Risky Biz News: FBI links Harmony's $100 million hack to the Lazarus Group
In other news: Apple patches iOS zero-day; Mango Markets hacker detained and charged; Security Keys for Apple ID goes live.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The FBI has formally attributed the hack of the Harmony cryptocurrency bridge platform to Lazarus, a cyber-espionage group working for the North Korean government.
The Harmony crypto-heist took place on June 23, 2022, and resulted in the theft of $100 million in cryptocurrency assets.
Less than a week after the incident, blockchain tracking company Elliptic linked the hack to Lazarus operators by tracking how the funds moved to wallets previously associated with the group.
The funds remained untouched until earlier this month when the Lazarus gang used the RAILGUN privacy protocol to move and launder $63.5 million of the stolen Harmony assets. Some of the laundered funds were frozen in Binance and Huobi accounts, but the bulk still remain under Lazarus' control.
This week's announcement marks the second time that the FBI has formally linked a cryptocurrency heist to the Lazarus Group in such a public fashion.
The FBI previously linked the theft of $620 million worth of cryptocurrency assets from the Ronin Bridge to the same Lazarus group back in April 2022.
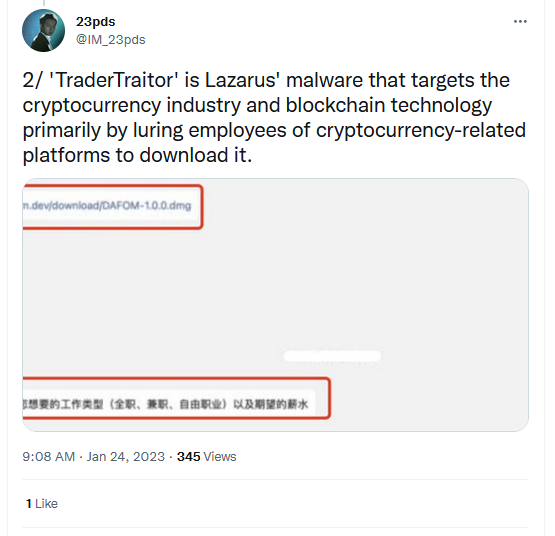
The FBI says that in both intrusions, the Lazarus gang used a form of malware known as TraderTraitor to compromise employee systems. US officials and security experts say the malware is typically delivered via emails or private messages sent to a company's employees disguised as high-paying job offers.
The malware is written in cross-platform JavaScript code that runs inside an Electron app, which can deploy different second-stage payloads for both Windows and macOS, depending on the compromised employee's platform. Besides cryptocurrency platforms, Lazarus has used the same malware to go after gaming and financial sector companies.
Breaches and hacks
Riot Games extorted: Riot Games says it received a ransom demand via email from the threat actor who hacked one of its employees and then gained access to one of its game development environments. Riot says the hacker is asking the company to pay a ransom demand, or they will release the source code for the League of Legends and Teamfight Tactics games and the source code of a legacy anti-cheat platform. The company says it does not intend to pay the ransom and expects the leaked source code to "increase the likelihood of new cheats emerging."
GoTo breach update: GoTo, the company that owns LastPass, updated a data breach notification it published last year when it said that some of its cloud hosting services were also impacted as part of the LastPass intrusion. GoTo says a recent investigation has found that the intruders managed to steal encrypted backups from its cloud storage. The backups contained data, including user information, for GoTo products such as Central, Pro, join.me, Hamachi, and RemotelyAnywhere. The company said the backups were encrypted, but the threat actor also stole an encryption key that would allow them to decrypt "a portion of the encrypted backups."
FanDuel breach: Sports-betting platform FanDuel emailed customers last week to let them know that their names and email addresses were stolen from the company's Mailchimp account. FanDuel joins e-commerce service WooCommerce as the second major company known to be affected by MailChimp's breach. Mailchimp, an email and newsletter platform, disclosed a security breach two weeks ago when it said that a threat actor hacked one of its employees and stole data from 133 Mailchimp customers.
Hacked Wormhole funds move: The threat actor behind that hack of the Wormhole cryptocurrency platform has moved $155 million worth of assets they stole from the company, according to blockchain analysis platform CertiK. The funds represent almost half of the $321 million that Wormhole reported stolen in February of last year. Once it saw the stolen funds move, Wormhole reiterated its intention to pay a $10 million reward if the funds were returned to its wallets, the CoinTelegraph reported.
