Risky Biz News: Four PR firms are behind a Chinese propaganda network
In other news: US telcos learned of Salt Typhoon breaches from Microsoft; Russian hackers pull off a crazy WiFi attack; hacktivists leak data from Andrew Tate's website.

This newsletter is brought to you by Stairwell. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
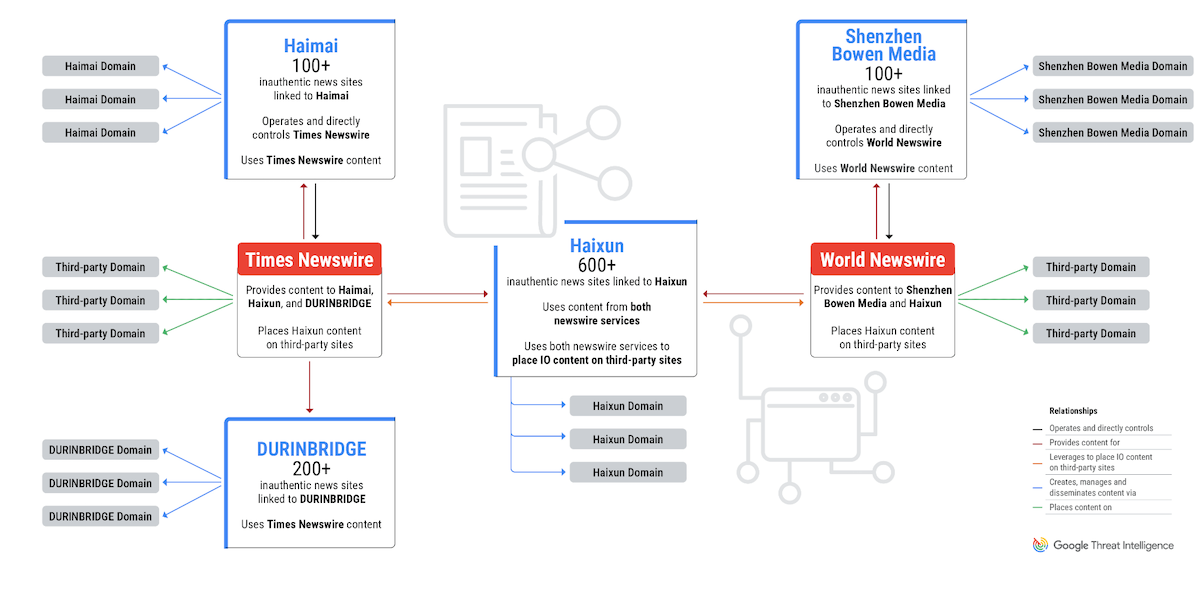
Google has removed from its search and news index hundreds of domains that were operated by four Chinese-based PR firms that published pro-PRC propaganda to international audiences.
The companies ran two newswire services where they published articles and collectively pulled content to distribute through their own "independent" news websites.
The articles were low-quality rewordings of stories from Global Times, a PRC state-controlled media outlet, designed to push China's views on various topics through smaller news sites and give the impression of mass consensus and authenticity.
News stories covered the PRC's territorial claims over the South China Sea, Taiwan, controversies over the Xinjiang region, coverage of the COVID-19 pandemic, conspiracy theories, and even ad hominem attacks targeting regime critics.
Many of the articles are repetitive, and they are mixed with stories on other benign topics in an attempt to hide the obvious propaganda inside a stream of what looks to be legitimate news reporting.
Google says that even if the four PR companies are separate legal entities, they all operated in a similar fashion, suggesting a form of coordination was taking place.
"Although the four PR firms discussed in this post are separate from one another, they operate in a similar fashion, bulk-creating dozens of domains at a time and sharing thematically similar inauthentic content. [...] By using private PR firms, the actors behind the information operations (IO) gain plausible deniability, obscuring their role in the dissemination of coordinated inauthentic content."
Google, through its TAG and Mandiant divisions, has named three of the PR firms. It's unclear why the company has not named the fourth but says it tracks this entire cluster as GLASSBRIDGE due to their modus operandi similarities.
- Shanghai Haixun Technology
- Shenzhen Haimai Yunxiang Media
- Shenzhen Bowen Media
- [unnamed PR firm] tracked as DURINBRIDGE
Two of the PR firms (Haixun and Hamai) were previously ousted by South Korean intelligence agency NIS in November of last year. NIS said the two PR firms ran 38 websites that blasted Korean audiences with PRC propaganda.
