Risky Biz News: EU data supervisor sues the EU and Europol for skirting data protection rules
In other news: Ask.fm user data pops up on hacking forum; new Metador APT; and new Windows 11 release comes with new security features.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The European Data Protection Supervisor (EDPS)—an EU-independent supervisory authority that monitors European institutions and bodies to see if they respect citizens' rights to privacy and data protection rules—has filed a lawsuit [PDF] with the European Court of Justice against the European Union and Europol.
Earlier this year, in January, the EDPS published the results of a three-year investigation and said that it found that Europol, the law enforcement agency of the European Union (EU), had secretly collected large troves of personal information on EU citizens dating back years, even if those persons had not committed any crimes or were under any investigation.
The EDPS used its regulatory powers to order Europol to sift through its database and delete any information on EU citizens that had not committed any crimes over the past six months. It ordered Europol to scrub its database by January 2023.
But in its lawsuit filed this week, the EDPS said that EU lawmakers went behind its back and passed new legislation in June (articles 74a and 74b) that allowed Europol to retroactively keep all its previously collected information.
In a statement published in June, the EDPS said it had "strong doubts as to the legality of this retroactive authorization."
Now, the EDPS says that this new development actively subverts its independence and authority and wants the court to invalidate the new amendments and stay its decision.
EDPS takes legal action @EUCourtPress as new @Europol Regulation puts rule of law and EDPS independence under threat - read our Press Release europa.eu/!hG6wjF
— EDPS (@EU_EDPS) 8:07 AM ∙ Sep 22, 2022
This EDPS investigation (and the current lawsuit) is a highly controversial topic among law enforcement officials. In an official response in January, Europol said that deleting this data will impact its "ability to analyze complex and large datasets at the request of EU law enforcement," which will hinder the EU's ability to detect and respond to many threats, such as terrorism, cybercrime, international drugs trafficking, child abuse, and others, many of which involve trans-national investigations at a very large scale.
In honesty, this is one of those situations where both parties are right at the same time. You can't fight crime in the XXI century without some serious ML and data analysis, but you also can't leave a giant database of PII data without any safeguards from institutional abuse. Sure, it's Europol. We're not talking about China or Russia, so the possibility of abuse is low. But it's also not zero, as there's always that rogue insider in every government agency.
Breaches and hacks
Ask.fm 2020 breach: Earlier this week, an individual named "Data" began advertising the data of 350 million Ask.fm users on an underground cybercrime forum. Data told DataBreaches.net that he reached out to Ask.fm in 2020 about the breach but was ignored. The company appears to have never publicly disclosed the incident.
Optus data breach: Optus, the second largest telecommunications provider in Australia, said it was dealing with a cyberattack. In a message posted on its website, the company said it is still investigating the incident, but it believes that a threat actor might have viewed the personal data of its customers. Optus didn't say how many users were impacted by this incident but said it's already working with authorities on the case.
Information which may have been exposed includes customers' names, dates of birth, phone numbers, email addresses, and, for a subset of customers, addresses, ID document numbers such as driver's licence or passport numbers. Payment detail and account passwords have not been compromised.
Russian conscription leak: An unknown threat actor released on Thursday a list that claims to contain the names and details of Russian citizens drafted into the Russian Army following President Putin's latest decision to mobile more troops. The list's origin and authenticity have yet to be verified, but several individuals have confirmed that at least some of the people listed in the list have been drafted over the past two days.
@RichardHannay17 @campuscodi They still have quite a lot to capture, most of the Donetsk oblast and a huge city.
— Seth 🇬🇧 (@dogageshafts) 1:58 PM ∙ Sep 22, 2022
General tech and privacy
Denmark rules Google Analytics illegal: The Danish Data Protection Agency ruled this week that the use of Google Analytics inside the country is not compliant with the GDPR. The agency told local companies to either adjust the tool for increased privacy (through the use of reverse proxies, see guide here) or stop using it. Denmark now becomes the fourth EU member to rule Google Analytics illegal after Austria, France, and Italy.
