Risky Biz News: FBI takes down Turla's Snake malware
In other news: Apple loses Corellium appeal; FBI takes down 13 DDoS booter sites; new CyberArk tool can recover ransomware victim files encrypted using intermittent encryption.
This newsletter is brought to you by Material Security, the company that provides visibility, defense-in-depth, and security infrastructure for Office 365 and Google Workspace. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The US Justice Department says the FBI crippled the Snake malware, a cyber-espionage toolkit operated by the Turla APT group for nearly two decades.
Officials say the FBI created and deployed a tool named PERSEUS that sent commands to computers infected with the Snake malware and overwrote some of its "vital components."
The malware's takedown was part of what officials called Operation MEDUSA.
According to court documents, the FBI and US intelligence agencies had been studying the malware and its inner workings for at least eight years, since 2015, ever since they found it on the networks of several US organizations.
Officials worked with the entities to watch how the Snake malware worked, its custom modules, how it established encrypted communications, and how it exfiltrated data from infected hosts.
This mammoth analysis work was also published this week as part of a 48-page technical report [PDF/PDF] authored by all the cybersecurity agencies part of the Five Eyes alliance (US, UK, Canada, Australia, New Zealand).
Officials also formally attributed Snake to Centre 16 of Russia's Federal Security Service (FSB)—marking the first time any foreign government has linked the highly advanced Turla APT to the Russian government.
At the technical level, officials called Snake the FSB's "most sophisticated cyber espionage tool."
Five Eyes agencies say the FSB typically used Snake to collect sensitive intelligence from high-priority targets, such as government networks, research facilities, and journalists.
Once deployed on an infected system, the malware would pull modules needed to perform an FSB operator's bidding, collect sensitive data, and exfiltrate the information via a custom, encrypted, and fragmented communication protocol.
All systems infected with Snake would not only be used for data collection, but they also acted as proxies as part of a larger Snake P2P botnet that helped mask and hide traffic from other Snake attacks.
It's this combination of custom encryption, proxies, and lack of visibility that gave officials headaches, but once the veil was lifted, investigations were not only able to find other Snake-infected systems, but they also managed to find the malware's main center of operations—which they linked to an FSB facility in Ryazan, a town located 200km south-east of Moscow.
Officials say they found the malware on systems in more than 50 countries, which they are now working to notify and provide guidance on how to remove the malware.
While the FBI crippled Snake, Five Eyes officials warn that Turla operators almost always deployed a keylogger on infected hosts, and they may return by using legitimate account credentials.
They also warned that while Snake's Windows version is well-known, the malware also has macOS and Linux versions as well.
Breaches and hacks
Iran MoFA hack: A hacktivist group named "Uprising till Overthrow" hacked the server infrastructure of Iran's Ministry of Foreign Affairs, defaced 210 sites, and shut down associated online services. The defacements called for the death of Iran's supreme leader and showed support for the Mujahideen-e Khalq (MEK) party, whose members are currently living in exile in Albania. In a Telegram post following the hack, the group leaked data stolen from MoFA servers, such as hundreds of identification documents, minutes of meetings, the ministry's correspondence, phone numbers of ministry officials, and the names of 11,000 employees. Iranian officials denied the hack, despite numerous screenshots of the defacements being shared on social media. MEK officials confirmed the hack via their official website. This is the group's second major intrusion after it hacked and shut down more than 5,000 Iranian government cameras and 140 government websites in June 2022.
SF MTA QR incident: A threat actor has distributed fake parking citations across San Francisco that contain malicious QR codes that redirect drivers to pay a $60 fine via a scammer-run platform. Authorities say the citations are easy to spot because they all have the same ticket ID number of 14010040.
Singapore QR incident: Singapore authorities are warning residents to be on the lookout for malicious QR codes posted across the city. The warning comes after a local 60-year-old woman scanned a QR code posted on a bubble tea shop and unwittingly downloaded a malicious app that later stole SGD$20,000 (USD$15,000) from her bank account.
