Risky Biz News: EU warns Temu to respect consumer protection laws
In other news: iPhones get a secret security feature; Palo Alto Networks warns of mysterious RCE; 2,700+ US schools and libraries apply for cybersecurity funds.

This newsletter is brought to you by Kroll. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The European Union has told Chinese e-commerce giant Temu to follow consumer protection laws or face major fines.
The EU says Temu uses fake discounts, pressure selling tactics, forced gamification, and fake reviews to trick users into buying products from its online marketplace.
The company also allegedly displays incomplete or incorrect information about consumers' rights to return goods and receive their refund backs, and also hides contact details so customers cannot file complaints.
The EU's Consumer Protection Cooperation (CPC) Network has also notified Temu that it is in violation of the EU's upcoming General Product Safety Regulation (GPSR).
Temu will have to establish an EU economic operator that will be responsible for taking down products deemed harmful or dangerous to human health.
The CPC's warning comes a week after the EU opened a formal investigation into Temu's business practices under the Digital Services Act (DSA). That investigation will look into the sale of illegal products, the potentially addictive design of the service, the systems used to recommend purchases to users, and data access for researchers.
Both EU legal actions were to be expected. EU consumer protection groups have recently started warning users that the platform was rife with misleading "dark pattern" designs and scams.
It is unclear how Temu will react to the investigations.
The Chinese company has taken the EU e-commerce by storm over the past year with a massive social media marketing campaign promoting what the EU now claims are "fake discounts" and "fake reviews." For both intent and purpose, it appears that Temu was well aware of what it was doing.
The company may stop its practices, or not. Temu's EU strategy and its willingness to play nice in the EU is somewhat of an open question.
In addition, although not under any official investigation, there are also concerns about the company's suspiciously broad data collection practices and its potential links to the Chinese Communist Party. All of this sounds like another TikTok drama in the making.
From a BEUC report linked above:
"Temu is evidently capturing markets through its ultra low prices while the cost-of-living crisis continues to hit Europe. But it is doing so by sacrificing the safety of goods on offer and the things consumers in Europe either take for granted or deserve by law."
Breaches, hacks, and security incidents
Chinese hackers target Trump lawyer: The FBI has notified Donald Trump's lead attorney Todd Blanche that his phone was tapped by Chinese hackers. The hackers allegedly obtained voice and text messages, but none were related to President-elect Trump. The hack are the work of Salt Typhoon, a Chinese APT group that breached US telco wiretapping systems earlier this year. The Blanche hack is part of a larger series of hacks that targeted politicians across both US parties. [Additional coverage in ABC News]
