Risky Biz News: Google discloses breach of its Fi cell service
In other news: GitHub discloses security breach; Microsoft is tracking more than 100 ransomware gangs active today; PoS malware blocks contactless transactions.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Google is notifying the customers of its Fi cell service that some of their information was exposed following a security breach at one of its upstream network providers.
Google says the intruder collected phone numbers, SIM card serial numbers, and mobile service plan details. The data appears to have been taken from a customer support system used to integrate its Fi service with the larger upstream mobile operator.
Other more personal details, such as names, ID scans, addresses, or financial information, were not compromised, Google said in an email to customers seen by RiskyBizNews.
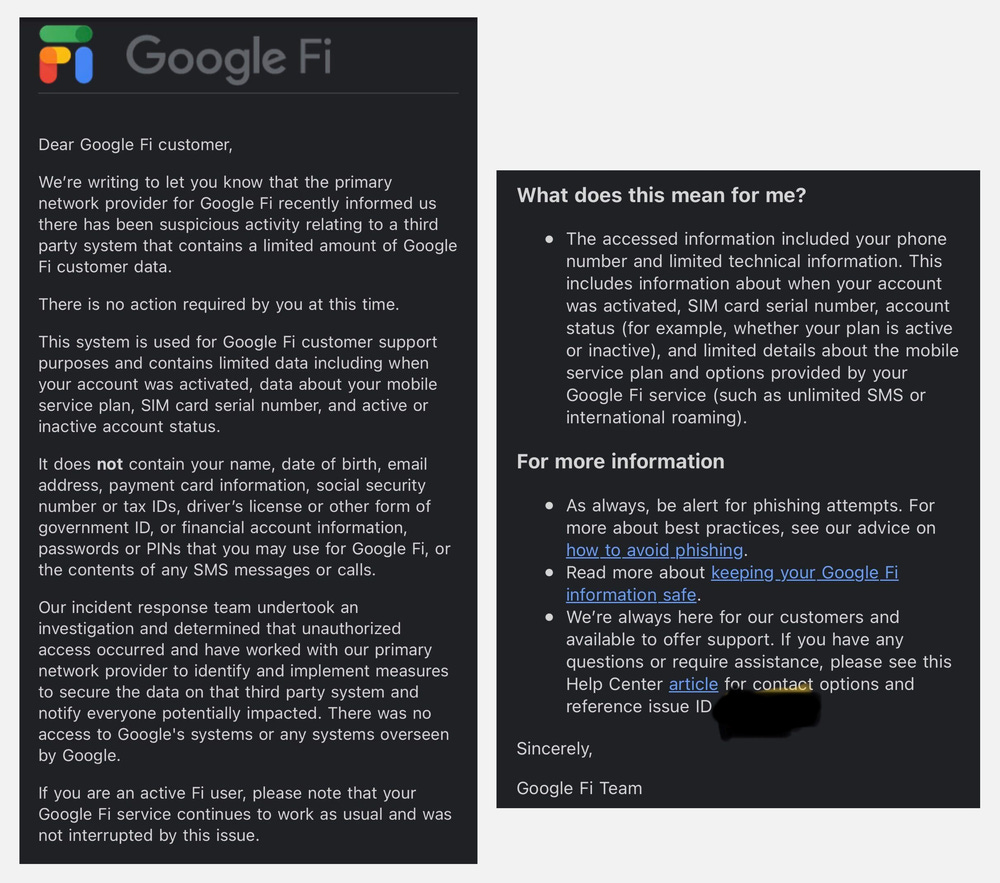
Google did not name the upstream operator by name, but its Fi service uses only two upstream providers, namely T-Mobile and US Cellular, and T-Mobile disclosed a security breach to the SEC earlier this month—so connecting the dots is definitely not rocket science.
While Google told customers they should be wary of possible phishing emails trying to leverage this incident, at least one Reddit user says the email they received from Google Fi also included an additional line notifying them that their Fi service was changed to a new SIM card as part of what looks like a SIM swapping incident. However, this scenario is currently being called into question as, per Google's email, the supposed stolen data would not have been enough to perform a SIM-swapping attack.
Breaches and hacks
GitHub breach: GitHub says that a threat actor breached internal source code repositories and stole two code-signing certificates. The breach took place last year on December 7. GitHub says the certificates were encrypted and password-protected, and as a result, they haven't seen any sign they were misused in the wild. Furthermore, both certificates were about to expire in January and February this year and will become useless to the intruder either way. The breached repositories contained the source code of the GitHub Desktop app and the GitHub Atom code editor. GitHub's security team says it did not find any unauthorized edits to the code, and both apps remain safe to use.
