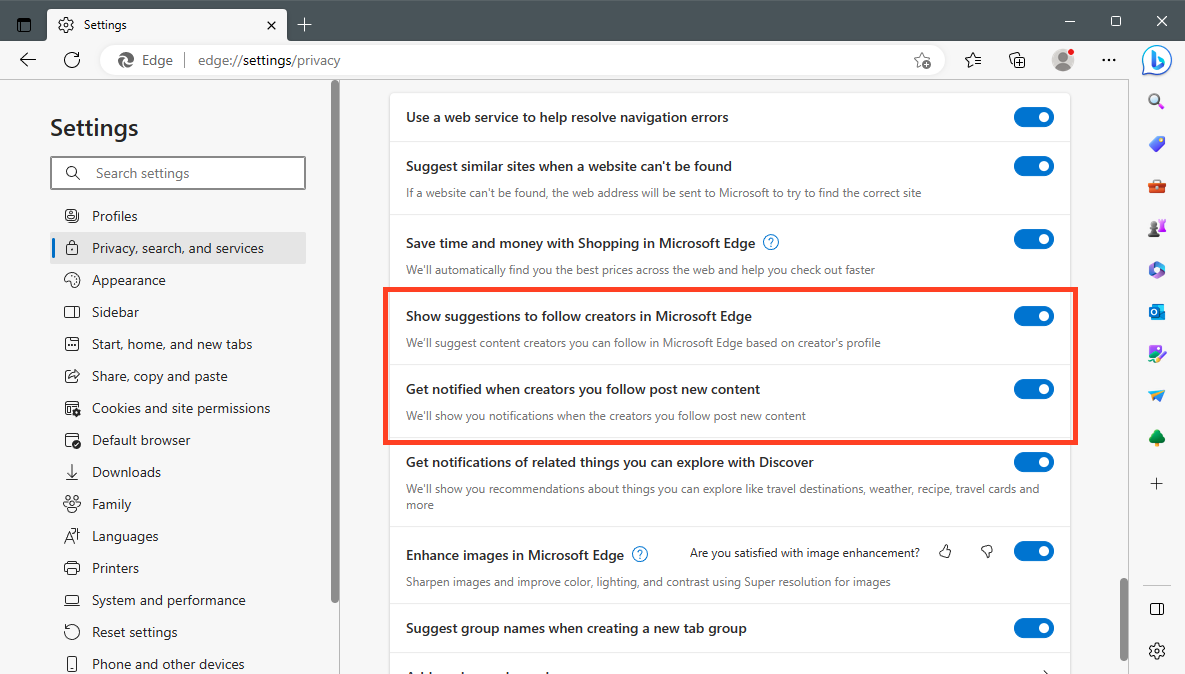
Edge browsing history leak: Microsoft's Edge browser is sending the URLs of web pages users are visiting to the Bing search engine API. The leak only affects recent versions of the browser and was linked to a feature that Microsoft added to Edge last year that lets users get notifications when their favorite content creators post new content on YouTube. Users on Reddit, where the leak was initially discovered, recommend disabling the feature until Microsoft fixes the leak. The feature is enabled by default and can be found in the Privacy section of the Edge browser's settings panel. [Additional coverage in The Verge]
Government, politics, and policy
Brazil bans Telegram: A Brazilian judge has temporarily suspended access to the Telegram app in the country. Government officials say Telegram failed to cooperate with a law enforcement investigation and provide information to police about neo-Nazi chat groups hosted on its service. Brazilian ISPs are already blocking access to the app, and Apple and Google were ordered to block access to the app in their stores for Brazilian users. [Additional coverage in ABC News]
US National Cybersecurity Strategy: The White House is expected to announce a roadmap to implement its new National Cybersecurity Strategy later this summer, Acting National Cyber Director Kemba Walden said this week at the RSA security conference. [Additional coverage in CybersecurityDive]
Hawaii censorship law will go: The US state of Hawaii is preparing to repel a Cold War-era law that can allow the governor or a simple mayor to suspend all "electronic media transmissions" during a state crisis. Lawmakers say they fear the law's generic language could lead to situations where state officials could abuse it to suspend all electronic communications, including internet content such as social media posts and emails. The push to have the law repelled has been led by the Hawaii Association of Broadcasters, which fears the law could be abused to silence media outlets. Hawaii lawmakers say the law has never been invoked. [Additional coverage in the Associated Press]
FBI aiding Ukraine collect digital evidence: Speaking at the RSA security conference this week, an FBI official said the agency is aiding the Ukrainian government in collecting and processing physical and digital evidence of war crimes committed by Russia's invading forces. Evidence ranges from DNA samples to fingerprints and digital artifacts related to cyberattacks on civilian infrastructure. One way the FBI is doing this is to work as a liaison and help Ukrainian investigators obtain data from US providers. [Additional coverage in CyberScoop]
EU Digital Services Act: The European Union has named 19 online platforms that have more than 45 million monthly active users across the EU and will fall under the scrutiny of its upcoming Digital Services Act. The new regulation enters into effect on August 25 and mandates that large online platforms have to crack down on illegal and harmful content or face huge fines. The list includes:
- Alibaba AliExpress
- Amazon Store
- Apple AppStore
- Bing
- Booking.com
- Google Play
- Google Maps
- Google Search
- Google Shopping
- Snapchat
- TikTok
- Wikipedia
- YouTube
- Zalando
Surprisingly, it does not include any adult websites, nor the likes of Discord and Twitch.
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
