Risky Biz News: Germany indicts GRU hacker for NATO think tank breach
In other news: CapitalOne hacker found guilty; Windows downloads blocked in Russia; and DDoS attack delays Putin's SPIEF speech.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
German prosecutors have charged and issued an arrest warrant in the name of Nikolay Kozachek, a Russian national and an officer in Unit 26165 of the Russian military's Main Intelligence Directorate (GRU).
German officials said that the 32-year-old Russian breached the IT systems of the Joint Air Power Competence Center, a NATO think tank based in Kalkar, North Rhine-Westphalia. The alleged cyber-attack took place in April 2017, according to German news outlet Der Spiegel, which first reported Kozachek's arrest on Friday.
Reporters said that investigators linked Kozachek to a hacking group known as APT28 (or Fancy Bear), previously linked to the GRU military intelligence agency in previous years by multiple countries.
Investigators said they linked nicknames such as "blabla1234565," found inside the code of GRU malware named X-Agent—malware used in the intrusion—to Kozacheck's identity.
Officials said they found evidence that besides the German NATO think tank, the group also attacked and infected more than 1,000 other targets.
This is no surprise, as Kozachek is a core member of the GRU's APT28 cyber-espionage operations, also being identified and charged by the US in 2018 for the 2016 DNC hack and subsequent attempts to influence the 2016 election via operations like DCLeaks and Guccifer 2.0.
The Joint Air Power Competence Center concerned was founded in 2005 and is a NATO competence center in which strategies and principles for warfare in air and space are developed.
Breaches and hacks
DDoS attack delays Putin's speech: Pro-Ukrainian hacktivists have carried out massive DDoS attacks against the infrastructure of the St. Petersburg International Economic Forum (SPIEF), the annual Russian business event for the economic sector. The attacks delayed Russian President Vladimir Putin's speech by one hour. SPIEF was listed as a target for DDoS attacks on the Telegram channel of the IT Army of Ukraine two days before.
CapitalOne hack: Paige Thompson, the former AWS employee who breached CapitalOne's infrastructure in 2019 and stole the personal details of more than 100 million Americans, was found guilty following a jury trial, the DOJ announced on Friday. Thompson's sentencing is scheduled for September 15, and she faces up to 20 years in prison. Following its hack, CapitalOne was fined $80 million and settled customer lawsuits for $190 million.
Desjardins hack: A Canadian court has approved a CAD$200.9-million (USD$154.6-million) settlement of a class-action lawsuit against Desjardins over its 2020 data breach. The incident exposed the data of 4.2 million people who had accounts at the bank and is one of the largest financial data breaches in Canada's history. The incident was linked to the actions of a rogue employee who was siphoning bank customer data silently for 26 months.
PurePC hack: Polish news site PurePC disclosed a security breach on Friday. The intruders allegedly gained entry to an IPBoard forum integration within the site's Drupal CMS. The breach took place in 2018, and the data was initially leaked in 2019, according to the site. The stolen and leaked information includes usernames, emails, and hashed & salted passwords.
Another crypto hack: DeFi platform Inverse Finance was exploited on Friday using a flash loan attack and lost $1.26 million worth of Tether (USDT) and Wrapped Bitcoin (wBTC). This is the second time the platform got exploited using a loan flash attack after losing another $15.6 million in April.
General tech and privacy
TikTok scandal: Leaked audio from more than 80 internal TikTok meetings obtained by BuzzFeed reporters show that ByteDance's Chinese employees have repeatedly accessed data on US TikTok users between September 2021 and January 2022. On the same day of the BuzzFeed exposé went live, ByteDance published a press release claiming that it is now storing the data of all US users on US servers, although this does not necessarily mean that Chinese staff won't be able to access this information.
More tech firm fines in Russia: After a Russian court fined Google 15 million rubles (~$260,000) last week for refusing to store the data of Russian citizens on servers within the Russian Federation, similar fines were also imposed on Threema (800,000 rubles / $14,000) and Likee (1.5 million rubles / $26,000). A fine of 4 million rubles ($70,000) was also levied against the Internet Archive for not removing "content prohibited in Russia."
Windows downloads blocked in Russia: Russian news agency TASS reported on Sunday that Microsoft was blocking Russians from downloading images for the Windows 10 and Windows 11 operating systems from its official website. This was confirmed by one of my Twitter followers, but it's unclear if this is a permanent ban or just a temporary error.