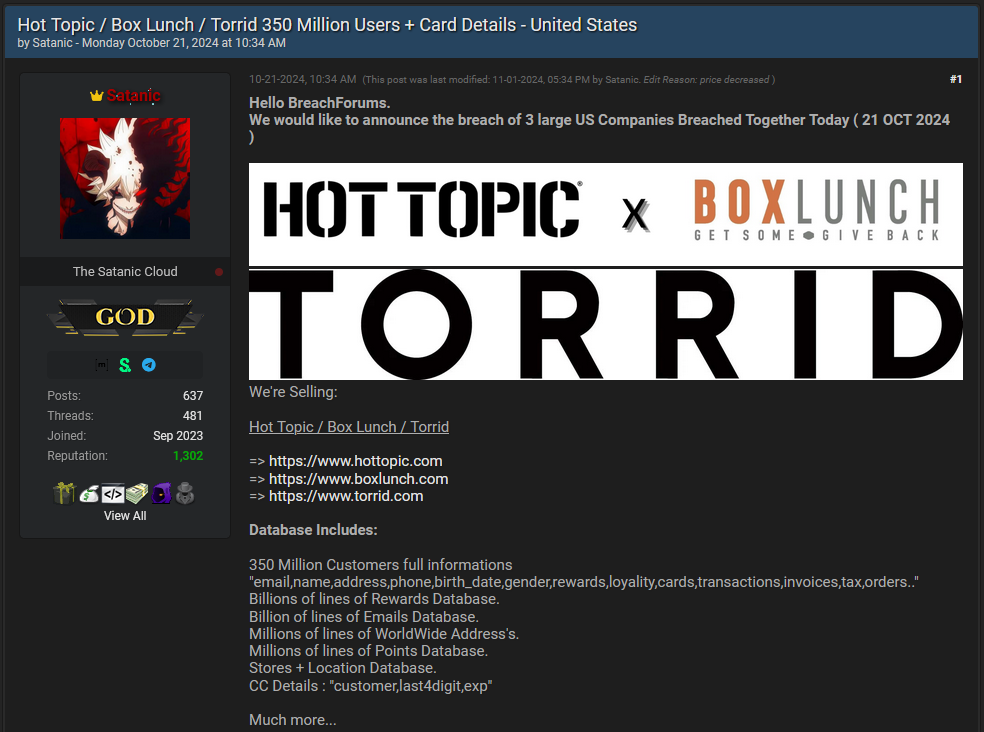
Hot Topic hack: A threat actor is selling the data of clothing store retail chain Hot Topic. The details of at least 54 million Hot Topic customers are being sold as part of a larger package of stolen data. The data was posted for sale at the end of October but was only recently confirmed to be authentic. The stolen data includes names, home addresses, past orders, and even the last four digits of payment cards. [Additional coverage in PCMag]
Halliburton cyberattack costs: US oil services company Halliburton has incurred $35 million in costs [PDF] related to an August cyberattack. Halliburton CEO Jeff Miller says the incident delayed billing and collections and caused lost or delayed revenue. A ransomware group named RansomHub took credit for the attack but never leaked any data from the company. It's unclear if Halliburton paid the ransom. [Additional coverage in CybersecurityDive]
Dutch police hack update: Dutch Police published an update on a state-sponsored breach that obtained the data of more than 62,000 of the country's police force. According to the new information, the hack took place via a pass-the-cookie attack that bypassed MFA protections.
DDoS attacks on South Korea: Pro-Kremlin hacktivist groups launched a massive wave of DDoS attacks against South Korean government websites at the end of last week. The attacks took place in the wake of South Korea's decision to send military observers to Ukraine after North Korean troops were deployed on the frontlines. South Korea's President's Office has urged government agencies and private businesses to boost their cybersecurity defenses.
DDoS attack blocks Israeli card payments: A DDoS attack has blocked credit card payments across Israel over the weekend. The incident targeted HYP, one of Israeli main financial clearing companies. HYP says it blocked the attack, but not before consumers were impacted by the downtime. [Additional coverage in the Times of Israel]
Tor spoofing attacks stopped: The Tor Project says it identified and shut down the source of an attack on Tor relays that had been taking place for over three weeks. The attacks used spoofed SYN packets to make it look like Tor relays were conducting unauthorized port scans. Some network operators detected the attacks and filed abuse complaints with the hosting providers of Tor relay servers. The Tor Project believes the attacker tried to get as many Tor relays on IP blocklists, hoping to disrupt Tor traffic. The Tor team says it worked with GreyNoise and InterSecLab to detect the origin and the attacks but did not provide other details.
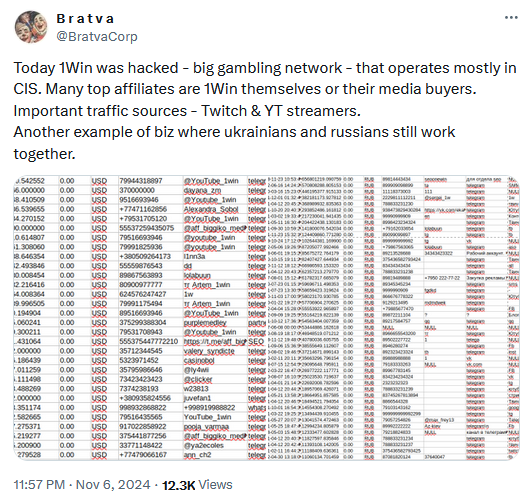
1win extortion: A threat actor has hacked Russian sports betting and gambling company 1win and is now extorting the company. The hacker allegedly used a wave of DDoS attacks to distract the company's security team and dump its user database. According to 1win's CEO, the hacker initially demanded a ransom of $1 million but increased the sum to $15 million after several failed negotiations.
