Risky Biz News: First US spyware visa ban hammer falls on 13 individuals
In other news: Pegasus used against Polish female military officers; Russian hackers used a secret Windows zero-day for years; US charges, sanctions four IRGC hackers.

This newsletter is brought to you by Trail of Bits. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

The US government has imposed entry visa restrictions on 13 individuals involved in the development and sale of commercial spyware.
The visa ban applies to the 13 individuals and their immediate family members, such as spouses and children.
The State Department has not released their names. Sources have told RiskyBiz the names would not be made public due to US laws.
It is very likely that the 13 individuals are linked to Candiru, NSO Group, Intellexa, or Cytrox—four commercial spyware and surveillance vendors sanctioned by US authorities in 2021 and 2023, respectively.
This marks the first time the US State Department imposed visa restrictions related to spyware. It announced its intention to do so at the start of February this year.
The US has been trying to limit the proliferation of commercial spyware since last year. Seventeen countries have joined a US-led anti-spyware coalition at the White House's Summit for Democracy in 2023 and 2024.
The State Department's new focus on spyware proliferation was also reflected in its yearly Country Reports on Human Rights Practices, which included for the first time mentions of spyware abuses.
While the market of commercial spyware and surveillance has been around for decades, things have gotten out of hand over the last decade following an influx of new companies.
In many instances, these newer companies have provided their tools to oppressive regimes and the private sector, leading to an increase in the number of reports of repression and human rights abuses. Spyware and hacker-for-hire services have also led to instances where companies are hacking each other as part of litigation and other legal disputes, trying to get in front of their rivals and competitors.
In a report earlier this year, Google said it was tracking around 40 commercial spyware vendors "with varying levels of sophistication and public exposure, selling exploits and surveillance capabilities to government customers."
Previous US sanctions have proven to have had an effect on spyware vendors, with NSO Group being close to going under. However, industry experts have warned that these companies are likely to rebrand and hide under a new umbrella of front companies as a way to disguise and evade sanctions.
Imposing entry visa restrictions was seen as the next step taken by the US toward discouraging investors and developers from working with these companies.
Breaches, hacks, and security incidents
SIAFI hack: Brazilian authorities are investigating a breach of the country's Integrated Financial Administration System, also known as SIAFI. The system is used by the government of Brazil to pay out contracts and its employees. An investigation was started after local media reported that hackers phished SIAFI employees and then used their accounts to steal government funds. The hackers are believed to have stolen at least 3.5 million Brazilian reals ($680,000). Reports claim the hackers compromised anywhere between 3 and 17 SIAFI accounts. [Additional coverage in Globo/English coverage in the Brazilian Report]
SG MOE breach: Singapore's Ministry of Education (MOE) has disclosed a data breach. Hackers stole data from Mobile Guardian, a mobile app installed on school devices like Chromebooks and iPads. The ministry says hackers stole and leaked data from 127 primary and secondary schools.
Synlab ransomware incident: Medical diagnostics service Synlab says that a ransomware attack has crippled the operations of its Italian branch. The breach took place last week and the company has shut down all IT systems as a result. The company operates more than 380 medical labs across Italy. No ransomware group has taken credit for the incident so far. The company's French division was one of the victims of the Clop gang's MOVEit hacking spree last year.
ELTA fine: The Greek data protection agency has fined the country's postal service €3 million for a security breach that leaked customer data. The Vice Society ransomware gang breached ELTA in March 2022. The group leaked the company's data on the dark web after it failed to extract a ransom. Leaked data included customer and employee personal information. The Greek data protection agency investigated ELTA and found the company failed to protect data.
DPRK leaky server: A North Korean cloud server was left exposed on the internet last year and leaked animation-related projects. The exposed files suggest that Western animation studios might have inadvertently hired North Korean animators for their projects. According to the leaked files, North Korean animators appear to have worked on shows that have run or will run on the BBC, Amazon Prime, and HBO Max. Titles include the likes of Invincible, Dahliya In Bloom, Octonauts, and Iyanu, Child of Wonder. [Additional coverage in 38North]
Leicester ransomware attack: Street lights in Leicester have been stuck on all day, six weeks after the UK city fell victim to a ransomware attack. The attack impacted a central management system used to manage the street lights. Officials say the lights entered a default mode for technical faults where they're left on all the time. City officials hope to have the system restored by the end of next week. [Additional coverage in the Leicester Mercury]
Change Healthcare cyberattack: The UnitedHealth Group published an update on the cyberattack on Change Healthcare that crippled large parts of the US healthcare system earlier in the year. The company says it has not yet determined the exact number of patients that had data stolen but that the breach "could cover a substantial proportion of people in America."
