Risky Biz News: Gmail will warn users when their email address appears on the dark web
In other news: Security firm Dragos discloses failed extortion attempt; Morocco used Pegasus to spy on Spanish PM; half of North Korea's missile program funded through hacks.
This newsletter is brought to you by Material Security, the company that provides visibility, defense-in-depth, and security infrastructure for Office 365 and Google Workspace. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
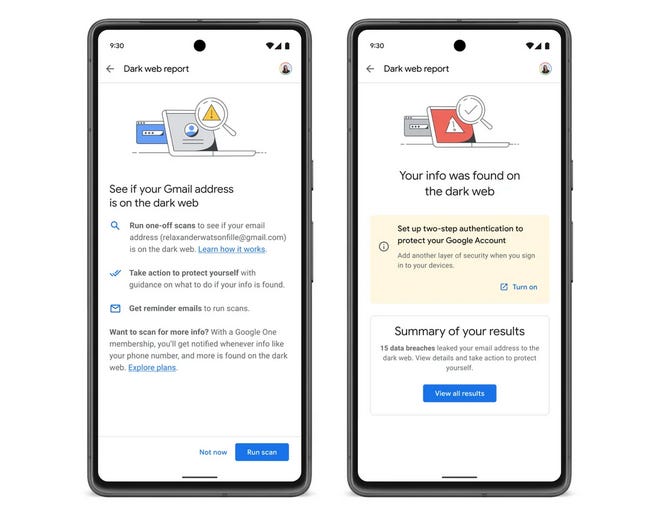
Google is rolling out a new feature for Gmail users in the US that will notify them when their email address pops up on the dark web.
The new feature is named the "Dark Web Report" and will be available in a Gmail account's security section.
Once enabled, Google will use its threat intel capabilities to scan dark web criminal sites and see when threat actors are either selling access to Gmail accounts or when a Gmail address is included in data leaks.
Once a match is found, Google will prompt the Gmail account owner to change their password and enable multi-factor authentication.
The same dark web scanning feature is also one of the security systems that powers a Chrome feature that warns users to change passwords that have appeared in data leak packages.
While the feature will initially roll out to the US market only, Google says it plans to make this available to all users.
The new feature is part of a series of security upgrades [1, 2] announced by the company at its annual I/O developer conference this week. The list also includes:
- Adding a "Spam" folder to the Google Drive service where the company plans to send files that it believes are either malicious or unwanted/unrequested.
- A new Safe Browsing API that is allegedly blocking an "additional 25% of phishing attempts every month in Chrome and Android."
- An easier way to delete search history in Google Maps.
- Android 14 will get an improved Data Safety section. With the new OS, every time an app asks for permission to use location data, Google will show if the app shares the location data with third parties.
- Starting with Android 14, Google will prevent apps that target an Android SDK level lower than 23 from being installed because "malware often targets older levels to get around newer security and privacy protections."
Breaches and hacks
TechnologyOne incident: Australian SaaS provider TechnologyOne has disclosed a security breach [PDF] after a threat actor gained access to its "internal Microsoft 365 back-office system." The company says its customer-facing SaaS servers were unaffected by the breach, yet its websites went down following the attack. The Australian Securities Exchange halted trading of TechnologyOne shares following the company's disclosure [PDF].