Election campaign BEC incident: The office of Republican Kansas Senator Jerry Moran says it lost $690,000 last November after a cybercriminal tricked its accounting firm into transferring the funds to the wrong account. In a letter to the US Federal Election Commission, Moran's campaign said one of its banks managed to recover more than $168,000 from the stolen funds, but the vast majority remains under the criminal's control. The incident is what security researchers call a "business email compromise," or BEC fraud, a type of crime that has topped the FBI cybercrime statistics for the past five years, responsible for tens of billions of US dollars in losses. [Original story, non-paywalled version, FEC letter/PDF]
General tech and privacy
FB Messenger E2EE: Meta says that it plans to onboard more users on the end-to-end encrypted (E2EE) version of its Facebook Messenger app over the next few months. The company says users will be chosen at random, and users will be notified when their private conversations will be upgraded to the E2EE version. In addition, the company has also expanded the features of its E2EE version, which now also supports some of the features of the original Messenger app, such as link previews, chat themes, user active status, and support for the Android floating bubble mode.
"Over the next few months, more people will continue to see some of their chats gradually being upgraded with an extra layer of protection provided by end-to-end encryption. We will notify people in these individual chat threads as they are upgraded. We know people will have questions about how we select and upgrade individual threads, so we wanted to make clear that this is a random process."
Twitter GodMode: GodMode, a feature that lets Twitter employees access and tweet from any account, is still active at Twitter, months after Peter Zaitko's original whistleblower complaint, a new whistleblower complaint filed with the FTC alleges. This second whistleblower told the Washington Post the feature was renamed to "Privileged Mode" following the original complaint and that the feature is primarily used to tweet on behalf of advertisers unable to do it themselves, but that Twitter is still unable to log how it is used or if it is being abused by its staff. [Non-paywall version here]
Android 14 to block very old apps: Android 14, the upcoming version of the Android OS, will block the side-loading and installation of Android apps written for very old versions of the Android OS, according to lines of code spotted in the project's source code. The code did not reveal what would be the most recent version of the Android OS to be set as a cutoff check for the side-loading process. The discovery comes after Google also updated the Play Store guidelines earlier this week and is now requiring that all new apps submitted to the Play Store be written to work on Android 12 or later. Both moves are expected to have a huge impact on the security of of Android 14 users, as it would block apps containing deprecated code and vulnerabilities from running on their devices.
Microsoft to block Excel add-ins from the internet: Microsoft plans to block the execution of Excel add-in (XLL) files inside Excel and other Office apps if the XLL files were downloaded from the internet, according to a product roadmap. Microsoft says it took this decision in order to "combat the increasing number of malware attacks in recent months" that have abused Excel add-ins to bypass email filters and execute malware on user devices.
Security Keys for Apple ID: While Apple has allowed users to use various forms of two-factor authentication (2FA) methods to secure their Apple ID accounts, the company has been one of the few big tech giants that did not support hardware security keys. This has changed this week with the release of iOS 16.3 and macOS Ventura 13.2, the first two iOS and macOS versions to allow users to use a FIDO-certified hardware security key to log into their Apple accounts. Apple announced support for hardware security keys last month as part of a major upgrade to its security features. [More on Apple Security Keys for Apple ID can be found here].
Government, politics, and policy
International Counter Ransomware Task Force: The operations of the International Counter Ransomware Task Force formally began activity this week. The project is led by Australia and is part of the US-led Counter Ransomware Initiative, a coalition of 37 governments working to stem the impact of ransomware gangs.
