Risky Biz News: Good news for the Capital One hacker, bad news for the former Uber CSO
In other news: Albania wanted to invoke NATO Article 5 over Iranian cyberattack; Binance hacked for $560 million; and new Zimbra zero-day.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Two high-profile hacking cases coincidentally reached their conclusions this week in US courts—the case of Paige Thompson, the Capital One hacker, and Joe Sullivan, Uber's former chief security officer.
Thompson, who stole data from Capital One's AWS accounts back in 2019, including the data of more than 100 million of the bank's customers, was sentenced to time served and five years of probation, including location and computer monitoring.
DOJ prosecutors, who asked for a seven-year prison sentence, said they were "very disappointed with the court's sentencing decision" and that "this is not what justice looks like."
They said that "… Thompson's crimes … were fully intentional and grounded in spite, revenge, and willful disregard for the law. She exhibited a smug sense of superiority and outright glee while committing these crimes…. Thompson was motivated to make money at other people's expense, to prove she was smarter than the people she hacked, and to earn bragging rights in the hacking community."
But while Thompson dodged a long prison stay—which is quite common for hacking charges in US courts—the case is not over yet, and it could end up ruining her life anyway. Thompson's case will have a final hearing in December, where the judge will determine the amount of restitution Thompson must pay to her victims—which prosecutors and victims have estimated at a whopping $250 million. It will probably not be $250 million, but not a negligible sum either.
As for Sullivan's case, the former Uber CSO was found guilty of lying to authorities about the company's 2016 breach, when two hackers broke into Uber's servers, stole customer and driver data, and demanded a ransom—which Sullivan arranged to be paid, disguised as a bug bounty reward.
The trial was a landmark case, the first time a CSO faced criminal charges for a security breach. However, contrary to popular belief, Sullivan wasn't found guilty of making the payment but was found guilty of hiding the breach from authorities, namely the FTC, which was investigating Uber at the time in connection to another breach from 2014.
Agreed, though I do have questions about why the feds decided to go after Joe Sullivan alone. Seems to me there could have been at least three potential defendants, but Sullivan was the only person indicted.
— Marcia Hofmann (@marciahofmann) 1:48 AM ∙ Oct 6, 2022
Prosecutors did add wire fraud charges to Sullivan's case, related to the actual bug bounty payout to the hackers, in December 2021, but the charges were eventually dropped, leaving the core of the case to hinge around the Uber exec's obstruction of justice.
Sullivan, who once used to be a prosecutor in the same office that charged him now, faces up to eight years in prison and $500,000 in fines. His sentencing hearing has not been scheduled yet.
But regardless of the fine minutia of the case, the infosec industry has been seriously rocked by Sullivan's prosecution. Several opinions going online argue that the case will either drive away legitimate professionals from CISO/CSO roles to minor or completely different positions or industries or will drive up position salaries through the stratosphere if security execs are now literally expected to fall on the legal sword following a security breach and all the legal shenanigans that often take place in the backstage of many organizations. Because we know they do.
This Uber verdict really is going to destroy CISO positions. If one can brief legal, obtain approval by the CEO, & still be hung out to dry for response actions that a hundred other firms have likely taken with far less structural cover, then there can't be enough $$ to sign on
— JD Work (@HostileSpectrum) 10:12 PM ∙ Oct 5, 2022
Breaches and hacks
CommonSpirit Health incident: CommonSpirit Health, the second-largest nonprofit healthcare system in the US, said it was dealing with a major cybersecurity incident that is impacting its IT systems. According to reporting in trade media publications, the incident has impacted healthcare service at several of the CommonSpirit facilities, and some had even diverted ambulances to other nearby hospitals in the first hours of the attack on Monday. The incident is currently believed to be a ransomware attack, although the company has not formally confirmed it. CommonSpirit Health operates more than 1,500 care sites and 140 hospitals in 21 states, but the scope and size of the incident are still unknown.
Lloyd's of London incident: UK banking and insurance giant Lloyd's of London said on Wednesday that it was investigating a possible security breach of its IT systems after its staff "detected unusual activity on its network." [Additional coverage in The Record]
Binance hack: Binance has paused its Binance Smart Chain (BSC) blockchain bridge project after a threat actor used an exploit to generate and steal 2 million Binance Coins (BNB), worth around $560 million. But despite the size of the hack, according to blockchain security firm SlowMist, Binance’s quick response has blocked the hacker’s access to roughly 80% of the stolen funds. [Additional coverage in The Defiant]
An exploit on a cross-chain bridge, BSC Token Hub, resulted in extra BNB. We have asked all validators to temporarily suspend BSC. The issue is contained now. Your funds are safe. We apologize for the inconvenience and will provide further updates accordingly.