Meta says it's not blocking Iranian users: Meta said on Thursday that it was not blocking Iranian phone numbers after earlier in the day, several Iranians said they couldn't connect to Meta's platforms using their Iranian numbers, even if they had been living abroad for years. Internet connectivity and access to western social media networks have been blocked for the past three days in Iran amidst widespread anti-government protests that have since turned violent.
I live in Germany but my whatsapp account with Iranian phone number is disconnected! thank you @Meta for your kind cooperation with Islamic Republic!!
— Reza Zamiri (@d3c0der) 7:37 AM ∙ Sep 22, 2022
#Mahsa_Amini #مهسا_امینی
New Windows 11 security baselines: With every new Windows release, there are always updates to security baseline docs. With Windows 11 22H2 rolling out, the security baselines are here too. New additions include the new Kernel Mode Hardware Enforced Stack Protection feature, enhanced phishing protections for Windows credentials, new security controls for working with printers, DoH hardening rules, new account lockout policies, and new credential theft protections.
Warning for storing plaintext passwords in text files: This Enhanced Phishing Protection that we mentioned above is actually pretty damn cool. While it can be useful in various ways, the feature can also warn users when it detects them trying to save plaintext passwords in text files. More on this feature in Microsoft's blog post.
SMB brute-force protection: But that's not the only good news for Windows 11 security nerds. In addition, Microsoft also announced a new security feature that will soon come to the OS and is currently ready for testing in Insider builds. Called the SMB authentication rate limiter, this new feature will block brute-force attacks against a Windows 11's SMB service, where attackers try a large number of user/password combos in an attempt to log into a Windows system via its SMB service.
With the release of Windows 11 Insider Preview Build 25206 Dev Channel today, the SMB server service now defaults to a 2-second default between each failed inbound NTLM authentication. This means if an attacker previously sent 300 brute force attempts per second from a client for 5 minutes (90,000 passwords), the same number of attempts would now take 50 hours at a minimum. The goal here is to make a machine a very unattractive target for attacking local credentials through SMB.
Twitter discloses password reset bug: Twitter said on Wednesday that they fixed a bug where users weren't logged out of all their devices when performing a voluntary password reset. The company said that in order to make sure this isn't being abused, they logged off all users they suspect might have been affected out of their active sessions.
Government, politics, and policy
NSA & CISA guide for OT/ICS networks: After issuing several guidelines and recommendations on various topics throughout the year, NSA and CISA officials have now turned their sights to OT/ICS networks.
Sponsor section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
Cybercrime and threat intel
Malicious npm package: Researchers from ReversingLabs discovered a malicious npm package disguised as the software tool Material Tailwind. When installed on a system, the package would download and run malicious Powershell code.
Zoho servers under attack: On Thursday, CISA said that it's now seeing attacks against Zoho ManageEngine servers that are exploiting CVE-2022-35405, a vulnerability the company patched back in June this year. A PoC and technical write-up for this one has been floating around the internet since early August, so no surprise here that it's now seeing active exploitation.
A new #KEV update for you❗
— US-CERT (@USCERT_gov) 8:06 PM ∙ Sep 22, 2022
Visit go.dhs.gov/Z3Q to see the latest #CVE that's been added to the Known Exploited Vulnerabilities Catalog. #VulnerabilityManagement #Cybersecurity #InfoSec
Magento vulnerability heavily exploited: On top of this Zoho bug, Magento e-commerce stores are also under heavy attacks as well. According to Sansec, CVE-2022-24086, a vulnerability in the Magento 2 CMS template engine, is being abused these days to drop remote access trojans on unpatched stores.
Credential stuffing is on a record pace: Authentication and authorization platform Auth0 published its yearly State of Secure Identity Report, and the company said that over the past year, credential stuffing attacks accounted for 34% of all authentication events on its platform.
Furthermore, the company also added that 58% of all customer apps also experienced login attempts with breached or leaked credentials, which Auth0 says perfectly illustrates the "widespread nature of these attacks."
