Risky Biz News: Facebook exposes large network of (low quality) fake news sites pushing Russian propaganda
In other news: Chile hit by ransomware for the second time in a month; Optus hacker changes its mind about selling the telco's data; and the UK ICO plans to fine TikTok on children's privacy violation
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
In a series of joint reports with Qurium, DFRLab, and the EU Disinfo Lab, Meta announced on Tuesday that it suspended Facebook and Instagram accounts that were part of a "large network that originated in Russia."
Meta's security team said this network of accounts began posting in May this year and targeted audiences primarily in Germany but also countries such as France, Italy, Ukraine, and the UK.
The accounts primarily posted links from over 60 websites carefully crafted to impersonate legitimate news organizations in Europe, including Der Spiegel, The Guardian, Bild, Süddeutsche Zeitung, Tagesspiegel, ANSA, and others.
These websites used typosquatted domains as close as possible to the original news site URLs in order to fool their readers and themes identical to the real sites. The sites would also host "articles that criticized Ukraine and Ukrainian refugees, supported Russia and argued that Western sanctions on Russia would backfire."
The fake accounts would then promote these propaganda articles on a variety of social networks—not just Meta properties—such as Facebook, Instagram, Telegram, Twitter, petitions websites like Change.org and Avaaz, and even the LiveJournal blogging platform.
Meta said that once its team blocked an initial wave of sites, the Russian propaganda network created new ones.
Furthermore, when some of these articles needed more visibility, the Facebook Pages of Russian embassies in Europe and Asia gladly lent a hand and shared it with their audiences, which is honestly no surprise at this point.
The fact that different disinformation labs spotted and documented this Russian network together with Facebook also stands testament to the obvious propaganda purpose of this operation and the low quality of their work. Here, Qurium has an insightful summary:
- Judging by how the 50+ fake news sites have been set up (hosting, CDN, SSL certificates, domain registrar), they are likely to be operated by one single actor.
- The use of the capabilities of tracking software Keitaro suggests that the operatives need to report on its success back to its supervisor or client.
- Although disinformation is being spread in no less than seven languages, the actor does not seem to possess these language skills but is using automatic translation services to localize the content.
- The actor works with staff in at least three time zones (UTC, GMT+2, GMT+8), corresponding to western Europe and the Irkutsk region in Russia.
But alas, disinformation efforts don't need to be carefully crafted. As it has already been proven, disinformation just needs to exist, and people will do the rest.
Breaches and hacks
Ransomware attack hits Chile's judiciary: The Chilean government got hit by a second ransomware attack in less than a month, after Sernac, the country's National Consumer Service, was hit at the end of August. This time, the attack hit the country's Judiciary branch, the PJUD, which said the attack only impacted a small portion of its enterprise network, specifically, only Windows 7 systems.
Ukraine backtracks on Viasat hack aftermath: Earlier this year, Victor Zhora, deputy chairman and chief digital transformation officer at the State Service of Special Communications and Information Protection in Ukraine, told media outlets that the hack of the Viasat satellite internet network led to a "huge huge loss in communications in the very beginning of war." But in an interview with natsec reporter Kim Zetter at the LABScon security conference last week, Zhora said there was a misunderstanding around that quote. Zhora said that while there was a loss of communications for the Ukrainian military's Viasat connectivity, troops coordinated operations just fine, as their primary means of communications were landlines, with Viasat being only its backup solution.
Auth0 discloses security incident: Authentication and authorization platform Auth0 disclosed a security incident on Monday, revealing that a threat actor gained access to older Auth0 code repositories dating before October 2020. Auth0, who is now owned by Okta, said the threat actor did not gain access to any customer information.
We immediately launched a thorough internal investigation and enlisted the services of a leading third-party cybersecurity forensics firm. Both investigations, recently concluded, confirmed that there was no evidence of unauthorized access to our environments, or those of our customers, nor any evidence of any data exfiltration or persistent access.