General tech and privacy
Grindr sued in the UK: Hundreds of UK users have filed a class-action lawsuit against dating site Grindr for allegedly sharing highly sensitive information with advertising companies. Plaintiffs say the company shared personal information without their consent, including information about their HIV tests. Over 670 people have signed up to the claim so far. [Additional coverage in NBC News]
Russia sentences Meta exec to prison: Russia has sentenced Meta's communications director Andy Stone to six years in prison "promoting terrorism." Don't let yourself be fooled by the TASS report. This is actually a sentence against Meta itself for not giving into the Kremlin's requests to censor Facebook content about its invasion of Ukraine. Russia ended up blocking all of Meta's sites in the country on the grounds of "supporting terrorism."
Firefox bug: Mozilla has disabled a security feature that proactively blocked downloads from potentially untrustworthy URLs because of unexpected behavior.
Government, politics, and policy
HIPAA privacy update: The Biden administration has updated the Health Insurance Portability and Accountability Act (HIPAA) with a new privacy rule that safeguards the privacy and identity of patients seeking abortion care. The new rule bars healthcare and insurance organizations from disclosing patient data to state officials under any circumstances, even for law enforcement investigations. The new rules also cover the data of healthcare workers in abortion cases. The new rules will enter into effect in two months. They are a result of Republican states criminalizing and actively investigating abortion cases. [Additional coverage in The Record]
CyberTipline report: A Stanford Internet Observatory report warns that the US CyberTipline is in dire need of funding as the era of AI-generated CSAM is slowly flooding investigators with artificial content.
"Congress should increase NCMEC's budget to enable it to hire more competitively in the technical division, and to dedicate more resources to CyberTipline technical infrastructure development. This funding should not be taken out of the budget for Internet Crimes Against Children Task Forces."
Russia's VPN blocks: Roskomnadzor's Evgeny Zaitsev has confirmed that Russia is indeed blocking about 150 VPN services. [Additional coverage in TASS]
Dutch AIVD and MIVD yearly reports: The Dutch Military Intelligence and Security Service (MIVD) and the Dutch General Intelligence and Security Service (AIVD) have both published their yearly security reports. The MIVD says it was involved in operations that disrupted Russian cyber attacks against Ukraine but did not provide additional details—for obvious reasons. Despite the war in Ukraine, both the AIVD and the MIVD say that the biggest threat to the Netherlands still remains China's espionage and IP theft operations.
Pegasus in Poland's military: The Polish Military Police used the Pegasus spyware to spy on two female officers who reported sexual harassment by their superiors. Military Police officials deployed Pegasus 78 times against female employees over the past seven years. Polish prosecutors are currently investigating the previous government's use of the Pegasus spyware. So far, officials have notified 578 individuals that they have been targeted with the spyware. [Additional coverage in Onet]
Pegasus in Greece: Something we missed from last year—it appears that the Greek data protection agency revealed that in 2022 alone, at least 92 Greek citizens had been subjected to attempts to install Predator spyware on their devices. [Surfaced via the State Department's 2023 Country Reports on Human Rights Practices report.]
Spyware investigation in Spain: A Spanish court has reopened a probe in a suspected Pegasus infection of the country's prime minister in 2022. The judge reopened the case at the request of French officials. According to the Associated Press, French investigators claim to have new evidence to advance the investigation. The French government previously found traces of the Pegasus spyware on the devices of President Emmanuel Macron and several ministers in 2021.
GDPR compliance: The European Data Protection Board has published its strategy for 2024-2027, and the agency has promised more concerted efforts to enforce GDPR compliance.