Google says that's part of the cluster's entire modus operandi, with the news sites targeting both local and Chinese-speaking audiences in several countries. So far, Google has found websites targeting Brazil, India, Japan, Kenya, Malaysia, Saudi Arabia, Singapore, Spain, Russia, Thailand, Qatar, and Vietnam.
The cluster relied on Google search and news to promote their articles, on YouTube channels, and on recruiting and paying freelancers via Fiverr to promote their articles on social media.
Google's research confirms a CitizenLab report from February this year that also tied the news sites to PR firms and linked some of the PR firms' activity to each other.
A recent Sekoia report published earlier this month claimed that China's Ministry of Public Safety (MPS), the country's internal police force, is mainly responsible for running most of China's influence operations—which may provide an initial place to look for who's paying the PR firms.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
FBI notifies ~150 Salt Typhoon victims: The FBI has notified fewer than 150 victims who were targeted by a Chinese espionage group named Salt Typhoon. The group spied on victims after breaching the lawful intercept systems of four major US telecommunication providers. According to the Washington Post, most of the victims are located in the DC area. According to the New York Times, the US government and the telcos learned of the breach after Microsoft notified them of anomalies on their networks. The anomalies included data on Salt Typhoon servers that traced back to US telco nodes. Government officials have also blamed the companies for being too slow to upgrade nodes, some of which date from the 70s and 80s.
NHS leak: The personal records of 1.1 million NHS employees were leaked online due to a misconfiguration in the Microsoft Power Pages platform. The leak was discovered by security firm AppOmni and exposed email addresses, phone numbers, and home addresses. AppOmni says the NHS was one of several companies that leaked data via websites built on the Microsoft Power Pages platform. The company says the leaks took place because website admins misunderstood how access controls work on the Power Pages platform and exposed private data via their websites' APIs. [h/t DataBreaches.net] [This story has been corrected from "Irish NHS" to just "NHS"]
IGT cyberattack: A cyberattack has crippled the IT systems of International Game Technology, one of the Top 20 largest gambling companies in the world. The hack took place last Sunday, on November 17. IGT says the hack affected internal systems and applications, although it's unclear if this will affect the company's bottom line. [Additional coverage in The Record]
Yakuza victim data leak: A local government resource for helping Japanese citizens cut ties with organized crime was successfully phished in a tech support scam. [Additional coverage in DarkReading]
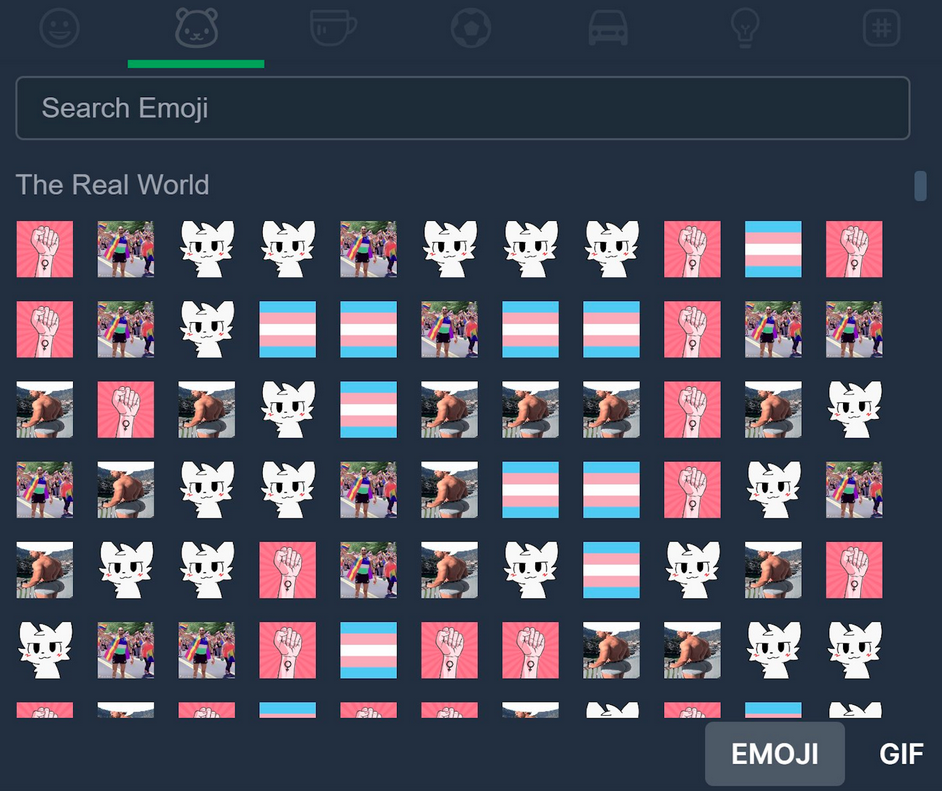
The Real Word hack: Hackers have breached the website of The Real World, an online course founded by Andrew Tate. The hackers leaked the email addresses of 325,000 users and flooded the site's main chatroom with LGBTQ and feminist-themed emojis. The platform was previously known as Hustler's University and is one of Tate's main revenue streams. [Additional coverage in The Daily Dot]
General tech and privacy
Appin SLAPP lawsuits: The Reporters Without Borders organization has published a deep dive into SLAPP lawsuits filed by Indian hacker-for-hire company against news organizations across the globe that covered its business.
