Risky Biz News: FIRST releases TLP v2.0
In other news: Hacktivists leak LatAm mining data; GitHub users attacked with phony repos; and academics find new eavesdropping method via fiber optics cables.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The Forum of Incident Response and Security Teams (FIRST) has released this week version 2.0 of the Traffic Light Protocol (TLP), an unofficial standard used by the vast majority of incident response teams and security professionals to share information about malware and cyberattacks.
The standard is a collection of "classification levels" that are applied to documents holding information about a cybersecurity incident. Since 2016, there have been four TLP levels: WHITE, GREEN, AMBER, and RED.
Cybersecurity professionals working on a case, would typically apply one of these TLP levels to a document, letting others know with whom a file might be shared. TLP:RED typically meant that information from that document should not be shared with anyone beyond the people who received the file or where present in a meeting. TLP:WHITE meant that information was not critical anymore and could even be published online, with the rest of the TLP levels being somewhere in between.
What's new in TLP v2.0
But with TLP v2.0, two major changes have been made to how these levels work.
For starters, the TLP:WHITE level has now been renamed TLP:CLEAR. While FIRST officials have not said why, this change most likely took place as part of a major trend in the tech industry over the past few years to remove gender and race-biased language.
Secondly, there is now a fifth TLP level—kinda. TLP:AMBER now has a sub-level named TLP:AMBER+STRICT.
In TLP v1.0, TLP:AMBER meant that a document could only be shared with the parties involved in a case. Depending on how organizations interpreted or decided to apply the TLP sharing standard, this sometimes meant an organization or an organization and its customers, who may need to know about a particular threat. This interpretation caused confusion ever since the TLP v1.0 standard was announced.
With TLP v2.0, the standard has been clarified to address these situations, with TLP:AMBER allowing the sharing of documents within an organization and its customers, while TLP:AMBER+STRICT, when applied, only allows the sharing of information within the organization only.

"These new changes are fairly minor, but that is for the best," Claire Tills, senior research engineer, Tenable, told Risky Biz News this week.
"Refining the labels to have a little more utility without overcomplicating the standard allows organizations to continue using the standard without significant disruption."
"The Traffic Light Protocol is a useful standard for an industry that relies on both information sharing and discretion. Balancing transparency with defenders against keeping sensitive information away from bad actors is difficult, and the TLP acts as both a clear guide and a tool of trust for organizations sharing information. However, the TLP only works if everyone abides by the standards.
@campuscodi @SwiftOnSecurity About time. TLP:AMBER is far too loose and TLP:RED is too restrictive. Without +STRICT, it was fairly useless for major service providers.
— Peter Bowen (@pzb) 6:36 PM ∙ Aug 4, 2022
Breaches and hacks
LatAm leaks: A hacktivist group calling itself Guacamaya posted 2 TB of hacked emails and files from multiple mining companies in Central and South America on Wednesday, in a move to apparently expose environmental damage in the region. According to Cyberscoop, the hacked materials come from ENAMI, an Ecuadorian state mining company; the Agencia Nacional de Hidrocarburos (ANH) in Colombia; New Granada Energy Corporation in Colombia; Quiborax, a mining company in Chile; Oryx, an oil company in Venezuela; Tejucana, a Brazilian mining company; and Guatemala's Ministerio De Ambiente y Recursos Naturales.
Slope incident: More details have emerged about the incident we reported in the last edition of the RBN newsletter—an attack that drained internet-connected wallets running on top of the Solana blockchain. According to new information, the incident only impacted owners of Slope wallets and took place after Slope developers logged the mnemonic keys of almost 8,000 users, which appear to have been discovered by a threat actor in Slope's Sentry server and then used to drain those wallets.
Indian UAN leak: Security researcher Bob Diachenko said he identified two Elasticsearch clusters this week that contained almost 289 million records. Based on his analysis, the researcher believes the two databases contained highly personal information on Indian citizens, although the data's origin remains unclear.
General tech and privacy
GitHub flooded with 35k malicious repos: A pretty unconventional malware attack was discovered this week on GitHub. Over the past three weeks, a threat actor created more than 35,000 GitHub repositories that were cloned from legitimate projects but modified with malicious code. If users were fooled into using the cloned projects instead of the legitimate ones, this code would collect their environment variables (data like API keys, tokens, Amazon AWS credentials, and crypto keys) and open a backdoor mechanism on their devices. The attack was stopped this week when GitHub's security team intervened to quarantine all the project clones that contained the malicious code. [Additional coverage in BleepingComputer]
@neurovagrant @campuscodi It's pretty simple, 1) fork or clone a repo, 2) add malware/sketchyness, 2.8) publish SEO the fake repos 3) profit?