Cheat maker says game studio hacked its employee: Bungie, the maker of the Destiny video game series, has been countersued by the popular cheat maker AimJunkies over claims that Bungie violated the DMCA on AimJunkies cheats, hacked one of their contractor's computers, and violated copyright law by reverse engineering the software to build countermeasures against it. [More on this drama in Motherboard]
Dutch commando part of IT Army of Ukraine: A report from Dutch newspaper De Volkskrant tells the story of a former Dutch commando member who joined the IT Army of Ukraine and has conducted cyberattacks against Russian targets. Going by the name of Hactic, the Dutch commando took credit, among other things, for hacking Aeroflot, Russia's largest airline, from where he stole passenger lists and radar positions that he later shared with Ukraine's SBU service.
Optus hacker backtracks: The hacker who breached, stole, and tried to sell data from Australian telco Optus has changed their mind, removed a forum entry advertising the company's data, and posted a new entry apologizing to Optus for the intrusion. It is unclear what caused this sudden change of heart, but infosec reporter Jeremy Kirk says that Optus has not paid a ransom to the attacker, so this looks like a decision taken on the hacker's side.
The old post is now deleted. The data samples are gone. Here is the new post (ht to @allyjfoster for sending it to me while I was out getting cat food).
— Jeremy Kirk (@Jeremy_Kirk) 12:58 AM ∙ Sep 27, 2022
deleting your extortion threat on a hacking forum after the AFP announces an international operation is self care 😊
— cammyboo KC (@cameronwilson) 12:26 AM ∙ Sep 27, 2022
In the meantime, the Australian government said that since driver's license numbers were stolen in the breach, anyone whose data was leaked in the Optus incident can apply for a free replacement.
General tech and privacy
Rust coming to Linux 6.1: The first components written in the Rust programming language are coming to the official Linux kernel with its upcoming v6.1 release, Linus Torvalds announced last week, speaking at the Kernel Maintainers Summit.
Chrome 106: A new version of the Google Chrome browser is out, including 20 security fixes.
Tracking via parking apps: In a study conducted between June and September 2022, security researcher Inti De Ceukelaire said he was able to track down cars based on data made available by parking applications. De Ceukelaire said he was able to find the cars of 35 of 120 volunteers (29%) who signed up for the study just by querying parking apps for certain license plates. The study's results are available in this paper and are also summarized in this Twitter thread.
TikTok fine coming in the UK: The UK's data privacy watchdog, the Information Commissioner's Office, said this week that TikTok could face a £27 million fine in the country following an investigation that found that the company failed to protect children's privacy on its service. More specifically:
- TikTok processed the data of children under the age of 13 without appropriate parental consent,
- TikTok failed to provide proper information to its users in a concise, transparent, and easily understood way, and
- TikTok processed special category data without legal grounds to do so.
The ICO issued a note of intent this week to TikTok, and the company will have an opportunity to counterargue against the possible fine.
Government, politics, and policy
Ukraine warns that the Kremlin is preparing cyber-attacks: Officials from the Main Directorate of Intelligence of the Ministry of Defense of Ukraine said on Monday that Russia is preparing "massive cyberattacks" on the critical infrastructure of Ukraine and its allies.
With this, the enemy will try to increase the effect of missile strikes on electricity supply facilities, primarily in the eastern and southern regions of Ukraine. The occupying command is convinced that this will slow down the offensive actions of the Ukrainian Defense Forces. The Kremlin also intends to increase the intensity of DDoS attacks on the critical infrastructure of Ukraine's closest allies, primarily Poland and the Baltic states.
Securing the IoT landscape: The Atlantic Council think tank has published a paper on the policy challenges of securing the IoT landscape in countries such as the UK, the US, Singapore, and Australia.
QUAD statement on ransomware: Members of the QUAD state alliance (India, Australia, Japan, and the United States) have reaffirmed their commitment to fighting ransomware in a joint statement issued last week.
US Coast Guard cyberspace workforce report: A GAO report found several deficiencies in how the US Coast Guard manages its cybersecurity workforce, including a possible disconnect with staffing levels needed to meet its cyberspace mission demands. Based on the most recent data, the Coast Guard has filed 91% of its cybersecurity roles, but since the agency lacks an assessment of the actual number of cyberspace experts needed for its mission, the staff shortage could actually be higher than 9%.