"This Reporters Without Borders (RSF) investigation discovered that at least 15 media outlets worldwide received these notices, and five have been subjected to legal proceedings."
Glovo fine: Italy's data protection agency has fined Foodinho €5 million for tracking the geolocation of its drivers outside of working hours. The agency has also banned the company from processing drivers' biometric data, which the company uses for driver authentication. Foodinho is part of the Glovo group of food delivery companies. This is the company's second fine in Italy. It was also fined €2.6 million in 2021 for using algorithms to measure employee performance.
Office AI data collection: Looks like Microsoft has enabled an option on user accounts to allow itself to collect data from Word and Excel to train its AI models.
Microsoft blocks Win11 update rollout: Microsoft has blocked the rollout of its new Windows 11 24H2 operating system update on systems where Ubisoft games are installed after it received feedback that the update was crashing the games. Known affected games include:
- Assassin's Creed Valhalla
- Assassin's Creed Origins
- Assassin's Creed Odyssey
- Star Wars Outlaws
- Avatar: Frontiers of Pandora
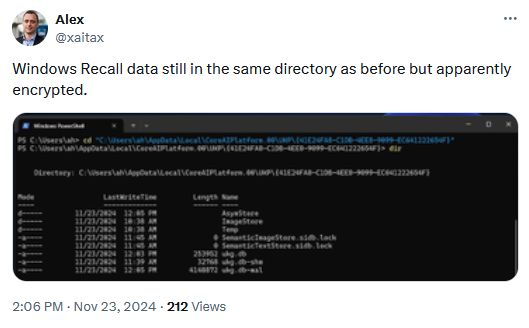
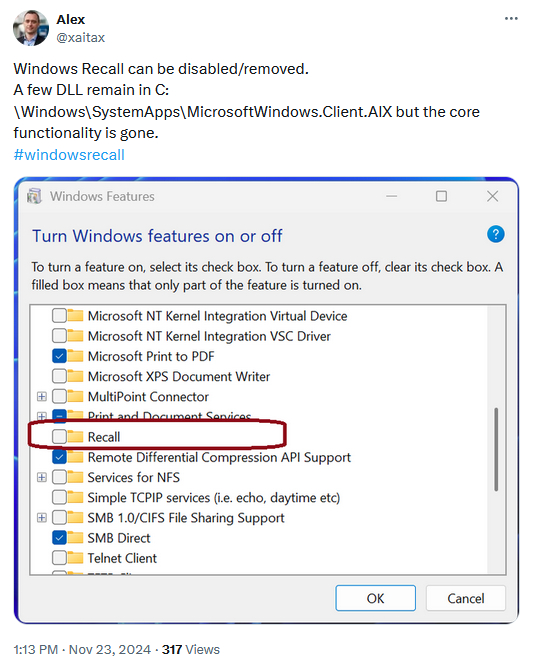
Microsoft re-adds Recall: Microsoft has re-added the Recall AI screenshotting feature back into Windows 11 Insider builds. Microsoft pulled Recall in June after massive public backlash and delayed its return twice this fall. According to security Alex Hagenah, Recall can now be disabled, and its data is encrypted—unlike its first iteration, where users couldn't disable it, remove it, and its data was sitting in cleartext on disk for anyone to take.
Government, politics, and policy
Microsoft urges Trump to be tougher on foreign cyber actors: Microsoft President Brad Smith has urged the incoming Trump 2 administration to be tougher on Chinese, Iranian, and Russian cyber actors targeting the US. Smith said the Biden administration had made progress, but "more steps are needed." [Additional coverage in FT]
US Cyber Force disagreements: CNBC has published an analysis of what happened behind the scenes at the Pentagon that led to the DOD pulling its support for the creation of a separate cyber force in the US armed forces.