Всё так
— ttldtor // ⚛️⌨️🏴 No War! (@ttldtor) 5:20 PM ∙ Jun 19, 2022
New Windows 11 privacy feature: New versions of Windows 11 now come with a new privacy feature that will let users review which locally installed applications have recently accessed and used the camera and microphone. The feature is great for detecting if systems are infected with spyware that constantly accesses these devices without the user's specific approval. The feature is active in Windows 11 Preview and Dev builds.
New Windows 11 Privacy Auditing features allow you to see history of sensitive device access like the Microphone
— David Weston (DWIZZZLE) (@dwizzzleMSFT) 7:39 PM ∙ Jun 16, 2022
Smart App Control: Another new feature coming to Windows 11 Insiders builds later this year is Smart App Control. This new feature works by trying to "predict" if a new app being installed on a Windows 11 system may be malicious or not. If the Windows 11 security service is unable to make a confident prediction, then Smart App Control checks to see if the app has a valid signature and allows the installation based on that check.
Clean install defaults 22H2.
— David Weston (DWIZZZLE) (@dwizzzleMSFT) 1:17 AM ∙ Jun 17, 2022
Smoother Exchange logins for Apple users: Microsoft said it worked together with Apple to improve the login experience for iOS and iPad users, who will soon be able to log into Exchange email servers using an OAuth token provided by their device instead of constantly having to re-type their usernames and passwords. Microsoft said it plans to notify all organizations which have iOS/iPad users still using its classic authentication scheme and prompt them to update server settings in the coming days.
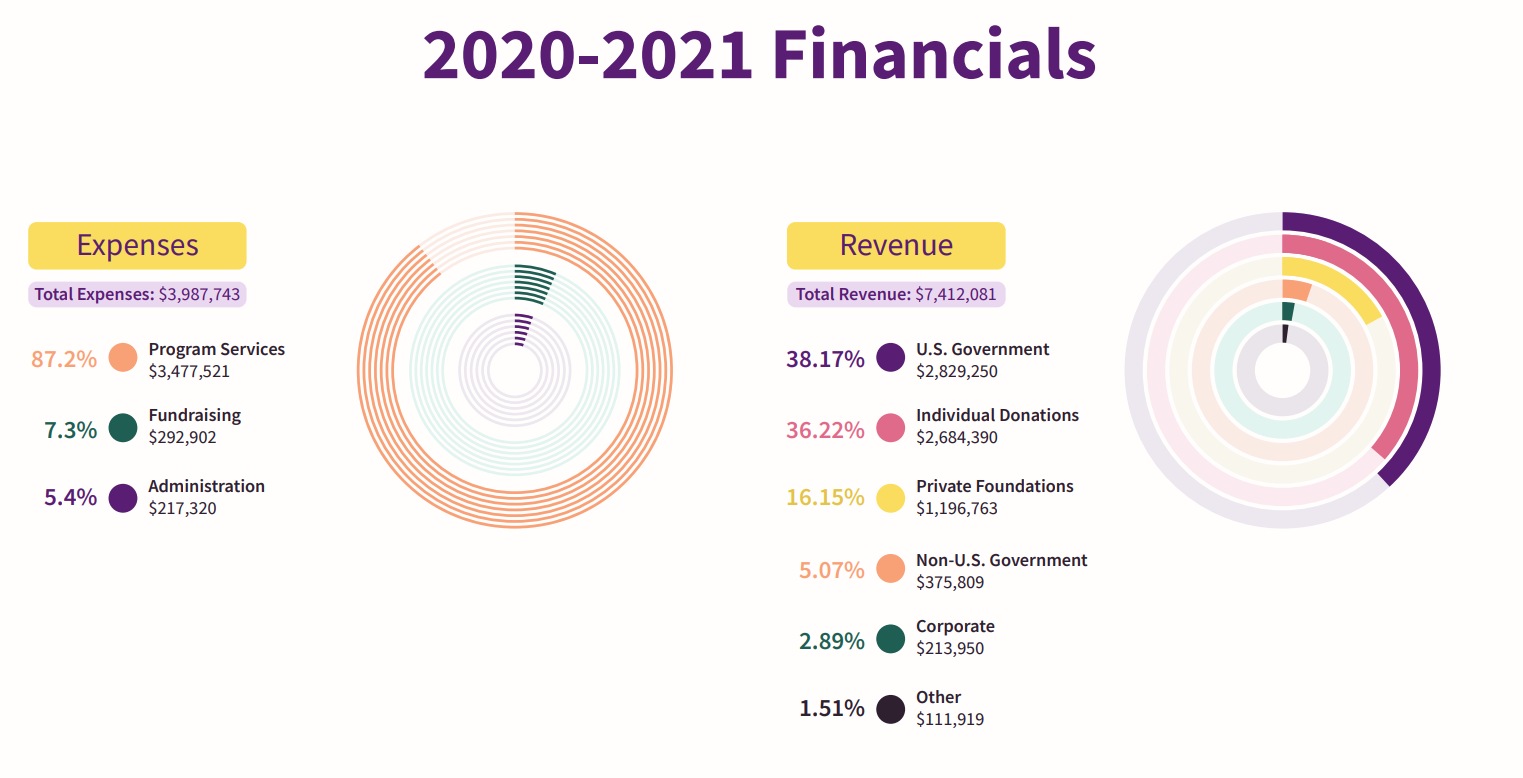
Tor Project finances: The Tor Project has published its annual review report, and while the US government still remains the main source of revenue for the project, its share has come down from nearly 80% a decade ago to just over 38% last year. Donations from individual members have seen the largest rise in recent years, accounting for over 36% in the 2020-2021 financial year.