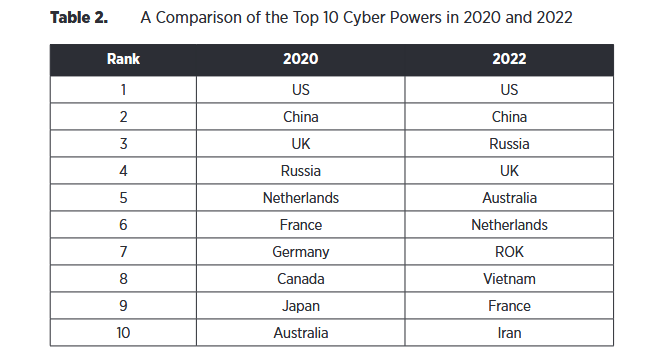
National Global Cyber Index 2022: Belfer Center's ranking that rates and organizes countries based on their "cyber power" has reached its second edition. In the spirit of all cyber-related academic research, please don't forget to go on social media to criticize its methodology and attack the authors if your country is not on the list at the position you envisioned. </sarcasm>
Sponsor section
RunZero (formerly Rumble Network Discovery) is one of this newsletter's four main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network. To learn more, please check out this runZero product demo below:
Cybercrime and threat intel
Phishing gang detained in Turkey: Turkish authorities said they detained a cybercrime gang comprised of ten members in the Diyarbakır province. Authorities said the group ran email-based phishing campaigns through which they collected their victim's passwords for various online accounts. Four members were released, while six still remain in custody.
DDoS threat landscape: Network security company Netscout has published a report on the DDoS threat landscape for the first half of the year. Main findings below:
- There were 6,019,888 global DDoS attacks in the first half of 2022.
- Malware botnet proliferation grew at an alarming rate, with 21,226 nodes tracked in the first quarter to 488,381 nodes in the second, resulting in more direct-path, application-layer attacks.
- When direct attacks failed, attackers switched to DNS water-torture attacks, and this trend accelerated into 2022 with a 46% increase primarily using UDP query floods against DNS nodes.
- Similarly, DDoS carpet-bombing attacks experienced a big comeback toward the end of the second quarter.
- The new TP240 PhoneHome reflection/amplifications DDoS vector was discovered in early 2022 with a record-breaking amplification ratio of 4,293,967,296:1; swift actions eradicated the abusable nature of this service.
- TCP-based flood attacks (SYN, ACK, RST) remain the most used attack vector, with approximately 46% of all attacks continuing a trend that started in early 2021.
- DNS amplification attacks decreased by 31% from 2H2021 to 1H2022.
New method of deleting volume shadow copies: VMWare's security team published a report last week on a new technique they encountered in the wild, used by the Hello ransomware gang to delete volume shadow copies on systems they encrypted. Deleting volume shadow copies prevents recovering previous versions of deleted/encrypted files. Normally, security software keeps track of when an app tries to delete volume shadow copies, but VMWare says this technique can "bypass many forms of detection and prevention."
@campuscodi This is the method that was developed by vx-underground member @am0nsec. The code base was developed and documented 14-months ago. It is interesting that @VMware did not know this...
— vx-underground (@vxunderground) 4:42 PM ∙ Sep 27, 2022
npm malware: Twenty-three JavaScript libraries were removed from the npm portal over the past two days after researchers found malware hidden in their code. See the list here.
Scammers target Russian draft dodgers: The security team of Russian bank Sberbank said it spotted a new scam going online, with cybercrime groups offering fake certificates of unfitness for military service—also known as white military IDs—to Russian men trying to avoid being mobilized by state authorities and sent to the Ukrainian front.
Scammers capitalize on energy crisis: In the meantime, scammers are also capitalizing on the war in Ukraine and its aftermath on the other side of the continent as well. Dutch police said on Tuesday that it received more than 500 reports about more than 60 webshops advertising wood pellets and firewood for the upcoming winter and possible energy and heating crisis but never delivering the paid goods.
Fake Cloudflare CAPTCHA pages: Sucuri said it was tracking a malware distribution campaign using fake Cloudflare CAPTCHA solving pages to trick users into downloading and installing malware on their devices.