Cybercrime and threat intel
Data trader arrested in Ukraine: Ukraine's Cyber Police has detained a 36-year-old man from the city of Netishyn for selling stolen databases online. The suspect is accused of trading the data of more than 300 million users from several countries for prices ranging from $500 to $2,000. Officials say that during the house search, the suspect obstructed the actions of law enforcement officers and also injured a policeman.
Avaya Aura exploitation: Cybersecurity firm Deepwatch says threat actors are exploiting an unauthenticated remote code execution vulnerability in Avaya Aura, an enterprise customer service solution for managing IP phones. The attacks began in February after security firm AssetNote published a write-up detailing vulnerabilities in the platform. Deepwatch says it observed instances where attackers exploited the bugs to install web shells and a log wiper on Avaya Aura servers. The vulnerabilities were fixed in Avaya Aura Device Services version 8.1.4.1.40 [PDF].
Clop linked to PaperCut attacks: Microsoft's security team has linked the recent attacks on PaperCut print management servers to the Clop ransomware gang. Microsoft's attribution confirms a report from earlier this week from HuntressLabs that also found connections between the PaperCut attacks and Clop infrastructure. Over the past two years, the Clop gang has made a name for itself by exploiting enterprise gear, gaining access to corporate networks, stealing sensitive data, and then extorting companies with threats to publish the stolen files. Prior to attacks on PaperCut servers, the Clop gang also targeted Accellion and GoAnywhere file-sharing servers, and the group used the stolen data to extort hundreds of companies.
FIN7 attacks on Veeam backup servers: WithSecure says it saw the FIN7 cybercrime group carry out attacks against Veeam backup servers at the end of March. The attacks exploited a vulnerability tracked as CVE-2023-27532, and they began days after a security firm published a proof-of-concept exploit.
"WithSecure Intelligence has so far identified two instances of such attacks conducted by FIN7. As the initial activity across both instances were initiated from the same public IP address on the same day, it is likely that these incidents were part of a larger campaign. However, given the probable rarity of Veeam backup servers with TCP port 9401 publicly exposed, we believe the scope of this attack is limited."
Facebook malvertising: Guardio Security has discovered a Vietnamese threat actor who, for the past few months, has been using malicious Facebook ads to lure Facebook users to malware-infected websites. Guardio says the threat actor has been very successful and has infected more than half a million victims across the world. Guardio says it worked with Facebook's security team and has had the threat actor's ads removed.
DDoS attacks double in India: Netscout researchers say the number of DDoS attacks against Indian targets has doubled since the start of the year. The company credits the attacks to campaigns carried out by pro-Kremlin groups Killnet and Anonymous Sudan.
"These attacks have largely targeted airports, among other key industries throughout the nation. Anonymous Sudan has also released a list of 6 new targets, including the largest bank in India, that provides evidence that this is just the beginning of this lashing of DDoS activity."