Senators demand Verisign monopoly investigation: Two US senators have asked the US government to investigate VeriSign over its "predatory pricing" of .com domains. US Senator Elizabeth Warren of Massachusetts and Congressman Jerry Nadler of New York have asked the Department of Justice and the National Telecommunications and Information Administration for a formal investigation in a letter sent last week. The two say VeriSign has increased .com domain prices by 30% even if its services remained the same. The two described the price hike as monopolistic behavior. [More in WIRED]
Senators want FCC to mandate telecom wiretap security rules: A US senator urged the Federal Communications Commission to write new rules and mandate cybersecurity rules for telecom lawful intercept wiretapping systems.
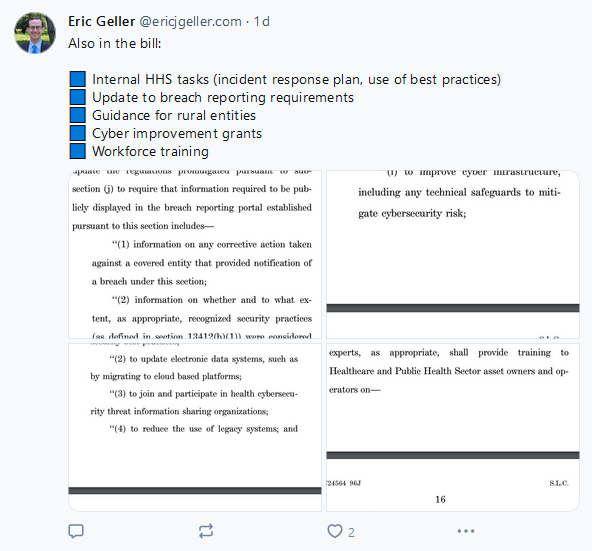
Health Care Cybersecurity and Resiliency Act: Four US senators (Cassidy, Cornyn, Hassan, and Warner) have introduced a bill [PDF] in the Senate to improve cybersecurity in the healthcare sector. The Health Care Cybersecurity and Resiliency Act of 2024 will introduce basic cybersecurity standards for the healthcare sector and allocate grants to health entities to improve their cybersecurity posture. The bill also updates data breach reporting requirements and will provide training and guides for rural health entities. Basic cybersecurity requirements will include the use of MFA, health data encryption, and conducting security audits and penetration tests. [Additional coverage in CyberScoop]
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Mike Wiacek, CEO and founder of Stairwell, about the occasionally dysfunctional relationship between IT and security teams. Mike talks about how security vendors need to reach out to turn IT teams into allies.
Arrests, cybercrime, and threat intel
Base station smisher detained in Thailand: Thai authorities have arrested a 35-year-old Chinese man for sending over a million SMS scam messages. Officials say the suspect was driving around Bangkok using a mobile radio base station installed in his car that sent out the SMS messages posing as AIS, Thailand's biggest internet service provider. The suspect was part of a larger group that registered local companies to obtain phone numbers and spam Thai citizens. [Additional coverage in the Thai Examiner]
Vietnam arrests infostealer gang: Vietnamese officials have detained 20 suspects back in May linked to infostealer malware campaigns. In a report last week, security firm Group-IB says the suspects appear to be behind the VietCredCare infostealer, which has seen less activity over the past several months. DuckTail, which is another Vietnam-based infostealer operation, has continued attacks and the malware also received several updates since the arrests.
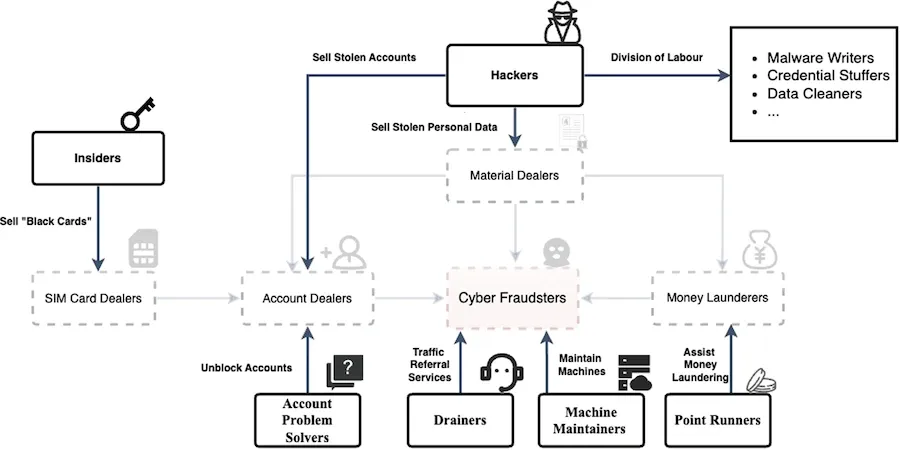
Chinese cybercrime: Oxford researcher Qiaoyu Luo has published a whitepaper analyzing the Chinese-speaking cybercrime ecosystem.
