Risky Biz News: FTC orders MoneyGram to return $115 million to scammed victims
In other news: New MortalKombat ransomware; Dalbit APT attacks go after Korean groupware software; the February Patch Tuesday is here.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The US Federal Trade Commission has ordered international payments service MoneyGram to return $115.8 million to nearly 40,000 customers defrauded by scammers.
The FTC says MoneyGram failed to crack down on scammers abusing their payment system for almost two decades.
The order to return funds to customer accounts comes after MoneyGram failed to follow previous settlements with the FTC and the Justice Department to improve its anti-fraud systems.
Previously, the FTC and the DOJ found that between 2004 and 2008, MoneyGram either knew or failed to crack down on more than 1,200 of its agents that accounted for the vast majority of fraudulent transactions on its platform.
These fraudsters would operate as telemarketers, contact consumers in the US and Canada, and trick them into wiring funds via the MoneyGram service. These groups used schemes like guaranteed loans, secret shopper programs, or told victims they won the lottery and needed to secure prizes.
In a 2009 action against MoneyGram, the FTC said the company "knew that its system was being used to defraud people but did very little about it," and that in some cases, even some of its agents in Canada participated in the schemes.
The FTC ordered MoneyGram to refund $18 million to consumers in 2009, and the company entered into a deferred prosecution agreement in 2012, promising to improve its anti-fraud and anti-money laundering systems.
In 2018, both the FTC and DOJ fined MoneyGram $125 million for failing to comply with the previous agreement. At the time, the FTC said MoneyGram had again failed to crack down on agents that had a large number of suspicious transactions, even in cases where 50% of transactions taking place at an agent location were found to be fraudulent.
Furthermore, in 2018, the FTC found that MoneyGram's computerized monitoring system, designed to spot and stop fraudsters from using its service, stopped working for a whopping 18-month period between 2015 and 2016, during which time known fraudsters abused MoneyGram unhindered.
The new round of $115.8 million consumer refunds is for US and Canadian consumers who submitted claims during 2021. A special website has been established for victims who lost funds to scammers and submitted a claim: moneygramremission.com.
Breaches and hacks
Namecheap incident: Domain registrar Namecheap says that hackers breached its account with email delivery service Sendgrid and abused it to send out DHL and Metamask-themed phishing campaigns. Because the emails had the proper DKIM signatures, they bypassed many email spam and security filters. Namecheap says it has shut down its Sendgrid account, which has caused downtime for some of its services that delivered authentication codes, helped with device verification, and with account password reset emails.
Al-Toufan attacks: A hacking group going by the name of al-Toufan (The Flood in Arabic) has taken down the websites of Bahrain's international airport, state news agency, and chamber of commerce. The attack, most likely DDoS, took place on the 11-year anniversary of the country's 2011 Arab Spring pro-democracy protests, brutally repressed by the government. [Check out AP's report on the incident]
General tech and privacy
Ubuntu RTOS: Canonical has released the first version of its Real-time Ubuntu OS, a stripped-down version of the Ubuntu kernel designed to be used on lightweight devices with tiny hardware and stringent low-latency requirements.
"From vision AI and 5G to robotics and autonomous vehicles, many of the solutions we develop rely on a real-time OS for ultra-low latency with end-to-end security. We are excited to see Real-time Ubuntu, an enterprise-grade, Linux operating system that will accelerate these markets."
