Risky Biz News: Former South Korean government officials hacked in Kimsuky campaign
In other news: Atomic wallet hacks linked to North Korea; Barracuda tells hacked customers to replace gear; malware found in Minecraft mods.
This newsletter is brought to you by Stairwell. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. Apple Podcasts link here:
The South Korean National Police Agency says that a North Korean hacking group known as Kimsuky has breached the email accounts of former government officials.
The Kimsuky campaign took place between April and August of last year and targeted 150 current and former South Korean government officials, professors, and defense and national security experts.
Police officials say Kimsuky operators successfully lured nine individuals on phishing pages and stole their login credentials for Google and Naver accounts.
According to reports in local media, three of the nine victims were ministers and vice ministers in the previous Seoul government.
News of the successful intrusions came to light a week after the South Korean government imposed sanctions on members of the Kimsuky group.
It was also at the center of the first joint US-South Korean cybersecurity advisory. The advisory warned that Kimsuky was carrying out social engineering and spear-phishing campaigns of the exact nature of the one that South Korean police just disclosed.
The group has been one of the most active North Korean hacking gangs in recent months. Cybersecurity companies like AhnLab, S2W, SentinelOne [1, 2, 3], and Qihoo360 have published reports on the group and its recent campaigns over the past month alone, with many other reports documenting the group's extremely prolific activity over the past year.
This marks the second time South Korean officials publicly attribute a North Korean hacking campaign to the Kimsuky group over the past 30 days. They also linked Kimsuky to the hack of the Seoul National University Hospital in 2021, when they stole the personal information of 810,000 patients and 17,000 employees.
Breaches and hacks
Atomic wallet hacks linked to NK: Blockchain security firm Elliptic has linked the hack of more than $35 million worth of crypto-assets from Atomic Wallet users to North Korea's Lazarus hacking group. The company says that the stolen funds are being laundered through the exact same steps the Lazarus gang has laundered stolen funds in the past. The funds are also laundered through Sinbad, a cryptocurrency mixer that the gang has used for past hacks.
Clop MOVEit hacks update: In a message posted on its dark web leak site, the Clop it gang has provided instructions on how hacked companies can pay their ransom, meaning the extortion phase has officially begun. A report from Kroll's security team also claims the Clop gang has been sitting on the MOVEit zero-day as far back as 2021.
Barracuda tells customers to replace hacked gear: Barracuda Networks has instructed customers to replace ESG appliances if they have been hacked using a recently patched zero-day (CVE-2023-2868). The company did not elaborate why such a drastic action was needed. Barracuda email gateways have been exploited since October 2022 as part of a mysterious hacking campaign. The identity of the attacker and the purpose of the hacks are still unknown.
General tech and privacy
Google SAIF: Google has published the Secure AI Framework (SAIF), a conceptual framework to create secure AI systems.
Upcoming Apple privacy & security features: Apple's WWDC conference has come to an end, and while this year's edition didn't focus on user security like last year, we still got some interesting features nevertheless.
- A new feature called Check In, which automatically notifies family members when you've arrived at your intended travel destination.
- A new AirDrop feature called NameDrop, which allows a user to hold their iPhone near another to share their contact information with only their intended recipient.
- Support for Lockdown Mode is also coming on watchOS.
- Apps like Messages, AirDrop, and FaceTime will now show a "Sensitive Content Warning" when someone sends an unwanted nude image or video.
- You can now lock Safari Private Browsing windows under a FaceID scan to prevent unwanted snoopers from sticking their nose in there.
- Communication Safety, designed to warn children when receiving or sending photos in Messages that contain nudity, now also covers video content.
- Safari Private Browsing, Messages, and Mail will soon remove tracking parameters from URLs.
Government, politics, and policy
China goes after mesh WiFi and Bluetooth networks: The Chinese government is working on a law that would regulate the use of Bluetooth and WiFi proximity networks inside its territory. Drafted by China's cyberspace agency—the CAC—, the law would require the operators of a Bluetooth, WiFi, or any other kind of ad-hoc, mesh, or proximity network to "promote socialist core values," "adhere to the correct political direction," and "prevent and resist the dissemination of bad information." Network operators will have to collect the real identity of any users who connects to their network and share it with authorities at their request. In addition, network operators will have to show warnings to users to remind and discourage them from abusing their infrastructure for dissent. The new law comes months after anti-COVID protests took place across China, where protesters used Apple's AirDrop feature to share anti-government material.
