Risky Biz News: Facebook takes down NodeStealer malware before it can take off the ground
In other news: Former Uber CSO avoids prison time; MSI private keys leak following ransomware attack; US takes down Pay2Check card-checking service; passkeys come to your Google account.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Meta's security team has disrupted the operations of a newly launched malware family named NodeStealer.
The company says it caught the malware shortly after it launched and, through cooperation with domain registrars and hosting providers, took down all of its web infrastructure.
Meta says the malware launched in late January, and following its efforts, they have not seen any new NodeStealer samples since February 27.
In a technical write-up, Meta says the malware was designed to infect Windows systems, install a modified version of the Node.js JavaScript runtime, and then extract credentials and authentication/session cookies from a victim's local browser.
The malware specifically targeted user credentials for Facebook, Gmail, and Outlook. In the case of Facebook, Meta says the NodeStealer operators accessed customer accounts using the compromised logins, bypassed 2FA, and, if the user had access to the Facebook Advertising platform, ran malicious ads.
Meta says the malware appears to have been created and distributed by threat actors based in Vietnam.
This would mark the third known malware operation based out of Vietnam that's focused on compromising Facebook advertising accounts and using them to post malicious ads. Previous operations include the likes of Ducktail and Malverposting.
Meta's takedown of NodeStealer comes a week after Google also took steps to disrupt the operations of CryptBot, another infostealer strain focused on stealing credentials and cookies for online accounts.
Breaches and hacks
MSI private key leak: The Money Message ransomware gang has leaked the private cryptographic keys for hundreds of MSI products, according to Alex Matrosov, the founder and CEO of firmware security company Binarly. Leaked private keys include firmware image signing keys for 57 MSI products and Intel BootGuard keys for 116 MSI products [see the full list here]. The leak originates from a ransomware attack that hit MSI's US branch at the start of April, during which the company refused to pay the ransom.
Orqa bricking incident: Croatian company Orqa says that "a greedy former contractor" planted a "ransomware time-bomb" in the firmware of some of its products with the intention of extracting a ransom. Orqa says the time bomb triggered over the last weekend, on April 29, and crashed the bootloader of Orqa first-person view googles used to visualize and experience drone flight paths. The company says the malicious code was planted in its firmware years in advance, and the incident was intentionally timed to take place on the Saturday of the May 1st Labor Day extended weekend when its support teams would not be in office, and most drone owners would be flying their devices. The company says the contractor tried to explain the malicious bootloader code as an expiring license. Orqa has released fixes for owners with bricked devices and has hinted at "pending legal and criminal proceedings."
Bluefield ransomware attack: A ransomware gang has breached the internal network of a private US university and hijacked its emergency alerts system to threaten students and faculty members with leaking their data unless the administration paid a ransom demand. The incident affected Bluefield University, a small, private university in the state of Virginia. The university's RamAlerts system is typically used to warn students via email and SMS about the cancellation of classes due to weather, IT outages, and active shooter drills. The Avos ransomware gang took credit for the incident in some of the messages sent throughout last week. [Additional coverage in WVVA]
Dallas ransomware attack: Dallas, the 9th largest city in the US, was hit by a ransomware attack that has disrupted its IT networks and official websites. The city's 311 public service hotline, municipal court, police department, and city hall IT services have been disrupted. The attack took place on Wednesday, May 3, and was allegedly carried out using the Royal ransomware, which apparently started printing its ransom note via all of the city's available printers. [Additional coverage in The Dallas Morning News, BleepingComputer]
General tech and privacy
FTC proposes ban on Facebook monetizing youth data: The US Federal Trade Commission has proposed barring Meta from monetizing children's data. FTC officials say the company violated a 2020 privacy order in regard to its Facebook Messenger for Kids service. The agency says Meta misled parents about their ability to control with whom their children communicated through the Messenger Kids app and misrepresented the access some app developers had to children's data.
40+ orgs sign open letter: More than 40 leading pro-privacy organizations have signed an open letter to urge governments around the globe "not to follow the path of authoritarian governments like Russia and Iran" and defend encryption, privacy, and press freedom. Organizations that have signed the letter include the Tor Project, Mozilla, Proton, Threema, Tutanota, the Document Foundation, and Mullvad, among many others.