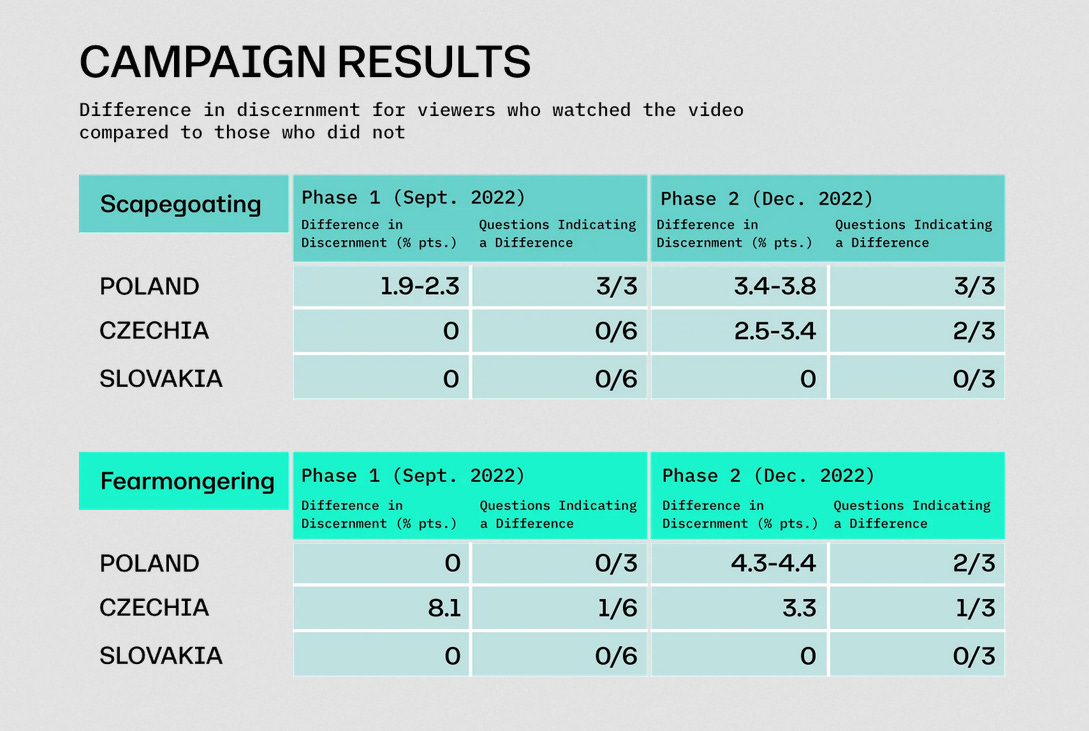
Jigsaw disinformation study: Google's Jigsaw division says it ran the biggest disinformation pre-bunking experiment on social media. The experiment took place last year, in two phases, in September and December, and targeted audiences in Poland, Czechia, and Slovakia. Jigsaw says it created videos to debunk Russian disinformation campaigns that tried to scapegoat Ukrainian refugees for the escalating cost of living. Jigsaw says the videos ran on Facebook, YouTube, Twitter, and TikTok, and reached large percentages of Czech, Slovakian, and Polish users, varying from 50% to 80% of that country's total internet population. Nonetheless, despite the campaign's reach, Jigsaw says it saw only a small improvement in the number of internet users capable of spotting disinformation. Similar experiments are also planned to run in Germany and India later this year.
"Ultimately, we found the share of viewers who could correctly identify these misinformation tactics increased by as much as 8 percentage points after viewing one of these videos. The full results are reported in the tables below."
Government, politics, and policy
Horny DOD: The Office of the Inspector General for the Department of Defence has found that DOD employees often flaunt rules and install unauthorized apps on government devices, exposing themselves to cybersecurity risks. An audit of DOD employee smartphones has found dating apps, third-party VPNs, cryptocurrency apps, Chinese drone apps, games, and apps related to multi-level marketing schemes installed on DOD devices. The DOD-OIG has recommended that the DOD employees remove the apps, remove access to unmanaged app stores, and require DOD employees to forward a complete list of DOD messages sent via unauthorized messaging apps installed on their work devices so officials can address any possible leaks and risks. [More in Gizmodo]
What a massive surprise: Everyone at RiskyBiz is absolutely shocked that the emails of a UK MP who showed support for Ukraine and were allegedly hacked by Russian intelligence services have reached the hands of a former UK politician peddling pro-Kremlin propaganda like "NATO blew up NordStream 2" and "NATO provoked Russian into invading Ukraine."