Telco and fin campaigns: EclecticIQ researchers have published a write-up on a phishing campaign targeting telcos and financial companies in the US and Canada.
Avast Anti-Rootkit driver abuse: Trellix researchers have spotted a threat actor installing an older version of the Avast Anti-Rootkit driver to exploit and disable antivirus software on targeted systems. The attacks are part of a recent trend of using BYOVD and AV killer tools in malware deployments.
PyPI attack: DevSecOps company Phylum has discovered malware inside a Python library named "aiocpa" that contained malicious code to steal private keys. The keys were sent to a Telegram when users initialized the library. Phylum says the malicious code was only included in the library's PyPI version but not its GitHub repo in order to avoid detection during public code audits.
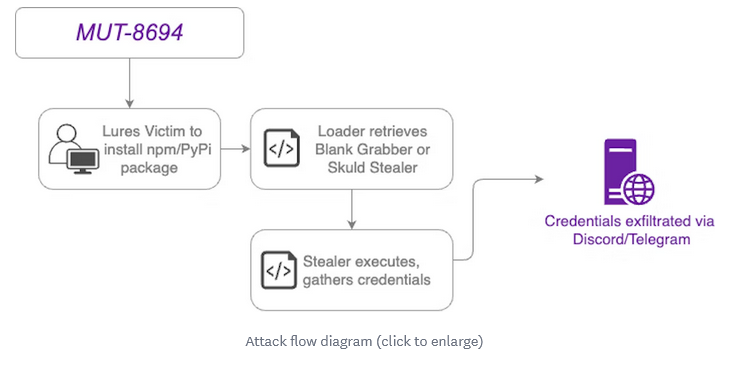
MUT-8694: Datadog looks at MUT-8694, a threat actor that planted malicious packages on npm and PyPI containing a version of the Blank Grabber or Skuld Stealer infostealer.
Malware technical reports
SMOKEDHAM: TRAC Labs has published a report on SMOKEDHAM, a backdoor used by a former Darkside and Lockbit ransomware affiliate tracked as UNC2456. The malware is currently deployed on victim networks via phishing emails.
BlackBasta ransomware: Red Sense has published a report on the evolution of the BlackBasta ransomware group.
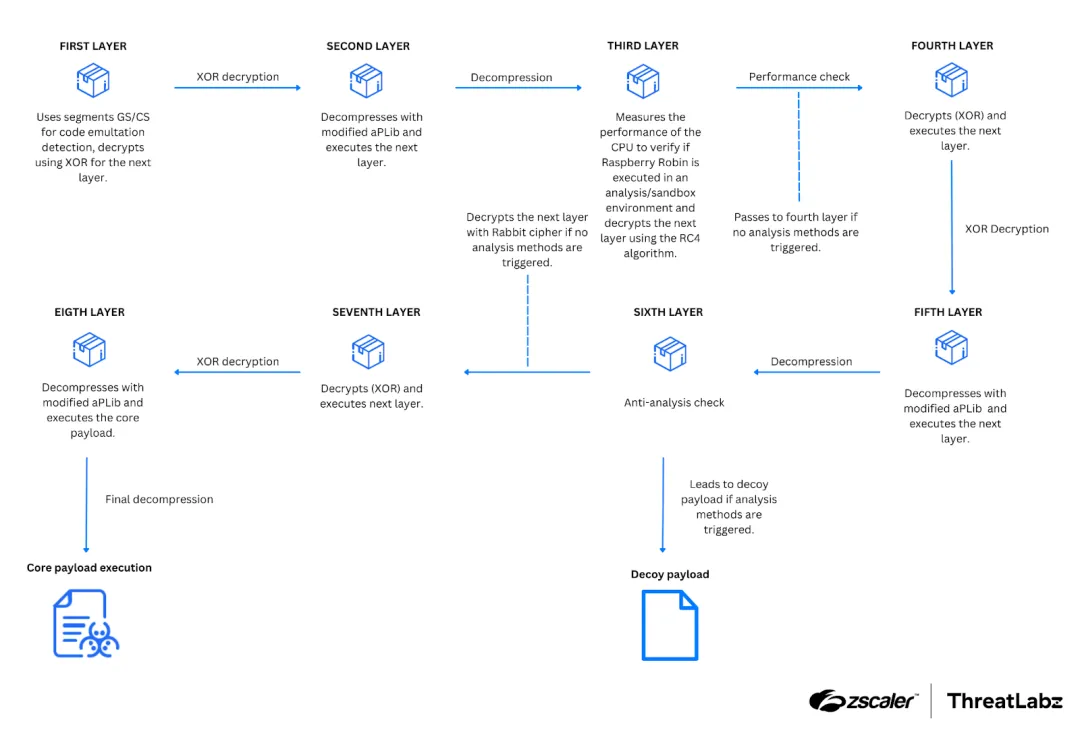
Raspberry Robin: Zscaler has published a report on the eight layers of obfuscation used by the Raspberry Robin malware, also known as the Roshtyak.
