Risky Biz News: FBI seizes Dispossessor ransomware servers
In other news: US charges Angler exploit kit member; hacker leaks upcoming Netflix shows; UK explores nation-wide cyber-deception network.

This newsletter is brought to you by Corelight. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

US officials have seized server infrastructure linked to a data extortion group known as Dispossessor and RADAR.
Officials from the DOJ and FBI have seized nine domains and 24 servers linked to the gang's operations.
A criminal complaint was also filed against an individual going by the hacker pseudonym of "Brain," which officials believe is based out of Europe—possibly Poland.
The Dispossessor group is a rather unique operation that is the result of the recent turmoil in the ransomware ecosystem over the past two years.
The group formed around August 2023 and is a team-up between two "affiliate groups/individuals" who used to work for larger ransomware gangs.
These "affiliates" worked by hacking into corporate or government networks, stealing files, and then deploying a file-encryptor (aka ransomware) on the victim's network.
This ransomware strain was usually rented from a Ransomware-as-a-Service (RaaS) platform, with the affiliate getting a percentage of what a victim paid to the RaaS platform for the decryption key or to avoid having their stole files published online.
According to reports from DataBreaches.net, SentinelOne, SOCRadar, and vxdb, the Dispossessor group appears to have formed when two former affiliates named RADAR and Dispossessor decided to team up.
This team-up operated at first as an initial access broker on underground forums such as BreachForums, although according to reports they didn't seem to be that good at it, often asking for help on intrusions and being ridiculed for it.
The group evolved and launched its own data leak site in February 2024.
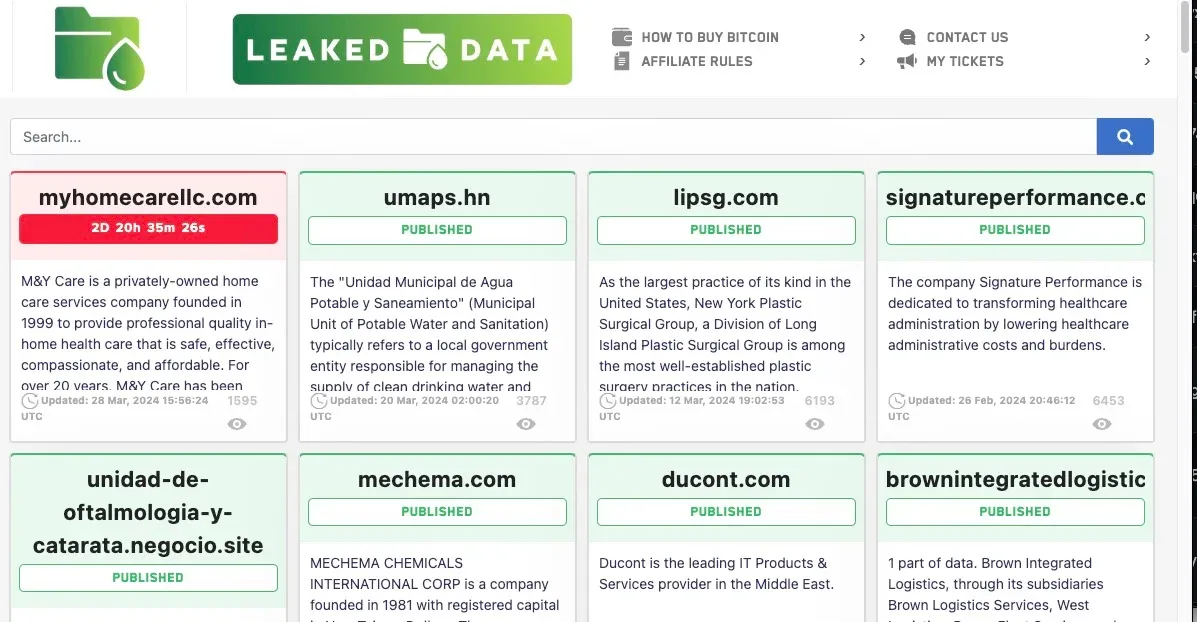
At first, they listed old victims from their past attacks. Based on entries on the site, it appears that RADAR and Dispossessor worked for groups such as LockBit, Clop, Hunters International, 8Base, and Snatch.
Newer entries eventually began being added to the site throughout the year, such as the Delhi Hospital in Louisiana and Aire Dental in New York.