Misconfigured registries: Aqua Security says they found thousands of misconfigured registries and artifact repositories that were allowing anonymous access to enterprise systems containing source code, authentication keys, and other sensitive artifacts. In total, Aqua says the registries exposed over the internet more than 250 million artifacts and over 65,000 container images.
- A registry is a central location for storing and managing packages.
- A repository is a collection of packages within a registry.
- An artifact management system is a tool for managing binary files such as JAR files.
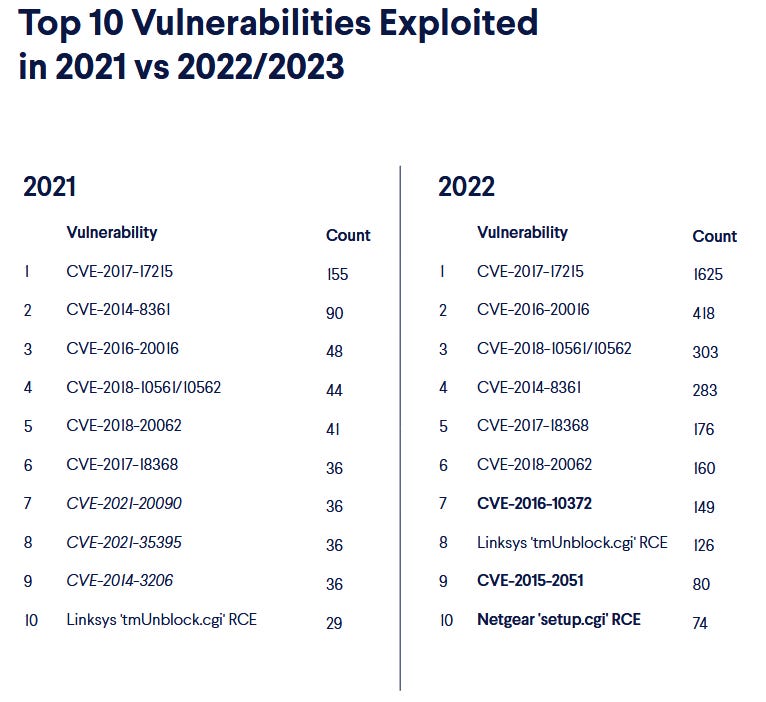
IoT botnet activity: Cybersecurity firm CUJO says that IoT botnets exploited 55 vulnerabilities in IoT devices last year, more than twice as in 2021. The most abused vulnerability last year was CVE-2017-17215, an RCE in Huawei routers, with exploits for it being found in 96% of the IoT malware binaries that CUJO analyzed last year. The most active botnet last year was Zerobot, which tried to exploit 22 different vulnerabilities last year.
Malware technical reports
EvilExtractor: Netresec has a report looking at the network activity generated by an infection with the EvilExtractor infostealer.
RTM Locker Linux variant: Uptycs security researchers have discovered a Linux version of the RTM Locker ransomware, initially spotted earlier this year by Trellix.
UNIZA ransomware: Fortinet has published an analysis of UNIZA, a new ransomware strain spotted this month.
HiddenAds: McAfee says it found 38 apps on the official Google Play Store that were infected with the HiddenAds malware. The apps posed as Minecraft-related content and were downloaded more than 35 million times.