EU police bosses complain about encryption: Police chiefs from European countries have called on governments and industry groups to stop tech companies from rolling end-to-end encryption (E2EE). Police officials say the E2EE roll blinds them to malicious activity on platforms such as social media sites. Thirty-two police chiefs have signed the joint declaration. The statement comes as Meta is rolling out E2EE features for its Messenger client.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Dan Guido, the CEO of security research company Trail of Bits. Dan and Tom discuss DARPA' upcoming AI cyber challenge, in which Trail of Bits will compete to solve very difficult bug discovery challenges. They also talk about Trail of Bits' approach to making some of its own tools available to the community.

Cybercrime and threat intel
US charges, sanctions Iranian hackers: The US government has charged four Iranian nationals for cyberattacks against US organizations. Officials say the four suspects worked for two front companies controlled by the cyber arm of the Iranian Islamic Revolutionary Guard Corps, the Cyber-Electronic Command (IRGC-CEC). The four are accused of hacking campaigns that targeted more than a dozen US companies and the US Departments of Treasury and State. The Treasury Department has sanctioned the four and the two front companies, and the US State Department is offering a $10 million reward for information on the group. US officials say one of the front companies—Mehrsam Andisheh Saz Nik (MASN)—has been associated with multiple Iranian APT groups, including Tortoiseshell.

Russian malware dev detained: Russian authorities have arrested a Moscow resident for developing and selling malware via Telegram. Officials describe the malware as having data-stealing and destructive capabilities. The FSB tracked down the suspect through a website they used to advertise the malware. [Additional coverage in TASS]
DDoSers detained in the Netherlands: Dutch police has detained two suspects for DDoS attacks against local companies.
Kivimäki profile: Bloomberg has published a profile on Aleksanteri Kivimäki, the hacker behind the ransomware attack and subsequent extortion campaign against Finnish health provider Vastaamo and its patients.
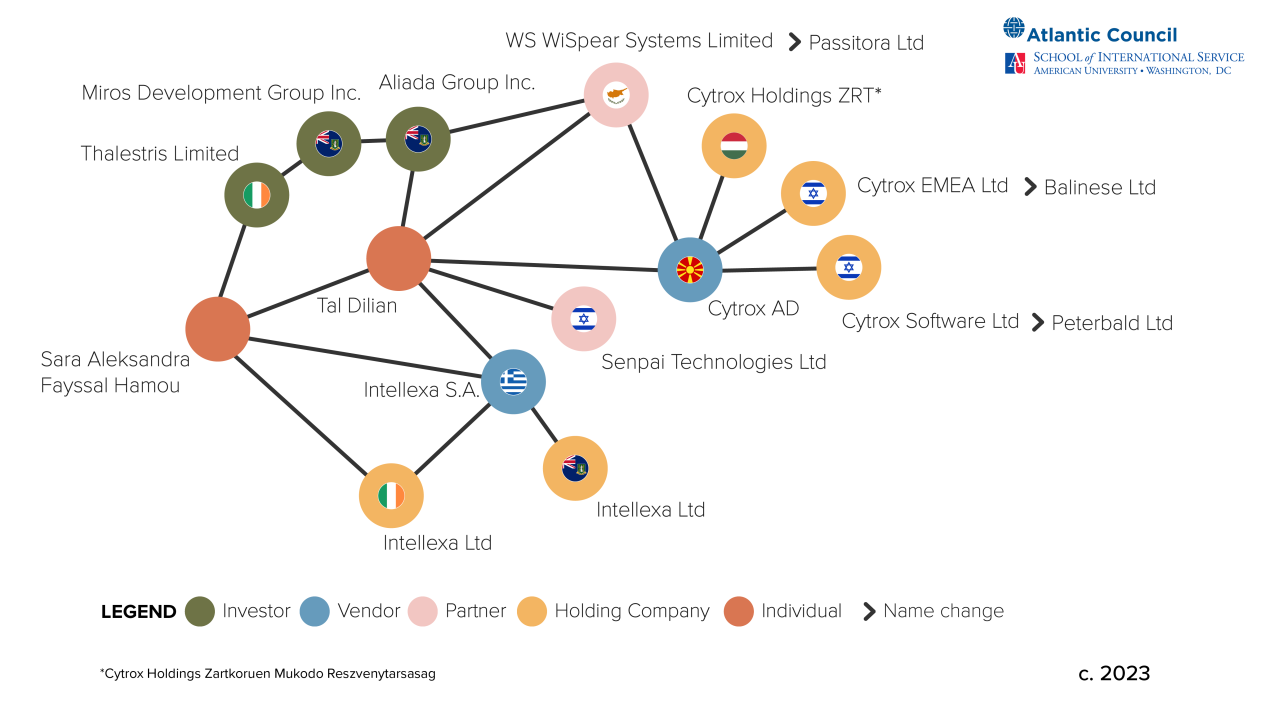
Spyware industry overview: DFRLab researchers have published an overview of the current spyware industry, using the Intellexa Alliance as an example.