Based on public reporting, the group was still engaging in data extortion attacks only. This appears to have changed somewhere in May-June, when the Dispossessor gang announced they were launching a full-blown RaaS of their own, with the ability to create custom ransomware builds for their attacks.
Both the leak site and the RaaS appear to have been built on the leaked source code of the LockBit ransomware gang—with the data leak site being basically a green-themed redesign of the old LockBit leak site.
This was no surprise, as per reports, the Dispossessor seems to have been one of the biggest LockBit affiliates, having tallied up more than 330 victims while working for the LockBit group in previous years.
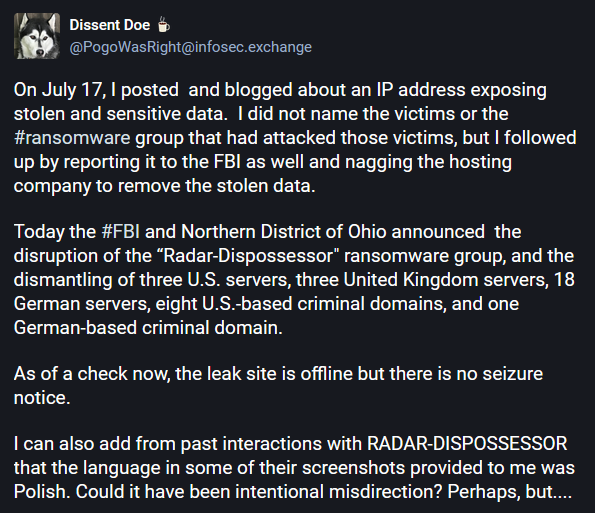
As the linked Mastodon post from above seems to suggest, the gang appears to have misconfigured their infrastructure, leaking some of their real-world IP addresses.
The group genuinely appears to have limited technical skills, asking many times on hacking forums for IT-related help, which is not the ideal scenario when you're trying to hide from the feds after you've extorted companies for millions of US dollars.
An OPSEC mistake was very likely what led to the group's downfall, and an arrest won't surprise us at all—if, indeed, mister big-"Brain" RaaS operator is based out of Europe.

Breaches, hacks, and security incidents
Crown Equipment hack: Forklift maker Crown disclosed a security breach last week after a threat actor gained access to one of its IT environments. The breach took place at the start of June, and Crown says the attacker was able to gain access to some employee benefits and retirement data. Crown says it since contained the intrusion. The company's name has not been listed on any ransomware leak site.
Evolution Mining ransomware attack: Australian gold mining company Evolution Mining says it was the victim of a ransomware attack last week. The company says it handled the incident with no material impact on its operations. The incident comes two months after the BianLian ransomware group hit Northern Minerals, another Australian mining company. Evolution Mining is one of Australia's six biggest mining corporations. [Full press release/PDF]
Scam group nets $60 million: Chemical manufacturing company Orion SA has lost a whopping $60 million in a wire fraud incident last week. The company says a threat actor managed to trick one of its employees into sending wire transfers to the wrong accounts. In an SEC filing, Orion says there was no breach of its IT network, suggesting this was a classic wire fraud scheme instead of the more prevalent BEC scam.
Crypto-heist recoveries: Binance said in a press release last week that it froze and recovered more than $73 million worth of assets this year from cryptocurrency crime. Around 80% of the funds are linked to past hacks and exploits, while the rest are linked to cryptocurrency scams.
Twitter's fake DDoS attack: Several sources inside Twitter claim that Twitter owner Elon Musk was lying on Monday when he claimed that a live space stream with former US President Donald Trump crashed because of a DDoS attack. [Additional coverage in The Verge]
Hacker leaks Netflix shows: A hacker leaked last week several upcoming episodes from major Netflix and Crunchyroll shows. Netflix confirmed and blamed the leaks on one of its post-production companies. Sources claim the source of the leak is Iyuno, a California company specializing in subtitling and content distribution services. Iyuno disclosed a security breach last Friday but did not take the blame for the Netflix show leaks. According to Beebom, the leaks included episodes from the upcoming season two of Emmy award-winning series Arcane.