France's Keeper of the Seals bill: The French Senate has passed an update to its "Keeper of the Seals" justice bill that will allow law enforcement agencies to secretly activate the cameras and microphones of remote devices without notifying the device owner. Officials say they plan to use this new provision to capture sound and images of suspects of certain types of crimes. The measure would be reserved for cases of delinquency, organized crime, and terrorism. The same update to the bill text would also allow law enforcement agencies easier access to geolocation data to track criminals suspected of committing offenses punishable by at least ten years in prison. [Additional coverage in FranceInfo]
Dutch Temporary Cyber Act: The Dutch government is working on a bill named the Temporary Cyber Act that will allow its intelligence and law enforcement agencies to automatically extend warrants they received against hacking groups to also cover their victims. The law would allow Dutch authorities to not only hack the hackers but also gain access to the devices of their victims. This is possible already, but the process requires approval from several government bodies.
New NCSC head: The White House has nominated Michael Casey to be director of the National Counterintelligence and Security Center (NCSC). Casey is currently the staff director for the Senate Intelligence Committee. [Additional coverage in The Record]
US critical infrastructure cyber policy: The Cyberspace Solarium Commission has published a report advising the US government to revise its policies on securing critical infrastructure. The commission says the government's current approach to public-private sector collaboration is "outdated and incapable of meeting today's demands" and will need a significant overhaul. [Additional coverage in CybersecurityDive]
Florida's Digital Bill of Rights: Florida Governor Ron DeSantis has signed into law a bill that would force Google and other search engines to disclose if they prioritize search results based on political ideology. The law also gives Floridians the right to opt out of having their data sold, to know if search results are manipulated, and prohibits state and local government employees from colluding with "Big Tech" companies to censor protected speech. We all know what this is really about. Someone needs visibility for their nutjob fascist propaganda. kek [Additional coverage in The Record]
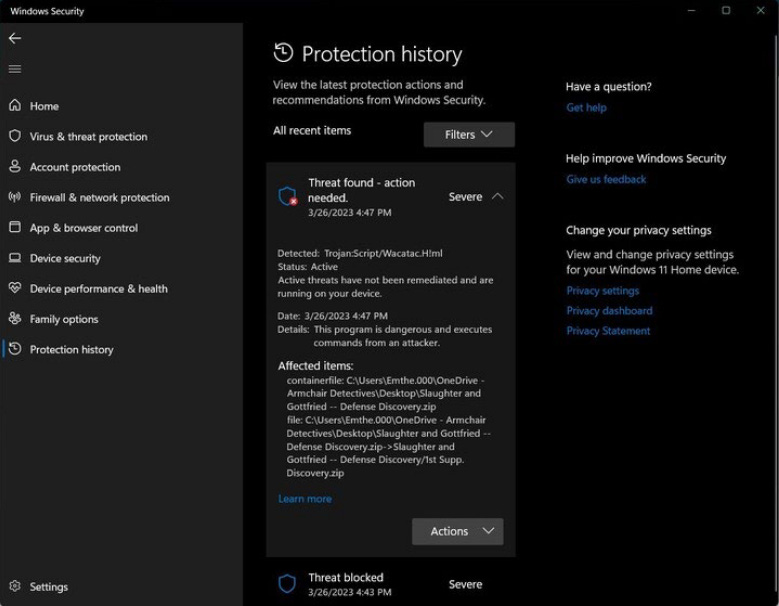
Some laughs: A lawyer representing two of the people who participated in the January 6 US Capitol riots claims the FBI tried to infect their computer with a trojan. The lawyer says they received an email from the FBI with a ZIP file that, when they unzipped it, triggered a Windows Defender alert. The lawyer seems to believe there's a whole conspiracy here to spy on them and their "fine" clients. The problem here is that the Defender warning was for Wacatac, one of the most widespread Windows viruses around, and definitely no gOvErNmEnT sUpEr MaLwArE! The lawyer now wants a whole investigation into the secret FBI spy plot to hack their PC. [Here's the PDF for some laughs]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Chris St. Myers, Threat Intelligence Lead at Stairwell, on how the company Inception platform can be used to find old or new threats that sometimes may go unnoticed.