"The letter pushes back against regulatory and legislative actions that undermine rights and freedoms such as privacy, security, access to knowledge, freedom of expression, self-determination, and freedom of the press. Signatories call on governments to: (a) ensure that encryption is not being undermined via overreaching legislative initiatives (b) ensure that technologies providing secure, encrypted services are not being blocked or throttled (c) revisit any bills, laws and policies that legitimize undermining encryption or blocking access to services offering encrypted communication."
Discord changes username format: Instant messaging service Discord plans to change the format of its user accounts and move away from the "username#code" format to the classic @username system typically used by Twitch and Twitter. The company plans to prompt users over the coming weeks to choose a unique username. The move is expected to lead to a rise in the prices of Discord accounts sold on hacking forums, where OG accounts are highly-valued.
Mullvad VPN raid: Swedish VPN provider Mullvad has published an update related to a police raid the company dealt with at the end of last month. Mullvad says the raid "was connected to a blackmail attack that hit several municipal institutions in the state of Mecklenburg-Western Pomerania in October 2021"—most likely in connection to a ransomware attack. Swedish police tried to obtain data on Mullvad users, but they left empty-handed after learning from Mullvad they weren't storing such information.
Dashlane goes passwordless: Password management application has removed its "master password" and has gone passwordless. This is a custom passwordless system, and the company says it's still working to integrate passkeys. The custom system uses biometrics authentication.
1Password snafu: Password management application 1Password says the user notifications it sent last week about changes to a user's account passwords and secret keys were the result of a glitch in one of its planned database maintenance windows.
Android security updates: ...for May 2023 are out!
Exchange update/modernization: Microsoft has released a security update for its Exchange Server 2019 email server that adds support for OAuth 2.0-based authentication.
Google adds passkeys support: Google has rolled out support for passkeys for Google Accounts across all services and platforms. Passkeys are a new technology meant to replace passwords and allow users to access an online account by authenticating on their computer or mobile phone using a fingerprint, facial scan, or a local PIN. Passkey authentication mechanisms are already supported in Chrome and all the major browsers, but passkeys still need to be supported on the server side by the online service. Google now joins a list of 40 other online service providers that support passkeys for user authentication, such as Microsoft, eBay, PayPal, and Shopify. Users can enable a passkey for their Google account by going into their account's security settings section.
Government, politics, and policy
Malaysia warned of Huawei 5G risk: Representatives from the EU and US have warned the Malaysian government about the national security risks of allowing China's Huawei to bid to build the country's future 5G network. The warning comes as the Malaysian government appears to be backpedaling on an initial decision to grant the contract to Swedish company Ericsson. [Additional coverage in Reuters]
Mexico's migrant tracking: A report from investigating journalism group R3D reveals how the Mexican government has been using unmanned drones, forensic scanners, and biometric systems to monitor the movement of migrants through its territory.
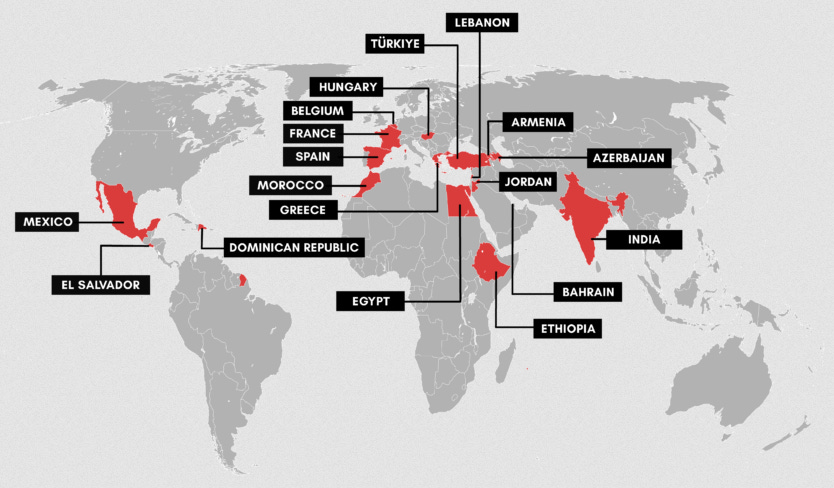
NSO spyware in the Dominican Republic: Amnesty's security team has discovered traces of the NSO Group's Pegasus spyware on the personal device of Nuria Piera, one of the Dominican Republic's most prominent investigative journalists. Researchers say Piera's smartphone was infected three times between 2020 and 2021. Piera's work has primarily focused on issues of government corruption and impunity. Amnesty says it has now observed cases of spyware deployed against journalists in 18 countries around the world.