POLADA leak: Hackers have stolen and leaked more than 50,000 sensitive files from Poland's anti-doping agency POLADA. The incident occurred last week and exposed personal details and medical records of thousands of Polish athletes. The agency claims the hack was carried out by "the services of an enemy state." A Polish minister told local media the government is currently looking at Russia or Belarus as the potential source of the leak. [Additional coverage in Notes from Poland and ZaufanaTrzeciaStrona]
C-Edge hack: Juniper Networks has published a report on how a threat actor exploited a Jenkins vulnerability to breach Indian software provider C-Edge Technologies and deployed ransomware in an incident that impacted a large part of the Indian banking sector this month.
mSpy data takedown: Ukrainian company Brainstack has filed a legal takedown against FlokiNet, the web hosting provider of DDoSecrets. The company has asked the web host to remove data belonging to a spyware company named mSpy. The spyware maker was hacked and had its data leaked in July after a hacker stole its Zendesk support forum database. According to TechCrunch security reporter Zack Whittaker, this marks the first time that Brainstack has confirmed ownership of the mSpy brand.
General tech and privacy
Geofencing warrant ruling: A federal appeals court has ruled that geofence warrants are unconstitutional, a decision that will limit the use of the controversial search warrants across the US. [Additional coverage in TechCrunch]
Noyb sues DPA: European privacy organization noyb has sued the Swedish data protection agency for failing to act on user privacy and GDPR complaints.
Microsoft deprecates Paint 3D: Microsoft has EOLed Paint 3D. The app only lasted 8 years and will be removed from the Microsoft Store on November 4, 2024. Existing installations of Paint 3D will continue to work, but the app will no longer be available for download from the Microsoft Store.
Google AdSense leaves Russia: Google is currently notifying Russian users that it will deactivate all AdSense accounts by the end of the month. Russian users will not be able to monetize websites and YouTube videos through AdSense ads. After Russia's invasion of Ukraine, Google disabled the ability for Russians to monetize Russian traffic, but they could still receive payments for traffic coming from abroad. The company plans to make final payments to Russian users between August 21 and 26 and then leave the Russian market altogether. Some Russian bloggers and YouTubers say the AdSense ban can be avoided by changing an account's country of origin and using a foreign card number to receive payments. The move comes after the Russian government blocked access to YouTube earlier this month and after a new round of US sanctions. [Additional coverage in The Moscow Times]
Government, politics, and policy
US presidential campaign hacks: The FBI said Monday that it is investigating attempts to hack both the Trump and Biden-Harris campaigns. The FBI says the investigation includes attempts to hack three Biden-Harris campaign staffers and former Trump advisor Roger Stone. The agency has confirmed the investigation after the Trump campaign said it was hacked by Iran earlier this year. Alleged Iranian hackers leaked documents from the Trump campaign to Politico at the end of July. The same files were also shared with the New York Times and Washington Post, which chose not to cover the files and the breach for days until Politico broke the news. The way the two outlets handled the hack is a 180-turn to how they treated the Clinton campaign's hacked emails in 2016 when they went with a fine tooth comb over the leaked data for months.
NIST PQE standards are out: The US National Institute of Standards and Technology (NIST) announced three new encryption algorithms designed to protect against attacks with quantum computers. NIST has been working on the standards for the past eight years. The three were selected from 82 algorithms submitted from 25 countries. The three selected standards are ML-KEM (short for Module-Lattice-Based Key-Encapsulation Mechanism, or FIPS 203), ML-DSA (short for Module-Lattice-Based Digital Signature Algorithm, or FIPS 204), and SLH-DSA (short for Stateless Hash-Based Digital Signature Algorithm, or FIPS 205). A fourth algorithm named FN-DSA (short for Fast-Fourier Transform over NTRU-Lattice-Based Digital Signature Algorithm, or FIPS 206) is still under development.
CISA's Wales retires: CISA's executive director Brandon Wales is retiring from the DHS this week. The Record has an exit interview with Wales, who spent almost 20 years working at the agency.
UK working on nation-wide cyber-deception network: The UK government is exploring the idea of deploying a nation-wide cyber-deception network. The network would involve the deployment of honeytokens inside private networks and honeypots with organizations that have mature security teams. The UK's cybersecurity agency is looking for a minimum of two million honeytokens and over 200,000 honeypots deployed across UK organizations.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Brian Dye, CEO of Corelight, about a string of recent CISA advisories. These advisories address specific technical issues, but when examined together, Brian says there is an underlying message about addressing security holistically.