— Ben April (@bapril) 1:27 AM ∙ Aug 4, 2022
GitHub is investigating the Tweet published Wed, Aug. 3, 2022:
— GitHub Security (@GitHubSecurity) 2:55 PM ∙ Aug 3, 2022
* No repositories were compromised
* Malicious code was posted to cloned repositories, not the repositories themselves
* The clones were quarantined and there was no evident compromise of GitHub or maintainer accounts
Microsoft blocks Tutanota accounts: Secure email provider Tutanota said on Thursday that Microsoft is now actively blocking its users from registering accounts on its platforms. The email provider said that after reaching out to Microsoft, the tech giant refused to change its policy.
Government, politics, and policy
Operation HaiEnergy: Cybersecurity firm Mandiant said it uncovered an information operation comprised of 72 news websites publishing pro-Chinese content.
The sites present themselves primarily as independent news outlets from different regions across the world and publish content in 11 languages. Based on technical indicators we detail in this blog, we believe these sites are linked to Shanghai Haixun Technology Co., Ltd (上海海讯社科技有限公司), a Chinese public relations (PR) firm (referred to hereafter as "Haixun").
Russian bot network: Ukraine's Security Service (SSU) said it dismantled a bot farm with more than one million bots that was used to spread fake news and disinformation about the war in Ukraine, in line with Russian propaganda.
FinFisher contract: A Netzpolitik investigation has uncovered that the German Federal Police paid more than €325,000 ($333,000) for access to the FinFisher spyware during 2013.
Cybercrime and threat intel
CISA's 2021 Top Malware Strains: CISA has published the list of top malware strains of 2021. The list includes Agent Tesla, AZORult, Formbook, Ursnif, LokiBot, MOUSEISLAND (part of the IcedID infection chain), NanoCore, Qakbot, Remcos, TrickBot, and GootLoader.
Dark Utilities: Cisco Talos researchers have uncovered Dark Utilities, a new cloud service for cybercriminals that offers hosted command-and-control (C&C) services for malware operations. In addition, the platform also allows customers to carry out DDoS attacks.
LNK builders are all in the rage again: As macro malware is dying out, LNK builders are all in the rage again, according to new research from SentinelOne.
Bumblebee campaign: Palo Alto Networks has a report out on recent campaigns carried out by the Project Libra (Exotic Lily) threat actor, a former initial access broker for the Conti ransomware gang. According to the company, the gang has been spending the past few weeks distributing malicious documents that infect victims with the Bumblebee malware loader.
PrivateLoader campaign: Similarly, the Walmart security team also has its own report on a recent spear-phishing campaign distributing the PrivateLoader malware, later used to deploy IcedID.
Mozlila threat actor: Security researchers from Trunc said they identified a new threat actor that has been using more than 1,000 IP addresses to scan websites for vulnerabilities. They said the threat actor can be identified in logs because they use a user-agent string where Mozilla is misspelled as Mozlila.
Pegasus spyware dashboard: We now know what the Pegasus spyware backend looks like, thanks to Israeli newspaper Haaretz.
SCOOP We got our hands on screen shots of an early prototype of Pegasus, called Syaphan and intended for use by the Israeli police
— Omer Benjakob (@omerbenj) 2:25 PM ∙ Aug 4, 2022
These photos are the closest we’ve gotten to seeing real working Pegasus system THREAD
@JoshBreiner @haaretzcom haaretz.com/israel-news/20…
Mr. Bitcoin extradited to the US: Alexander Vinnik, the administrator of the now-defunct BTC-e cryptocurrency exchange, has been extradited to the US to be trialed for his platform's role in various cybercrime money laundering operations, including the Mt. Gox hack and many ransomware payments.
Phishing panel seller arrested: Dutch police have arrested a 20-year-old from the city of Limburg on charges of selling phishing panels via Telegram. In the now-classic style of Dutch authorities [1, 2], once they detained the suspect, police officers also left a message on his Telegram channels warning customers to stop buying illegal software as the next time they might rent a phishing panel might be from an undercover police agent.
Malware technical reports
RapperBot: Fortinet published a report on Wednesday on RapperBot, a new IoT malware strain that gains access to devices via SSH brute-force attacks. The malware has been in the wild since mid-June when it was first discovered by CERTCN.
Bumblebee: While Palo Alto Networks has published details about recent campaigns distributing the Bumblebee malware loader, CloudSEK researchers have an analysis of the actual malware.
Gwisin ransomware: A new ransomware strain named Gwisin has been spotted in targeted attacks against South Korean companies.