CoralRaider group: Cisco Talos reports on an expansion in the activities of Vietnamese threat actor CoralRaider, which they first documented at the start of the month.
Scaly Wolf: Russian security firm BI.ZONE has published a report on Scaly Wolf, a financially motivated group active in Russia and Belarus. The group appears to have been active since June 2023. The group's favorite tool is the White Snake infostealer.
New APT73 RaaS: Threat intel analyst Rakesh Krishnan has published a blog post on APT73, a new ransomware gang that appears to have launched this month. The group also goes by the name of Eraleig.
New Embargo RaaS: Threat intel analyst Dominic Alvieri has spotted a new ransomware gang named Embargo.
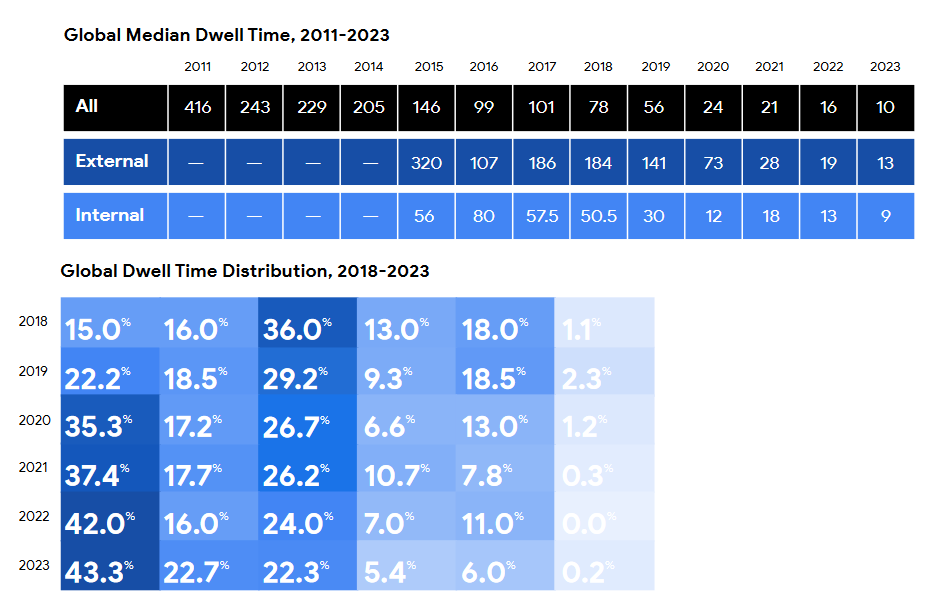
Threat/trend reports: CyFirma, Forescout, Mandiant, and Positive Technologies have recently published reports covering infosec industry threats and trends. The Mandiant M-Trends report is the one you'd probably wanna read since it covers trends observed by the company's IR team. The report highlights that the median dwell time for cybersecurity intrusions has fallen last year to an all-time low of 10 days. Mandiant says that 43% of all incidents last year were detected in one week or less. The company also observed a decrease in intrusions that remain undiscovered for long periods of time compared to previous years. Only 6% of 2023 intrusions went undetected for more than a year.
Malware technical reports
Sharp Stealer: G DATA has published an analysis of Sharp Stealer, a new infostealer advertised online.
HydraCrypt ransomware: SonicWall has published a technical deep dive into HydraCrypt, a new iteration of the older CryptBoss ransomware (2016). This version has been seen in Brazil in attacks targeting home users, with ransoms of up to $5,000.