Cybercrime and threat intel
Angler EK and Ransom Cartel admin charged: The US government has charged a Belarussian and Ukrainian dual-national for his role in two long-running cybercrime operations. Officials say Maksim Silnikau was a core member of the Angler exploit kit malvertising operation for nine years between 2013 and 2022. He also founded and ran the Ransom Cartel ransomware service in May 2021. UK officials say that while part of the Angler gang, Silnikau was also involved back in 2011 in the deployment of Reveton, the first-ever widely distributed ransomware strain. The UK NCA says that at its peak, Angler accounted for 40% of all exploit kit infections and was making its operators around $34 million per year. The 38-year-old Silnikau was arrested in a resort town in southern Spain in July of last year and extradited to the US last week to face charges for his crimes. The US has also charged two other individuals for their role in the Angler malvertising operation—Vladimir Kadariya, 38, from Belarus, and Andrei Tarasov, 33, from Russia.
CryptoCore group: A cybercrime group named CryptoCore has stolen over $5.4 million worth of crypto assets using a highly sophisticated social media scam campaign. The group used hacked accounts with large followings, a flood of online comments, and deep-fake videos to redirect users to scam sites impersonating famous brands. Victims were asked to invest in crypto-tokens supposedly managed by the large brands but had their funds stolen from their accounts. Security firm Avast described the group as very professional, having deep fake videos prepared for multiple topics in advance, ready to be weaponized at the most opportune time. Recent CryptoCore campaigns exploited Donald Trump presidential nomination, several SpaceX flights, and even Apple's yearly developer conference.
Ego and Reiko interviews: Threat intelligence analyst Jacob Larsen has published interviews with Ego and Reiko, two individuals involved in the hacks of the DEA Data Portal and Doxbin.
New Vanir Group: A new ransomware and data extortion operation named Vanir Group launched last month. The group's data leak site looks like an Akira clone and currently lists only three victims.
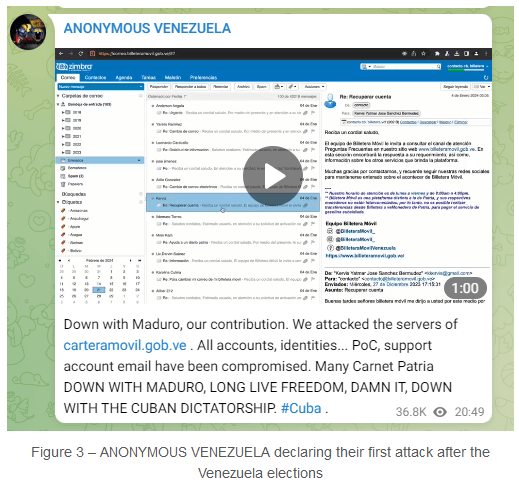
Venezuela hacktivism: Check Point takes a look at the hacktivism activity surrounding the mass protests in Venezuela that got underway after the country's disputed election.
Malware technical reports
Unknown functions: Trellix malware researcher Max Kersten has published research on "a tried and tested method for dealing with thousands of unknown functions" in suspicious/malware files.
Sponsor Section
James Pope, Corelight's Director of Technical Marketing Engineering, demonstrates the company's Open NDR Platform and how it combines network detections with a whole host of other data sources.
APTs, cyber-espionage, and info-ops
UAC-0198: Ukraine says that hackers compromised the systems of central and local governments following a massive spam campaign that posed as the country's security service. The campaign took place on Monday, August 12, and compromised at least 100 computers. CERT-UA says systems were infected with a backdoor named ANONVNC, which the agency linked to a group it tracks as UAC-0198.
APT42: CyFirma has published a report on the activities of Iranian cyber-espionage group APT42.
Info-ops overview: Recorded Future has published an overview of recent efforts to influence the upcoming US presidential election, some of which simply pivoted from meddling in the recent EU elections. This is an update to an older December 2023 RF report.
Kurks disinformation: Ukraine's security service has accused Russia of launching a disinformation campaign about its Kurks offensive, using fake news and fake leaks to claim that Ukraine is committing war crimes.
"According to the SBU, in the near future the Russian special services may resort to staging crimes, in particular against the civilian population of the Kursk region, in order to later accuse the Ukrainian side of committing them."