Domain shadowing threat: Palo Alto's Unit42 security team has a report out on "domain shadowing," a technique where threat actor gains access to a domain's DNS records and use it to create subdomains without the owner's knowledge, where they host malicious content. The company said it's currently detecting 12,197 domains that have been "shadowed" and have subdomains hosting malware or other malicious content.
Cryptomining on Atlassian Confluence: Trend Micro has documented a recent cryptomining campaign that has targeted Atlassian Confluence servers through CVE-2022-26134, an RCE vulnerability previously abused by nation-state actors, ransomware gangs, hacktivists, other coin-miners, and various botnets.
FIN11 phishing: A CyFirma report describes recent FIN11 phishing campaigns where the threat actor relied on impersonating Zoom meeting invites to lure users to malware downloads.
GitHub phishing campaign: GitHub's security team has warned users about a phishing campaign that has been going on since at least September 16 and has targeted the owners of GitHub accounts. The company said emails part of this campaign are made to look like they're coming from the CircleCI service but redirect users to phishing pages meant to capture their GitHub credentials and multi-factor authentication codes. "Accounts protected by hardware security keys are not vulnerable to this attack," GitHub said.
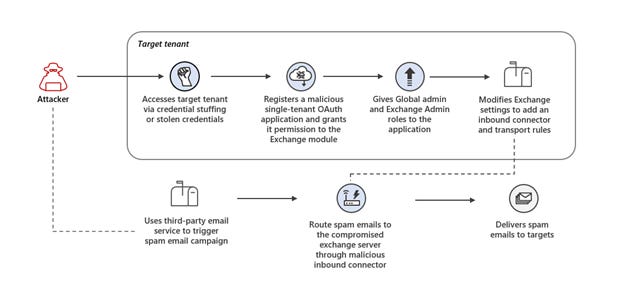
Exchange servers compromised for spam operations: Microsoft has a report out on a clever campaign where attackers compromise Azure tenant accounts through stolen credentials, install an OAuth app on the account, grant the app permission to interact with the server's underlying Exchange email server module, and then use this server as a proxy to relay spam campaigns via "clean servers." Pretty clever stuff, tbh.
Malware technical reports
Roshtyak: Avast's malware reversers analyzed Roshtyak, the backdoor component part of the Raspberry Robin USB-based worm that has been wreaking havoc across corporate networks this year.
Noberus ransomware: Broadcom's Symantec team covers changes and toolsets used by the Noberus (BlackCat, ALPHV) ransomware gang in recent attacks. This includes the deployment of a new version of the ExMatter exfiltration tool and its use of the Eamfo info-stealing trojan to steal credentials, including those stored in Veeam backup software.
More on ExMatter: And if you didn't like that report on ExMatter, here's one from Stairwell instead. As Lucian Constantin points out in his CSO coverage, ExMatter might be a game changer since it allows BlackCat operators to exfiltrate files, corrupt them on the victim's network, and then demand a ransom to return them—a process that's much faster than encrypting and decrypting them.
LockBit ransomware builder leaks online: The builder for the LockBit 3.0 ransomware strain was leaked online and has been widely shared over the past few days. The builder leak was initially advertised as a hack of the LockBit ransomware gang servers, but the leak was later also attributed to an intentional leak by one of LockBit's former programmers in a gesture of revenge against their former employer. As was the case of other core ransomware tools that leaked in the past, such as the Babuk and Conti source code, security experts now expect that numerous low-level threat actors will adopt the highly advanced LockBit builder for their own operations going forward. A technical analysis of the LockBit builder is also available here, and the builder itself is available on GitHub.
Crytox ransomware: Zscaler has published a report on the Crytox ransomware, active since late 2020 and mostly known for its successful attack on Dutch TV station RTL Nieuws.
FARGO ransomware: In newer ransomware attacks, AhnLab said on Friday that it's seeing a new strain named FARGO infecting and encrypting data on MSSQL servers.
Harly Android trojan: Kaspersky has published a report on Harly, an Android trojan that has been active since 2020 and which secretly subscribes infected devices to premium SMS services. Kaspersky says that since its first versions, they found the trojan in 190+ apps hosted on the official Play Store, collectively downloaded more than 4.8 million times.