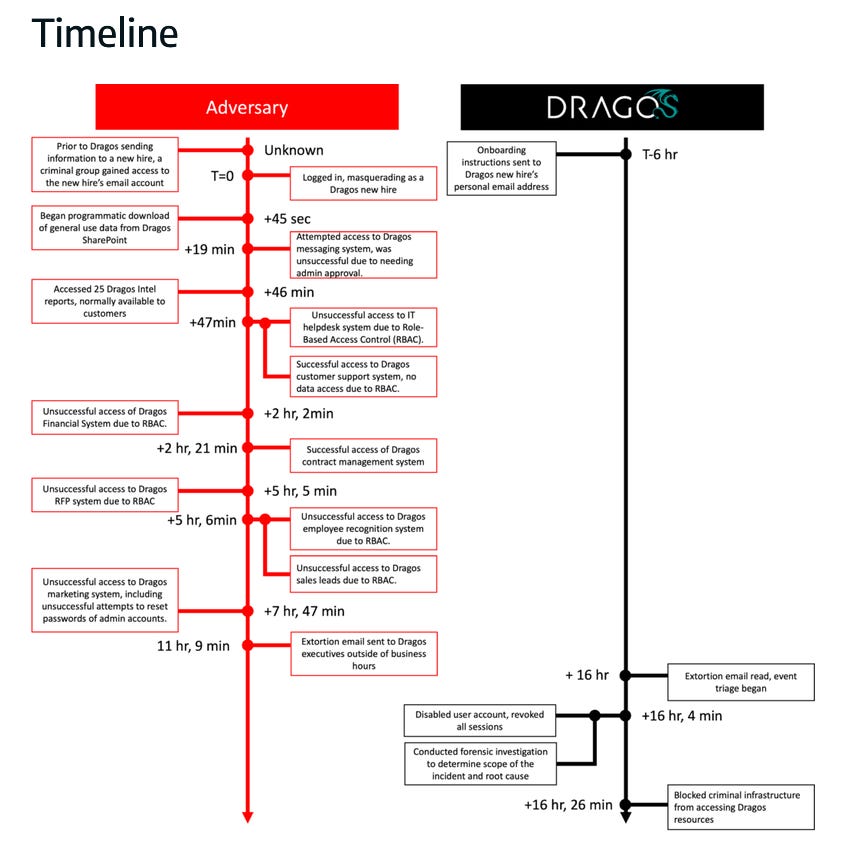
Dragos breach: Cybersecurity firm Dragos says it narrowly avoided a ransomware attack. The incident took place earlier this week on Monday after a threat actor gained access to a new employee's account before their onboarding process. Dragos says the threat actor only gained access to its SharePoint cloud service and contract management platform. The attacker tried and failed to move laterally and gain access to other internal systems, and eventually moved to extort the company only after 16 hours inside its network. Extortion messages were sent to Dragos executives, with some containing references to family members. Dragos publicly disclosed the incident after they secured their network. Three hours later, the attacker leaked some images of data they stole from Dragos' network, claiming they had more than 130GB of files.
General tech and privacy
Clearview AI fined again in France: France's privacy watchdog CNIL fined American company Clearview AI €5.2 million for failing to pay a previous fine of €20 million. The fine represents penalties of €100,000 per day since October 20, 2022, when CNIL imposed its previous fine. In addition, the French privacy agency says Clearview also ignored an order that barred the company from collecting people's photos off the internet without their consent.
Twitter encrypted DMs: Crypto-spam, state propaganda, right-wing nuthouse, harassment, and the butt-of-all-jokes platform Twitter has rolled out encrypted DMs. The company's announcement got a lot of pushback because it only works if both sender and recipient have a Twitter Blue subscription and because it's not actually a properly designed E2EE system. While the DMs are encrypted, links shared inside messages and metadata, such as message recipient and message time, are not.
YouTube tests ad-blocker block: The company that sabotaged ad-blocker features in Chrome and is tracking everyone without their consent across the internet wants to block ad-blockers on YouTube because it hurts its billion-dollar profits.

Government, politics, and policy
Austria bans TikTok on govt devices: Austria has joined a long list of Western countries that are barring government employees from installing the TikTok app on government-issued devices. Other countries that have taken similar measures include the US, the UK, the EU, Canada, Australia, New Zealand, Taiwan, France, Norway, Denmark, Sweden, the Netherlands, and Belgium. [Additional coverage in The Local]
PEGA blames Morocco: The EU's PEGA commission claims the Moroccan government most likely used the Pegasus spyware against Spanish government officials. The alleged hacking took place in July 2021 and targeted Prime Minister Pedro Sanchez, Minister for Defence Margarita Robles, and Minister of the Interior Fernando Grande-Marlaska. The hacks came to light at the same time Spain's own use of the Pegasus spyware against Catalan politicians—known as the CatalanGate scandal— was exposed and led to the firing of the country's head of intelligence services. Prior to this week's PEGA accusations, the Moroccan government was also accused of using the Pegasus spyware to spy on French President Emanuel Macron and other French ministers.