Art Coin crypto-heist: The Art Coin crypto project misconfigured a part of its liquidity pools and allowed a user to buy crypto-tokens for 0.1ETH ($184), which they later resold for 181 ETH ($330,000). [Additional coverage in Bitcoinist]
RO Edu hack: A hacker defaced the portal of the Romanian Ministry of Education to tell students they can learn on YouTube in 10 months what they'd normally learn in school in 10 years. [Additional coverage in HotNews]
General tech and privacy
TikTok tracked LGBTQ content: TikTok maintained a backend dashboard that contained lists of users who watched certain types of videos, including users who viewed LGBTQ content. The dashboard was allegedly live for several years. TikTok shut down the dashboard last year after complaints from its own employees, who feared user lists and their interests might leak, the WSJ reports [non-paywall]. In addition, Forbes reporters have obtained a long list of words that TikTok's parent company Bytedance tracks and censors across the service. Forbes says these lists are managed by staff in China.
More ads coming to Windows 11: After adding ads to the Windows 11 Start menu, Microsoft is apparently experimenting with the idea of ads in the Settings panel as well. You know what they say. If it's free, then you're the product.
Number-matching in Microsoft Authenticator: The number-matching security feature is now available for Microsoft Authenticator push notifications. The feature works by showing a random number on login forms that Microsoft Authenticator users must enter in the app. Microsoft previously rolled out the number-matching feature in October 2022, but only for Azure AD accounts. With this week's update, the Microsoft Authenticator app can now be used for any online account that supports number matching and protect accounts against MFA fatigue (MFA prompt-bombing) attacks.
Truecaller prepares IM expansion: Caller-identification service Truecaller will make its service available to WhatsApp and other messaging apps to help users spot spam messages and calls over these services. The feature is currently in beta testing. Truecaller expects to roll it out globally later in May, the company's CEO told Reuters.
WebAuthn support in KeePassXC: The KeePassXC password manager is working on adding WebAuthn support.
Thunderbird donations: The Thunderbird project says it raised more than $6.4 million from more than 300,000 donors last year. That's more than double the $2.7 million it raised in 2021.
Firefox 113: Mozilla released version 113 of its Firefox browser. One of the most important changes is that Firefox's built-in password generator can now add special characters to your random passwords, which will allow Firefox to generate passwords that will pass most password complexity tests (which it did not previously).
PS VR2 hardware authentication cracked: A software developer has cracked the hardware authentication procedures for the PlayStation VR2 headset. While further work still needs to be done, in theory, this can allow the creation of drivers to allow VR2 headsets to be used on a PC instead of a PS console.
Apple Personal Safety User Guide: Apple has rolled out an update to its Personal Safety User Guide [PDF], a document the company has been publishing since 2020 on how Apple users can protect their devices from various threats. The May 2023 update adds instructions and tips on how to configure the Safety Check on iPhones, how to turn on Lockdown Mode, details on iMessage's new safety settings, how to share estimated time of arrival (ETA) via Apple Maps, how to wipe content from Apple Maps, and how to collect evidence of abuse, stalking, and harassment and how to request evidence related to an abuser's account.
Corellium-v-Apple lawsuit: The US Court of Appeals for the Eleventh Circuit ruled in favor of cybersecurity firm Corellium in its lawsuit against Apple. The court ruled that Corellium's CORSEC iPhone simulation tool is protected by copyright law under the fair use doctrine. Corellium's CORSEC tool allows security researchers to monitor and inspect the inner workings of iOS, something that Apple has always tried to prevent. The 11th Circuit Appeals Court upheld a lower court's decision. If Apple wants to take down CORSEC, they'd have to take the case to the US Supreme Court. [Additional coverage in Bloomberg Law / Court ruling PDF]
Google's false promise: Google promised last year to protect users who searched for abortion information and visited abortion clinics by deleting such information from its data cache. Except, it didn't—WaPo reports.
GitHub Push Protection: GitHub has announced the general availability of a new security feature named "Push Protection" that proactively prevents developers from including secrets in public or private repositories. Unlike the company's already existing "Secret Scanning" feature that just warns developers, Push Protection blocks a developer's push action with an error. Push Protection is free for all accounts, not just enterprise users.
Government, politics, and policy
EU Tech Lab: The European Parliament's Committee of Inquiry to investigate the use of Pegasus and equivalent surveillance spyware (or PEGA) has called on EU officials to create an EU Tech Lab. The new institution would be tasked with investigating and uncovering illicit use of spyware across EU governments. The lab would also provide legal and technological support to victims, such as device screening and forensic research.