Indian govt throws a fit: The Indian government has abused national security laws to order Twitter, YouTube, and the Internet Archive to remove copies of a BBC documentary that looked into the role played by Prime Minister Modi in an anti-Muslim massacre in Gujarat in 2002. [More in CNN]
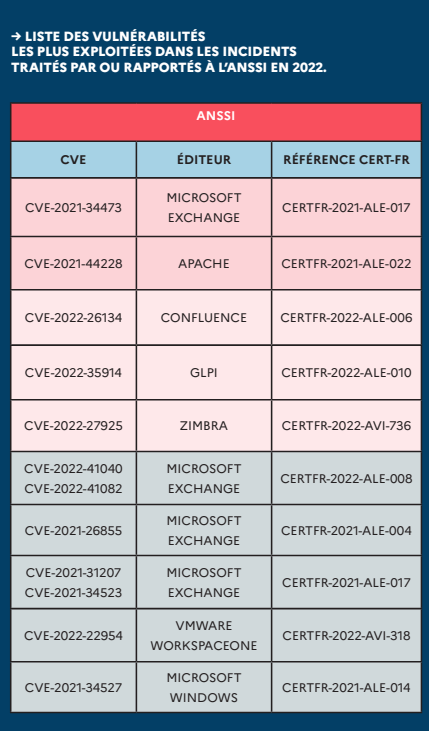
ANSSI yearly report: France's cybersecurity agency ANSSI has published its yearly activity and threat report for the year 2022. The report is only available in French for now, but English versions are also published in the following days. APTs continued APTing, basically. The list of top exploited vulnerabilities, as seen by the agency, is below.
Sponsor section
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. The company has recently released a new type of canary token that's basically a real and valid payment card number. Companies can store the token in one of their systems, and Thinkst will alert them when the card (token) is used somewhere in the real world; alerts that companies can use to investigate possible breaches of their financial data storage systems.
Cybercrime and threat intel
Instagram hacker detained: Japanese police have detained a 28-year-old man on charges of hacking into the Instagram accounts of more than 60 victims. Most of the victims were women, and the hacks took place between August 2020 to October 2021. The suspect allegedly derived victims' birthdays based on social media posts and used combinations of their names and date of birth details to guess their passwords. The man admitted to the charges and told police that he wanted to "harass people who are living a fulfilling life" and women who graduated from high-level universities and had jobs at big companies.
Mango Markets hacker charged: The US Securities and Exchange Commission has revealed formal charges against cryptocurrency expert Avraham Eisenberg. Officials say Eisenberg engaged in a trading scheme that stole approximately $116 million from crypto asset trading platform Mango Markets in early October 2022. Eisenberg's actions were discovered by the cryptocurrency community shortly after the attack. Eisenberg did not deny his actions but tried to explain them as a "highly profitable trading strategy." Eisenberg was arrested in Puerto Rico at the end of 2022 and is awaiting transfer to the US. [Official complaint/PDF]
Bitzlato arrest and takedown: Europol says it has taken down the website and servers of Bitzlato, a cryptocurrency exchange that was used to launder criminal profits. The Bitzlato founder, a Russian national, was charged and arrested by US authorities last week. Europol says it also detained four other of the company's executives, three in Spain and one in Cyprus. These included the company's CEO, Financial, and Marketing directors. Europol and US authorities say Bitzlato played a crucial role in criminal money laundering schemes, helping criminal groups convert cryptocurrency into Russian rubles. Europol says that almost half of Bitzlato transactions were linked to criminal activity, such as ransomware attacks and drug trafficking. As part of the takedown, Europol said it seized cryptocurrency wallets holding €18 million worth of crypto assets and also worked to freeze more than 100 accounts at other cryptocurrency exchanges linked to Bitzlato, holding around €50 million.
ShareFinder abuse: The team at DFIR Report has a good summary of how threat actors have adopted and are now abusing Invoke-ShareFinder, a script part of the PowerView module of the PowerSploit framework. The script allows users to find all network shares inside a large network, which can be very useful for threat actors trying to find a victim's data and steal it or encrypt it.
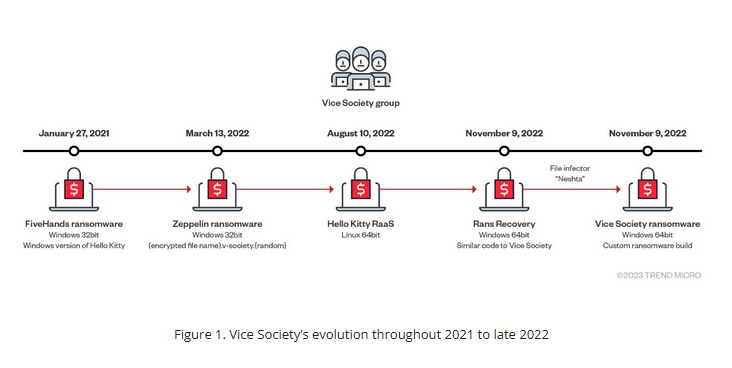
Vice Society: Trend Micro has a profile on the Vice Society ransomware and data extortion gang.