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
Cybercrime and threat intel
Former Uber CSO walks: Former Uber chief security officer Joe Sullivan was sentenced to three years probation and wil avoid prison time after covering up a 2016 Uber data breach. Prosecutors were seeking a sentence of 15 months imprisonment. Sullivan's legal team argued that sending him to prison would deter skilled individuals from taking CSO and CISO positions in the future, fearing they would be asked to hide breaches and then made scapegoats. [Additional coverage in the Washington Post / non-paywall]
Try2Check takedown: US authorities have charged Russian national Denis Gennadievich Kulkov with running Try2Check (or Try2Service), an underground service used by carding gangs to check the validity of stolen credit cards. Authorities have taken down the site's servers and are offering a $10 million reward for any information leading to Kulkov's arrest. The US Justice Department estimates Kulkov made more than $18 million in Bitcoin from the site. The service launched in 2005, and officials say Try2Check became a "primary enabler" in the trade in stolen credit card information, processing tens of millions of card numbers every year.

Powershell obfuscation: Alexander Hübert has a blog post on the many attacker methods to obfuscate and hide malicious Powershell code and how to detect and analyze them.
IPFS abuse: DomainTools joins the ranks of Cisco Talos, Trustwave, Palo Alto Network, and Trend Micro to warn that threat actors are increasingly adopting the IPFS peer-to-peer protocol as part of phishing infrastructure.
Avast Q1 2023 report: Cybersecurity firm Avast says that in the first quarter of 2023, infostealers and phishing operations have remained the top threats to desktop consumers. On the mobile side of things, adware is still king, with more than three-quarters of all detections.
Bassterlord profile: Analyst1 has published the second part of its profile on the LockBit ransomware gang, this time covering Bassterlord, a Ukrainian cybercriminal who used to work as an affiliate for the gang but has since retired (allegedly).
Anonymous Sudan: ThreatMon has published a 45-page report on Anonymous Sudan, the pro-Kremlin African and totally not-Russian hacktivist group. [wink-wink]
New GazpromLock ransomware: A new ransomware strain has been spotted in the wild since mid-April. Named GazpromLock, the ransomware uses the leaked source code of the Conti gang and an ASCII art of Putin's headshot.
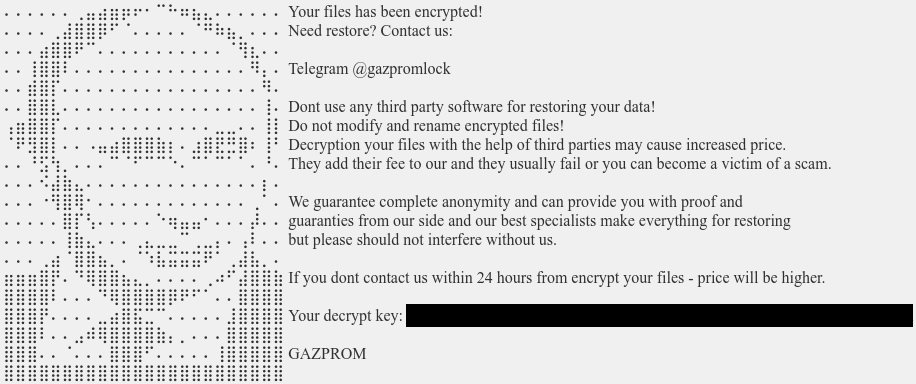
Malware technical reports
macOS infostealer market: Over the course of the past few months, three new macOS infostealers have been released and are currently being advertised on underground hacking forums and Telegram channels. Since the start of the year, security researchers have spotted new ads for macOS malware such as Pureland, MacStealer, and Atomic Stealer. All three are on par with infostealers available for the Windows market and are capable of grabbing account passwords, browser data, session cookies, and crypto-wallet configuration files. The emergency of these three new strains shows a clear trend, and macOS users should take it as an early warning and be more careful about what apps and from where they install on their devices going forward.