Cybercrime and threat intel
Chilean Army corporal detained: Chilean authorities have detained an Army corporal in connection to a ransomware attack that hit the Army's internal network on May 26 this year. Officials say the suspect "participated" in the attack but did not elaborate further. Authorities have seized and are analyzing the suspect's electronic devices. They believe the suspect operated as an insider for the Rhysida ransomware gang.
Flint24 case goes to military tribunal: The trial of a sprawling carding group that operated tens of carding sites is headed to a military court in Russia, according to Kommersant. The group was detained in March 2020, including its leader, a Russian businessman named Alexey Stroganov, who went online as Flint24. According to Recorded Future's Gemini Advisory, Flint24 might have drawn the FSB's gaze to him after trying to get too close to President Vladimir Putin.
Conti, one year later: Almost a year after the Conti ransomware gang shuttered operations, its members have spread across the underground ecosystem and are core members of various other cybercrime cartels. RedSense Head of R&D Yelisey Bohuslavskiy has tracked past Conti members moving to ransomware groups like BlackBasta, BlackByte, BlackSuit, Royal, and Zeon. Conti members are also working as part of Karakurt and SilentRansomGroup, two gangs that extort companies using data stolen from networks the other gangs can't encrypt. [Additional coverage in DataBreachToday]
New Darkrace ransomware: A new ransomware group named Darkrace has started leaking victim data on the dark web this week.
Killnet: Radware has an update on recent developments in the Killnet crew, such as its silly Black Skills Private Military Hacker Company (PMHC), its Dark School hacker training operation, and the Killnet cryptocurrency exchange.
Malicious Chrome extensions: AdBlock Plus creator Wladimir Palant has identified a cluster of 109 malicious Chrome extensions. The extensions have been downloaded more than 62 million times. They contain code to track user browsing and inject JavaScript code to redirect them to new destinations.
BEC campaign targets fin sector: Microsoft has been tracking a BEC group targeting the banking and financial sector. The group uses compromised accounts at trusted vendors to send emails to their targets that redirect victims to AitM-based phishing sites. The attacks are capable of intercepting some weaker forms of 2FA.
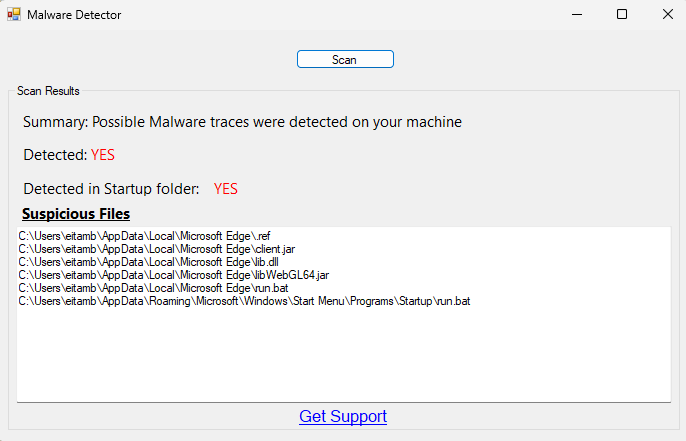
Malware found in Minecraft docs: A threat actor has hijacked developer accounts on the Bukkit and CurseForge platforms and injected malware in mods and plugins for the Minecraft video game. Named Fractureiser, the malware can steal cookies and passwords stored in web browsers and can hijack the clipboard to replace cryptocurrency addresses. It can also find and extract passwords for the OS account and the Discord and Minecraft clients. Researchers say Fractureiser has been live since mid-April and can work on both Windows and Linux. The list of affected mods has constantly grown over the past few days as the investigation has progressed and has now surpassed 50. The CurseForge team has released a tool to detect and remove the malware from the systems of affected users. [Additional coverage in ArsTechnica]
Malware technical reports
RecordBreaker: Antiy has a breakdown of RecordBreaker, the so-called v2 of the old RacoonStealer malware. Similar reports are available from CloudSEK and AhnLab.
Clop advisory: CISA and the FBI have published a joint advisory on the Clop ransomware gang and its TTPs and IOCs following their latest wave of attacks targeting MOVEit file-transfer servers.
