Risky Biz News: F-Droid narrowly avoided XZ-like incident in 2020
In other news: CSRB report scolds Microsoft over China hack; new Chrome feature fights auth cookie theft; anti-Kremlin hacktivists breach Russia's prison system.

This newsletter is brought to you by Resourcely, the company that can help you manage Terraform securely. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Back in June 2020, a mysterious individual tried to insert an SQL injection vulnerability in F-Droid, an open-source app store for Android devices.
The incident was disclosed this week by Hans-Christoph Steiner, the project's current lead developer.
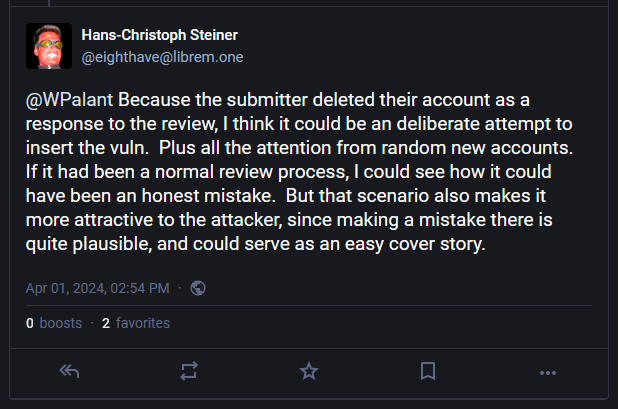
Steiner likened it to the recent XZ Utils backdoor incident.
Just like in the XZ incident, a new account submitted code to the project, and then a bunch of other new accounts began pressuring the F-Droid team to merge (accept) the code.
Steiner says the project got really lucky as they spotted the SQL injection bug before caving to the pressure.
The new code was supposed to improve F-Droid's search functionality by improving its SQL query concatenation.
"The author of the [original] SQL code was no longer involved," Steiner wrote on Mastodon this week. "I suck at SQL but was well aware that string concat to build SQL queries is a bad idea. So I was terrified to merge any changes to the SQL without really confirming them."
Since SQL query concatenation is a complex operation that may result in honest mistakes, some security researchers suggested this might have been an honest mistake from the individual who submitted the code.
Steiner dismissed this theory because of the concerted effort from new accounts to have the code included and because the threat actor deleted their account after the SQL injection was discovered.
Breaches, hacks, and security incidents
OWASP data breach: The OWASP Foundation has disclosed a data breach that involved its old wiki web server. Members who applied between 2006 and 2014 had their resumes exposed online due to a directory misconfiguration. Exposed data includes names, email addresses, phone numbers, physical addresses, and other personally identifiable information. OWASP says it is now notifying affected members and applicants.
Russian prison system hack: An anti-Kremlin hacktivist group has hacked Russia's prison system following the death of opposition leader Alexey Navalny. The hackers claim they stole a database containing the data of hundreds of thousands of Russian prisoners. The database contains information on prisoners, their families, and contact information. The hackers claim they are a mix of nationalities, including Russian expats and Ukrainians. [Additional coverage in CNN]
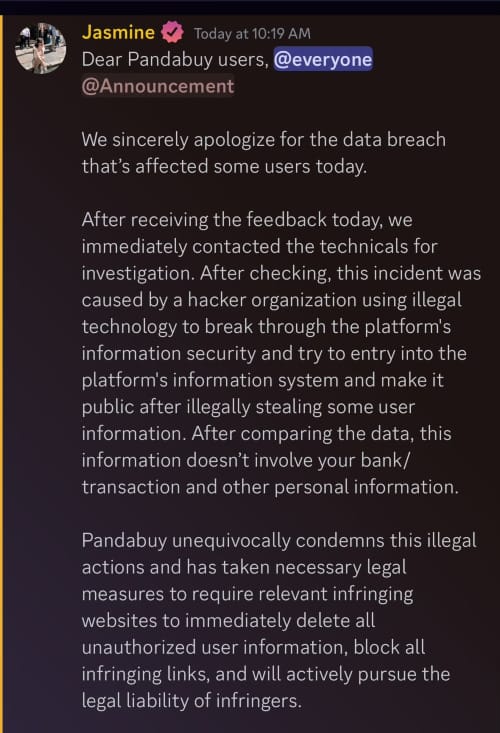
PandaBuy breach: Hackers have stolen the personal data of 1.3 million PandaBuy customers. The online shopping platform confirmed the breach after hackers posted the data for sale online. PandaBuy initially denied the breach for days until users started confirming the authenticity of the stolen information. [Additional coverage in BleepingComputer]
General tech and privacy
Chrome incognito mode lawsuit: Google has settled a class-action lawsuit and has agreed to delete user data it collected through the Chrome browser's private browsing mode. The company was sued for breaching user privacy in 2020 after users learned that Google was tracking their movements even in Chrome private browsing sessions. Google settled the lawsuit after plaintiffs allegedly asked for $5 billion in monetary damages. As part of the settlement, Google will also redesign Chrome's private browsing mode. [Additional coverage in the BBC]
Chrome DBSC: Google is working on a new Chrome security feature named Device Bound Session Credentials (DBSC). The new feature binds an authenticated website session to the user's device. Once implemented, the feature will prevent hackers from using stolen authentication cookies to bypass MFA and access online accounts. Google hopes the new feature will become an open web standard and be adopted by other browsers. Google is currently testing DBSC with Chrome beta versions.