RobotDropper: BlackBerry has a report out on RobotDropper, a new dropper first spotted in malspam campaigns this August. Its primary clients appear to be infostealers.
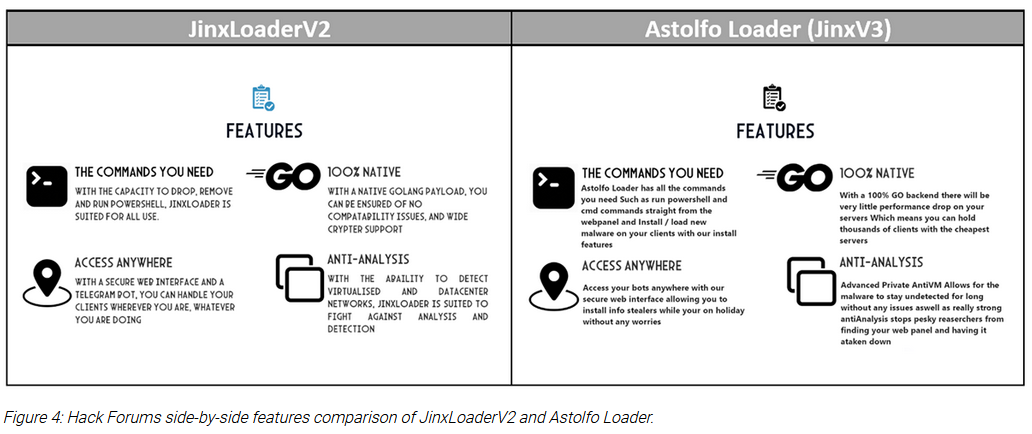
JinxLoader: The same BlackBerry team also analyzes JinxLoader, a new Go-based malware loader typically distributed via phishing emails and designed to deploy additional malware. Its latest version, v3, has been recently rebranded as Astolfo Loader.
Spectre RAT: OALABS has published IOCs for Spectre RAT, a commodity malware advertised on hacking forums.
Hexon Stealer: CyFirma looks at Hexon Stealer, a new infostealer that launched this August.
"Hexon Stealer is based on an electron framework, just like most other Discord stealers. [...] Hexon Stealer leverages Electron for its desktop application interface and is packaged using NSIS to distribute its malicious payload."
Sponsor Section
Stairwell's Mike Wiacek demonstrates Stairwell's file analysis and threat detection platform to Risky Business host Patrick Gray. Stairwell helps you monitor and analyze every executable file in your organization, automatically collecting crucial intelligence and providing your security team with in-depth visibility and detections.
APTs, cyber-espionage, and info-ops
Mysterious Elephant (APT-K-47): Knownsec 404 looks at a recent campaign linked to the Mysterious Elephant (APT-K-47) APT. The group is believed to operate out of India and the final payload in this campaign was Asynshell.
Storm-2077: Microsoft has published a report on a new Chinese APT group it tracks as Storm-2077. The company presented its findings at the CYBERWARCON security conference last week. The CYBERWARCON talks and report also include details about the most common tactics employed by North Korean APTs as part of their heavy shift towards social engineering campaigns and IT workers over the past few years.
"While their methods have changed throughout the years, the primary scheme used by Sapphire Sleet over the past year and a half is to masquerade as a venture capitalist, feigning interest in investing in the target user's company. The threat actor sets up an online meeting with a target user. On the day of the meeting, when the target user attempts to connect to the meeting, the user receives either a frozen screen or an error message stating that the user should contact the room administrator or support team for assistance."