Sponsor Section
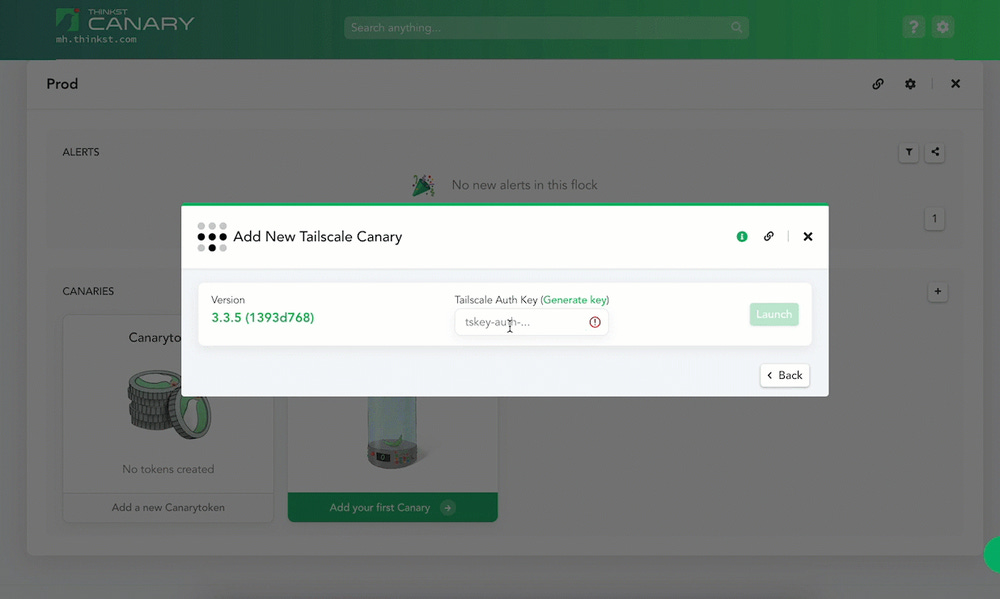
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. The company has launched a new type of canary token that can help companies detect intruders on their Tailscale VPN networks.
APTs and cyber-espionage
LoneZerda: In its quarterly APT activity report, Kaspersky says it saw new activity from LoneZerda, a Libyan cyber-espionage group. Kaspersky notes that the group is now targeting individuals outside Libya, primarily targets in the Middle East.
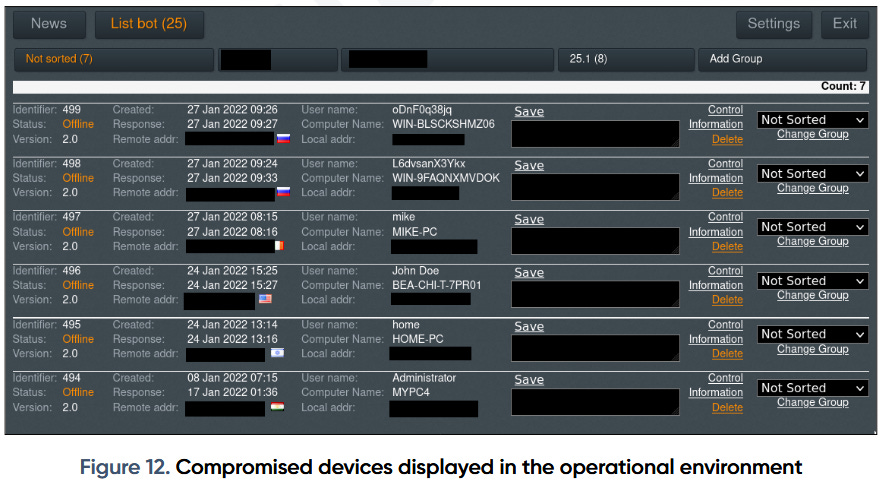
Nomadic Octopus: Prodaft researchers have published a report on Paperbug, a cyber-espionage campaign carried out by suspected Russian-speaking group Nomadic Octopus and which targeted entities in Tajikistan. According to Prodaft, known compromised victims included high-ranking government officials, telcos, and public service infrastructures. Compromised devices also included OT devices, besides your typical computers, servers, and mobile devices. In typical Prodaft fashion, the company also gained access to one of the group's C&C server backend panels.
Charming Kitten's BellaCiao: Bitdefender has published a report on BellaCiao, a malware strain used by the Charming Kitten APT group in attacks against targets in the US, Europe, Turkey, and India.
Tonto Team: AhnLab published a report on new attacks by the Tonto Team targeting Asian countries with the Bisonal malware.
Evasive Panda: Cybersecurity firm ESET says it observed incidents where software updates for Tencent's QQ app delivered a Chinese APT group's malware on selected user devices. The infections took place in January 2022, and ESET says the majority of victims are members of an international NGO that operates in two Chinese provinces. ESET linked the attacks to Evasive Panda, a Chinese APT group that has been active since 2012. The malware deployed in the attack is known as MgBot, and was also spotted in attacks targeting an African telco in November of last year, according to a Symantec report published last week. ESET couldn't say if the malware was deployed thanks to a compromise of Tencent's software supply chain or if Evasive Panda hijacked internet infrastructure to perform an Adversary-in-the-Middle attack.