PQ features coming to Chrome 124: Chrome 124, which will be released later this month, will ship with support for the ML-KEM (Kyber) key encapsulation system, a post-quantum encryption safety feature. The feature will be turned on by default for all users.
Open Source Cybersecurity Standards: Seven major open-source foundations say they will work together to establish new open-source cybersecurity standards. The new standard will be compliant with the EU's new Cyber Resilience Act (CRA). Founding members include the PHP Foundation, the Apache Software Foundation, the Blender Foundation, the OpenSSL Software Foundation, the Python Software Foundation, the Rust Foundation, and the Eclipse Foundation. The EU CRA introduces new requirements for secure-by-design and robust supply chain security standards. It is set to enter into effect in 2027.
NetBSD 10: NetBSD v10.0 is now out. No XZ backdoor, I was told. 🤣
Sunlight: Let's Encrypt has launched Sunlight, a new Certificate Transparency (CT) log.
"We’ve released software and a specification for Sunlight, and have Sunlight CT logs running. Head to sunlight.dev to find resources to get started. We encourage CAs to start test submitting to Let’s Encrypt’s new Sunlight CT logs, for CT Monitors and Auditors to add support for consuming Sunlight logs, and for the CT programs to consider trusting logs running on this new architecture. We hope Sunlight logs will be made usable for SCTs by the CT programs run by the browsers in the future, allowing CAs to rely on them to meet the browser CT logging requirements."
Government, politics, and policy
CSRB report scolds Microsoft: The DHS Cyber Safety Review Board (CSRB) has published its long-awaited report on Microsoft's Storm-0558 hack from May of last year. As it was widely expected, the report found Microsoft at fault for the intrusion, which officials called it "preventable" and that it "should never have occurred." The report's seven conclusions are below.
- There was a cascade of Microsoft avoidable errors that allowed this intrusion to succeed;
- Microsoft failed to detect the compromise of its cryptographic crown jewels on its own, relying instead on a customer to reach out to identify anomalies the customer had observed;
- Microsoft failed to maintain security controls that other cloud providers already use;
- Microsoft's failed to detect a compromise of an employee's laptop from a recently acquired company prior to allowing it to connect to its corporate network in 2021;
- Microsoft's failed to correct its inaccurate public statements about the incident for months and months. It took the company almost six months to fix a September 2023 blog post, and it did only after the CSRB constantly bombarded the company about a fix, and was ready to publish its report;
- Microsoft's security culture is almost non-existent and the company doesn't seem to prioritize security practices;
- The CSRB—using Google TAG attribution—linked an entity inside Storm-0558 group to the Google 2009 and the RSA 2011 hacks.
EU election security guidance: The EU has published guidance for online platforms on how to deal with election security risks ahead of the upcoming European Parliament elections in June. The EU has ordered large online platforms to cooperate with local authorities, mitigate generative AI threats, and label political advertising. The guidance applies to platforms that have more than 45 million monthly active users in the EU. This includes Google, Meta, Twitter, TikTok, LinkedIn, and others.
Poland's spyware investigation: Poland has launched a formal investigation into the previous government's use of the Pegasus spyware. A parliamentary inquiry is underway, and officials don't rule out criminal charges against the former government. The former government has been accused of using Pegasus to spy on opposition leaders, journalists, and prosecutors. Officials plan to notify all former victims. Under Polish law, victims could seek financial compensation. [Additional coverage in The Guardian]
Russia's crypto dependency: A new report shows how cryptocurrency—and Tether specifically—has become Russia's new avenue of evading international sanctions and fueling its war machine. [Additional coverage in the WSJ]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Resourcely co-founder and CEO Travis McPeak about how the DevOps ecosystem has evolved and ushered the need for DevSecOps and how the company provides and manages its secure-by-default templates.

Cybercrime and threat intel
Tornado Cash case: Dutch prosecutors are seeking a 64-month prison sentence for one of the developers of the Tornado Cash platform. Officials say Alexey Pertsev worked with two other Russian nationals to develop and operate Tornado Cash. Criminal organizations and cybercrime groups abused the platform to launder more than $1.2 billion worth of cryptocurrency. Pertsev was arrested in August 2022, days after the US sanctioned the Tornado Cash platform. He was formally charged last month.