IRS donates tools to Ukraine: The IRS Criminal Investigation team will hold cyber training and provide blockchain analysis tools to Ukrainian law enforcement agencies. Fifty Ukrainian law enforcement officers participated in a virtual training in April, and 20 Ukrainian officials are being trained this week in Frankfurt, Germany. The IRS has also donated 15 licenses for Chainalysis Reactor, a cryptocurrency investigations platform. The agency hopes Ukrainian law enforcement will use the training and the new tools to track down and target financial networks used by sanctioned Russian oligarchs. Ukrainian agencies working with the IRS-CI include the Cyber Police Department of the National Police of Ukraine, the Economic Security Bureau of Ukraine, the Department of Cyber and Information Security of the Security Service of Ukraine, and the Prosecutor General's Office of Ukraine.
Hunt-forward mission: US Cyber Command says it recently concluded a hunt-forward mission in Latvia where its cyber team found malware deployed by a foreign adversary. Officials did not share other details. This now brings the total number of CyberCom hunt-forward missions to 47, deployed to 22 different countries.
Jankowicz sues Fox News: Nina Jankowicz, the former head of the now-defunct DHS Disinformation Governance Board, has sued Fox News. Jankowicz says the television network spread lies about her and the agency's role that generated threats to her personal safety. Jankowicz says Fox News and its hosts intentionally attacked her in more than 300 segments over the course of eight months, even after she left her position. She accused the network of intentionally lying in order to advance the political agenda of the US right-wing. She also accused Fox host Tucker Carlson of making veiled threats that would "get men with guns to tell you to shut up." The lawsuit was filed in the same state where Fox News was sued and settled with voting machine maker Dominion Voting for $787.5 million after the network promoted conspiracy theories about the 2020 election and the company's voting machines. Jankowicz is seeking unspecified damages. [Additional coverage in the New York Times/non-paywall]
Mythbusters: The UK NCSC and ICO have published a joint blog post dispelling some of the myths about responding to cyber-attacks and reporting the incident to authorities rather than paying attackers and hiding the breach—which there's a lot happening these days.
Sponsor Section
Material Security co-founder Ryan Noon demos Material Security's email security solution to Risky Business podcast host Patrick Gray.
Cybercrime and threat intel
Twitter hacker pleads guilty: Joseph James O'Connor, a 23-year-old British citizen, pleaded guilty this week to the July 2020 Twitter hack. Known online as PlugwalkJoe, O'Connor was extradited from Spain to the US at the end of April. Together with three other individuals, O'Connor gained access to Twitter's internal network and hijacked 130 accounts to promote a cryptocurrency scam. In addition, O'Connor also pleaded guilty to SIM-swapping Snapchat, TikTok, and cryptocurrency exchange accounts, stealing from the latter more than $794,000 worth of crypto-assets.
Former Ubiquiti employee gets six years in prison: Former Ubiquiti developer Nickolas Sharp has been sentenced to six years in prison. Sharp stole gigabytes of sensitive files from Ubiqiti's network in December 2020 and tried to extort the company for $2 million dollars in early 2021. He was arrested in March 2021 after tricking infosec reporter Brian Krebs into thinking they were a whistleblower trying to expose Ubiquiti for hiding a breach. The DOJ says Sharp's fabrications caused Ubiquiti's share price to drop 20% and the company to lose $4 billion in market capitalization.
Trinitarios gang dismantled: Spanish police have arrested 40 suspects that are part of Trinitarios, a criminal gang that engaged in phishing, smishing, and other bank scams. Members were detained following house searchers across Madrid, Seville, and Guadalajara. The group allegedly gained access to more than 300,000 bank accounts and stole more than €700,000. Two of the 40 detained suspects worked as the group's hackers, in charge of phishing and smishing.
Venotex: A joint investigation by the Lighthouse Reports, Der Spiegel, Haaretz, Tamedia, and Mediapart claims that a Swiss technology expert and a former ally of Julian Assange has turned from a vocal critic of security states into a provider of surveillance products. Reporters say that Andreas Fink built a platform named Venotex that exploits vulnerabilities in the SS7 telecommunications protocol to pinpoint the location of phone numbers around the globe and even hijack their communications. Investigators say the platform has been used to track an assassinated journalist in Mexico, critics of the Democratic Republic of the Congo government, and suspects in war-torn Mali. In addition, Venotex was also used to redirect SMS messages and hijack Telegram and other online accounts from individuals in Israel and South East Asia.