General tech and privacy
Open Source AI drama: Tech companies, through the Open Source Initiative, are trying to redefine the meaning of "open source AI" to allow for secret training data and mechanisms.
Meta's regulation of political ads fraught with deficiencies: A study [PDF] conducted by France's VIGINUM agency has found that 60% of the political ads on Meta platforms across the EU break the company's guidelines regarding political advertising. In other words, the guidelines are there just for show.
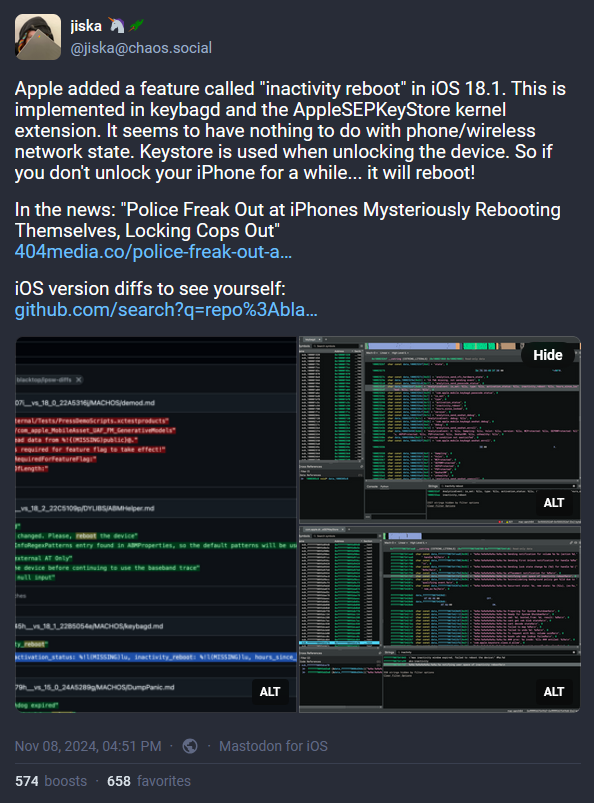
Secret iPhone reboot feature: Apple has added a secret feature that reboots iPhones that have not been unlocked for a long period of time. The reboots put devices into Before First Unlock, a state where the phone's data is harder to obtain. According to 404 Media, the feature was added to iOS version 18.1, released at the end of October. The feature was discovered by law enforcement after the iPhones of detained suspects were mysteriously rebooting while in custody. The reboots occurred even when the phone was in Airplane mode or inside Faraday boxes.
Government, politics, and policy
TSA cyber rules: The US Transportation Security Administration has proposed new cyber rules that would mandate pipeline and railroad operators to establish cyber risk programs. In addition, pipeline, railroad, and high-risk bus operators are required to report cybersecurity incidents to the TSA, to pass on along to CISA. The White House ordered the TSA to establish new cybersecurity rules in 2021, after the Colonial Pipeline ransomware attack.