ANO Dialog creates fact-checking org: ANO Dialog, a Russian company sanctioned by the US and EU for running Russian info-ops, has created a new fact-checking organization called the International Association for Fact-Checking. The organization is designed to be a clone of the International Fact-Checking Network (IFCN), an international network of fact-checkers that have been fighting Russian disinformation efforts since 2015. [Additional coverage in TASS]
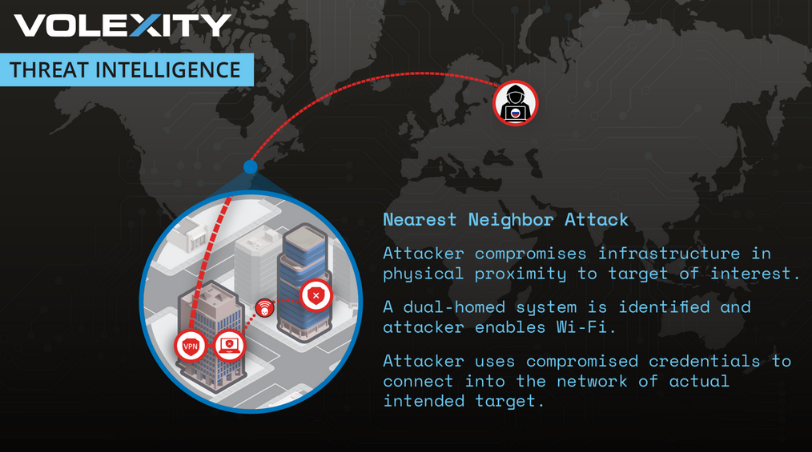
APT28 pulls off novel WiFi attack: A Russian cyber-espionage group has breached a US company by hacking another firm in a neighboring building and then connecting to the victim's internal WiFi network from across the road. The attack took place ahead of Russia's invasion of Ukraine and sought to collect data from the victim company's network related to individuals and projects involving Ukraine. Security firm Volexity called this technique the Nearest Neighbor Attack. It attributed the intrusion to GruesomeLarch, or APT28, a cyber unit inside Russia's military intelligence agency GRU.
Vulnerabilities, security research, and bug bounty
Fortinet VPN logging issue: A design flaw in the Fortinet VPN allows threat actors to hide brute-force attacks. The issue was discovered by researchers at Pentera, who found that Fortinet VPN servers only log failed login attempts during the authorization phase but not during authentication. Attackers can test as many credentials as they want during the initial authentication phase and only establish a working VPN connection with the valid ones. None of the failed logins would get logged.
New AMSI Bypass Technique: Practical Security Analytics have discovered a new AMSI bypass that leverages the Common Language Runtime library (CLR.DLL) and safely loads malicious binaries into memory undetected.
Vaultwarden auth bypass: The stuff you don't usually wanna hear is "authentication bypasses in your password manager." Well, there's one in Vaultwarden.
Sitecore RCE: Assetnote researchers have published details on an RCE in Sitecore that can be achieved via the CMS' automatic zip backups.
QNAP security updates: QNAP has released fixes for 31 security flaws.
Atlassian security updates: Atlassian's November patches are out with fixes for 20 vulnerabilities.
NVIDIA security updates: Two fixes are out for NVIDIA too.
Zyxel urges firewall updates after ransomware attacks: Taiwanese equipment vendor Zyxel has urged firewall owners to install security updates released on September 3 to protect against ransomware attacks. Vulnerabilities patched on that day are currently being used by the Helldown ransomware gang to gain an initial foothold on corporate networks. Zyxell has also recommended changing firewall admin passwords.