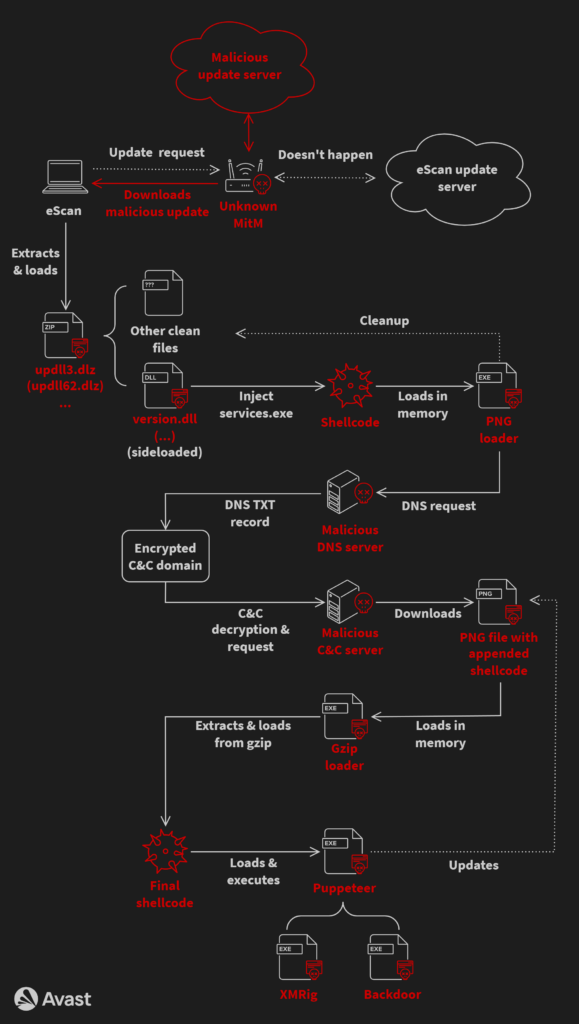
GuptiMiner: A threat actor has hijacked the update mechanism of the eScan antivirus to distribute backdoors and crypto-miners. Avast says the campaign has been active since 2018 and has primarily targeted large corporate networks. Named GuptiMiner, the threat actor has distributed two different backdoors. The first was used to move laterally across networks while the second was used to scan and steal private keys and crypto-wallet information. Avast says it found connections between GuptiMiner's malware and the Kimsuky North Korean APT.
Sponsor Section
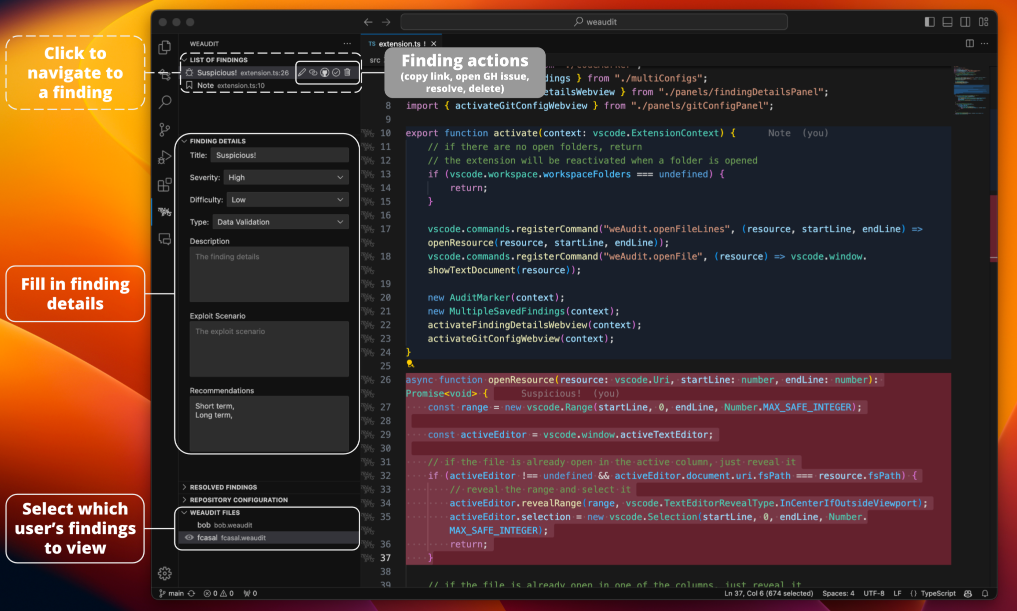
Trail of Bits has released weAudit, a VSCode extension the company's security engineers use for source code reviews during their security audits. The company also released SARIF Explorer, another VSCode extension for triaging static analysis results.
