Risky Biz News: Explosive whistleblower report exposes Twitter's shoddy security
In other news: Oracle sued in the US in privacy case; two new air-gap exfiltration channels disclosed; and Windows Dirty Pipe vulnerability.
This newsletter is brought to you by Airlock Digital, Proofpoint, RunZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
If you spent your Tuesday under a rock, then you probably missed one of the biggest tech stories of the year as one of the most respected white-hat hackers in the cybersecurity industry came forward to disclose a series of cybersecurity and leadership lapses taking place inside Twitter.
In an explosive whistleblower report filed with the US government, Peiter "Mudge" Zatko, who served as Twitter's head of security between November 2020 and January 2022, painted a grim picture of their former employer, describing them as negligent and a national security risk.
The accusations have been extensively covered and put into context in reports by CNN and the Washington Post, who led reporting on this story, but you can also read them yourself via Zatko's redacted 84-page whistleblower letter filed with the US Congress last month.
If time bites at your heels, we summarized Zatko's main accusations in the points below (Still a long list, we know. It's a long report):
- Twitter has no access control system in place, and most engineers can access the site's production environment and user data at any time.
- Twitter doesn't keep logs of what engineers are changing in the production environment or who is accessing what.
- About half of Twitter's 500,000 servers run outdated software that does not support basic security features such as data encryption or does not receive regular security updates.
- Twitter is failing to properly delete user data when users request their data be deleted, mainly because data is spread across different internal systems and is hard to keep track of.
- Twitter lacks sufficient redundancies and procedures to recover from data center crashes, putting crucial user data at risk.
- Twitter was forced by the Indian government to hire government agents in its staff, who then had access to Twitter's vast amounts of user data.
- Twitter's CEO Parag Agrawal was willing to honor Russia's request to censor Twitter content according to the Kremlin's demands and views.
- Twitter execs prioritized user growth over security, as they stood to earn bonuses of as much as $10 million. This led to Twitter execs not being interested in measuring the prevalence of bot accounts on the platform because revealing such figures would most likely hurt its stocks.
- A Twitter executive actually tried to disable ROPO, a Twitter security feature that would put accounts into read-only mode until they went through a phone number verification process, a security feature that was added to fight spam bots.
- Twitter's leadership went behind Zatko's back to scrub a report compiled about government propaganda and misinformation campaigns active on the site that was compiled by a third-party consulting firm (identified by WaPo as Alethea Group) at Zatko's request.
- Twitter was never in compliance with an FTC 2010 order and lied to regulators about its security practices and ability to protect user data.
- Zatko said he was also told to cherry-pick and misrepresent data to create a false perception of progress on cybersecurity issues when presenting reports to the board.
- Twitter management tried to hide or misrepresent Zatko's reports from other board members, effectively committing fraud.
- Zatko said he was fired after bringing the security/fraud issues to Twitter's management and complaining to its Compliance Officer.
In the aftermath of today's reporting, Zatko's revelations have been widely accepted and taken at face value by a vast majority of people, primarily for two reasons. First, Zatko has a decades-long reputation as a white-hat hacker and previously worked with the US government on many cybersecurity projects.
This is Peiter "Mudge" Zatko - as in the l0pht, DARPA, CoDC infosec pro.
— Arbitrary Capital (@arbutuscapital) 1:58 PM ∙ Aug 23, 2022
Twitter says Mudge is “disgruntled employee,” who was fired for poor performance/leadership. But there’s probably no security exec with more ethics, more credibility than Mudge. He worked for gov for years, his wife is former NSA. I wrote about them here:
— Kim Zetter (@KimZetter) 11:52 AM ∙ Aug 23, 2022
Second, we all have Twitter accounts, and we've seen first-hand how the platform has declined in its moderation quality and has failed in recent months to address dis/misinformation campaigns, bot accounts, and abuse—a trend that at first glance appears to have taken off after Agrawal was named CEO last November.
For starters, Twitter's once-vaunted Transparency Center, where the company would name-and-shame state-backed bot networks and influence operations, has not published any new report since December 2021, three days after Agrawal's appointment as CEO.
But can you also recognize the following text?
"After reviewing the available information, we want to let you know [@username] hasn't broken our safety policies."
Oh, but yes, it is the standard reply that Twitter sends you after you report an account for policy violations. Death threats. Calls for genocide. Obvious scams. Doesn't matter. None of your reports will ever lead to an account being suspended on the platform these days.