Malvertising campaign: Malwarebytes has discovered a malvertising campaign active on adult websites that redirects users to a web page that mimics the Windows update screen. The company says that users who land on this page are asked to download a Chrome update that infects their systems with the Aurora Stealer.
Chrome extension to RedLine campaign: Stormshield published a report on a malware distribution campaign that uses malicious Chrome extensions to install the RedLine infostealer on user systems.
Infostealer logs: Sekoia researchers have an overview of how modern infostealers collect and handle logs and how that data is being offered for sale on the cybercriminal underground, currently made up of various Genesis-like "log shops" and Telegram channels.
Leaked Babuk ransomware code: SentinelOne says it is now tracking ten ransomware gangs that have adopted the leaked Babuk ransomware source code to build lockers that can encrypt VMWare ESXi systems. The list includes the likes of Conti, Cylance, Dataf, Lock4, Mario, Play, Revix, Rorschach (BabLock), and RTM Locker.
Greatness PaaS: Cisco Talos researchers say they've uncovered a new Phishing-as-a-Service platform named Greatness that has been used in several phishing campaigns since at least mid-2022. For now, the platform only supports Microsoft 365 phishing pages, but other online services are expected to be supported in the future. Researchers say Greatness incorporates all the common features seen in top-of-the-line phishing platforms, such as multi-factor authentication (MFA) bypass, integration with Telegram bots, IP filtering, and its own API.
Mont4na profile: S2W Talon has a profile on Mont4na, an initial access broker selling access to corporate networks on several underground cybercrime platforms.
Israel BEC group: Abnormal Security says it discovered a new threat actor based in Israel that has engaged in more than 350 BEC campaigns since February 2021. The attacks have targeted roughly 100 organizations, with all being large, multinational enterprises with average annual revenue exceeding $10 billion/year. Abnormal says the group typically carries out attacks during three time periods each year—namely, in March, in June and July, and from October to December. Researchers say that despite the group's apparent location in Israel, 74% of the BEC attacks they've analyzed since the start of 2022 have been carried out by Nigerian threat actors.
Malware technical reports
CLR SqlShel: South Korean security firm AhnLab has published an analysis of CLR SqlShel, a web shell that was recently found deployed on hacked MSSQL servers. The malware was often found during attacks carried out by the ShadowForce group, which typically used it to deploy crypto-miners on compromised systems.
BPFDoor: DeepInstinct has detected a new version of BPFDoor, a Linux-based backdoor used by a Chinese APT known as Red Menshen.
RapperBot: Fortinet researchers have discovered an updated version of the RapperBot malware that has received a crypto-mining module. This is the latest evolution in the malware's capabilities, which started out as an IoT botnet capable of carrying out brute-force attacks, then received a DDoS feature, and now this. Fortinet says it saw RapperBot crypto-mining attacks taking place since January this year, which is when QiAnXin also saw the same thing.
JasPer Loader: Stairwell and Solis Security have published a technical report on a new loader called JasPer that they've seen distributed in the wild, including as part of an early IcedID killchain. JasPer is typically distributed as a trojanized Dynamic Link Library (DLL) file that mimics legitimate software and then downloads additional malware inside compromised networks.
CryptBot: ANY.RUN has a technical breakdown of CryptBot—the infostealer disrupted last month by Google.
SocGolish: Sucuri has an update on recent changes to SocGolish infrastructure.
"By the end of March, 2023, we started noticing a new wave of SocGholish injections that used the intermediary xjquery[.]com domain. It appeared to be another evolution of the same malware."
Akira ransomware: Sophos published an analysis of the new Akira ransomware. So far, their leak site has listed 17 victims since its launch at the end of April.
LokiLocker: AhnLab says the new LokiLocker ransomware contains many similarities to the BlackBit strain.