Sponsor section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year, in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
Cybercrime and threat intel
Lurk member sentenced: A Russian court has sentenced a member of the Lurk cybercrime group to eight years and six months in prison. Russian authorities cracked down on the Lurk gang in May 2016. The gang developed malware that stole more than 2.5 billion rubles from Russian bank accounts. Russian authorities said the suspect, identified as Gulyaeva A.V., helped the gang run its server infrastructure and the software needed for unauthorized money transfers.
Phishing gang detained: Spanish authorities dismantled a cybercrime gang that stole more than €5 million from victims using phishing, smishing, vishing, and other social engineering techniques. The gang used more than 100 fake companies and bank accounts to collect the stolen money. Funds would typically be withdrawn via ATMs, sent abroad, or converted into cryptocurrency. Spanish police say they detained nine suspects in total, with eight arrested in Madrid and one in Miami.
SIM swapper sextortion: Amir Hossein Golshan, a 24-year-old from Los Angeles, used SIM swapping to hijack the Instagram accounts of social media influencers. According to court documents, Golshan extorted the hacked victims for money but also for sexually explicit content, such as striptease videos. Authorities say they discovered a Coinbase account in Golshan's name that held $423,575 in funds but also a bank account that received $23,790 in Zelle payments referencing Instagram account names and verification procedures. The FBI says that in some cases, Golshan also tried to extort some of the victims into going on real-world dates. [Read the original report in Motherboard]
Blender relaunched as Sinbad: Blockchain analysis company Elliptic says Sinbad, a newly launched cryptocurrency mixing service, is very likely a rebranded reincarnation of Blender. The Blender mixing service shut down operations last May after it was sanctioned by the US Treasury for helping North Korean hackers launder hacked funds. Elliptic's findings come days after Chainalysis found that Sinbad had already embroiled itself in controversy after helping the same North Korean hackers launder a new batch of stolen funds—this time stolen from cryptocurrency platform Harmony Bridge in June last year. Elliptic researchers say a number of clues connect Sinbad to the defunct Blender, such as transactions linking Sinbad to Blender-associated wallets and platform backend technical similarities. In addition, Elliptic said that Sinbad has "a clear nexus to Russia," a country with a history of hosting cryptocurrency platforms used in laundering cybercrime profits.
IBM Aspera Faspex attacks: The Shadowserver Foundation is reporting active exploitation of CVE-2022-47986, an unauth RCE in IBM Aspera Faspex servers. The attacks apparently began a day after IBM released patches and AssetNote published a blog post about the vulnerability.
DDoS record: Cloudflare says that over the last weekend, its staff mitigated a record-breaking HTTP DDoS attack of 71 million requests per second (rps). The company says the attack was 35% higher than the previously reported HTTPS-based DDoS record, an attack of 46 million rps, blocked by Google Cloud in June 2022.
npm malware: Check Point's research team says it detected 16 malicious JavaScript packages uploaded on the official npm registry. Researchers say all packages were created by the same author and were designed to download and run a hidden cryptominer on a developer's system. All packages have now been removed.
YouTube USDT crypto scams: WithSecure says it found a massive scam campaign operating on YouTube aimed at defrauding cryptocurrency users. The company says it identified more than 700 YouTube channels that posted thousands of videos advertising websites that pose as Tether (USDT) cryptocurrency investment schemes. The malicious sites urge users to invest their crypto assets for massive returns. WithSecure says that more than 900 users sent $100,000 to these scam sites between July and November 2022, money they will likely never see returned.
Rise of multi-functional malware: In its yearly threat report, Picus Security says it has seen a rise in what it calls "Swiss Army knife" malware, strains that evolved year to year into multi-purpose behemoths. The report was based on analyzing more than half a million malware samples and mapping their capabilities to the MITRE ATT&CK Framework.