— CZ 🔶 Binance (@cz_binance) 11:51 PM ∙ Oct 6, 2022
Since the $BNB Chain was suspended, the ~$430M on it cannot be transferred any further.
— SlowMist (@SlowMist_Team) 3:07 AM ∙ Oct 7, 2022
In total, over $110M was moved off the BNB Chain
Frozen: ~6,5M $USDT
Supplied to lending pools: ~$37.5M
Borrowed: ~$16.5M
Still have access to: $83.3M
General tech and privacy
Meta sues app maker: Meta sued a Chinese company on Wednesday for developing Android clones of its WhatsApp mobile application that contained hidden functionality to steal user credentials. The company, named HeyMods, but also known as Highlight Mobi and HeyWhatsApp, allegedly collected credentials to more than one million accounts, according to Meta's lawsuit.
Supply chain attack protection for Dart: GitHub has updated its Dependabot service to support checking dependency trees for possible vulnerabilities and supply chain attacks against Dart libraries.
Zcash blockchain getting spammed: The size of the Zcash blockchain has more than tripled to more than 100GB since June this year following a spam attack using bloated but cheap "shielded transactions." As the blockchain size has grown to a massive size, cryptocurrency experts expect Zcash node servers, which need to keep a copy of the blockchain locally, to start failing due to memory-related issues. [Additional coverage in The Block]
The zcash spam attack continues. Almost every block contains a shielded transaction with hundreds of outputs. In doing so, the spammer can successfully blow up the size of the chain by maxing each 2mb block every 75 seconds. The cost of each spammed transaction? Less than a cent.
— xenu (@xenumonero) 6:23 AM ∙ Oct 5, 2022
Somebody's having fun spamming the zcash blockchain and tripling its size to over 100 GB. Rough estimate is that this attack is costing them ~$10 a day in transaction fees.
— Jameson Lopp (@lopp) 5:51 PM ∙ Oct 5, 2022
Government, politics, and policy
UK to formally ditch GDPR: Michelle Donelan, the UK Secretary of State for Digital, announced this week plans for the UK to ditch the EU GDPR for a new data protection system. Speaking at the Conservative Party Conference in Birmingham on Monday, Donelan said the UK government will look to pass new legislation inspired by data protection laws used in Israel, Japan, South Korea, Canada, and New Zealand. [Additional coverage in TechCrunch]
Ukraine dismantles another bot farm: Ukraine's Cyber Police said they took down a "large-scale" bot farm that spread fakes and Russian propaganda about the war in Ukraine. Officials said the network was run by four suspects, amassed more than 50,000 bots, and was growing with 3,000 social media and email accounts each week. The operation marks the fifth time Ukrainian officials have gone after Russian bot farms operating inside Ukraine, after similar operations in February (18,000 bots), March (100,000 bots across five bot farms), August (1,000,000 bots), and September (7,000 bots).
Albania wanted to invoke NATO Article 5: POLITICO reported on Wednesday that the Albanian government had considered invoking NATO's infamous Article Five in the aftermath of an Iranian cyberattack that crippled several government systems in mid-July. Article Five is a cornerstone of the NATO alliance and implies that an attack on one member of NATO is an attack on all of its members. If invoked, this would have been the first time that Article Five would have been called following a cyberattack.