ZarazaBot: ThreaMon researchers have published a technical breakdown of the new ZarazaBot infostealer, currently heavily advertised on underground hacking forums.
drIBAN: Cleafy has published a report on drIBAN, a web injection kit that has been sold on underground markets since 2019. The tool is primarily used to perform Man-in-the-Browser attacks that modify the content of a web page in real time. It is typically used as a component inside various banking trojans.
RecordBreaker Stealer: And staying on the topic of infostealers, AhnLab researchers have spotted a new one—named RecordBreaker Stealer—being spread via hacked YouTube accounts promoting game cheats, keygens, and cracked software.
TrafficStealer: Trend Micro has discovered a threat actor targeting misconfigured cloud resources to install a Linux container that generated money by driving traffic to specific websites and engaging with ads. TrendMicro says it's tracking this malware operation under the name of TrafficStealer.
IcedID: We had two IcedID reports this week. PAN's Unit42 has an analysis of IcedID's configuration, while LoginSoft has a report on IcedID's evolution through the years.
Raspberry Robin: Equinix security researcher William Thomas has a write-up on the Raspberry Robin USB worm, which over the past year, has been used as an entry point for ransomware attacks.
CrossLock ransomware: Netskope has a report on CrossLock, a new big-game hunting ransomware gang that launched in April 2023. Just like most ransomware gangs these days, the group operates a dark web leak site. According to Netskope, the group's ransomware is written in Go, and their leak site currently lists just one victim org.
Fleckpe Android trojan: Kaspersky researchers have discovered 11 Android apps available through the official Play Store that were infected with a new Android trojan. Named Fleckpe, the malware operates by subscribing users to unwanted premium services. Kaspersky says the malware appears to have been active since 2022 and has infected more than 620,000 devices so far.
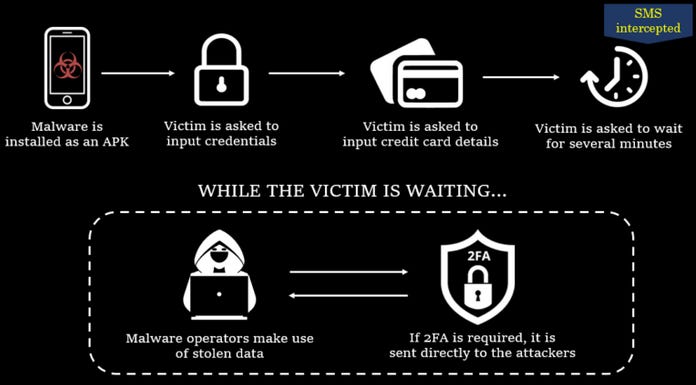
FluHorse Android trojan: Check Point researchers have spotted a new Android malware strain named FluHorse that mimics legitimate applications in order to infect users and steal mobile banking credentials, bypass 2FA, and then steal funds from their bank accounts. Check Point says they found the malware in two apps available on the official Play Store, both of which were installed more than 1 million times. The two apps targeted users located in Vietnam and Taiwan, but researchers believe other apps are still out there targeting other Eastern Asian countries.
Sponsor Section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
APTs and cyber-espionage
Mustang Panda: Lab52 says the Mustang Panda Chinese cyber-espionage group is targeting Australian government organizations.
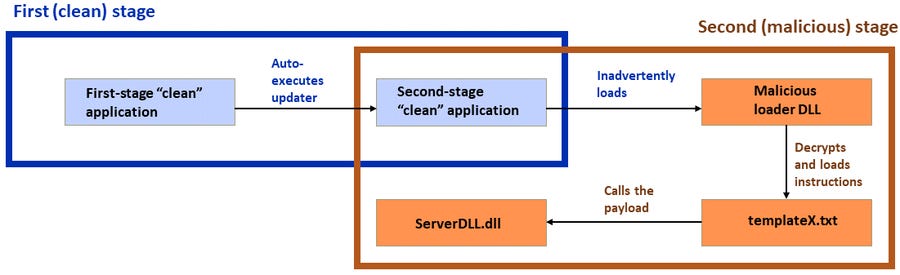
Dragon Breath: An APT group named Dragon Breath (Golden Eye Dog, APT-Q-27) has been using "double DLL loading" to evade detection and load malicious payloads on compromised systems. The group typically targets Chinese-speaking users that engage in online gambling. According to Sophos, the group's most recent campaign targeted Windows users via Telegram in countries such as the Philippines, Japan, Taiwan, Singapore, Hong Kong, and China.