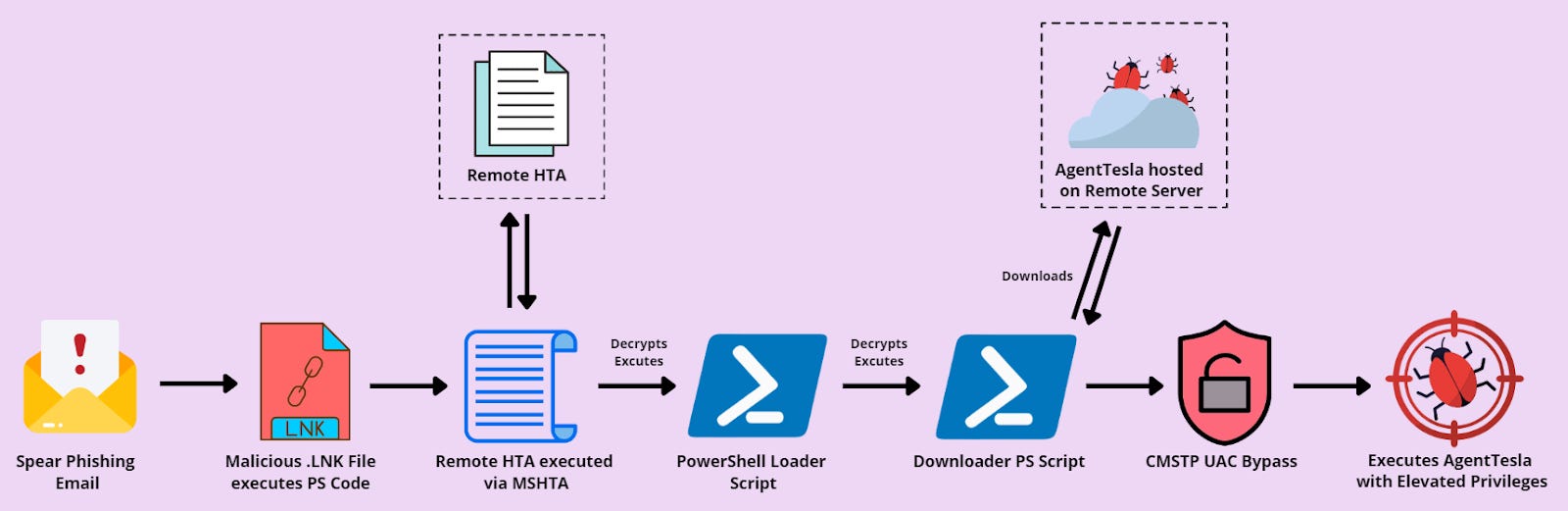
Agent Tesla campaign: Zscaler has a report out on a new malspam campaign delivering versions of the Agent Tesla keylogger and infostealer.
Malware technical reports
Bumblebee: The DFIR Report team has an update on the operations of the Bumblebee malware loader service, which they first covered in a report last month.
Pegasus spyware: Part two of a technical analysis of the Pegasus spyware is now live. Part one is here.
Zimbra web shells: CISA published on Tuesday three malware reports on three JSP web shells found deployed on Zimbra servers [1, 2, 3].