Dragos year in review: ICS security firm Dragos has published its year-in-review report. Loads to unpack, but the company says it tracked 2,170 vulnerabilities impacting ICS/OT equipment last year and that ransomware attacks against critical infrastructure sectors continued to increase. [Some of the report's findings are summarized in Cyberscoop]
Malware technical reports
Beep malware: Researchers with MinervaLabs have discovered a new malware named Beep. They named the malware Beep because it uses the Beep Windows API function to delay its execution with a sleep function and avoid detection by security sandboxes. Minerva says it discovered the malware after multiple samples were uploaded on VirusTotal last week. The malware's main function appears to be reconnaissance, to collect data from infected systems.
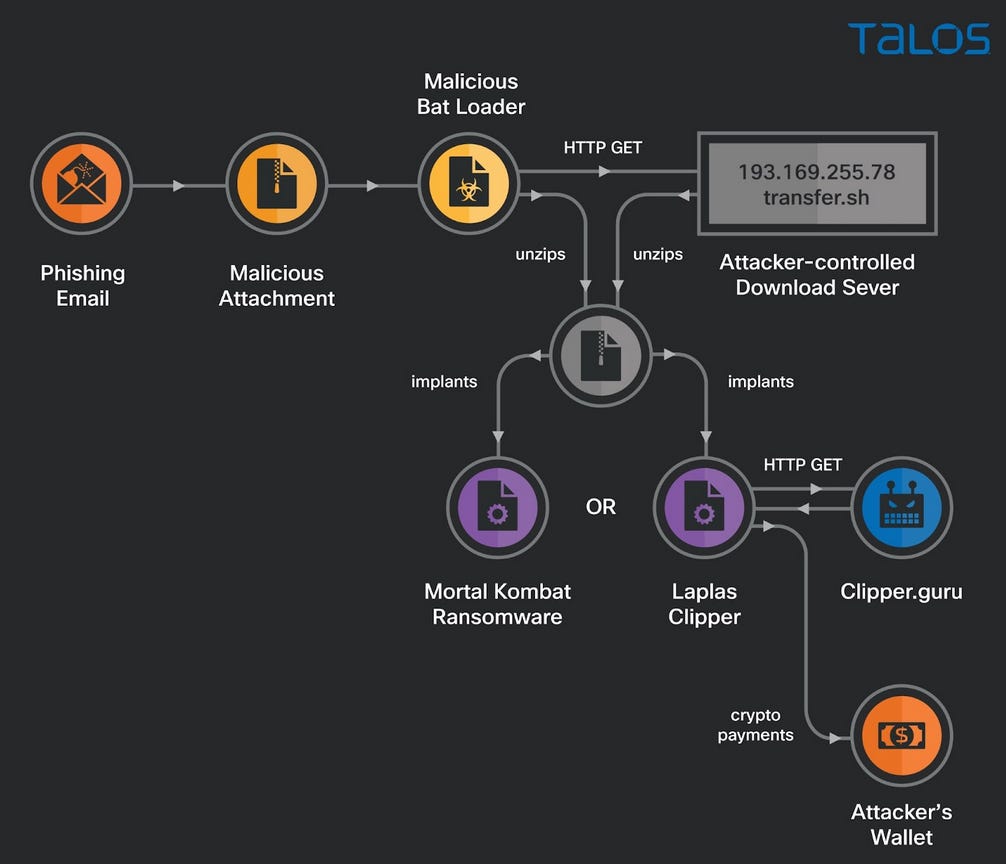
MortalKombat ransomware: Cisco Talos researchers say they are tracking an unidentified threat actor that is using phishing campaigns to deploy a new ransomware strain named MortalKombat. The attacks have been taking place since December 2022. Not all infections ended with a MortalKombat ransomware infection. Cisco says it also saw the group deploy Laplas, a clipper that manipulates the victim's clipboard, replacing copied cryptocurrency addresses with malicious ones. In addition, Cisco researchers say the same threat actor has also scanned the internet for systems with an exposed remote desktop protocol (RDP) port in order to deploy MortalKombat.
APTs and cyber-espionage
APT-C-56 (Transparent Tribe): Qihoo 360 has a report on recent APT-C-56 (Transparent Tribe) campaigns. The report found that APT-C-56 and the SideCopy group used the same infrastructure in operations earlier this year. Both groups have a Pakistan nexus.