Short 🧵 on implication of invocation of NATO Article 5 in response to cyber attacks, as Albania apparently may have considered recently in response to Iranian cyber-enabled disruption against that country per @magmill95 @politico reporting
— Dmitri Alperovitch (@DAlperovitch) 6:33 PM ∙ Oct 6, 2022
politico.com/news/2022/10/0…
Sponsor section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year, in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
Cybercrime and threat intel
SMS blackmailer detained in Australialand: The Australian Federal Police detained on Thursday a 19-year-old from Sydney on charges of using some of the recently leaked Optus customer data in an SMS blackmail scheme. According to the AFP, the teen messaged Australians who had their data leaked online last month and demanded AUD$2,000; otherwise, he'd use their details in financial crimes. A copy of the SMS victims would receive is embedded in the tweet below:
Victims of Optus data hack are now receiving text messages from hackers demanding $2000AUD be paid into a CBA bank account, with threats their data will be sold for “fraudulent activity within 2 days.” @9NewsAUS
— Chris O'Keefe (@cokeefe9) 2:10 AM ∙ Sep 27, 2022
JEE hacker detained in India: Indian officials arrested on Monday a Russian national in connection with the hacking of the Joint Entrance Examination (JEE), the country's national college admittance test. Identified as Mikhail Shargin, officials said the suspect hacked into JEE servers in 2021—when the exam was being held online due to the COVID-19 pandemic—and provided remote access to the servers for other suspects to tamper with exam results. Shargin was detained at the New Delhi airport after arriving via a flight from Kazahstan and is still detained pending additional questioning.
The "Al Capone" cybercrime-fighting strategy: Ethan Thomas Trainor, a Florida man who bought and sold hacked online accounts on dark web marketplaces, pleaded guilty this week to tax evasion after he failed to report his ill-gotten funds to the IRS. According to the US DOJ, Trainor made more than $1 million worth of cryptocurrency from his dark web transactions and then tried to hide his profits.
Hacktivist sentenced in Belgium: Meanwhile, in a very weird case in Belgium, an anti-vaccine activist was sentenced this week to 100 hours of community service. According to local media, Marie Samijn hacked into the personal laptop of Flanders prime minister Jan Jambon on December 7, last year. Testifying in court, Samijn said she visited Jambon's residence last year after returning from an anti-government protest. She was allegedly left alone for 90 minutes to wander around the residence, during which time she found the prime minister's laptop, on which his account password was taped. Jambon admitted to accessing the device and changing one of the official's PowerPoint presentations to add statistics on child pornography and human trafficking across various European countries. SHOCKING HACKING NEWS! UNBELIEVABLE HACKERY!
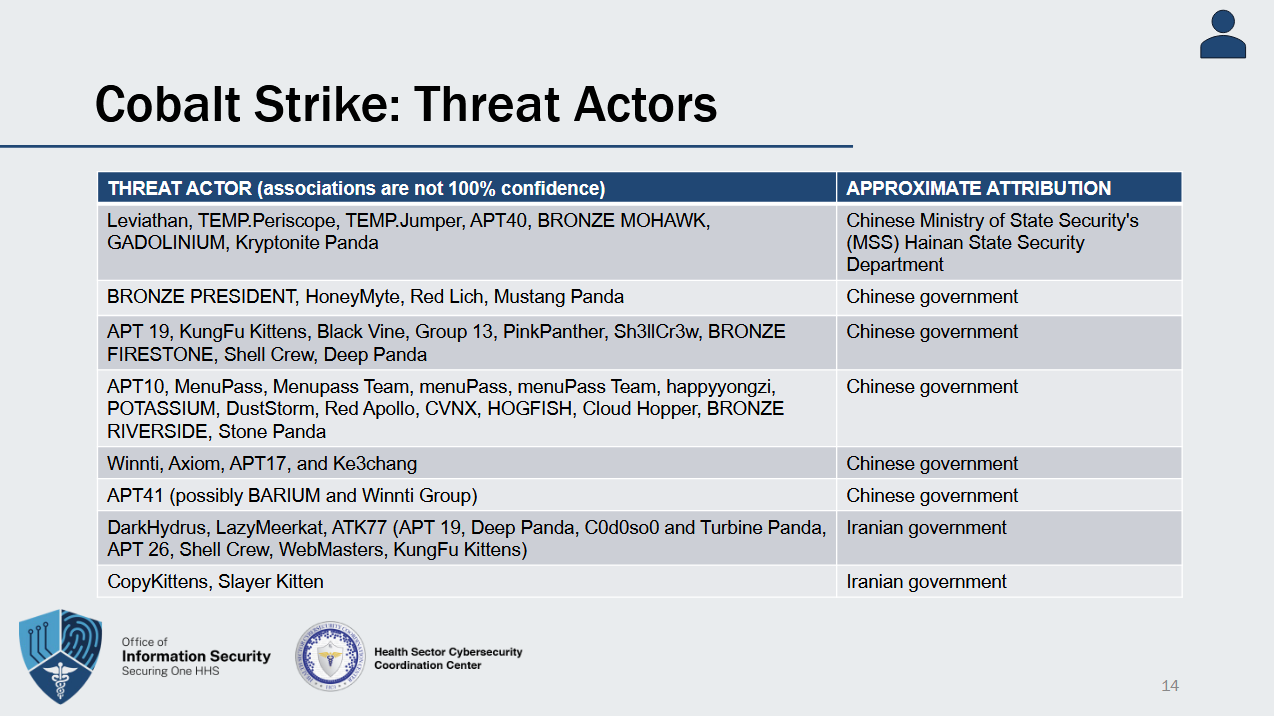
Security tools abuse in US healthcare: The US Department of Health & Human Services published this week a summary [PDF] on the most common red-team and security tools abused during attacks on US healthcare organizations. The list includes the usual suspects like Cobalt Strike, Mimikatz, Powershell, Anydesk, Brute Ratel, and Sysinternals.