JD Sports incident: JD Sports, one of the largest sportswear chains in the UK, says a threat actor gained access to a system that was storing data on past customer orders. In a filing with the London Stock Exchange, the company says the personal data of more than 10 million customers who placed online orders between November 2018 and October 2020 was likely stolen. Compromised PII data includes names, addresses, email accounts, phone numbers, order details, and the final four digits of bank cards.
Yandex leak: The Yandex source code leak from last week has apparently exposed the secret sauce (1,922 factors) the company uses to classify and rank web pages, but also racial slurs.
General tech and privacy
Oracle Java licensing change: Oracle has changed Java's licensing model to a per-employee model [PDF]. Running very outdated and insecure software has now become insanely expensive. kek!
Government, politics, and policy
Ireland spyware investigation: The Irish Parliament is investigating how many companies involved in the production of spyware and surveillance products are based in the country. The government started an investigation after it was discovered that Intellexa, the maker of the Predator spyware, has two business entities registered in the country. Namely, the spyware maker's holding company, Thalestris Ltd, and a subsidiary called Intellexa Ltd have registered addresses in Dublin. According to the Irish Times, MP Barry Andrews alerted the Joint Committee on Justice and asked for an investigation to avoid the country becoming a "haven" for spyware makers.
Abraham Accords expand to cybersecurity: The Abraham Accords, a collaboration treaty between Israel, the United Arab Emirates, and Bahrain has been expanded to cover cybersecurity, according to US DHS Under Secretary Rob Silvers.
Ransomware drill in Japan: Japanese police and more than 130 Japanese tech companies held a drill on Monday that mimicked the aftermath of a ransomware attack. Authorities said the drill will last through February 9 and is meant to prepare law enforcement and IT providers for a possible attack on Japanese infrastructure before and during the G7 Summit, to be held in Hiroshima between May 19 and 21 this year.
Academia warning: The Swiss Federal Intelligence Service has published a 19-page brochure [PDF] to warn members of universities, colleges, and research institutes that they may be the target of foreign intelligence services as part of (cyber)espionage campaigns meant to steal their work.
New House cyber chief: New York Republican Andrew Garbarino has been named the new Chair of the Homeland Cybersecurity, Infrastructure Protection, and Innovation Subcommittee, part of the House Committee on Homeland Security.
Federal agencies sleeping on cybersecurity: A report from GAO, a US government agency watchdog, has found that federal agencies had implemented only 21% of the 712 cybersecurity recommendations GAO had issued since 2010, as of December 2022. The report covers recommendations related to:
- Improving the implementation of government-wide cybersecurity initiatives
- Addressing weaknesses in federal agency information security programs
- Enhancing the federal response to cyber incidents to better protect federal systems and information
This is the second GAO report dealing with how federal agencies implemented cybersecurity recommendations over the past decade. The first report, published two weeks ago, covered recommendations related to:
- Establishing a comprehensive cybersecurity strategy
- Mitigating global supply chain risks
- Addressing the federal cybersecurity worker shortage
- Ensuring the security of emerging technologies
Only 40% of GAO's 335 cybersecurity recommendations for those topics were implemented.
Sponsor section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
Cybercrime and threat intel
Vladislav Klyushin trial begins: The trial of Vladislav Klyushin, a Russian national, has begun this week in Boston, Reuters reported. Together with four other Russian nationals, Klyushin stands accused of hacking into companies and using stolen documents to make transactions on the stock market using non-public information. Authorities say Klyushin made up to $90 million from illegal trades. Klyushin was arrested in March 2021 in Sion, Switzerland, and extradited to the US in December of the same year. His four accomplices are still at large. The case is particularly interesting for two reasons. First is because one of Klyushin's four accomplices is Ivan Ermakov, a former officer in Russia's GRU military intelligence service, who is also charged in a different case for hacking and interfering in the 2016 US Presidential Election. Second is because Klyushin is the owner of M-13, a Russian IT firm and regular contractor for the Russian government.
iSpoof aftermath arrests: Dutch police have detained three suspects because of their role in a bank helpdesk fraud scheme. Officials say they detained the suspects as part of their follow-up investigation into iSpoof, a service they took down last year and which allowed users to make calls and send SMS messages using spoofed identities.
Killnet HHS warning: The US Department of Health and Human Services has issued a security advisory about the increased activity coming from Killnet, the pro-Kremlin hacktivist group. The HHS says Killnet has targeted US healthcare organizations with DDoS attacks in the past and will likely continue to do so. [PDF]
O365 campaign: Proofpoint researchers have published a report about a new campaign targeting Microsoft 365 users that aims to trick them into authorizing malicious third-party OAuth apps on their accounts. The campaign stood out because many of the malicious apps received a "verified publisher" tag from Microsoft. Microsoft says it suspended the accounts.
Malicious npm campaign: Phylum researchers have identified 102 npm libraries that contain a malicious post-install script that gathers information about the infected systems and sends the data to a remote server. The packages are listed here.