APTs and cyber-espionage
Albania ransomware attack: Mandiant researchers have linked the ransomware attack that crippled the IT network of the Albanian government last month to an Iranian politically-motivated threat actor. Mandiant said the attack took place because members of (banned) Iranian opposition party Mujahedeen-e-Khalq (MeK) were granted residence and planned to hold a conference in Albania. Mandiant said the attackers used a ransomware strain named RoadSweep in the attack, along with a backdoor named ChimneySweep, and a new variant of ZeroClear, a wiper historically associated with Iranian state-sponsored operations.
Posing as Albanian nationalists, the Iranian actor leaked government docs and railed against the MeK. Check out the imagery. Notice the Angry Bird in the Star of David? When Iranian steel was targeted in a cyber op, a group called Predatory Sparrow used an Angry Bird logo. 3/x
— John Hultquist🌻 (@JohnHultquist) 2:42 PM ∙ Aug 4, 2022
Woody RAT: Malwarebytes said it discovered a new remote access trojan named Woody RAT being distributed in the wild and linked to an advanced persistent threat actor.
This advanced custom Rat is mainly the work of a threat actor that targets Russian entities by using lures in archive file format and more recently, Office documents leveraging the Follina vulnerability.
APT31: Russian security firm Positive Technologies has a report on recent attacks carried out by Chinese threat group APT31 against Russian organizations.
Meta cracks down on Bitter and APT36: Meta, Facebook's parent company, said it took action against two APT groups—Bitter and APT36—that had used its platforms to launch attacks against various targets across Southeast Asia. In addition, Meta said it also took down several influence operations in Russia, Israel, Malaysia, Pakistan, India, South Africa, Greece, and the Philippines.
Vulnerabilities and bug bounty
DrayTek Vigor router bugs: Router maker DrayTek released security updates to address a security flaw tracked as CVE-2022-32548 and impacting multiple router models. The vulnerability is a one-click unauthenticated remote code execution that can allow attackers to hijack vulnerable devices. Security firm Trellix said that during the discovery of this vulnerability if found more than 200,000 DrayTek routers connected online, but more are also most likely in private networks.
Chromium Site Isolation bypass: While the bug was patched back in May, we now have more details about CVE-2022-1637, a bypass of the Chromium Site Isolation feature. [Additional coverage in The Daily Swig]
XSS in Gmail's Amp4Email: Here's a write-up on a cross-site scripting vulnerability in Gmail's AMP component.
New QNAP vulnerability: Rapid7 has a write-up on yet another vulnerability in QNAP NAS devices. No CVE for this one yet, but Rapid7 said QNAP silently patched the reported issue.
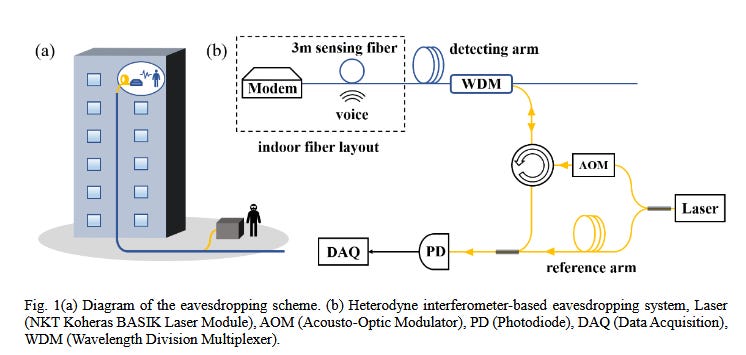
Eavesdropping via fiber optic cables: In a research paper published last month, a team of Chinese academics said they developed a method to monitor fiber optics cables coming out of a building and eavesdrop on conversations taking place inside. The crux of the research is that human speech or other noises create phase changes in the signal sent over fiber optics cables, which can be picked up using a laser interferometer by a threat actor and then converted back into sound waves. Researchers said this technique could recover conversations from inside a building at distances up to 1.1 kilometers down the fiber optics cable.
Infosec industry
Shodan stops accepting crypto-moneyz: IoT search engine Shodan, a tool often used by cybersecurity professionals, has announced its intention to stop accepting cryptocurrency payments from its users, citing online scams and "undue burden on [their] support team."
Flashpoint acquires Echosec: Threat intelligence outfit Flashpoint has acquired Echosec Systems, a provider of open-source intelligence (OSINT) services on topics like national security, public safety, and enterprise customers.
New tool #1: Google has open-sourced a new tool called Paranoid that can be used to check for well-known weaknesses in cryptographic artifacts such as public keys, digital signatures, and general pseudorandom numbers.
New tool #2: Italian security researcher Federico has open-sourced a new blue-team tool called PersistenceSniper, a Powershell script to hunt for common persistence methods across a network of Windows systems.
fwd:cloudsec videos: Talks from the fwd:cloudsec 2022 security conference, which took place last week, are now available on YouTube.