CryptoMimic/SnatchCrypto: Japan's CERT team says it detected a new campaign carried out by CryptoMimic (SnatchCrypto), a North Korean APT group specialized in attacks targeting cryptocurrency exchanges. The new campaign (named DangerousPassword) used job lures sent via LinkedIn to infect users via CHM and OneNote files that infected a user's Windows systems and then tried to pivot to nearby macOS machines. [Item updated on May 14 with link to English version of the report]
Kimsuky: SentinelOne has a report on Kimsuky's latest campaign that involved the distribution of a new malware strain named ReconShark.
"ReconShark functions as a reconnaissance tool with unique execution instructions and server communication methods. Recent activity has been linked to a wider set of activity we confidently attribute to North Korea."
SideCopy: Fortinet published a report on recent campaigns of Pakistani APT group SideCopy.
Meta's Q1 2023 APT report: Meta took down accounts used by several APT groups to target audiences across South Asia. The company says it suspended Facebook and Instagram accounts operated by the likes of hacker-for-hire group Bahamut, Indian APT group Patchwork, and an unnamed Pakistani state-linked actor. Meta says the groups used profiles on its sites to approach victims and lure them to malware download or credentials phishing websites. In addition, Meta says it also suspended accounts used for influence operations out of China, Iran, Venezuela+US, Georgia, and Togo+Burkina Faso. The purpose of these info-op networks ranged from financially motivated to political spamouflage. More in Meta's Quarterly Adversarial Threat Report for Q1 2023 [PDF].
Qihoo's US hegemony report: Last month, ASPI researchers published a report on the Chinese government's social media disinformation campaign to portray the US as an "irresponsible cyber power." The report mentioned how some Chinese security firms contributed with some pretty lame and inaccurate reports to this campaign, which they named Operation Honey Badger. The latest of these reports comes this week from Qihoo 360, which goes over the CIA Vault7 leak and tries to pass the leaked files as proof that the US is running a Matrix-like "cyber hegemony." The report also accuses the US and the CIA of using technology to help support regime changes across the world. What technology? Well, mesh networks, secure messengers, and everything else an autocratic government doesn't usually like. Heck, the report claims Twitter's Speak2Tweet feature is a powerful regime-changing tool. The entire thing is just US fearmongering propaganda with no technical merit and completely in line with ASPI's Operation Honey Badger.
Intrusion Truth news: APT-doxing group Intrusion Truth is apparently prepping some news. [rubs hands together]
Vulnerabilities and bug bounty
New PaperCut PoC: VulnCheck researchers have developed a new PoC for the recent PaperCut vulnerability (CVE-2023-27350) that has been recently abused to breach and backdoor corporate networks. Researchers say the new PoC can bypass all known detection rules and exploit a PaperCut print management server without the attacker being detected.
Apple Beats firmware update: Apple has released a security update for its Beats headphones that fixes a Bluetooth attack vector that could grant attackers access to user devices. The issue was discovered by two ChromeOS devs—Yun-hao Chung and Archie Pusaka—and is a port of an AirPods fix from last month.
Cisco SPA vulnerability: Security researchers have found an unauth RCE in the web management interface of Cisco SPA112 phone adapters that could be used to take over the devices. In a security alert this week, Cisco told customers it does not plan to release a firmware update as the devices have reached end-of-life.
"This vulnerability is due to a missing authentication process within the firmware upgrade function. An attacker could exploit this vulnerability by upgrading an affected device to a crafted version of firmware."
CVE-2019-17558 (Apache Solr): Four years later, SCRT's Nicolas Brunner published a write-up and a PoC for CVE-2019-17558, an RCE in the Apache Solr search engine.