Russia's cybercrime connections: Recorded Future has published a new part of its research project into the possible ties between the Russian government and its underground cybercrime ecosystem. Part one was published in September 2021.
"It remains highly likely that Russian intelligence, military, and law enforcement services have a longstanding, tacit understanding with cybercriminal threat actors; in some cases, it is almost certain that these agencies maintain an established and systematic relationship with cybercriminal threat actors, either by indirect collaboration or via recruitment."
Ransomware stats: Microsoft's security team says that at the end of 2022, its security team was tracking more than 50 different ransomware variants and more than 100 threat actors using ransomware to perform intrusions. The company says that while many groups still use phishing as an initial entry vector, some groups have switched to using malicious ads (malvertising) in recent months. Ransomware strains that have been linked to malicious ads as the entry vector include the likes of Lockbit Black, BlackCat (ALPHV), Play, Vice Society, Black Basta, and Royal.
SocGolish-to-ransomware: Confirming Microsoft's reporting above is a blog post from ReliaQuest that describes two recent incidents where a threat actor tried to deploy ransomware after an initial compromise via the SocGholish (FakeUpdates) malware.
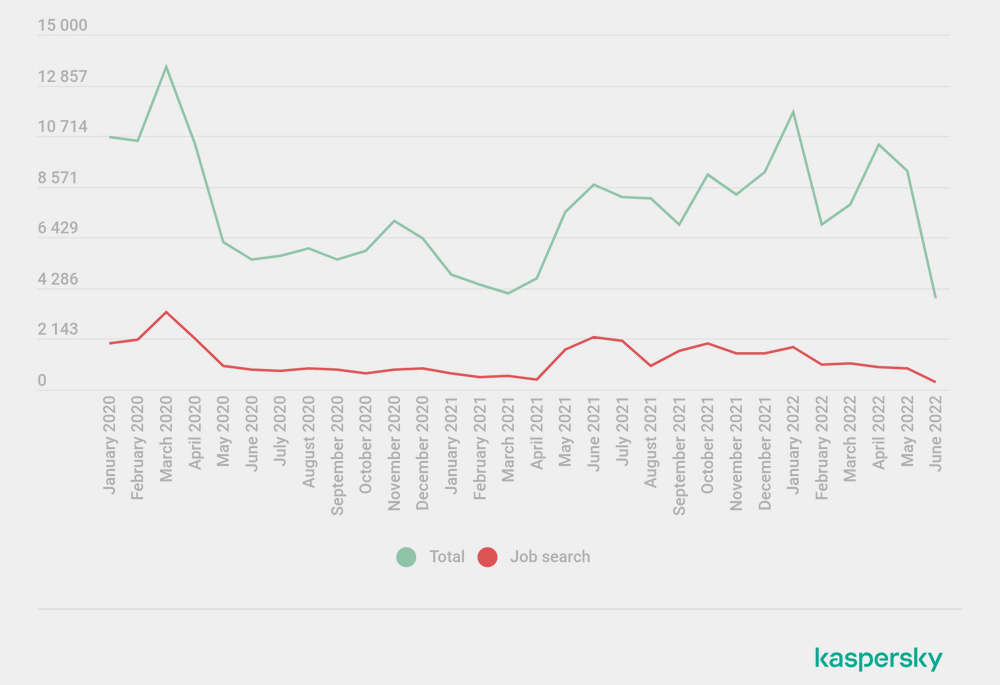
Cybercrime job ads: Kaspersky researchers have analyzed job ads posted in underground forums over a period of two and a half years and found that developers have been in high demand. Kaspersky says that 61% of the 200,000 employment-related ads posted on 155 dark web forums from January 2020 through June 2022 were related to software development. Individuals capable of developing and spreading malware could earn between $1,300 and $4,000 per month, with some coding-related jobs paying up to $20,000. Kaspersky says the highest number of job posts were made in March 2020, after the onset of the COVID-19 pandemic, when many laid-off IT staff went online looking for new jobs.
Malware technical reports
Prilex PoS malware evolves: Kaspersky researchers say they found an updated version of the Prilex malware that can block NFC transactions made via contactless payment cards and force stores and their customers to make payments by inserting their card in the PoS device and capturing the card's details via the older protocols it is accustomed to. The Prilex PoS malware was first discovered last year and was named after the group that used it—Prilex—a suspected Brazilian threat actor. The group has been active since 2014, but for the majority of its lifespan, it focused on performing ATM jackpotting attacks and only recently switched to writing and deploying its own custom PoS malware strain—and one very advanced, according to Kaspersky.