Risky Business Demo
Stairwell's Mike Wiacek demonstrates Stairwell's file analysis and threat detection platform to Risky Business host Patrick Gray. Stairwell helps you monitor and analyze every executable file in your organization, automatically collecting crucial intelligence and providing your security team with in-depth visibility and detections.
APTs and cyber-espionage
ASD cyber operations: My colleague Tom Uren has published an analysis of past offensive cyber operations conducted by the Australian Signals Directorate (ASD).
"ASD studied IS's electronic communications, which included the use of a variety of encrypted messaging apps, including Surespot, Wickr, WhatsApp, and Telegram. It used an implant, "Light Bolt," that could be deployed to IS devices without user interaction and three different denial-of-service payloads that would disrupt internet access: "Rickrolling," "Care Bear," and "Dark Wall." These payloads all cut internet access, but with different degrees of permanence.
After deploying the "Rickrolling" payload, a device's internet access could be restored with a reboot. "Care Bear" could be overcome by someone with some technical nous, while "Dark Wall" was effectively permanent. Disappointingly, "Rickrolling" did not actually involve using Rick Astley's classic as an internet weapon."
Volt Typhoon: HuntressLabs' Joe Slowik published an analysis of the recent Volt Typhoon disclosure and activity.
SharpPanda APT: ThreatMon researchers have published a report on the SharpPanda APT.
Stealth Soldier: Check Point has identified a highly-targeted cyber espionage operation against Libyan and Egyptian targets. Researchers say the attackers behind this campaign are politically motivated. The operation involves a significant network of phishing domains and a new malware strain named Stealth Soldier. Check Point says the entity behind the attacks is the same threat actor who conducted the Eye on the Nile campaign in 2019.
SideCopy's FetaRAT: Chinese security researchers have a write-up on a SideCopy campaign spreading the new FetaRAT.
Core Werewolf: Russian cybersecurity company BI.ZONE has a report on Core Werewolf, a former cybercrime group that appeared in 2021 and has since turned to cyber espionage. BI.ZONE says that since 2021, the group has launched attacks on Russian organizations associated with the military-industrial complex and critical information infrastructure.
Asylum Ambuscade: Also on the same note, ESET has a similar report on another cybercrime group that recently turned to cyber espionage. This one is Asylum Ambuscade, a group that has been active since at least 2020. ESET says the gang previously targeted banks and cryptocurrency traders in North America and Europe but is now doing espionage against government entities in Europe and Central Asia.
APT activity on cybercrime forums: And sticking with the theme, threat intel firm KELA published a report on the activity of various APT groups on cybercrime forums. The report covers activity from Emennet Pasargad (data leaker), Bronze Starlight (ransomware op), and Pioneer Kitten (initial access broker).
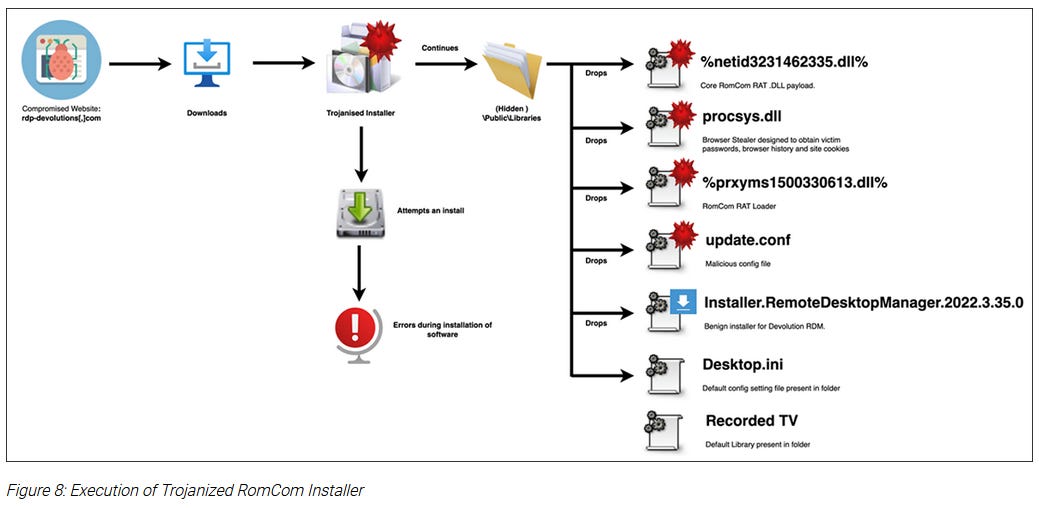
New RomCom campaign: BlackBerry says the threat actor behind the RomCom malware has returned with a new set of attacks that are targeting politicians in Ukraine who are working closely with Western countries. The campaign also targeted a US-based healthcare company providing humanitarian aid to the refugees fleeing from Ukraine and receiving medical assistance in the US. Previously, both BlackBerry and Trend Micro say they've seen the RomCom group pivot from financially motivated attacks to conducting cyber-espionage operations on behalf of the Kremlin regime. According to Trend Micro, this sudden pivot took place in October of last year.