APTs and cyber-espionage
Metador APT: At the first edition of the LABScon security conference, security firm SentinelOne presented details about Metador, a new APT they said has been targeting telcos, internet service providers, and universities across the Middle East and Africa. SentinelOne said Metador is a top-tier threat actor that is "highly aware of operations security, managing carefully segmented infrastructure per victim, and quickly deploying intricate countermeasures in the presence of security solutions." Based on current evidence, Metador operates two malware platforms to target Windows systems, along with at least one Linux implant.
At this time, there’s no clear, reliable sense of attribution. Traces point to multiple developers and operators that speak both English and Spanish, alongside varied cultural references including British pop punk lyrics and Argentinian political cartoons.
Void Balaur: At the same conference, SentinelOne also published new research on Void Balaur, a hacker-for-hire group first exposed last year by Trend Micro. In new attacks carried out this year, the group has targeted "a wide variety of industries, often with particular business or political interests tied to Russia."
Lazarus BYOVD attacks: AhnLab researchers have published an extensive report on BYOVD (Bring Your Own Vulnerable Driver) attacks employed by the Lazarus North Korean APT. The company notes that while these attacks have been seen since 2014, Lazarus is the first APT to have designed an elaborate rootkit that takes advantage of BYOVD techniques to elevate privileges and compromise all major Windows versions from the old Windows 7 up to the most recent OS version, Windows Server 2022.
New Lazarus attack: In the meantime, Chinese security researcher Hao Zhixiang said this week that he detected a new phishing campaign linked to the Lazarus group that has targeted virtual currency company Maitixport. IOCs in the Twitter thread below:
1)The North Korean Lazarus APT organization attacked the virtual currency company Maitixport. The link sent by the attacker was actually a malicious pdf file. Fake the content of the company's CEO's salary increase
— zhixiang hao (@HaoZhixiang) 3:55 AM ∙ Sep 21, 2022
@cyberwar_15 @malwrhunterteam @ShadowChasing1 @abuse_ch
HomeLand Justice IOCs: CISA and the FBI have published a joint report [PDF] on Wednesday with indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) used by "HomeLand Justice," the name used by the Iranian hackers in their attack against the Albanian government. The joint report confirmed a similar analysis published by Microsoft earlier this month, which said that the Iranian hackers gained access to the Albanian government's network a year prior to their attack in May 2021.
Pro-Indian Army influence operation: The Stanford Internet Observatory published a report on Wednesday on a sprawling Twitter influence operation involving 1,198 accounts that tweeted about India and Pakistan and which pushed pro-Indian Army views. SIO said their report expands on a previous report from ASPI.
Tweets praised the Indian Army's military successes and provision of services in India-administered Kashmir and criticized the militaries of China and Pakistan. Two accounts existed to target specific individuals who were perceived as enemies of the Indian government.
Scarlet Mimic: Check Point has published a report on Scarlet Mimic, a Chinese APT that has repeatedly targeted the Uyghur minority since 2016
Since then, CPR has observed the group using more than 20 different variations of their Android malware, disguised in multiple Uyghur-related baits such as books, pictures, and even an audio version of the Quran, the holy text of the Islamic faith. The malware is relatively unsophisticated from a technical standpoint. However, its capabilities allow the attackers to easily steal sensitive data from the infected device, as well as perform calls or send an SMS on the victim's behalf and track their location in real-time. Also, it allows audio recording of incoming and outgoing calls, as well as surround recording. All this makes it a powerful and dangerous surveillance tool.
TA413: On the same note, Recorded Future also has a report on TA413, a suspected Chinese APT group that's targeting Tibetans, another of China's favorite-to-abuse minority groups.
Over the first half of 2022, we have observed TA413 exploit a now-patched zero-day vulnerability targeting the Sophos Firewall product (CVE-2022-1040), weaponize the "Follina" (CVE-2022-30190) vulnerability shortly after discovery and publication, and employ a newly observed custom backdoor we track as LOWZERO in campaigns targeting Tibetan entities.