Singapore's Online Criminal Harms Bill: Singapore's government is looking to pass a new bill (Online Criminal Harms Bill) that would grant it the power to block access to online websites "that are criminal in nature." According to the government, this would include websites that peddle scams, misinformation, cybercrime, drug trafficking, and CSAM content. The bill went through a first reading in parliament this week and is part of a suite of legislation meant to regulate Singapore's control over its online space.
Sponsor Section
Material Security co-founder Ryan Noon demos Material Security's email security solution to Risky Business podcast host Patrick Gray.
Cybercrime and threat intel
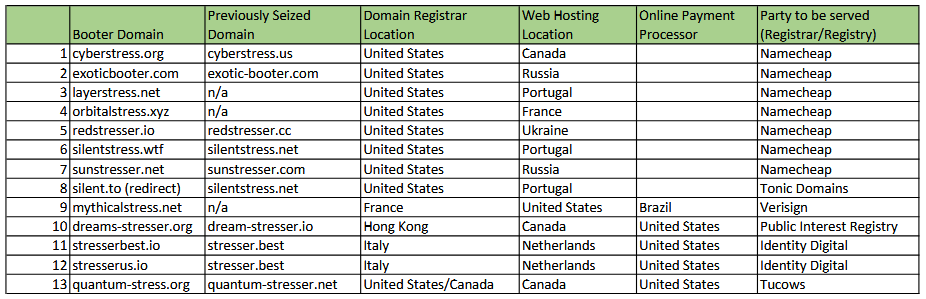
DDoS booter takedowns: US authorities have seized 13 domains that had been used to host DDoS-for-hire portals. Officials say ten of the 13 domains seized this week are reincarnations of DDoS portals previously taken down in December 2022. At the time, Europol and the FBI took down a batch of 48 domains used for DDoS attacks and detained six suspects. According to the US Justice Department, four of those six suspects pleaded guilty and are scheduled to be sentenced this summer. The latest seizures this week and the ones from last year are part of Operation PowerOFF, a long-standing law enforcement action to take down DDoS booter services.
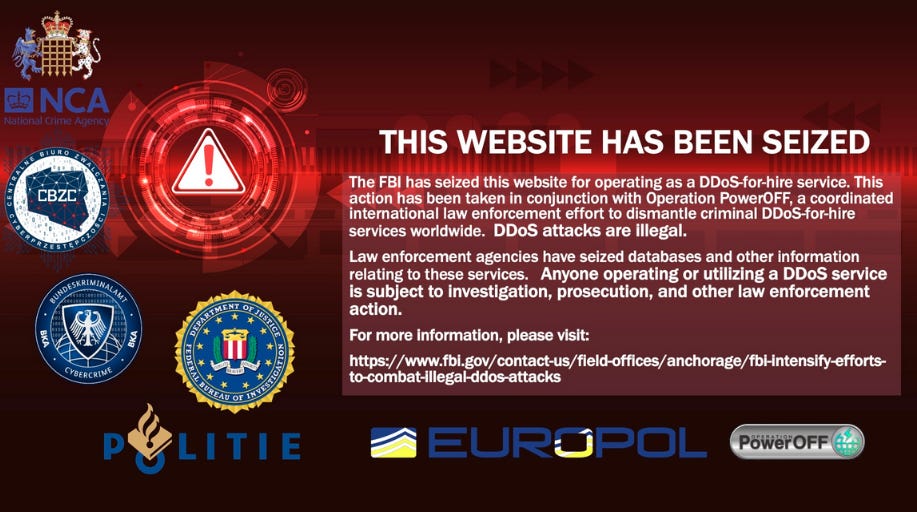
Big Pipes: Wired has a profile on Big Pipes, a group of roughly 30 cybersecurity professionals and IT experts who hunt down DDoS-for-hire services. The item above was also one of their operations.
SHMTL phishing campaign: McAfee says it's tracking a threat actor abusing server-parsed HTML (SHTML) files in phishing campaigns.
New type of typosquatting spotted on npm: Checkmarx has discovered a new type of typosquatting on the npm package repository. The new technique takes advantage of the fact that prior to 2017, the npm team used case-sensitive package names. That was changed in 2017 when all new npm packages used exclusively lowercase characters. The company says it's seeing threat actors record lowercase versions of older pre-2017 packages and hoping to hijack their userbases who don't spell the older names correctly.