Azure API vulnerabilities: Ermetic researchers have discovered three vulnerabilities in the Azure API Management service, including a bug that could be used to bypass web application firewalls.
Packagist incident: A security researcher with the pseudonym 'neskafe3v1' hijacked 14 PHP libraries published on the Packagist repository as part of a stunt to help them find a job. Four of the packages had more than 20 million downloads, with one package having 528 million lifetime downloads. The Packagist team told BleepinComputer that no malicious impact had been observed on the platform as a result of the incident. Packagist says the hijacks took place after the researcher compromised maintainer accounts using weak credentials.
faulTPM attack: Academics from the Technical University of Berlin have devised a new attack against the firmware-based Trusted Platform Module (fTPM) of AMD processors. Named faulTPM, this is a voltage fault injection attack that can allow threat actors to access cryptographic data stored inside the fTPM. The attack requires "2-3 hours of physical access to the target device" and can be used to break stuff like BitLocker encryption. More in their paper.
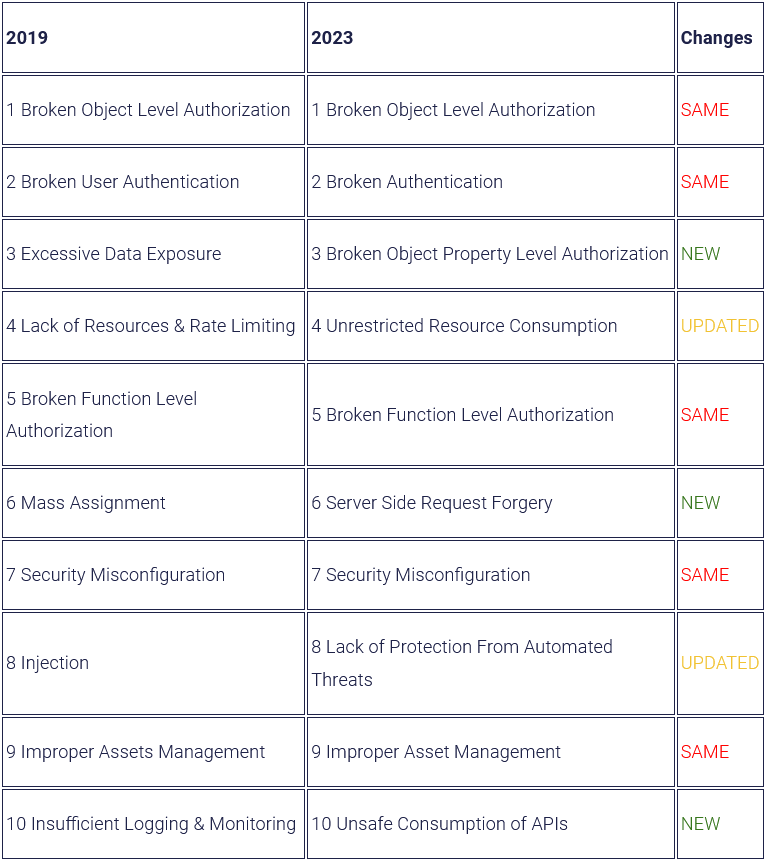
OWASP API Security Top 10 (2023 edition): The OWASP project published back in February a draft of its Top 10 API vulnerabilities, which is set for a refresh this year from its last edition released back in 2019. Tanya Janca has a summary of the changes between the two editions here.
Infosec industry
New tool—ETWHash: Cybersecurity firm Nettitude Labs has open-sourced a new tool named ETWHash that ingests ETW SMB events and extracts NetNTLMv2 hashes for cracking offline.
New tool—Dracon: Security firm Ocurity open-sourced back in February an ASOC (Application Security Orchestration and Correlation) tool named Dracon.
New tool—Microsoft 365 Extractor Suite: Invictus Incident Response has open-sourced a tool named Microsoft 365 Extractor Suite that can extract necessary IR data from various sources within Microsoft's cloud services.
Industry layoffs: Cybersecurity firm BishopFox has laid off 50 employees, or roughly 13% of its workforce.
New VT feature: Google has announced a new VirusTotal feature named the Crowdsourced YARA Hub that allows security companies and individual researchers with a VTI account to share and crowdsource YARA threat actor hunting rules.