DOD reduces cyber vacancy rate: The US Department of Defense has cut its civilian cyber vacancy rate this year to 16%, down from over 20% in 2023. Officials said the civilian cyber vacancy rate was double what they initially anticipated. The new hiring effort was part of a DOD cyber strategy unveiled in March last year. [Additional coverage in DefenseScoop]
DHS tells employees to use Teams after telco hack: The Department of Homeland Security has told employees in an internal memo to use Microsoft Teams to communicate whenever possible. The DHS' CIO has issued the new guidance in the aftermath of a Chinese hack of three major US telecommunications providers. The intrusion allowed the hackers to intercept phone calls and SMS messages. The DHS is the second US agency after the US Consumer Financial Protection Bureau to tell employees to stop using phones for work-related matters in the hack's aftermath. [Additional coverage in NextGov]
Schools & Libraries Cybersecurity Pilot: The FCC has received over 2,700 applications from schools and libraries to receive funding for cybersecurity expenses. The funding is provided through a cybersecurity pilot the FCC established in November of last year. The agency plans to provide up to $200 million in funding over three years. The applications have requested $3.7 billion in funding help, showing the program's extraordinary success.
NIST supply chain guide: The US NIST has published a guide for identifying, assessing, and mitigating cybersecurity risks throughout the supply chain. [h/t DataBreaches.net]
ENISA NIS2 guidance: The EU's cybersecurity agency, ENISA, has published technical guidance to help EU organizations implement the NIS2 cybersecurity risk-management framework.
Cambodia promises crackdown on cyber scam compounds: Cambodia's National Police director has ordered local police to crack down on online gambling and cyber scam compounds operating inside the country's border. General Su Thong says the government is committed to maintaining a good national image and ensuring the stable development of the tourism sector. Officials have announced the new crackdown after neighboring Asian countries accused Cambodia of allowing criminal syndicates to operate undisturbed, sometimes with the protection of local military and police forces. [Additional coverage in CC Times/English coverage in The Phnom Penh Post] [h/t CyberScamWatch]
Sponsor Section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with George Glass, Senior Vice-President for Kroll's Cyber Risk business. George covers the company's latest report, a Kimsuky attack on ConnectWise ScreenConnect devices with a new malware strain named ToddlerShark.

Arrests, cybercrime, and threat intel
BEC scammer gets long prison sentence: US authorities have sentenced a 33-year-old Nigerian man to ten years in prison for a BEC scam that targeted the real estate sector. Officials say the man was part of a group that stole almost $20 million from over 400 victims. The group compromised the email accounts of real estate agents, title companies, and real estate attorneys. Once inside, they monitored emails and stepped in to provide misleading account details and hijack customer payments.
Bitcoin Fog admin sentenced: A US judge has sentenced a Russian-Swedish national to 12 years and six months in prison for laundering cryptocurrency on the dark web. Roman Sterlingov operated the Bitcoin Fog service and laundered more than $400 million worth of Bitcoin between 2011 and 2021. During the trial, Sterlingov's lawyer attacked blockchain tracking company Chainalysis, which helped US law enforcement identify and arrest his client. He called the company's tools "junk science" and described Chainalysis as the "Theranos of blockchain analysis."
Cyber suspects detained in Nigeria: Nigeria's national police has detained 130 individuals suspected to have participated in cybercrime operations. The arrests included 17 Nigerians and 113 Chinese and Malay nationals. Officials did not provide any details about the nature of the group's activities. [Additional coverage in PUNCH]
Phisher detained in the Netherlands: Dutch Police have arrested a 33-year-old suspect for allegedly running phishing operators that collected payment card details.
Malicious Python library: The Socket Research Team uncovered a malicious Python package typosquatting the popular 'fabric' SSH library, silently exfiltrating AWS credentials from unsuspecting developers.
New npm malware: Ninety-eight malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
npm malware targets Roblox developers: Socket Security has discovered five malicious npm packages designed to infect Roblox developers with malware. The five packages mimicked the names of more legitimate libraries but deployed versions of the Skuld infostealer and Blank Grabber malware. The packages were spotted and reported by Socket Security. The company says they only garnered a few hundred downloads before being removed.
Skimmer season is here: Since the 2024 sales are coming, Sucuri looks over some of the recent credit card skimmers spotted in the wild this season.