APTs, cyber-espionage, and info-ops
DPRK hacks: North Korean hacking groups have breached at least 10 South Korean defense companies over the past 18 months. South Korea's police force says the hacked companies were unaware of the breaches until they were notified by authorities. Officials linked intrusions to North Korean groups such as Andariel, Lazarus, and Kimsuky.
ToddyCat: Kaspersky has published a report on new ToddyCat attacks. ToddyCat is a new APT the company discovered last year attacking the APAC region.
Forest Blizzard's GooseEgg: Russian hacking group Forest Blizzard (APT28) has used a zero-day in the Windows Print Spooler service undetected for almost three years. The tool is named GooseEgg and has been used in attacks since April 2019. Russian hackers used GooseEgg to elevate privileges and steal credentials on already compromised networks. Microsoft patched the bug (CVE-2022-38028) at the base of the tool in October 2022 but only recently discovered the attacks.
"While a simple launcher application, GooseEgg is capable of spawning other applications specified at the command line with elevated permissions, allowing threat actors to support any follow-on objectives such as remote code execution, installing a backdoor, and moving laterally through compromised networks."
APT-Q-31: QiAnXin looks at APT-Q-31 (APT32, OceanLotus) and its latest Rust-based malware loader.
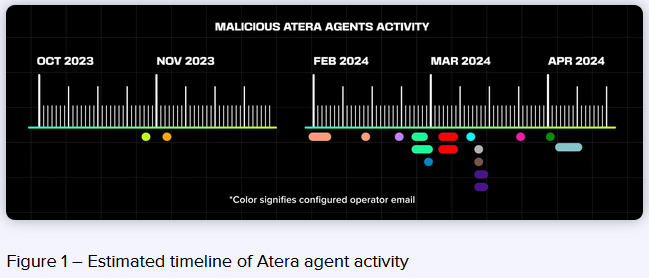
MuddyWater: HarfangLab researchers have published a report on Iranian APT group MuddyWater. The report covers the group's operations since the October 7 Hamas attack. Harfang notes the group has increasingly used legitimate versions of the Atera remote management tool to deploy its malware on compromised hosts.
Vulnerabilities, security research, and bug bounty
Apache dependency confusion: Researchers at Legit Security have discovered a dependency confusion attack impacting an archive Apache project—Cordova App Harness.
Flowmon security update: Rhino Labs has published a write-up on an unauthenticated command injection vulnerability in the Kemp Flowmon network monitoring suite. Progress Software patched the bug at the start of the month. The issue is tracked as CVE-2024-2389 and was a CVSSv3 10.0 bug.
CrushFTP zero-day: Rapid7 has confirmed that the recent CrushFTP zero-day is, indeed, fully unauthenticated.
Vulnerabilities in cloud keyboards: CitizenLab researchers have identified vulnerabilities in eight of nine Chinese cloud-based keyboard apps. The vulnerabilities allow threat actors to intercept keystrokes in real-time. Researchers estimate that up to one billion users have the apps installed and are vulnerable. Vendors with vulnerable keyboard apps include Baidu, Honor, iFlytek, OPPO, Samsung, Tencent, Vivo, and Xiaomi. Huawei keyboard apps were not vulnerable.
Infosec industry
New tool—Dauthi: Security researcher Matt Burch has published Dauthi, a tool designed to perform authentication attacks against various Mobile Device Management (MDM) solutions. Burch says Dauthi can be used to hack BlackBerry MDM solutions.
Tool update—MITRE ATT&CK: MITRE Corp has releaed v15 of the MITRE ATT&CK framework.
Acquisition news #1: Backup & recovery platform Veeam has acquired ransomware IR and negotiations company Coveware.
Acquisition news #2: IBM is planning to acquire secure cloud provisioning company HashiCorp.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at Google's review of zero-days in 2023. They discuss what this kind of information tells us and how Google's perspective influences the report.