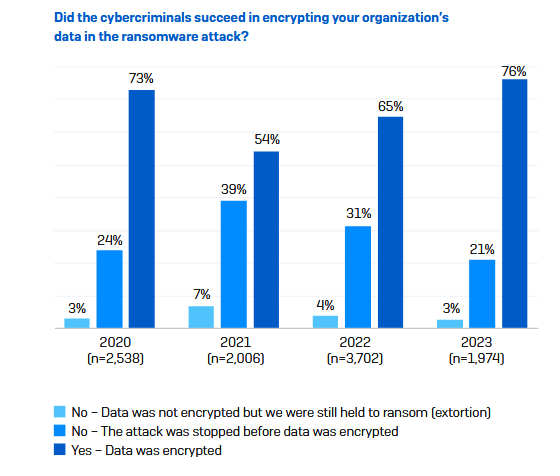
Ransomware encryption rates go up: In its State of Ransomware report, cybersecurity firm Sophos says that ransomware gangs appear to have encrypted data in roughly three-quarters (76%) of incidents they gained access to a victim's network this year. The number is up from the 65% recorded last year in 2022 and the highest it reached ever since the company started tracking this stat. Furthermore, Sophos says that of the 76% of cases where files where encrypted, the attackers also exfiltrated data that they later used to ransom the company as part of "double extortion" or "double dip" schemes.
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
APTs and cyber-espionage
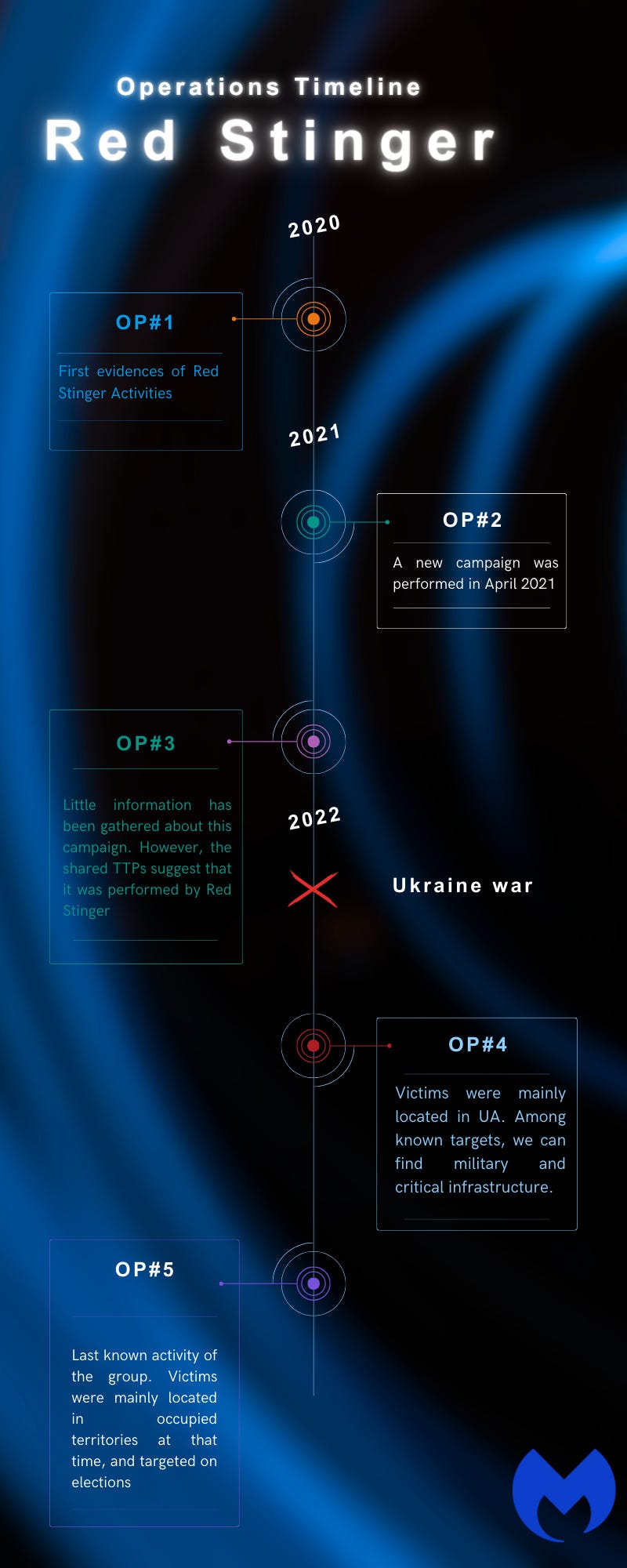
Red Stinger: Malwarebytes researchers have published a report this week exposing the operations of a new APT group the company calls Red Stinger. Researchers say the group has been active since 2020 and has targeted both pro-Ukraine and pro-Russia organizations inside Ukraine. Malwarebytes says the group's principal motives were surveillance and data gathering and that its operators were not particularly sophisticated. Targets included Ukrainian military members and election officials running Russian referendums in Ukrainian regions. The company says it couldn't attribute the group to a specific country as Red Stinger's targeting fit both Ukraine and Russia alike. Malwarebytes says it published its report after Kaspersky first documented the group in a blog post last month under the name of Bad Magic.