Realtek SDK attacks: Palo Alto Networks says it is seeing a spike in attacks trying to exploit a remote code execution vulnerability in the Realtek Jungle SDK (CVE-2021-35394). The security firm says that 40% of the attacks it tracked between August and October 2022 involved this vulnerability. The vulnerability affects more than 190 IoT device models from 66 different vendors. Multiple threat actors exploited the vulnerability to hack routers and IoT devices and deploy malware such as Mirai, Gafgyt, Mozi, and RedGoBot.
QR code phishing: Fortinet says it spotted a phishing campaign targeting Chinese-speaking users that used QR codes to send users to phishing sites and steal credentials for various online services.
Top phished brands: Check Point has put out its quarterly phishing report. We found this interesting because the top most-used brand in phishing emails in Q4 2022 was Yahoo. Yeah. Shocking! We were expecting Apple, Amazon, or PayPal, not an ancient and almost dead email service.
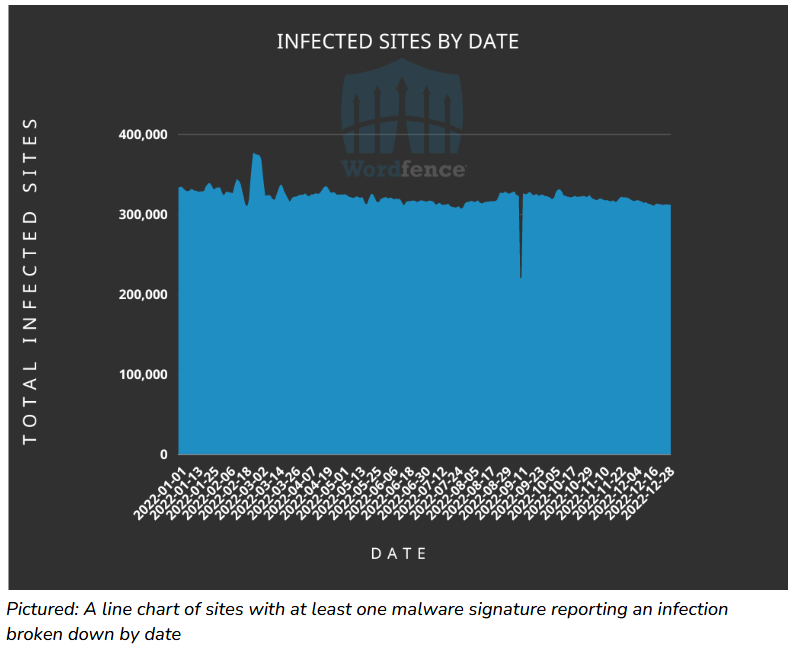
Cred-stuffing on WP sites goes down: Both good and bad news are included in the year-in-review report of Wordfence, a company that provides security services for WordPress sites. The company says that while credential stuffing attacks have remained the top threat for WordPress site operators in 2022, the number of attacks "saw a significant reduction" compared to the previous year. Unfortunately, threat actors appear to have redirected their attention to scanning WordPress sites for configuration files or other threat actors' web shells and then using those to hijack sites instead. As for websites infected with malware, Wordfence says the number remained steady throughout the year, with the company detecting between 310,000 to 330,000 hacked WordPress sites at any given time last year. A total of 1.2 million WordPress sites appear to have been hacked last year, and of these, 210,000 appeared infected at the start and end of the year, meaning there was no one maintaining them.
Malware technical reports
DragonSpark and SparkRAT: SentinelOne says it has spotted a Chinese-speaking actor breaking into web servers and MySQL databases and deploying a version of SparkRAT, a new Go-based remote access trojan that was open-sourced in November of last year by a Chinese developer. The vast majority of these attacks, which SentinelOne called DragonSpark, have targeted the networks of East Asian organizations. SentinelOne says the same SparkRAT malware was also used by another malware botnet named Zerobot, but they "have not observed concrete evidence" linking DragonSpark to this group so far.