Kamala Harris, the Vice-President of the United States, found out this earlier this year after thousands of accounts sending her death threats and inappropriate language never got suspended. As CBS News reported in June, this lackadaisical approach to user moderation appears to have started this year in what obviously looks like a new and more relaxed approach inside Twitter's once strict moderation teams.
Policies change at companies when new CEOs take over all the time. It's not something new, and old employees will get their feathers ruffled when this happens. If you read Zatko's complaint close enough, it does seem to point the finger at Twitter's new CEO for a vast majority of the platform's problems, and Zatko himself confirms that he and Agrawal had a strained working relationship, which started before Agrawal was named CEO when he first highlighted issues in Twitter's server and engineering departments. We quote from the report:
Perhaps Agrawal's defensiveness should not have been surprising—as a senior engineer later promoted to then Chief Technology officer for years, Twitter's problems had developed under Agrawal's watch.
And there is obviously still some bad blood between the two. Responding to Zatko's whistleblower report today, Agrawal effectively called Zatko a disgruntled former employee who was just a bad leader.
NEW: First time Twitter CEO @paraga weighs in on whistleblower story.
— Donie O'Sullivan (@donie) 1:28 PM ∙ Aug 23, 2022
Sending this message to staff this morning.
Obviously, happy employees don't file whistleblower complaints with the US government. There is something going on at Twitter.
If you believe Zatko, Agrawal is a bad CEO that has lied to regulators, lied to his own board, failed to address bots, failed to address IT security issues, allowed foreign intelligence to penetrate the platform, and is cozying up or cracking in the face of oppressive regimes.
If you believe Agrawal and Twitter, Zatko was just bad as his job and is now trying to blame Twitter for his failures in a job he had for years before he was let go.
And there's something to be said in Twitter's defense as well. As Casey Newton points out, Twitter has been addressing many of the IT security issues that Zatko mentioned in his report, many of which have already been fixed.
Furthermore, Newton and many others have found it odd that despite accusing the company and its CEO of committing fraud and being a national security risk, Zatko's whistleblowing report focuses a long intro to how Twitter and Agrawal have lied to Elon Musk about the number of spam accounts currently active on the platform. That's a weird way to start your whistleblower report. I don't know. Maybe start it with the fact that you have Indian intelligence agents as employees with direct access to user data first next time.
With Musk trying to weasel his way out of a $44 billion Twitter acquisition deal, there's the case to be made that this whistleblower report and its obsession with spam bot statistics is more geared toward helping Musk's Twitter lawsuit than it is about fixing Twitter.
Anyway, grab your popcorn! We're gonna have an entertaining fall in tech this year.
Breaches and hacks
DESGFA attack: Greece's national natural gas operator DESFA confirmed this weekend that it was hit by a cyberattack but said it would not negotiate with the people behind the incident, identified as the RagnarLocker ransomware group. [More in The Record]
CDCR breach: The California Department of Corrections and Rehabilitation (CDCR) issued a breach notification this week in regards to an incident from earlier this year. [Additional coverage in DataBreaches.net]
The breach potentially included medical information on everyone who was tested for COVID-19 by the department from June 2020 through January 2022, including staff, visitors, and others. It did not include COVID testing information for the incarcerated population. The breach also potentially included mental health information for the incarcerated population in the Mental Health Services Delivery System going as far back as 2008.
General tech and privacy
Oracle sued in the US: A group of privacy experts has filed a class-action lawsuit against Oracle in a California court, accusing the company of amassing "detailed dossiers on 5 billion people" without their consent. The group says Oracle has been using the data to power its advertising division, which generates around $42.4 billion in annual revenue. Since there is no privacy legislation in the US, the lawsuit claims that Oracle has violated federal, constitutional, tort, and state laws. [Additional coverage by Natasha Lomas in TechCrunch]
Chrome stats: In its quarterly report for Q2 2022, the Chrome security team said it saw "a 13% quarter-over-quarter growth in the number of Chrome users who opted in to Enhanced Protection." In addition, the Chrome team also said that its new extension telemetry signals have also proven useful and helped the Chrome Web Store team to catch and quickly take down a malware campaign.
Carbon Black errors: System administrators surely didn't love Carbon Black EDRs on Tuesday, especially after it was discovered that a bug was crashing their Windows devices with BSOD errors. (via @TGesches)
Government, politics, and policy
Poland and Ukraine cyber treaty: The governments of Poland and Ukraine signed a memorandum on cooperation in the field of cybersecurity defense, the two countries announced on Monday. Per the new treaty, Poland and Ukraine will exchange best practices in countering cyberattacks, participate in cybersecurity conferences, conduct joint training, share information about cyber attacks, and fight online disinformation.