"At the beginning of this year, Transparent Tribe and SideCopy were found to use the same infrastructure and use the same theme to target similar targets. They used smuggled intelligence-related lures and disguised Indian Ministry of Defense emails to frequently launch attacks against India. We also discovered its attack activities targeting the foreign trade industry by using external links."
UAC-0096: CERT Ukraine's team has a report on a recent UAC-0096 spear-phishing campaign.
Saaiwc (Dark Pink) APT: Researchers with the Anheng Information Hunting Lab have discovered new attacks carried out by a new APT group they are tracking as Saaiwc, also known as Dark Pink.
ShadowPad expands to Latin America: A Chinese cyber-espionage group known as ShadowPad and DEV-0147 was seen attacking Latin American targets. The attacks, spotted by Microsoft, represent a notable shift in the group's activities, known for its persistent targeting of European and Asian government agencies and think tanks.
Tonto Team: Russian security company Group-IB says that in June 2022, a Chinese APT known as Tonto Team tried to infect two of its employees with malware. The attackers used phishing emails to deliver malicious Microsoft Office documents to the two employees. Group-IB says it detected and blocked the attacks, which were aiming to install the Bisonal.DoubleT backdoor on its systems.
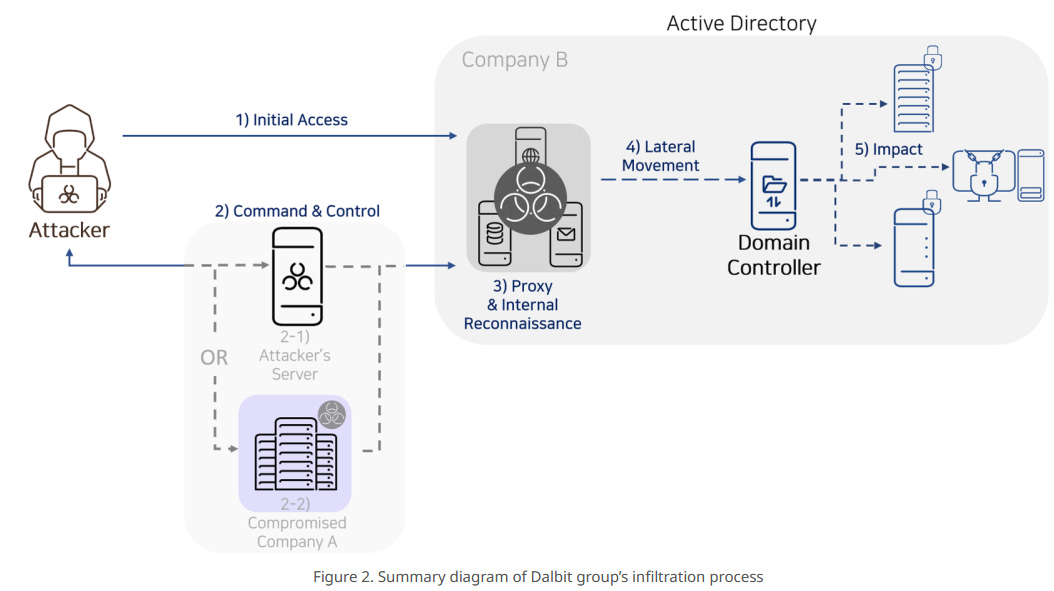
Dalbit (m00nlight) APT: AhnLab has a report on attacks carried out by a Chinese APT group named Dalbit against South Korean companies. The campaign took place in 2022, and AhnLab says that 30% of the infected companies were using the same local Korean groupware software. AhnLab says it wasn't able to tell if the product was vulnerable or if attackers exploited misconfigurations.