"This is highly advanced malware adopting a unique cryptographic scheme, doing real-time patching in target software, forcing protocol downgrades, manipulating cryptograms, doing GHOST transactions and performing credit card fraud—even on cards protected with the so-called unhackable CHIP and PIN technology. And now, Prilex has gone even further. [...] During a recent Incident Response for a customer hit by Prilex, we were able to uncover three new Prilex versions capable of blocking contactless payment transactions, which became very popular in the pandemic times."
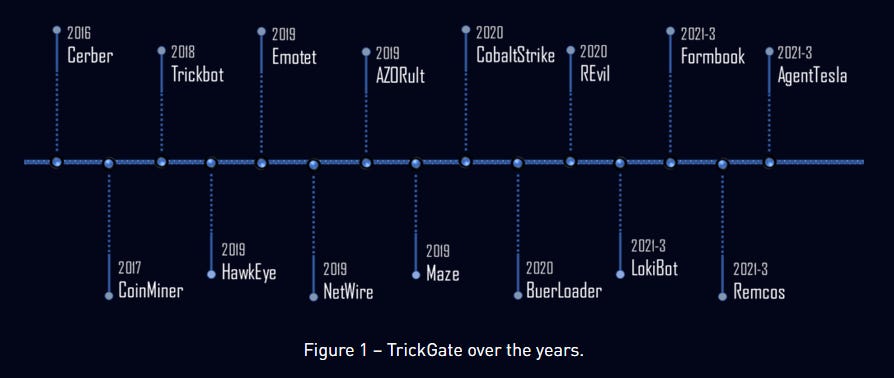
TrickGate: Check Point's research team has lifted the veil from a pretty secretive crypter/packer that has been used by malware gangs since at least 2016. Known as "TrickGate," "Emotet's packer," "new loader," "Loncom," and "NSIS-based crypter," the packer has been used by some of today's largest malware operations, such as Emotet, Trickbot, Maze, REvil, Cerber, AZORult, Formbook, AgentTesla, and more. More in the report.
APTs and cyber-espionage
New NikoWiper: Cybersecurity firm ESET has discovered a new data wiper that was deployed in an attack against a Ukrainian energy company in October last year. ESET researchers say the malware was based on the Sysinternals SDelete application. Researchers have attributed the malware to Sandworm, a Russian cyber-espionage group linked to Russia's military intelligence service, the GRU. Sandworm used the malware to destroy systems at the Ukrainian energy company around the same period that the Russian military targeted Ukrainian energy infrastructure with missile strikes, although ESET says it wasn't able to demonstrate any coordination between the two events. ESET named the malware NikoWiper (see ESET's APT T3 2022 report for more). Last week, ESET discovered another new Sandworm data wiper, named SwiftSlicer, also used in Ukraine.
Vulnerabilities and bug bounty
VMware vRealize Log Insight PoC: Cybersecurity company Horizon3 has published a detailed write-up, and proof-of-concept exploit code for a vulnerability in the VMware vRealize Log Insight application. Tracked as CVE-2022-31706, the vulnerability is exploitable in the default configuration. VMWare released a patch last week.
CVE-2022-47929 (Linux): Cloudflare's engineering team has a write-up on CVE-2022-47929, a denial of service vulnerability in the Linux traffic control queue that can be used to crash servers.
CVE-2022-44707 (Windows): Akamai has a write-up on CVE-2022-44707, a denial-of-service (DoS) vulnerability in Microsoft's Wininit.exe that can be used to bypass security checks and initiate or stop a Windows shutdown.
KeePass vulnerability: Even though the KeePass team disputes that one of their app's features is insecure by design, the CERT teams from Belgium and the Netherlands are warning companies that the app is now insecure and that it may get easily abused by malware in the coming future to dump a user's passwords in cleartext without the need for the master password.
Password managers vulnerabilities: Bug hunter David Dworken has discovered that multiple password management applications can be tricked into auto-filling passwords on untrusted web pages, even without the user entering their master password. Vulnerable clients include Bitwarden, DashLane, and Safari's password management feature.
Sh1mmer exploit: A Chromebooks hobby group has released Sh1mmer, an exploit that can be used to unenroll Chromebooks from school and enterprise networks.
Infosec industry
Metasploit 6.3: Rapid7 has released v6.3 of the Metasploit framework with support for a ton of Kerberos and Active Directory attack modules.
XSSHunter new home: TruffleSecurity and Mandatory have set up a new home for XSSHunter, the popular open-source blind cross-site scripting detection platform. XSSHunter's old home was to be discontinued this week.
Tool retired: And since we're on the topic of discontinued apps, the UK NCSC has retired Logging Made Easy (LME), an open-source project that pulls together multiple pieces of free software to provide basic logging of security information on enrolled Windows devices.
Bad detections: Apparently, Carbon Black's EDR is labeling many Go and Nim-based binaries as malware. Fun, fun, fun!
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