Vulnerabilities and bug bounty
Google/Gmail BIMI vulnerability: Cyberscoop's AJ Vicens has an excellent write-up on a Gmail BIMI verification bypass vulnerability that scammers have been abusing in recent phishing campaigns. Google initially ignored the bug report but changed its mind after it got its cheeks spanked on social media.
MLflow vulnerabilities: The MLflow open-source machine learning platform has patched two LFI/RFI vulnerabilities.
Cloudogu SCM Manager vulnerability: A detailed write-up and PoC is available for CVE-2023-33829, a stored XSS affecting the Cloudogu SCM Manager, a unified platform for managing Git, Mercurial, and Subversion repositories.
Visual Studio bug: Varonis has published a write-up on a vulnerability (CVE-2023-28299) they found in Microsoft Visual Studio. The bug resides in the VS extension installer and allows an attacker to spoof an extension signature and effectively impersonate any publisher. The vulnerability was patched in April 2023.
VMWare security updates: VMWare has released a security update to fix three vulnerabilities, including a command injection issue that may lead to RCE scenarios. This one, tracked as CVE-2023-20887, has a 9.8 severity score.
Cisco security updates: Cisco has released seven security updates for various products. Two bugs are rated critical.
"Multiple vulnerabilities in Cisco Expressway Series and Cisco TelePresence Video Communication Server (VCS) could allow an authenticated attacker with Administrator-level read-only credentials to elevate their privileges to Administrator with read-write credentials on an affected system."
Honda e-commerce platform hack: Security researcher Eaton Zveare has gained access to Honda's e-commerce platform by exploiting a vulnerability in the platform's password reset API.
2023 vulnerabilities: Rezilion has a list of this year's most important security vulnerabilities. The list goes from PaperCut (CVE-2023-27350) to stuff like ChatGPT and Apache Superset.
Infosec industry
SSTIC 2023 videos: Talks from the SSTIC 2023 privacy & security conference, which took place this week, are now available on the conference's website. It's a French security conference, so expect French.
New tool—IRCP: A new tool named IRCP is available for large-scale reconnaissance on Internet Relay Chat servers.
IOActive's Cyber Park: Cybersecurity firm IOActive has opened a 5,000 sq ft (464 sq meters) cybersecurity laboratory in Cheltenham, near the GCHQ's new headquarters. The lab is believed to be the first privately-owned lab of its size anywhere in the world. [Additional coverage in the BBC]
Cyber insurance market: The cyber insurance market is showing signs to have stabilized after rates spiked last year as insurers were trying to cut their losses. According to a Moody's report, the need for cyber insurance remains high, but insurance rates are leveling off as insurers are starting to turn a profit again. Moody's has credited this to insurance companies tightening requirements for their clients to maintain coverage, and insurers are now avoiding incidents where they need to cover huge losses. [Additional coverage in CybersecurityDive]
Dragos layoffs: ICS cybersecurity giant Dragos is cutting 50 employees, representing around 9% of its workforce. Props for putting the announcement on their blog instead of acting like nothing happened. Also, big props for severance pay, the company covering healthcare for two additional months, and more.
Risky Business Podcasts
In this edition of "Between Two Nerds," Tom Uren and The Grugq look at how different cyber powers leverage companies through coercive power, regulation, and the attraction of values.