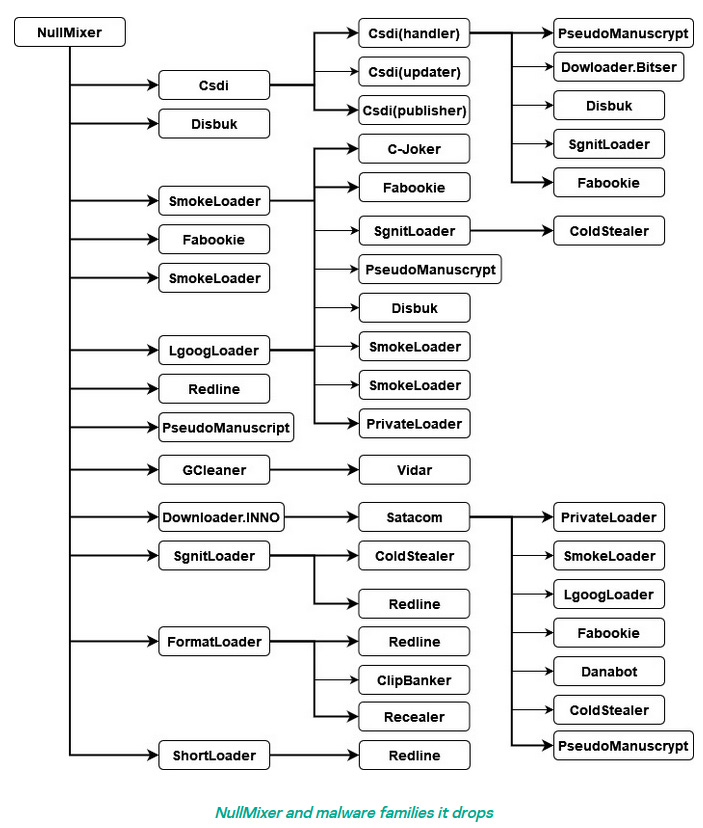
NullMixer: Kaspersky researchers have analyzed NullMixer, a new malware dropper family linked to SEO spam campaigns spreading a large number of various malware strains, but mostly infostealers.
APTs and cyber-espionage
Operation In(ter)ception: SentinelOne has a report out on Operation In(ter)ception, a Lazarus APT op targeting macOS users with cryptocurrency sector-related job offers.
APT targets military contractor: Securonix researchers said they identified a new covert campaign targeting multiple military and weapons contractors, including a strategic supplier to the F-35 Lightning II fighter aircraft. Securonix named this campaign STEEP#MAVERICK but did not attribute it to any specific threat actor.
Unattributed APTs: A fun and puzzling thread from Kaspersky's Costin Raiu on still-unattributed APTs. If you don't wanna go on Twitter, the list includes Project TajMahal, DarkUniverse, PuzzleMaker, Project Sauron (Strider), some clever USB worm, White Tur, PlexingEagle [PDF], SinSono, AcidBox, and Metador.
Here's my top 10 big "unattributed" #APT mysteries:
— Costin Raiu (@craiu) 11:25 AM ∙ Sep 23, 2022
Vulnerabilities and bug bounty
Vultron: Academics from the Carnegie Mellon University open-sourced Vultron, a new protocol for coordinated vulnerability disclosure (MPCVD), and a system specifically designed for coordinating across multiple parties, including both research parties and equipment vendors.
Infosec industry
New tool—YARI: Antivirus maker Avast open-sourced on Tuesday a new tool called YARI that works as a debugger for writing YARA rules. YARI is written Rust and is available as a Python package and a module for the YARA Language Server (YLS).
New tool—DNS Reaper: UK DevOps security firm Punk Security open-sourced last month a new tool called DNS Reaper that can scan and test domains for subdomain takeover attacks.
Snowden is officially a Ruski now: Russian President Vladimir Putin has granted Russian citizenship to former US NSA security contractor Edward Snowden.
@McGrewSecurity Of course, he's already been serving for years
— Shane Huntley (@ShaneHuntley) 10:22 PM ∙ Sep 26, 2022
I wonder if NASA could lend us one of its DART spacecrafts so we can yeet Snowden into the sun!
I don't care about your personal life, I want you to resign as President of the Freedom of the Press Foundation & stop making a mockery of our profession while you reside complicit in a fascist dictatorship that executes journalists in cold blood. Resign.
— Oz Katerji (@OzKaterji) 9:57 AM ∙ Sep 27, 2022
The President of the Freedom of the Press Foundation spent the lead-up to Russia's invasion of Ukraine attacking the Press for accurately reporting what the dictator he lives under was planning. Then he stopped discussing the war altogether. Insidious.
— Oz Katerji (@OzKaterji) 10:17 AM ∙ Sep 27, 2022
Edward Snowden has made zero comment on any of the journalists murdered in Ukraine by the Russian dictatorship. The President of the Freedom of the Press Foundation. How are you not fucking appalled at this?
— Oz Katerji (@OzKaterji) 10:18 AM ∙ Sep 27, 2022