Vulnerabilities, security research, and bug bounty
Takeover of Enphase solar panels: A team of Dutch security researchers has discovered a series of major vulnerabilities in Enphase smart solar panel systems. Researchers at the Dutch Institute for Vulnerability Disclosure (DIVD) claim they could have hijacked over four million internet-exposed Enphase solar panels across 150 countries. The vulnerabilities include weak passwords and pre-auth RCE exploit chains. The DIVD says Enphase has released fixes for five of the six vulnerabilities and has made exploitation of the sixth impossible using any of the other CVEs. [Additional coverage in Follow The Money]
Docker registry exposure: Security researcher Christopher Bleckmann-Dreher warns that hundreds of organizations are exposing their Docker container registries over the internet, allowing threat actors to easily modify images and other settings.
Azure Health Bot Service vulnerabilities: Tenable researchers have discovered multiple vulnerabilities in the Azure Health Bot Service that could have been exploited to access cross-tenant customer resources. The Azure Health Bot Service allows healthcare organizations to deploy virtual machines to run healthcare-specialized AI-powered virtual assistants and chatbots.
Cozy+ vulnerabilities: German security firm SySS has identified several vulnerabilities that could allow threat actors remote access to Ewon Cosy+, a remote access gateway used by companies to access PLCs and other industrial systems.
Outlook bug: Morphisec researchers have published a technical write-up on CVE-2024-30103, an Outlook bug they discovered earlier this year that allows remote execution through malicious-injected Outlook Forms. Microsoft patched the bug back in June together with another Outlook RCE discovered by the same researchers.
GitHub Actions leak: Palo Alto Networks has published research on a new method of hacking GitHub repositories through GitHub Actions. At this point, I've honestly lost track of all the GitHub Actions bugs and leaks, and this is slowly turning into the cloud version of Internet Explorer.
Patch Tuesday: Yesterday was the August 2024 Patch Tuesday. We had security updates from Adobe, Microsoft, Ivanti, Fortinet, Intel, AMD, SAP, Kubernetes, Splunk, Schneider Electric, Siemens, and Zoom. The Android Project, Chrome, Cisco, Solarwinds, Rockwell, Elastic, JetBrains, 1Password, and Jenkins released security updates last week as well. This month, Microsoft patched 186 vulnerabilities, including six zero-days. Adobe also had a massive patch day with 72 fixes. The Microsoft zero-days are below.
- CVE-2024-38178 - Scripting Engine Memory Corruption Vulnerability (via AhnLab and South Korea's NCSC)
- CVE-2024-38193 - Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability (via Gen Digital)
- CVE-2024-38213 - Windows Mark of the Web Security Feature Bypass Vulnerability (via Trend Micro)
- CVE-2024-38106 - Windows Kernel Elevation of Privilege Vulnerability
- CVE-2024-38107 - Windows Power Dependency Coordinator Elevation of Privilege Vulnerability
- CVE-2024-38189 - Microsoft Project Remote Code Execution Vulnerability
Infosec industry
DEF CON room searches: A scandal broke out before the DEF CON security conference this year after the Resort World Las Vegas hotel announced it would search all guest rooms while the conference was taking place at its premises. Initially, it was unclear what staff would be looking for. But, according to 404 Media, hotel staff appear to be searching for Flipper Zeroes, WiFi Pineapples, and soldering kits.
New tool—TraceeShark: AquaSec has released TraceeShark, a WireShark extension to analyze Linux runtimes.
New tool—Pythia: Security researcher Efstratios Lontzetidis has released Pythia, a generic and standardized query format that can search across multiple infrastructure-hunting platforms at the same time.
New tool—DriverJack: Security researcher Klez has released DriverJack, a tool designed to load a vulnerable driver by abusing lesser-known NTFS techniques.
allInfoSecNews shuts down: Infosec-themed portal allInfoSecNews has shut down and open-sourced its code. A new portal named AllSecurityNews was set up on that code to replace it.
Acquisition news: Experian has acquired behavioral analytics company NeuroID.
Threat/trend reports: Cato Networks [PDF], Check Point, CyFirma, Intel471, Kaspersky, and Sophos have recently published reports covering infosec industry threats and trends.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss what it would mean to be in a golden age of OSINT and whether we are in one.
In this podcast, Tom Uren and Patrick Gray discuss the US's National Counterintelligence Strategy, and that it highlights the risk that foreign intelligence entities will use personal information to target and blackmail individuals.
The Risky Business team has recently started publishing video versions of our podcasts. Below is the main weekly show, with Pat and Adam at the wheel!