npm malware: Twenty-one JavaScript libraries were removed from the npm portal over the past three days after researchers found malware hidden in the code. See the list here.
ZipB malvertising campaign: Researchers from GuardioLabs published a report this week on ZipB, a malvertising campaign that has been active since May this year and which has distributed various malware payloads, including the likes of Zusi, Tiggre, and Wacatac. GuardioLabs said the campaign has infected more than 50,000 users, and the vast majority of compromised systems are located in Romania, the Middle East, and South Asia.
BazarCall: Trellix has a report on BazarCall, a complex social engineering campaign that tricks users into installing the BazaarLoader backdoor.
Magniber ransomware: AhnLab has an update on Magniber, the ransomware strain that has been active for more than half a decade and has exclusively targeted South Korean users only.
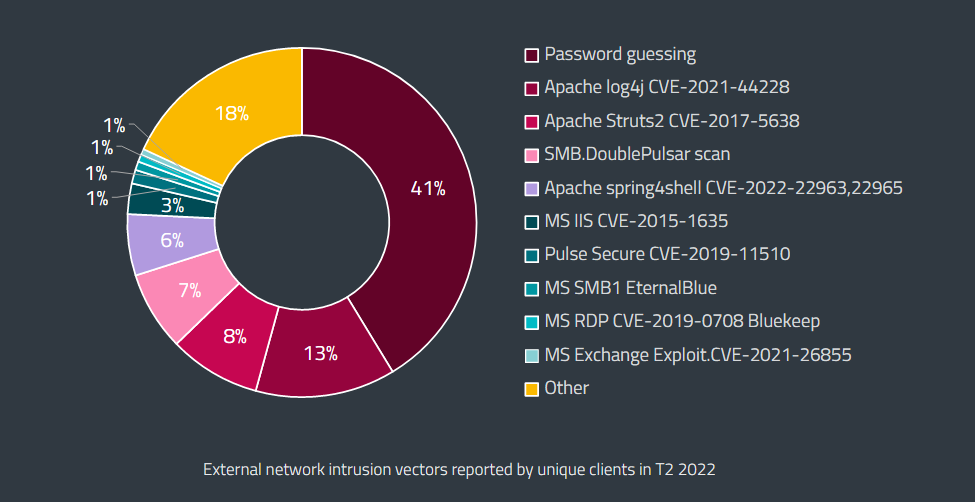
ESET threat landscape: Slovak security firm ESET published on Wednesday its report on the H1 2022 threat landscape. Among the report's findings, the company noted that around 41% of network-related intrusions were the results of password-guessing attacks.
Malware technical reports
LilithBot: Zscaler researchers have discovered a new malware strain named LilithBot, which researchers believe was developed by the Jester Group, a malware dev team that runs the Eternity Malware-as-a-Service. LillithBot appears to be the group's attempt to develop an infostealer component for their service.
RatMilad: Zimperium researchers have a report out on RatMilad, an Android spyware strain that is currently being spread across the Middle East hidden inside a mobile VPN app. According to the research team, this VPN app is currently being promoted to possible victims via a Telegram channel.
APTs and cyber-espionage
Exchange zero-day update: Earlier this week, US cybersecurity firm Volexity linked the recent Chinese APT group that exploited the ProxyNotShell vulnerabilities (CVE-2022-41040 and CVE-2022-41082) to a known threat actor that has previously targeted Outlook Web Access and Zimbra servers in the past. However, in a tweet on Thursday, the company backtracked on its findings, saying that two different Chinese APTs used the same infrastructure for different attacks in the past, hence the confusion. As Mandiant's Mark Lechtik points out, this indicates the existence of specialized initial access brokers serving Chinese APTs, similarly to how both Russian and Iranian groups also employ IABs for some of their operations.