Cybercrime and threat intel
Russian hacktivism: Several Russian "hacktivist" groups have announced coordinated DDoS attacks against Moldavian targets. The campaign appears to have been triggered by the visit of a Moldavian government official to Bucha, the site of one of Russia's genocides in Ukraine. (h/t @SwitHak and @CyberKnow)
At this stage sounds like #killnet will be targeting #Moldova for several days.
— CyberKnow (@Cyberknow20) 11:25 AM ∙ Aug 23, 2022
#CyberSecurity #infosec #RussiaUkraineWar #UkraineRussiaWar
Ukrainian hacktivism: In the meantime, Ukraine's IT Army is also carrying out its own operations, and this week they appear to be targeting Russian money transfer services. And then this:
🚨🚨🚨
— CyberKnow (@Cyberknow20) 11:49 AM ∙ Aug 23, 2022
A newly launched pro-ukraine hacktivist group #2402team has leaked an alleged 550gb of #Russian banking data.
#CyberSecurity #infosec #RussiaUkraineWar #UkraineRussiaWar #Ukraine
SaaS platforms abused for phishing and malware ops: Researchers from Palo Alto Network's Unit42 cybersecurity division said in a report on Tuesday that they'd seen a spike in the abuse of legitimate SaaS platforms as a medium to host phishing sites and infrastructure. So far, researchers have seen file-sharing, form builders, website builders, note taking, collaboration, design, prototyping, and personal branding sites abused for attacks.
Donut Leaks: A new data extortion group named 'Donut Leaks' is linked to recent cyberattacks, including those on Greek natural gas company DESFA, UK architectural firm Sheppard Robson, and multinational construction company Sando. [Additonal coverage in BleepingComputer]
Backdoored counterfeit smartphones: Dr.Web researchers said they identified counterfeit smartphones of popular brands that come with pre-installed malware configured to abuse the WhatsApp and WhatsApp Business apps, using them to download and install additional payloads on the vulnerable devices. At least four smartphone models were found to contain this particular malware, including clones of P48pro, Radmi Note, Note30u, and Mate40.
Sponsor section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
Malware technical reports
XCSSET: Threat actors behind the XCSSET malware have updated their code from Python v2 to v3, according to a recent SentinelLabs report.
Escanor: Resecurity published a report this week on Escanor (also known as Esca RAT), a new RAT (remote access trojan) advertised on the dark web and Telegram channels. The RAT is available in both Windows and Android versions.
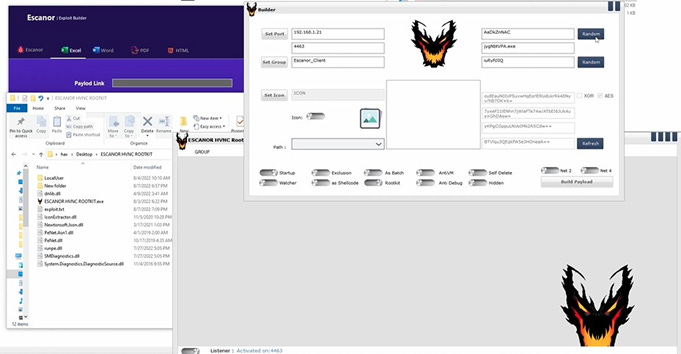
APTs and cyber-espionage
Charming Kitten has a new tool: Google TAG published a report on Tuesday on a new tool used by the Iran-based Charming Kitten APT and named HYPERSCRAPE. Google says Charming Kitten operators can use this tool together with previously acquired credentials to automate the process of retrieving emails from its victims' Gmail, Yahoo, and Outlook email accounts.
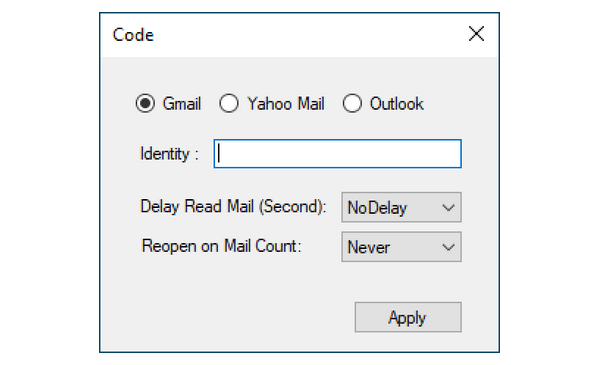
It spoofs the user agent to look like an outdated browser, which enables the basic HTML view in Gmail. Once logged in, the tool changes the account's language settings to English and iterates through the contents of the mailbox, individually downloading messages as .eml files and marking them unread. After the program has finished downloading the inbox, it reverts the language back to its original settings and deletes any security emails from Google.