Alloy Taurus: PAN Unit42 researchers have spotted a Linux variant of PingPull, a malware strain previously seen used by Alloy Taurus, a suspected Chinese cyber-espionage group. In addition, researchers also spotted new malware used by the group, a backdoor named Sword2033.
Operation Honey Badger: The Chinese government has engaged in a two-year-long social media disinformation campaign to portray the US as an "irresponsible cyber power." Tracked by ASPI researchers as Operation Honey Badger, the campaign involved thousands of posts on websites like Twitter, Facebook, Reddit, VK, Tumblr, and Medium. ASPI says Operation Honey Badger began in 2021 after the US and allied countries accused Chinese government hackers (the Hafnium APT) of the massive ProxyLogon attacks that targeted Microsoft Exchange servers. ASPI researchers say that Chinese cybersecurity firms QiAnXin and PanguLabs have, at times, supported the campaign by publishing reports on "US hacking" that cited years-old evidence or contained inaccuracies. ASPI notes that as soon as these reports would go live, they'd often be picked up and promoted by Operation Honey Badger's social media accounts.
"Accounts in the network often posed as Westerners outside of China but our research geolocated some of the operators of the Spamouflage-linked accounts to Yancheng in Jiangsu Province. In addition, we show it's likely that at least some operators behind the campaign are affiliated with the Yancheng Public Security Bureau, the MPS or are 'internet commentators' hired by the Cyberspace Administration of China."

Vulnerabilities and bug bounty
PostScript interpreter vulnerabilities: Zscaler researchers have found vulnerabilities in the PostScript file interpreters of Adobe Acrobat Distiller and Apple's PSNormalize. The issues have been fixed, and Zscaler has published a technical write-up, complete with PoC exploits.
NATO finds Cisco bug: Pierre Vivegnis of the NATO Cyber Security Centre (NCSC) has discovered an XSS vulnerability in the web panel of the Cisco Prime Collaboration Deployment. Cisco says it has not seen active exploitation in the wild and is currently working on a fix.
Zyxel security updates: American networking company Zyxel has released security updates this week to fix nine vulnerabilities across several products.
Odoo security flaw: SonarSource has a write-up on CVE-2023-1434, an XSS vulnerability in the Odoo open-source business suite.
KeyCloak vulnerability: Offensity researcher Jordi Zayuelas has discovered a vulnerability (CVE-2023-0264) in KeyCloak, a Single-Sign-On solution from Red Hat. According to Zayuelas, Keycloak's user authentication was found to incorrectly authenticate requests. An authenticated attacker who could obtain a certain piece of info from a user request could use it to impersonate the victim and generate new session tokens.
Infosec industry
Acquisition news: Allurity has acquired two managed security service providers (MSSP) companies—Portuguese company CloudComputing and Swiss company Securix.
Merger news: MFA behemoth Yubico has announced plans to merge with ACQ Bure, a Swedish holding company that Yubico says it will help grow and achieve its wider market goals.
New tools—ReconAnalyzer, JSpector: Security researcher Hisxo has released ReconAnalyzer, a Burp Suite extension that leverages OpenAI for bug bounty hunting, as well as JSpector, a Burp Suite extension that crawls JavaScript files and automatically creates URLs from endpoints found inside the JS files.
New tool—BlueLiteBlocker: Security researcher Marcus "MalwareTech" Hutchins has released BlueLiteBlocker, a Chrome and Firefox extension for hiding tweets from Twitter Blue verified users.
Twitter breaks Abuse.ch: Twitter has suspended the API access for Abuse.ch, a malware-sharing and threat intel collaboration platform. Abuse.ch was using the Twitter API for its login system. The platform's administrator says they did not receive any advance notice from Twitter. Security researchers are currently unable to log into the platform and share cyber threat intelligence with the community. Abuse.ch is working on rolling out a new user authentication system.