Malware technical reports
Frag ransomware: A new ransomware gang named Frag is exploiting an RCE vulnerability in Veeam backup servers to breach corporate networks and deploy its file encrypter. The ransomware was first spotted in October and appears to be using tactics similar to the Akira and Fog groups. Both groups also previously attacked Veeam backup servers with the same vulnerability.
Remcos RAT: Fortinet's security team has published a report on a malspam campaign delivering Remcos RAT via malicious Excel files.
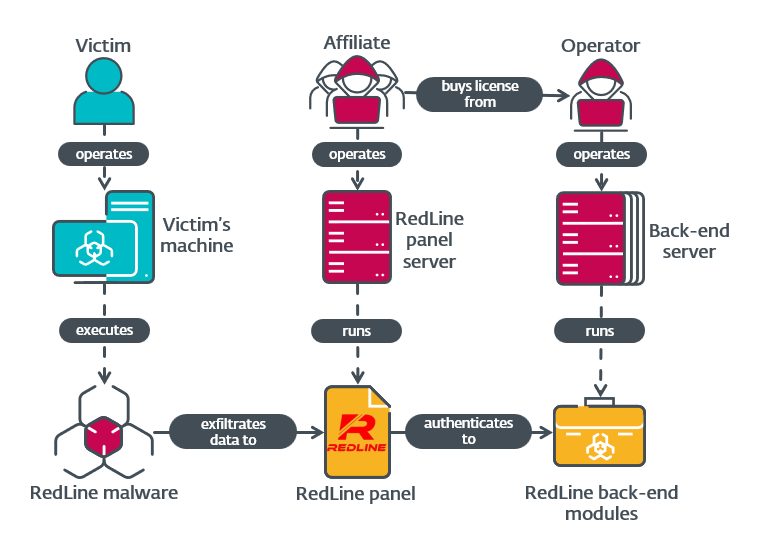
RedLine: ESET has published a technical write-up on RedLine, an infostealer whose infrastructure was recently taken down by law enforcement agencies.
Sponsor Section
Kroll has investigated many different tactics that threat actors use to steal consumer data on e-commerce sites. These types of attacks can be especially damaging for organizations that are responsible for storing customers' personal and financial information that is collected during transactions. Read more about Kroll's prevention tips and security best practices.
APTs, cyber-espionage, and info-ops
MSS head profile: The WSJ has published a profile on Chen Yixin, the head of China's Ministry of State Security, the agency behind some of China's cyber-espionage efforts—including the recent Salt Typhoon US telco hacks.
Earth Estries: Trend Micro has published a technical report on Earth Estries, an APT group it first discovered last year.
"Our analysis of Earth Estries' persistent TTPs in prolonged cyber operations reveals a sophisticated and adaptable threat actor that employs various tools and backdoors, demonstrating not only technical capabilities, but also a strategic approach to maintaining access and control within compromised environments."
CloudComputating's QSC: Kaspersky has published a report on QSC, a new malware framework used by the CloudComputating group.
"Our telemetry data indicates that the group has initiated limited yet targeted campaigns using QSC framework and focusing specifically on the telecommunication sector. Additionally, in response to detection of the Quarian backdoor, the group has begun deploying a protected version. The usage of the QSC framework suggests a strategic change in their toolkit, serving as a secondary means to maintain access within compromised networks. This evolution underscores the group's adaptability and emphasizes the importance of continuous monitoring of its future activities."
GoblinRAT: Rostelecom's security team has discovered a novel Linux malware on the servers of a Russian IT service provider. The company described the new GoblinRAT malware as one of "the most stealthy attacks" it has ever investigated. Artifacts suggest the malware may have been developed as early as 2020. Rostelecom has yet to attribute the malware to any known group but believes the malware may be the work of a state-sponsored group.