DownEx: Bitdefender researchers have discovered a series of attacks against Kazakh and Afghan organizations using the DownEx malware strain. The purpose of the attacks appears to have been espionage and data exfiltration. Bitdefender believes the intrusion campaign was likely carried out by a Russian threat actor.
SideCopy: Qihoo 360 published a report on the SideCopy APT and its recent attacks against Indian organizations.
Intrusion Truth report: Intrusion Truth's latest report is out, and this latest piece claims that the Kerui Cracking Academy in the Chinese city of Wuhan is responsible for training members of Chinese MSS-sponsored APT groups. This is just part 1, and more will follow.
Kimsuky's hospital attack: South Korean officials say that between May and June 2021, North Korean hackers breached the internal network of the Seoul National University Hospital (SNUH) and stole the personal information of 810,000 patients and 17,000 employees. Officials have not attributed the attack to any particular group, but local media reports that the intrusion might have been the work of the Kimsuky APT.
North Korean crypto-heists: About half of North Korea's nuclear missile program has been funded by cyber operations and cryptocurrency theft, Anne Neuberger, Deputy National Security Adviser for Cyber and Emerging Technology for the White House, said at an event this week. The remark finally puts a percentage on the contributions of North Korea's cyber operations to the regime's weapons and missile programs. The US first accused North Korea of using bank and cryptocurrency heists to fund its missile program in September 2019 when the US Treasury Department imposed sanctions on three North Korean APTs. At the time, Treasury did not elaborate on the size of the role hacking groups played in financing the regime's weapons program. Neuberger's remarks and the subsequent talk can be found in the video below at the 5h10m mark. [Additional coverage in CNN]
Vulnerabilities and bug bounty
µC/OS vulnerability: Cisco Talos researchers have discovered an authentication bypass (CVE-2022-41985) in µC/OS, an embedded open-source operating system developed by Micrium. Patches were released.
PwnAssistant: Elttam researchers have published their write-up on PwnAssistant (CVE-2023-27482), a pre-auth RCE in HomeAssistant, a popular open-source home automation software. The company patched the issue back in March.
IE vulnerability: Akamai's Ben Barnea published a technical breakdown of CVE-2023-29324, a vulnerability in the MSHTML engine, an IE component.
GateKeeper bypass: Red Canary's Csaba Fitzl published a write-up on CVE-2023-27951, a vulnerability that can allow threat actors to bypass Apple's GateKeeper using a malformed archive file.
Sitecore vulnerabilities: The Assetnote team has identified three RCEs and two auth-bypasses in the Sitecore CMS. Fixes have been rolled out at the end of last month.
WP plugin vulnerability: Patchstack researchers have identified a vulnerability (CVE-2023-32243) in the Essential Addons for Elementor WordPress plugin that can be used to reset the password of any user, including admins, and take over a WP site.
Infosec industry
New tool—Buzzer: Google's security team has open-sourced a new tool named Buzzer that can be used to fuzz the Berkeley Packet Filter (eBPF) for new vulnerabilities. Google says Buzzer was already used to discover a first vulnerability tracked as CVE-2023-2163.
New tool—Snapchange: AWS has open-sourced Snapchange, a framework for fuzzing and replaying a memory snapshot/dump using KVM.
Tool update—Mythic: SpecterOps' Cody Thomas has announced v3 of Mythic, a plug-n-play command and control (C2) framework that heavily leverages Docker.
HITB videos: Talks from the Hack In The Box 2023 security conference, which took place last month in Amsterdam, are now available on YouTube.