Malware technical reports
StrelaStealer: OALABS published details on StrelaStealer, an email stealer that has been in operation since at least November 2022.
AgentTesla: Embee Research published an analysis of AgentTesla's multi-stage loader.
"The loader utilizes a Nullsoft package to drop an exe-based loader and multiple encrypted files. We'll follow the loader as it locates and decrypts the encrypted files, ultimately resulting in Shellcode which deploys AgentTesla malware."
AsyncRAT Loader: In a similar report, Huntress has a report on AsyncRAT's loader.
GULoader: McAfee published a technical breakdown of GULoader.
PowerDash: Poland's CERT team says it discovered a malspam campaign in late April that was distributing a new PowerShell-based malware strain named PowerDash.
AndoryuBot: A botnet named AndoryuBot has been spotted in the wild exploiting a vulnerability (CVE-2023-25717) in Ruckus routers. AndoryuBot first appeared in February 2023 and contains functions for executing DDoS attacks. It also communicates with its command-and-control server using SOCKS5 proxies.
Royal ransomware: PAN's Unit42 published a breakdown of Royal, a ransomware operation that launched in September 2022. Unit42 believes the ransomware is managed by a group of former Conti ransomware members known as Team One (previously also involved in Ryuk too).
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
APTs and cyber-espionage
SideWinder: An APT group known as SideWinder (Rattlesnake, Razor Tiger, APT-C-17) has been seen targeting Pakistan and Turkish organizations. The group has historically targeted Pakistani entities with a passion, but its targeting of Turkish organizations is new, BlackBerry researchers note.
Mustang Panda: Lab52 has a deep dive into the Mustang Panda group's malware they saw used in attacks against Australian targets.
ESET APT Q4 report: Cybersecurity firm ESET has a rundown of the APT operations that took place in Q4 2022. Loads of phishing and cyber-espionage, as usual. [thank you for subscribing to this newsletter for this high-level overview]
PwC 2022 APT report: Consulting giant PwC has published its yearly report on cyber-espionage and APT activities. It's all there, from the Log4Shell disaster to LAPSUS$, ransomware gangs, and the war in Ukraine. The report also details the company's APT naming convention.

Vulnerabilities and bug bounty
CVE-2023-0386 PoC (Linux): A proof-of-concept exploit has been published for CVE-2023-0386, an LPE vulnerability in the Linux kernel's OverlayFS subsystem.
CVE-2023-32233 (Linux): The Linux kernel team has patched a vulnerability (CVE-2023-32233) in the Netfilter utility that can grant attackers root access.
"The issue is about Netfilter nf_tables accepting some invalid updates to its configuration."
Patch Tuesday: Yesterday was also the May 2023 Patch Tuesday. We had security updates being released by Adobe, AMD, Intel, Microsoft, Mozilla Firefox, Citrix, and SAP. The Android project, Chrome, Fortinet, and Zyxel released security updates last week as well. This month, Microsoft patched 49 vulnerabilities, including two zero-days (CVE-2023-29336 and CVE-2023-24932). The company published an advisory on the last one, which was actively exploited in the wild by the BlackLotus bootkit.
Infosec industry
BSides London videos: Talks from the BSides London security conference are available on YouTube, here, and here. They're marked 2023, but they're most likely from the 2022 edition, which took place last December.
New tool—White Phoenix: CyberArk researchers have open-sourced a tool named White Phoenix that can be used in some limited cases to recover files that have been encrypted using intermittent encryption. Intermittent encryption is a technique where ransomware strain encrypts just a small portion instead of an entire file, but enough to prevent a user from opening it. White Phoenix supports recovering PDFs, Office documents, and ZIP files. CyberArk says other formats, such as video and audio files, may also be recoverable. The tool was tested with ransomware strains such as BlackCat/ALPHV, Play, Qilin/Agenda, BianLian, and DarkBit.
New tool—MCDA: The Malcore Desktop Agent is now generally available and also free of charge.
New tool—TritonDSE: Quarkslab has open-sourced TritonDSE (doc, source), a Python library built on top of the Triton dynamic binary analysis toolkit that can provide easy and customizable Dynamic Symbolic Execution capabilities for binary programs.
New tool—AskJOE: Security Joes has open-sourced a tool named AskJOE that uses OpenAI to help researchers use Ghidra for malware analysis.