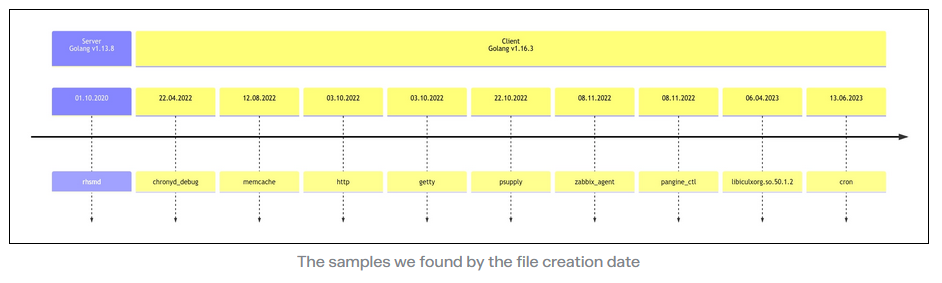
Vulnerabilities, security research, and bug bounty
PAN-OS attacks: Palo Alto Networks has told customers to restrict access to firewalls after rumors of a supposed exploit in their management interfaces. The company says it's investigating the claims but has not yet identified the vulnerability. The security vendor has asked customers to restrict access to the firewall management panel only from internal IP addresses and block logins from the internet.
Exploits in EOL D-Link NASes: Taiwanese networking equipment vendor D-Link has told customers to replace old NAS devices that have reached End-of-Life and are vulnerable to a newly discovered vulnerability. Details and proof-of-concept code were published online on Friday. D-Link has not released patches because many of the affected devices had reached EoL years ago.
Veeam security update: Backup tech provider Veeam has released a fix for an auth bypass tracked as CVE-2024-40715.
New macOS sandbox escapes: Security researcher Mickey Jin has discovered over ten vulnerabilities in the macOS operating system. The vulnerabilities exploit the XPC service to escape the macOS app sandbox. The XPC service is a mechanism for basic interprocess communication, similar to the Windows IPC service. Jin says five more sandbox escapes are still in Apple's patching queue.
More macOS vulnerabilities: Kandji researchers have published part one of three about vulnerabilities they discovered in the macOS diskarbitrationd and storagekitd system daemons. The vulnerabilities include sandbox escapes, local privilege escalations, and TCC bypasses.
Microsoft Bookings facilitates impersonation: Security firm Cyberis is warning companies to disable the Shared Bookings option in their Microsoft 365 accounts. The feature allows employees to create and manage appointments inside a Microsoft 365 environment. Cyberis says the feature is insecure because it creates new email accounts whenever a booking is made for non-existing users. A threat actor who compromised a company's low-level employee can abuse it to register new accounts inside a company's email server. This includes registering accounts that mimic existing employees and executives, re-registering accounts of former employees, or hijacking special addresses such as admin, contact, or webmaster.
GigaDevice vulnerabilities: Positive Technologies have found vulnerabilities that can be used to extract unencrypted firmware from GigaDevice G32 microcontrollers.
Mazda vulnerabilities: ZDI researchers have found six vulnerabilities that can be exploited to take over the infotainment system of Mazda vehicles produced between 2014 and 2021. The bugs require physical access to plug into a USB drive into the car dashboard. ZDI says the vendor has not patched the reported vulnerabilities.
Infosec industry
New tool—Hyperlight: Microsoft's Azure team has open-sourced Hyperlight, an open-source Rust library you can use to execute small, embedded functions using hypervisor-based protection for each function call.
Threat/trend reports: Cockroach Labs and CyFirma have recently published reports and summaries covering various infosec trends and industry threats.
SANS CloudSecNext 2024 videos: Talks from the SANS CloudSecNext 2024 security conference, which took place earlier in September, are available on YouTube.
Hexacon 2024 videos: Talks from the Hexacon 2024 security conference, which took place earlier this month, are available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss what the Russian state gains and loses from hosting a ransomware ecosystem.
In this podcast, Tom Uren and Patrick Gray talk about the Snowflake hack after the person allegedly responsible was arrested in Canada. Telegram is involved at all sorts of levels and Tom wonders if this crime would have occurred if Telegram didn't exist.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!