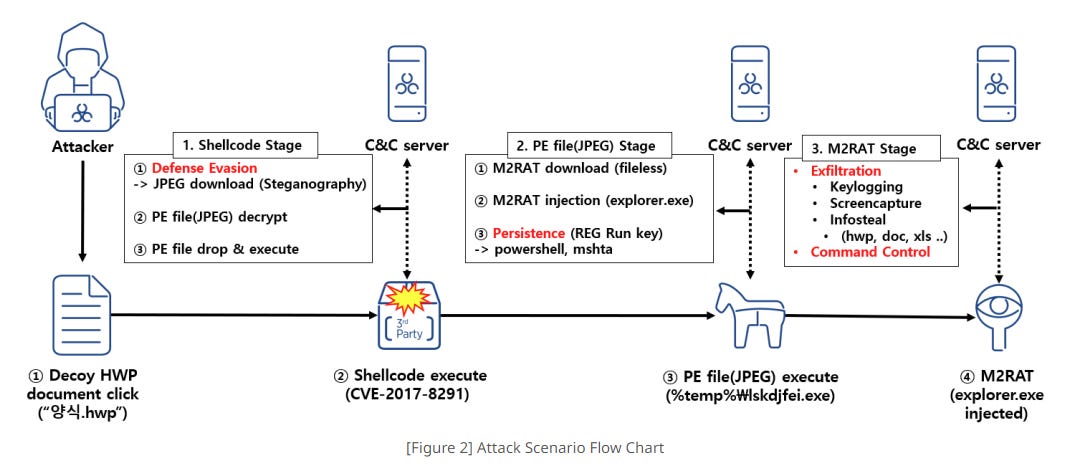
ScarCruft (APT37): The same AhnLab lab has also discovered a new malware strain used in recent attacks by ScarCruft, a North Korean cyber-espionage group also known as RedEyes and APT37. Named M2RAT, the malware was used in attacks against South Korean targets, with the group trying to exploit an old vulnerability in the Hangul word processor to infect targets.
Vulnerabilities and bug bounty
Patch Tuesday: Yesterday was also the February 2023 Patch Tuesday. We had security updates being released by Apple, Adobe, Git, Microsoft, and SAP. The Android project, OpenSSL, and VMWare released security updates last week as well. This month, Microsoft patched 80 vulnerabilities, including three zero-days (CVE-2023-21715, CVE-2023-21823, and CVE-2023-23376). Apple also released security updates that included a patch for an actively exploited Safari (WebKit) zero-day vulnerability tracked as CVE-2023-23529.
cURL audit findings: Trail of Bits has published the findings of its cURL audit from last year. The audit found four issues, including two that received CVE identifiers.
WD NAS RCE: Almost a year and a half after the Pwn2Own Austin 2021 hacking contest, Synacktiv has published the technical details of an RCE exploit they used during the competition against a Western Digital MyCloudHome NAS.
"Our exploit was unusual because triggering the vulnerability required to mess with the remote TCP stack, so we wrote our own [TCP stack]."
Infosec industry
PT update: Positive Technologies, one of the largest Russian cybersecurity companies, has closed down its Czech (Brno) and UK (London) offices. The closures took place at the end of 2022, according to an RBC report. PT's western business died out long before Russia's invasion of Ukraine, in April 2021, after it was sanctioned by the US Treasury for providing hacking technology to the FSB and using its security conference as an FSB and GRU recruiting hub. Besides Russia, the company still has offices in Kazakhstan and says it plans to open new offices in other countries.
Azure canary tokens: Thinkst has launched a canary token for Azure infrastructure. Named the Azure Login Certificate Token, the token will alert system administrators when a threat actor finds the token on one of their environments and tries to use it to move laterally across a network, allowing sysadmins to quickly determine which of their internal segment/server is most likely misconfigured, exposed, or has been compromised.
Pwn2Own Miami hacking contest: The Pwn2Own ICS-themed hacking contest is taking place this week in Miami. You can follow this ZDI blog entry for live updates.
OneKey vulnerability: Cryptocurrency wallet maker OneKey says it fixed a vulnerability in its product that would have allowed threat actors to crack its hardware wallets in one second. The issue was discovered and privately reported to the company by security firm Unchiphered (see video below) and apparently also impacts other yet-to-be-named wallet vendors (see here for future updates).
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