Unidentified APT operation: Fortinet has published details about a suspected APT operation targeting Southeast Asian countries and which uses the Chinoxy and PivNoxy malware for its attacks.
Vulnerabilities and bug bounty
Windows Dirty Pipe: Kunlun Lab security researcher k0shl has published details on Windows Dirty Pipe, an elevation of privilege vulnerability the researcher used during the Tianfu Cup 2021 hacking contest. Microsoft patched the issue, tracked as CVE-2022-22715, back in February. A PoC is also available on GitHub.
We @KunlunLab will share the vulnerability and exploitation I used in the TianfuCup2021 for escaping Adobe Reader sandbox on #BCS2022, this vulnerability existed in Named Pipe File System for nearly 10 years since AppContainer was born. We called it "Windows Dirty Pipe".(1/2)
— k0shl (@KeyZ3r0) 3:30 AM ∙ Aug 15, 2022
Pie on CrowdStrike's face: Swiss cybersecurity consulting firm modzero AG has accused CrowdStrike of trying to play down a vulnerability in its Falcon Sensor product and then secretly patching the issue while telling the researchers the exploit didn't work in their tests. Drama. There's lots of drama in that blog post if you like that sort of thing.
"Useless" path traversal in Zyxel routers: Well, not that useless, but a good write-up on CVE-2022-2030.
Jenkins plugins: Security updates are available for three Jenkins plugins.
Firefox 104: Mozilla released Firefox 104, which also comes with its regular security fixes.
Intel PPAM attack: At the Black Hat security conference earlier this month, Binarly researchers detailed a new attack that can disable the Intel Platform Properties Assessment Module (PPAM), a security component that is used to verify the validity of code running inside Intel BIOS/UEFI firmware.
WMI attack: The same Binarly team also published a second piece of research, which was also presented at the same conference, on a new method to disable the Windows Management Instrumentation (WMI), a crucial Windows service meant to collect data from hosts and send it to central servers, a system often used for and by security solutions.
Since the WMI service doesn't have any protection mechanisms, WMI event delivery can easily be disabled by attackers without triggering any security alert thus breaking the defense mechanism that relies on such telemetry. All the attacks presented in the Black Hat talk have been carried out from user-land, most of them following the one-bit change attack template.
ETHERLED: Researchers from the Ben-Gurion University of the Negev in Israel have discovered a new method to exfiltrate data from air-gapped systems using the activity and status LEDs on modern network cards. Named ETHERLED, the attacker controls the LED blinking phases to take stolen data and send it out as Morse code to a nearby observer, such as a compromised security camera or an insider with a video recording device. Depending on the size of the stolen data, the exfiltration can take from 2 seconds (for passwords) to minutes (for 1KB text files).
GAIROSCOPE: In addition, the same Ben-Gurion researcher also published a second paper, this one on GAIROSCOPE, another air-gap exfiltration attack. GAIROSCOPE uses malware planted on an air-gapped system to send out ultrasonic sound waves containing encoded stolen data to nearby gyroscopes, such as those typically found in modern smartphones. See the demo video below:
Infosec industry
Kaspersky Russia employees told to resign: A Motherboard report alleges that Russian employees of security firm Kaspersky were denied requests for relocation outside Russia following the country's invasion of Ukraine; and that some were also told to resign following their request.
A current Kaspersky employee, who spoke to Motherboard on condition of anonymity as he was not allowed to speak to the press, confirmed that the company asked employees who wanted to live and work somewhere else to resign, and some of them decided to resign.
Windows system calls for hunters: Marco Ramilli, founder and CEO of Yoroi Security, has published a list of Windows 10 system calls that could be abused by attackers and could hide potential vulnerabilities due to their complexity. Ramilli argues that defenders should keep an eye on these calls in their networks, as they could reveal suspicious or even malicious activity.
New tool—Sandman: Offensive security researcher Ido Veltzman published this week a new project named Sandman, a backdoor meant to work on hardened networks during red team engagements and which uses the NTP protocol to run arbitrary code downloaded from third-party servers on infected hosts.
Had a lot of fun working with @ORCx41 on this project: A backdoor specially made for hardened networks which leverages NTP - A usually overlooked protocol - to get and run shellcode.
— Ido Veltzman (@Idov31) 11:15 AM ∙ Aug 21, 2022
github.com/Idov31/Sandman
#infosec #CyberSecurity