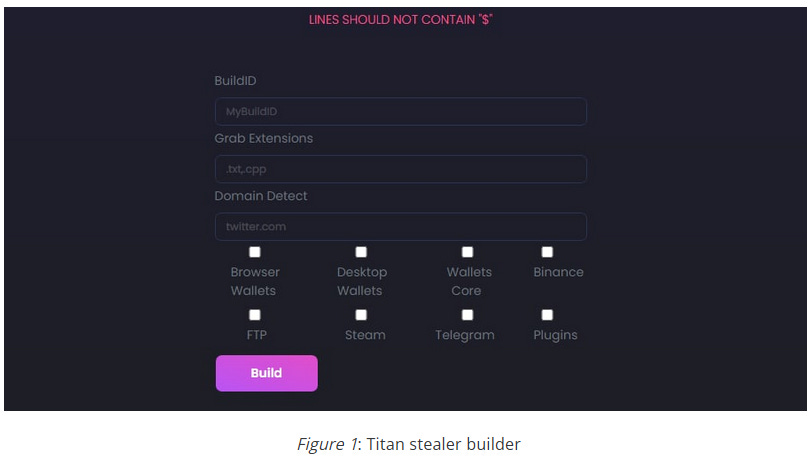
Titan Stealer: Uptycs has published a report on the new Titan Stealer malware, currently advertised on a Russian-speaking Telegram channel. The malware is your typical infostealer designed to steal data from browsers, FTP clients, and crypto-wallets. The malware is currently being sold for $900 or rented for $150/month, somewhat of a high price for an infostealer.
Vulnerabilities and bug bounty
iOS zero-day: Apple has released security updates for iOS and macOS, including a patch for an actively exploited zero-day (CVE-2022-42856). Discovered by a Google security researcher, Apple said it is aware the vulnerability "may have been actively exploited against versions of iOS released before iOS 15.1." The zero-day resides in the WebKit browser engine, and Apple has released iOS 12.5.7 to patch the vulnerability.
Zoho exploitation: A day after security firm Horizon3 published proof-of-concept code for a remote code execution vulnerability in the Zoho ManageEngine, attacks have been spotted in the wild. Security firm Rapid7 says it is responding to multiple compromises at various companies, compromises that were linked to Zoho ManageEngine products. The company said threat actors were using the vulnerability to gain access to ManageEngine servers, disable security tools, and download and install remote access tools. The vulnerability exploited in these attacks is CVE-2022-47966, for which Zoho released patches last October.
CVE-2022-38181 (Android): GitHub's Security team has a write-up on CVE-2022-38181, a vulnerability in Arm's Mali GPU driver for Android. The bug was used to take over the Google Pixel 6 phone and was patched last October.
CVE-2023-0210 (Linux): Sysdig researchers have a write-up on CVE-2023-0210, an unauthenticated remote code execution against KSMBD, a Linux kernel daemon that implements support for the SMBv3 protocol. While the bug looks pretty bad, its impact is limited as the KSMBD is not enabled by default on most Linux distros.
New bug class: ZDI's Simon Zuckerbraun has a write-up on a new class of vulnerabilities that he named "activation context cache poisoning" that impacts the Windows Client/Server Run-Time Subsystem (CSRSS) service. Successful exploitation generally results in privilege escalation. One of these bugs, CVE-2022-22047, has already been exploited in the wild by a hacker-for-hire group Microsoft tracks as KnotWeed.
DensePost: A team of researchers from Carnegie Mellon University has designed a system that uses the signals from simple WiFi routers to detect and perceive the 3D shape, pose, and movements of humans inside a room. The system, which they called DensePost, uses a deep neural network to process the phase and amplitude readings from at least three WiFi antennas in order to identify and track human bodies inside a room. Researchers hope their work "paves the way for low-cost, broadly accessible, and privacy-preserving algorithms for human sensing."

Infosec industry
Bitwarden analysis: In the aftermath of the recent LastPass breach, security researcher Wladimir Palant has analyzed the design and security of the Bitwarden password manager client.
Acquisition news: Private equity company ThomaBravo has announced plans to acquire incident response and digital forensics software company Magnet Forensics for a whopping $1.33 billion. Thoma Bravo says it plans to combine Magnet Forensics with Grayshift, another company that builds forensics tools under its portfolio.
New tool—GATO: Security firm Praetorian has open-sourced a tool called GATO (Github Attack TOolkit) for evaluating the security of an organization's GitHub infrastructure.
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