Vulnerabilities and bug bounty
Chrome vulnerability write-up: Numen Cyber Labs have published a write-up on CVE-2021–38003 and CVE-2022–1364, two Chrome zero-days patched in October 2021 and April 2022, respectively, that could be used for RCE attacks against Chrome users. The company warns that even if these two security flaws have been patched in the main Chrome browser, the patch gap that exists in software that uses Chrome's WebKit engine as their built-in browser means that many mobile apps are still vulnerable to this, including the likes of Skype and many crypto-wallets.
Study on jQuery vulnerabilities: Finnish security Lari Huttunen also conducted an interesting study this month. The researcher selected CVE-2020-11022, a vulnerability in the jQuery JavaScript framework, and used Shodan to scan the internet for web applications that are still vulnerable to attacks. During Shodan scans carried out over 60 days, the researcher found that:
- Approximately 26% of all the publicly reachable jQuery UI web applications contain a version of jQuery which is vulnerable to CVE-2020-11022.
- Approximately 21% of jQuery UI instances are EOL which raises my eyebrows even further.
15yo Python tarfile vulnerability: But if you were preparing to make an "if you use jQuery then you deserve it" joke, don't! Because stuff like this is everywhere, including in Python. According to a recent report published by the Trellix team, CVE-2007-4559, a vulnerability in the Python tarfile module is still impacting more than 350,000 software projects even today. Patching disasters like these are in every programming language. It's that people haven't been looking close enough.
This is well known.
— TheZero (@Th3Zer0) 9:01 AM ∙ Sep 22, 2022
Usually falls into "Zip Slip" or "Directory Traversal" vuln classes.
Most of modern static code analyzers already have rules to detect this.
Arbitrum vulnerability: A white-hat hacker has reported a vulnerability to the Arbitrum cryptocurrency platform that, if exploited, could have allowed an attacker to steal all funds sent to the network. The researcher received 400 ETH ($530,000) as a bounty for his report.
Would @arbitrum have been insolvent if that $470mm deposit a few days ago was stolen and they had to reimburse?
— riptide (@0xriptide) 5:02 PM ∙ Sep 20, 2022
Juplink router vulnerabilities: NCC Group researchers have found vulnerabilities in Juplink WiFi routers that can allow an attacker to reset an admin account's password.
Infosec industry
Tool update—Scout Suite: NCC Group updated this week its Scout Suite toolkit to be able to scan Kubernetes clusters for misconfigurations and not just cloud infrastructure.
Twitter list: AmpereSec CEO Patrick C. Miller has done the entire infosec industry a favor and created a Twitter list with all the CERT and ISAC teams from all around the globe.
If anyone is interested in following all of the global CERTs, CIRTs, SIRTs, CSIRTs, PSIRTs, NCSCs and ISACs - I made a list https://t.co/h9OtsVy5dK
— Patrick C Miller (@PatrickCMiller) 2:24 PM ∙ Sep 21, 2022
Let them fight: In a tweet on Tuesday, Microsoft Azure CTO and Sysinternals creator Mark Russinovich has urged the development community to move away from C and C++ and adopt Rust as their main programming language for future software projects, citing the language's better security and reliability. Since developers like to defend their favorite programming language like it's their own baby or their religion, drama, insults, and hilarity ensued.
Speaking of languages, it's time to halt starting any new projects in C/C++ and use Rust for those scenarios where a non-GC language is required. For the sake of security and reliability. the industry should declare those languages as deprecated.
— Mark Russinovich (@markrussinovich) 10:50 PM ∙ Sep 19, 2022
Cool Sysmon feature coming: At the LABScon conference on Thursday, the same Mark Russinovich also announced a new feature coming to Sysmon v14.1, the app's next version, which will include anti-wiping protection to prevent files from being deleted without authorization.
I'm excited to demo Sysmon 14.1 at @labscon_io today with file shred blocking, a feature that's been in the internal version since the start and that we enhanced to foil Russian activity in Ukraine. Public release is next week.
— Mark Russinovich (@markrussinovich) 4:17 PM ∙ Sep 22, 2022