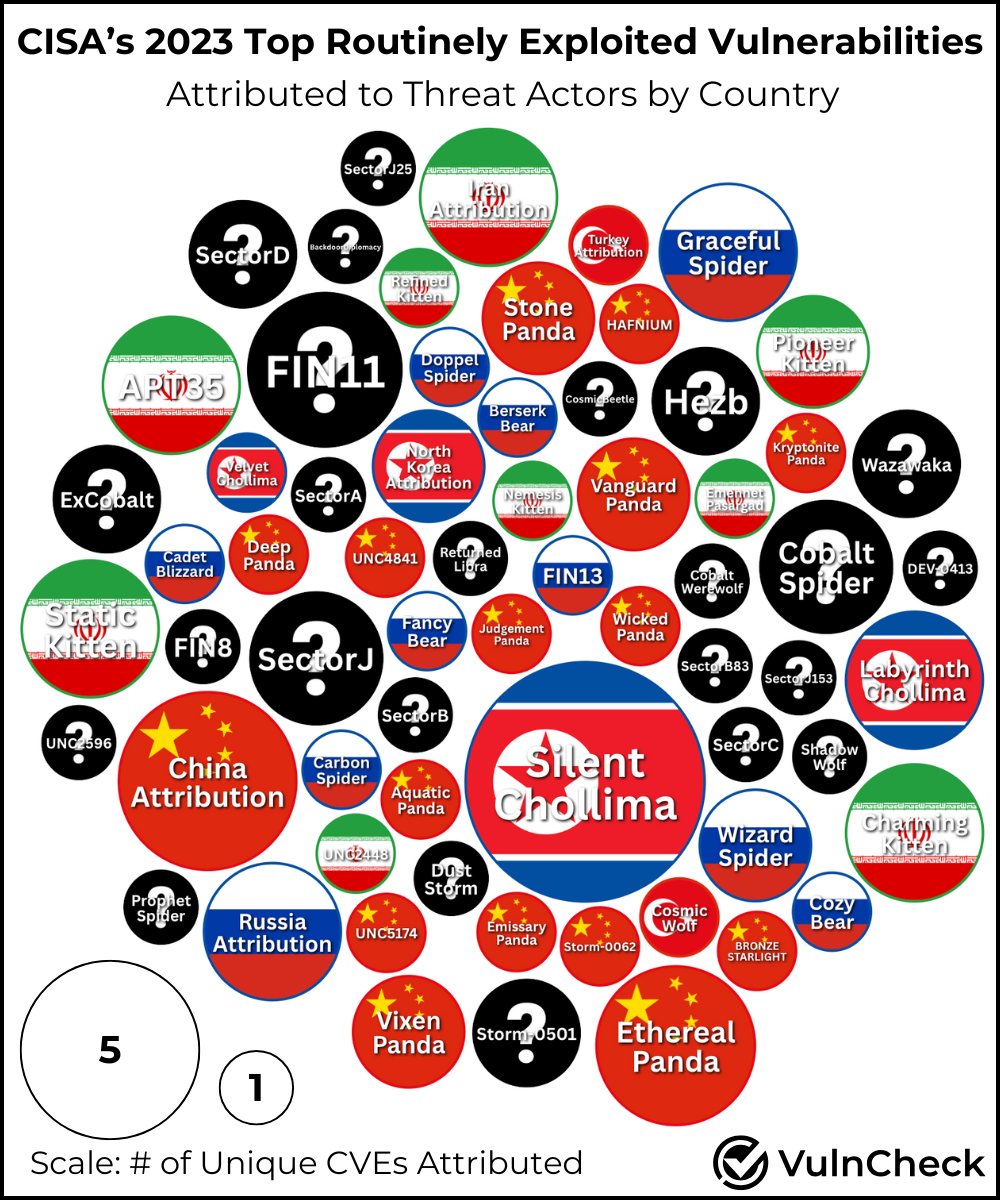
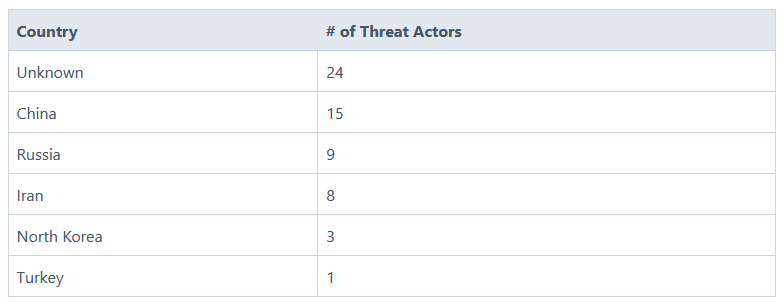
CISA's 2023 top exploited vulnerability: At least 60 known threat actors exploited vulnerabilities from CISA's list of most exploited bugs last year. According to security firm VulnCheck, North Korean group Silent Chollima was the most active, targeting 9 out of 15 CVEs from CISA's list. China and Russia had the most active groups, with 15 and 9, respectively. VulnCheck says that over 400,000 systems currently exposed online may be vulnerable to attacks using one of last year's most popular vulnerabilities.
Infosec industry
Threat/trend reports: Eclypsium [PDF], F5, Red Canary, ThreatMon, UHY, and Wordfence have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how ungoverned spaces on Telegram result in increasingly toxic and antisocial communities.
In this podcast, Tom Uren and Patrick Gray talk about what the People's Liberation Army cyber operators have been up to. They used to be China's most visible cyber operators but have since disappeared.




