Risky Biz News: France says cyber deterrence doesn't work
In other news: LockBit gang member arrested in Canada; major data breach in Hungary; Microsoft links the Sandworm APT to the Prestige ransomware.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The French government has exhibited a rare showing of truthfulness and clarity and has admitted in a national security planning document published this week that cyber deterence doesn't work and government officials should plan accordingly.
"There is no way to envisage a cyber shield that would thwart any cyber-attack on France, but strengthening its level of cyber security is essential to prepare the country for more cyber threats. Similarly, the application of a deterrent approach in cyberspace that would force any attacker to restrain himself against France is illusory," the French president's office said on Wednesday, in a document titled the National Strategic Review 2022.
Instead, French officials believe that while full deterrence isn't possible, a coordinated and harsh reply could make attacks more costly for an attacker—may it be from a cyber-criminal or intelligence/espionage background.
Officials suggest this could be done by "adopting response strategies that mobilize all the levers of the State, both European and international."
As a result, French officials propose a plan of action centered around cyber resilience of the French ecosystem—which the French government sees as "a condition of sovereignty"—rather than one focused on the deterrence of external threats, one it clearly doesn't see succeeding in any way or form.
In hindsight, it also doesn't take a genius to see that deterrence doesn't actually work beyond producing some cool headlines and academic papers. Over the past few years, we've seen sanctions and public exposés (doxxings) of both cybercrime and APT groups merely slow down some operations. Cybercrime groups disbanded or rebranded, but members continued their "careers," while APT groups trudged on regardless of the international blow-back. Deterrence will never work if the other party doesn't give a s**t—and APTs and ransomware gangs are experts at that, especially the ones in countries with no extradition treaties.
Breaches and hacks
Major breach in Hungary: A hacking group named Sawarim has breached eKRÉTA, the company behind a school management platform widely deployed across Hungary. The platform is believed to store the personal details of more than 720,000 Hungarian students, aged between 6 and 18 years. While the hackers told a local news outlet they don't plan to release any of the students' personal details, they have already begun leaking some of the software company's source code, internal chats, and email messages, including with state officials.
Medibank leaks begin: After Medibank said it wouldn't pay an extortion demand to a ransomware crew that hit its systems last month, the group—tracked as BlogXX—has started leaking the personal data of some of the healthcare provider's customers. In light of the new development, the Australian Federal Police said it took "immediate measures," including covert techniques and the scouring of cybercrime sites to identify individuals abusing this data.
Silverstone F1 circuit incident: In one of the weirdest targets to ever get hit by ransomware, the operators of the Silverstone Formula 1 circuit appear to have been hit by the Royal ransomware gang.
Compensation for Yandex.Food users: The 13 users who sued Yandex after their personal information was stolen and dumped online were awarded a 5,000 rubles ($82) compensation (each) for their troubles by a Moscow court this week. Each had initially asked for at least 100,000 rubles ($1,650).
General tech and privacy
Apple limits AirDrop in China: iPhone users in China will not be able to use the Airdrop file-sharing feature using the "Share to Everyone" option for more than 10 minutes. The change has rolled out to everyone this week with the release of iOS 16.1.1. The feature has been widely abused in recent weeks to secretly share anti-government posters and materials criticizing China's leader Xi Jinping. It was also used in previous years to share instructions and other helpful materials during the Hong Kong anti-government protests. There is rampant—and obviously well-grounded—speculation that Apple might have caved in to a request/threat from the Chinese government. There is no technical reason to limit that feature to only 10 minutes. It's actually a dumb idea since it will prevent the successful sharing of any larger files. Apple also told Bloomberg it also plans to expand this feature globally next year, in a serious hit to protesters and a helpful hand to all oppressive governments around the world.
Kaspersky to discontinue VPN service in Russia: Russian security company Kaspersky said it would discontinue its Kaspersky Secure Connection VPN application for its Russian customers. The free version will be discontinued on November 15, while the paid/commercial version will end service at the end of the year. The news comes after the Russian government has spent the last year banning various VPN services within its borders. [English coverage in BleepingComputer]
Elon's clueless, part #917,663: Elon's plan to allow users to verify themselves by purchasing a Twitter Blue subscription is not going as planned, with several "users" already running scams or personal attacks on the platform. In the meantime, Twitter's Chief Information Security Officer, Lea Kissner, has resigned, along with the company's Head of Trust and Safety Yoel Roth, Chief Compliance Officer Marianne Fogarty, and Chief Privacy Officer Damien Kieran. Rest in pieces, Twitter!
It took me less than 25 minutes to set up a fake anonymous Apple ID using a VPN and disposable email, attach a masked debit card to it (with the address being Twitter's HQ), and get a verified account for a prominent figure. Just think what a nation-state or bad actor could do...
— Jack Lawrence (@JackMLawrence) 11:03 PM ∙ Nov 9, 2022
El*n M*sk stated imposters, Threat Actors, and trolls, would be deterred by the $8 fee for the checkmark.