Abdilo case: David Kee Crees, a hacker also known as Abdilo, has been extradited to the US. His trial is set to start in August.
Russian carders detained: Russian authorities have arrested six members of a web skimmer gang. Officials claim the group planted malware on online stores and collected payment card details from users. The group is believed to have stolen and sold 160,000 payment card details.
XZ incident: We published a summary of the XZ backdoor incident on Monday, but since then, new interesting research has surfaced. This includes an analysis of the XZ shell script and a timeline of the entire attack from Russ Cox, the tech lead at Google's Go programming language.
ASR on remote access tools: Cisco Talos has published a report on steps companies can take to reduce the attack surface and harden networks against remote access tools, often used by threat actors for remote access and data exfiltration. Cisco's advice is to pick one tool and design detection strategies for the other tools.
Google-based malvertising: Both AhnLab and Huntress have put out reports on how threat actors are leveraging Google's advertising platform for malware delivery.
Bignosa dox: Security firm Check Point says that a threat actor known as Bignosa is actually a young Kenyan man named Nosakhare Godson. The threat actor has been active for years and recently launched malspam campaigns delivering the Agent Tesla infostealer to American and Australian companies.
Threat/trend reports: Check Point, Fastly, and ScamSniffer have recently published reports covering infosec industry threats and trends.
Malware technical reports
Nokoyawa ransomware: The DFIR Report team has published an analysis of a recent malware infection that began with a malicious OneNote file that delivered IcedID and ended up with a Nokoyawa ransomware attack.
Pegasus spyware: The iVerify team has published an analysis of the infamous Pegasus spyware. The team will present more at this year's Black Hat Asia security conference, set to take place later this month.
Sponsor Section
Setting up infrastructure is complex, and improper configuration is a bane to developers, security teams, and DevOps/platform teams everywhere.
❌ Wasted development time
😢 Platform teams stuck in ops mode, support developers
🔓 Unnecessary incidents
See why your team is wasting thousands of hours and millions of dollars, and how Resourcely can help you avoid misconfiguration.
APTs, cyber-espionage, and info-ops
Earth Freybug: Trend Micro has discovered a new APT group named Earth Freybug. Researchers say the group has been active since 2012, and its main focus has been on espionage and financially-motivated attacks. The group's main tool is a novel piece of malware named UNAPIMON. Trend Micro believes Earth Freybug might be a subset of the larger APT31 Chinese cyber-espionage group.
"This article provides an in-depth look into two techniques used by Earth Freybug actors: dynamic-link library (DLL) hijacking and application programming interface (API) unhooking to prevent child processes from being monitored via a new malware we’ve discovered and dubbed UNAPIMON."
Indian disinformation on YouTube: Researchers from Access Now and Global Witness say that YouTube is failing to detect disinformation in India on the platform.
Vulnerabilities, security research, and bug bounty
Android Security Bulletin: Android security updates for April 2024 are out. No zero-days, and there are no security issues addressed in Google Play system updates (Project Mainline) this month.
Imperva firewall bypass: A security researcher has discovered a vulnerability (CVE-2023-50969) in Imperva SecureSphere firewalls. The vulnerability allows attackers to manipulate HTTP headers and slip malicious payloads past the firewall. Approximately 400 Imperva SecureSphere firewalls are currently exposed online. Imperva released a fix at the end of February.
Kemp LoadMaster bug: Tenable says it found another way to exploit CVE-2024–1212, an unauthenticated command injection in the Progress Kemp LoadMaster.
DOMPurify bypass: Security researchers RyotaK and Slonser have found a bypass in DOMPurify, a library for sanitizing web documents such as HTML, XML, SVG, and others.
Samsung bug bounty: Samsung recently secured an exposed Jenkins servers based on a security researcher's report.
IBIS hotels keypad leak: Pentagrid researchers have found a vulnerability in the automatic check-in terminals used by the IBIS budget hotel chain. The vulnerability can be exploited by typing a series of dashes (------) in the terminal's booking ID field. This exposes the names and room keypad codes for other hotel guests. Pentagrid reported the issue to the hotel chain in January, and the terminals have been patched (or so they say).
Infosec industry
New tool—xzbot: Google Cloud vulnerability researcher Anthony Weems has published xzbot, a proof-of-concept exploit for the XZ Utils backdoor.
New tool—XZ.fail: Security firm Binarly has released XZ.fail, an online scanner that can detect if Linux binaries (ELFs) are vulnerable to the XZ backdoor.
NetNoiseCon: GreyNoise is launching its own security conference named NetNoiseCon.
"NetNoiseCon is a livestream conference viewable on the GreyNoise YouTube channel on April 19th, starting at 12pm ET / 9am PT."
Risky Business Podcasts
Listen to Resourcely CEO Travis McPeak talk with Risky Business Snake Oilers host Patrick Gray about the company's automagic Terraform cloud-provisioning technology.