Another data point alluding to the existence of an initial access broker serving Chinese threat actors (most likely state sponsored ones)
— Mark Lechtik (@_marklech_) 2:50 PM ∙ Oct 6, 2022
Dracarys RAT: Here's an interesting sample for the APT hunters out there.
Weather app asks for full control of device🚩
— Lukas Stefanko (@LukasStefanko) 6:57 AM ∙ Oct 5, 2022
It's open-source weather patched with Dracarys RAT operated by Bitter APT group
After Meta's first publication of #Dracarys, malware devs replaced all occurrences of string "Dracarys" for "Lodge"
CC: currweather[.]com
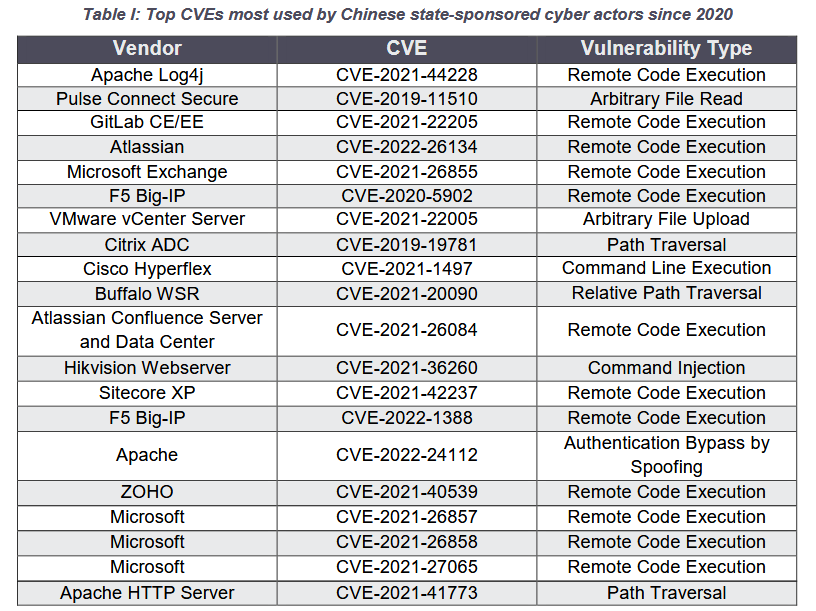
Top CVEs exploited by Chinese APTs: The NSA, CISA, and the FBI published a joint advisory [PDF] on Thursday with a list of the top 20 vulnerabilities exploited by Chinese state-sponsored threat groups.
"All of the CVEs featured in the advisory are publicly known. The top recommended mitigation is to patch these and other known exploited vulnerabilities."
Vulnerabilities and bug bounty
State of PostgreSQL servers: Some very interesting research here from Jonathan Mortensen of Bit.io, who found that the vast majority of internet-connected PostgreSQL databases either don't require (85% of 820,000) or don't even support encrypted connections at all (64%).
Malicious POCs: Despite what the tweet says below, Microsoft is not removing ProxyNotShell proof-of-concept exploits but malicious ones that install malware on users' devices. There's a niche for that kind of stuff, and malware devs have no shame.
Microsoft appears to be removing GitHub accounts that post PoC for latest Exchange 0day. I think this came up and has been done before? I seem to recall conversation about them selectively removing only accounts that post 0day for Microsoft products and not others?
— Richard Johnson (@richinseattle) 12:22 AM ∙ Oct 4, 2022
Zimbra zero-day: An actively exploited zero-day vulnerability exists in the Zimbra CRM. Tracked as CVE-2022-41352, attacks using this vulnerability were first spotted on September 10, but despite the active exploitation, the Zimbra team has failed to deliver a security update for almost a month (beyond some mitigation advice). In the meantime, we now also have a public PoC.
Android security updates: ...for the month of October 2022 are out!
Infosec industry
WireShark update: WireShark 4.0.0 is out. Big change? No more 32-bit releases on Windows. Plus more.
New tool—GitFive: An OSINT tool to investigate GitHub profiles. The code is here.