— vx-underground (@vxunderground) 3:15 AM ∙ Nov 10, 2022
In less than 24 hours this has been proven to be false.
Twitter Blue is going about as well as everyone predicted, and it's an amazing spectacle to watch. Like a train crash filled with glitter.
— matt ratt (@MisterRatt) 9:07 AM ∙ Nov 10, 2022
Government, politics, and policy
DDOS attacks on election day: Some websites operated by the Mississippi state government were knocked offline during the US midterm elections on Tuesday following DDOS attacks claimed by pro-Russian hacktivist groups. None of the attacked websites were involved in the vote and vote counting process.
Not a cyber-attack: Officials from Suffolk County in the state of New York dismissed rumors of a cyber-attack on their infrastructure on Tuesday, on election night, after some election workers had to collect voting tallies on memory cards and drive to a central office to upload the results on state computer servers. Officials said this happened because "electronic security measures put in place to protect elections systems from cyber attacks had overtaxed and slowed an older operating system," which initially made election authorities believe they were the victim of a cyber-attack.
Cyber.org Range expands nationwide: A Louisiana pilot program called Cyber.org Range—designed to teach K-12 students cybersecurity skills—announced it would expand to all 50 US states after receiving funding, including from the US Cybersecurity and Infrastructure Security Agency.
"The CYBER.ORG Range is accessible to all K-12 students but is primarily geared toward high school students interested in learning core cybersecurity concepts and curriculum."
Tornado Cash sanctions: The US Treasury Department has updated its sanctions against the Tornado Cash cryptocurrency mixing service and has formally tied it to entities linked to North Korea's nuclear weapons program. The Treasury initially sanctioned Tornado Cash in August for its central role in laundering funds stolen by North Korean hackers from multiple cryptocurrency platforms. A conglomerate of cryptocurrency platforms sued the Treasury for its sanctions, and this week's update looks like a step the Treasury is taking to defend its initial sanctions in court by releasing more information about how the platform was used by North Korean entities.
Cyprus Parliament calls for investigation: After the PEGA commission said in a report on Tuesday that Cyprus acted as a hub and central role for several commercial spyware operations, the Cyprus Parliament opened an inquiry into the matter.
Sponsor section
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. The company launched a new product called Sensitive Command Canarytoken, a simple canary token that sends an alert every time any command you choose as "sensitive" or "malicious" is executed on your host.
Cybercrime and threat intel
LockBit operator arrested in Canada: Mikhail Vasiliev, 33, a dual Russian and Canadian national, was arrested in Canada for his alleged participation in the LockBit global ransomware operation. According to court documents, Vasiliev appears to have been one of the LockBit gang’s affiliates, a member that buys access to corporate networks and deploys the gang’s ransomware. US authorities are seeking his extradition to the US to face charges for attacks on US organizations.
Scam gang disrupted in Ukraine: Ukraine's Cyber Police said it raided and disrupted a local company that operated a call center linked to phone scams all over the world that defrauded users out of more than €200 million a year.
Concerns about TrustCor: Concerns have been raised about browser vendors trusting certificates issued by TrustCor, a Panamanian company with deep links to companies from the surveillance industry. [Original report here, WaPo coverage here]
IPFS adoption: Cisco Talos said it observed multiple malware campaigns that leverage the IPFS peer-to-peer protocol to host their malware payloads and phishing kit infrastructure for ongoing attacks. Cisco's report comes after Trustwave saw a similar spike in IPFS adoption over the summer after several cloud providers added support for the protocol on their servers. The IPFS protocol is widely used by blockchain platforms, according to Cisco.
Crypto-mining landscape: Antivirus maker Kaspersky published a report this week on the landscape of crypto-mining malware. Some of the report's main findings are below.
- In Q3 2022, nearly one in six cases of exploiting well-known vulnerabilities were accompanied by a crypto-miner infection.
- Q1 2022 saw the biggest number of users (over 500,000) affected by malicious mining software and the smallest number of new malicious miner variants.
- The country with the highest number of attacked users was Ethiopia, where cryptocurrencies are banned officially.
- Monero (XMR) is the most popular cryptocurrency for malicious mining.
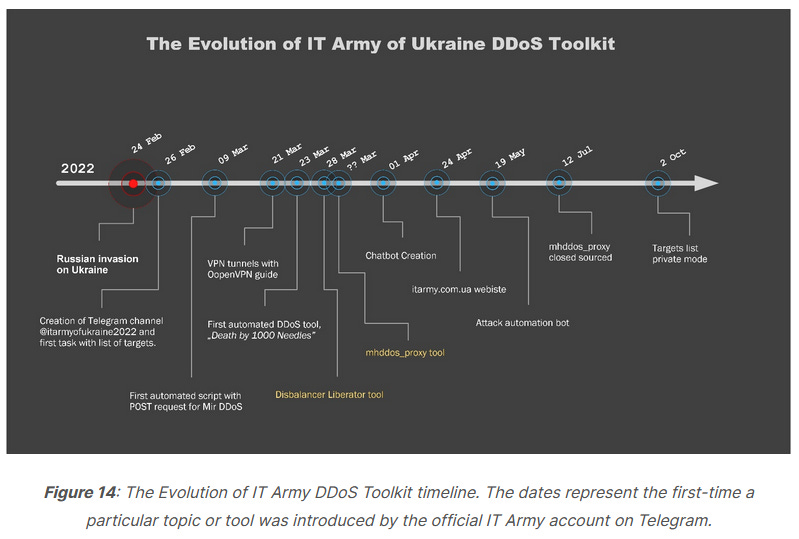
IT Army of Ukraine: Trustwave has a report recapping some of the IT Army of Ukraine's recent operations.