Minefield: Academics have proposed a software-level defense (named Minefield) against dynamic voltage and frequency scaling (DVFS) side-channel attacks. See the full paper here and here [PDF].
Government, politics, and policy
US offensive operations: Kim Zetter has a deep dive into the recent comments from Gen. Paul Nakasone that US Cyber Command has carried out offensive cyber-operations in support of Ukraine.
Cringe Chinese cyber propaganda: More propaganda from Chinese state media about the "US-centered axis of cyber stealing." [eye roll]
Cybercrime and threat intel
SiegedSec: Threat intel firm DarkOwl has published a report on SiegedSec, a new criminal gang specialized in defacement attacks and data leaks.
ech0raix goes after QNAP: A new wave of the ech0raix (QNAPCrypt) ransomware is hitting QNAP NAS devices. The attacks come after the company said it was investigating new reports of NAS devices being encrypted earlier last week.
Voice phishing attacks: Zscaler said that since May 2022, they've been closely monitoring a threat actor that has been targeting users in various US-based organizations with malicious voicemail-notification-themed emails in an attempt to steal their Office365 and Outlook credentials.
Malware technical reports
Matanbuchus: Details on a campaign distributing the Matanbuchus malware dropper that is currently doing the rounds.
Qakbot: Security researcher @kasua has published a technical report on the Qakbot malware.
BRATA: Mobile security firm Cleafy has published a report on recent versions of the BRATA Android banking trojan, which has received several new features meant to acquire GPS, overlay, SMS, and device management permissions.
BlackGuard stealer: Threat intel firm CyberInt has a report on BlackGuard, a new infostealer trojan that was launched earlier this year and is currently advertised on Russian cybercrime forums and Telegram channels. Previous reports on this same malware are available from S2W and Zscaler.
IceXLoader: Fortinet has published a report on IceXLoader 3.0, the latest version of the IceXLoader malware loader. This latest version is written in Nim, a new language utilized by threat actors over the past two years, most notably by the NimzaLoader variant of BazarLoader used by the TrickBot group.
CopperStealer: Trend Micro has detected a new version of the CopperStealer infostealer being distributed in the wild using websites hosting fake software cracks.
APTs and cyber-espionage
DarkElephant: Chinese cyber-security firm Antiy has published a report on DarkElpehant, an Indian APT group targeting social activists, social groups and opposition parties in India, and military forces in China and Pakistan.
Vulnerabilities and bug bounty
Fastjson RCE: DevOps security firm has published a report on CVE-2022-25845, a remote code execution vulnerability in the Fastjson Java library. Fastjson is used by almost 5,000 other open-source Java projects.
Hardcoded backdoor: SEC-Consult researchers said they found a hidden hardcoded backdoor user account (CVE-2022-32985) in industrial-managed FTTO GigaSwitch devices from Nexans. The vendor released patches.
Infosec industry
YARAify: The Abuse.ch project has launched YARAify, a central hub for scanning and hunting files at scale using YARA rules. Announcement and project description here.
RSA 2022: There's at least 109 cases of people getting infected with COVID-19 after attending the RSA security conference this year. Makes you think twice about attending other conferences this year.
So far we have at least 109 self-reported cases from RSA. Which might not sound like very many, but its over 20% of the survey respondents so far.
— Ray [REDACTED] (@RayRedacted) 4:04 AM ∙ Jun 16, 2022