Malware technical reports
Ois[.]is redirection campaign: GoDaddy's Sucuri team said it identified a massive spam operation where a threat actor has compromised more than 15,000 websites and planted malicious code to redirect users (via the ois[.]is domain) to spammy Q&A sites. Sucuri researchers believe this campaign is the work of a black-hat SEO spam group meant to boost the ranking of the spammy Q&A domains in search results.
Venus ransomware: The security team of the US Department of Health and Human Services has published a report [PDF] on the new Venus ransomware, which they say has hit at least one US healthcare organization since it was first spotted in the wild this August. The ransomware is known for targeting systems and networks that run unprotected RDP endpoints, which it uses as entry points for the attack.
Xenomorph on the Play Store: The Xenomorph Android banking malware has been found inside apps on the Play Store, according to Zscaler. Finding malware in Play Store-hosted apps is becoming a trend again.
JSP web shell targeting Zimbra: Out of the blue and with no context, CISA published a malware analysis report (MAR) on a JSP web shell targeting Zimbra.
"Four CVEs are currently being leveraged against ZCS: CVE-2022-24682, CVE-2022-27924, CVE-2022-27925 chained with CVE-2022-37042, and CVE-2022-30333."
APTs and cyber-espionage
Worok: Avast researchers have published their own analysis on the tools used by Worok, a relatively new APT first documented in an ESET report this September, linked to attacks that targeted energy companies in Central Asia and public sector entities in Southeast Asia.
Earth Longzhi: Trend Micro has published a report on Earth Longzhi, a sub-group of the larger APT41 Chinese cyber-espionage group. According to Trend Micro, Earth Longzhi attacks targeted government, infrastructure, and health industries in Taiwan and the banking sector in China.
TA423/Leviathan/RedLadon: At the CyberWarCon conference on Thursday, Proofpoint researchers said they linked cyber-espionage operations carried out by TA423 (also known as Leviathan and RedLadon) against Malaysian off-shore energy companies to kinetic maritime intimidation operations conducted by the Chinese Coast Guard in the South China Sea. See original research here.
Iridium/Sandworm: Also at the CyberWarCom conference on Thursday, Microsoft said it linked the attacks with the Prestige ransomware against organizations in Ukraine and Poland to a Russian state-sponsored group it tracks as Iridium, also known as Sandworm. At the same conference, Microsoft researchers also presented research about other threat actor groups like BROMINE (aka Berserk Bear) (on their abuse of data center infrastructure management interfaces), ZINC (on their use of social engineering campaigns built around weaponized legitimate open-source software), and several Chinese state actors (on their use of SOHO routers to obfuscate operations).
Ravin Academy: PwC has published additional threat intelligence on Ravin Academy, the Iranian company recently sanctioned by the US Treasury Department for its role in training Iran's cyber operators. PwC believes Ravin Academy helped train at least some of the members of the Yellow Nix cyber-espionage group.
Vulnerabilities and bug bounty
CISA guide: The US Cybersecurity and Infrastructure Security Agency published this week a guide on Stakeholder-Specific Vulnerability Categorization (SSVC), a vulnerability management methodology that assesses vulnerabilities and prioritizes remediation efforts based on exploitation status, impacts on safety, and prevalence of the affected product in a singular system.
Security updates: On the trail of Patch Tuesday, security updates have also been released for Apple and Cisco devices and the Google Cloud Platform.
Plesk vulnerability: Security firm Fortbridge has published details about a vulnerability in the Plesk web hosting automation software, which the company says was able to compromise via four CSRF vulnerabilities in its REST API.
CVE-2022-41049: Security researcher Kuba Gretzky published an analysis of CVE-2022-41049, a Mark-of-the-Web bypass patched earlier this week by Microsoft.
Major Google Pixel lock screen bypass: Security researcher David Schütz found a way to bypass the lock screen of all Google Pixel smartphones that works against all forms of lock screen protection. The attack works only if the attacker knows a SIM card's PUK code. The vulnerability was patched in this month's Android security updates, as CVE-2022-20465, and Schütz said he received a $70,000 bug bounty reward from Google for his finding.
Wow wow wow, all police departments in the world can now bypass Android lock screen with this simple procedure. (Assuming your phone is not yet patched) 😱
— Marcus Maciel (@underlinux) 2:56 PM ∙ Nov 10, 2022




