Risky Biz News: EU bans anonymous crypto payments
In other news: Russian cyber-spies go after German political parties; US to undertake airline privacy review; Apple chips leak secret keys via new side-channel attack.

This newsletter is brought to you by Sublime Security, an email security platform that's not a black box. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

The EU Parliament has passed new anti-money laundering legislation that bans anonymous cryptocurrency payments.
The legislation applies to payments made through online service providers, also known as hosted wallets. It also applies to platforms that exchange virtual for regular fiat currency. It does not apply to owners of hardware and self-hosted wallets.

The new rules come to complement the EU's MiCA (Markets in Crypto-Assets) framework, which passed last year and is scheduled to go into effect on December 30, 2024.
MiCA introduced mandatory know-your-customer (KYC) requirements for crypto-trading platforms, which forced them to obtain the names of their customers, including both sender and beneficiary, regardless of the size of the transfer. The new package completes MiCA and outright bans anonymous transactions.
The anonymous crypto payments ban was part of a new anti-money laundering legal package that also bans anonymous cash payments over €3,000 and any cash payments—anonymous or not—over €10,000.
The new rules passed through the EU Parliament's lead committees last week, according to Patrick Breyer, a member of the European Parliament for Germany.
Breyer, who is a member of the German Pirate Party and a renowned privacy advocate, is not a fan of the new rules.
"Generally prohibiting anonymous payments would at best have minimal effects on crime, but it would deprive innocent citizens of their financial freedom. The medicines or sex toys I buy is nobody’s business. To collect donations, dissidents such as the late Alexei Navalny and his wife are increasingly reliant on anonymous donations in virtual currencies worldwide. [...] This EU war on cash will have nasty repercussions! For thousands of years, societies around the world have lived with privacy-protecting cash. With the creeping abolition of cash, there is a threat of negative interest rates and the risk of banks cutting off the money supply at any time. Dependence on banks is increasing at an alarming rate."
In a Twitter post, Dash's Joel Valenzuala explains how the new rules will draw a line in the crypto-trading community between legitimate services and... the rest—call it criminal/privacy/anonymous/laundering world, or whatever.
"There will be a growing divide between the KYC crypto ecosystem and the anonymous world. [...] If we lived 100% on p2p crypto and only used decentralized/noncustodial tools, this new law wouldn't affect anyone at all!"
Back in January, Reuters reported that the EU's upcoming anti-money laundering package—besides introducing bans on anonymous cash and crypto transactions—would also include new rules for traders of luxury goods.
Reuters reported the EU was considering forcing traders to check the origin of funds used to purchase luxury goods, such as cars, planes, yachts, precious metals, jewelry, and even football clubs.
Informally referred to as the oligarch checks, that package has yet to pass through the EU Parliament (to our knowledge).
Breaches, hacks, and security incidents
Air Europa breach: Spanish airline Air Europa says that hackers might have stolen customer data in a security breach last year. The company said in a letter sent to customers that it got breached in October of last year. The company says hackers might have stolen data such as passport details, ID cards, phone, and email addresses. [Additional coverage in Reuters]
Med-Data settlement: Med-Data agreed to pay $7 million to resolve claims that one of its employees publicly posted patient information on GitHub in 2018 and 2019. [Additional coverage in TopClassActions]
KB hack lawsuit: A South Korean judge has ordered the Korea Credit Bureau to pay $46 million in damages to the KB Kookmin Card company over a 2013 security breach. The court found the Korea Credit Bureau at fault for placing a new employee in a position that had access to KB's customer data. The employee later stole the personal data of 53 million KB customers and sold it to an advertiser and loan agency. [Additional coverage in STS/English coverage in The Readable]
Dolomite crypto-heist: A threat actor has stolen $1.8 million worth of assets from the Dolomite cryptocurrency exchange. The incident took place on March 20. The hacker exploited a vulnerability in one of the platform's 2019 smart contracts. Users who still had the contract allow-listed lost funds from their wallets. [Additional coverage in CoinTelegraph]
Super Sushi Samurai crypto-rescue: Blockchain game Super Sushi Samurai has recovered $4.6 million worth of tokens that were stolen in an incident last week. The company says the hack was the work of a security researcher who exploited a bug in its code to move the funds and prevent a future theft. Super Sushi Samurai described the incident as a "white hat rescue" and ended up hiring the white-hat as a technical advisor.
General tech and privacy
Apple abandons HomeKit Secure Routers: Router vendors seem to believe that Apple has abandoned its HomeKit Secure Router program. Apple announced the technology at its 2019 developer conference. It allowed routers running the HomeKit software to firewall off and isolate each device on the internal network. [Additional coverage in AppleInsider]
Cloud providers call for Broadcom inquiry: A European cloud trade consortium has urged regulators and courts to investigate Broadcom over its new VMware licensing tactics. CISPE says Broadcom unilaterally canceled all VMware licenses following its acquisition of the company last year. Broadcom has since hiked prices for some licenses as much as twelve times. CISPE warns that several EU cloud providers are in danger of going bankrupt and out of business. The organization claims Broadcom should be categorized as a "gatekeeper" under the terms of the EU's new Digital Markets Act.
"As market leader in the cloud virtualisation sector (VMware held almost 45% of the virtualisation market in 2023) and the only viable option in some specific cloud sector applications which must be certified by software or service providers. Broadcom should be regarded as a Gatekeeper under the terms of the DMA and its actions should be seen as those of a dominant player as it forces ‘take it or leave it’ terms on customers. CISPE calls on regulators to swiftly examine Broadcom’s actions and call it to account."
Threads federates: Meta has now federated with Mastodon and the rest of the Fediverse.
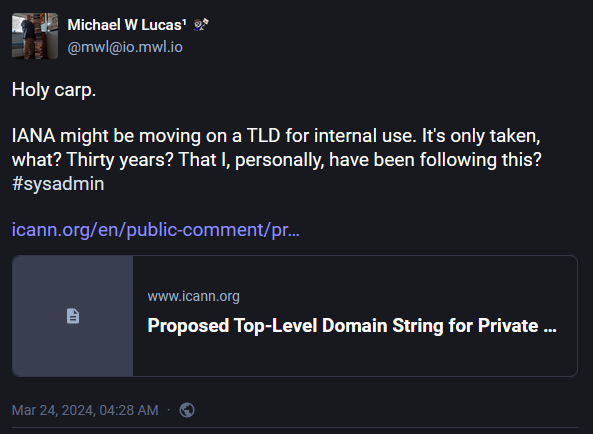
Private TLD: IANA is working on a private top-level domain (TLD) that will be reserved for use on private networks. After a public submission period, IANA has decided on .internal.
Government, politics, and policy
UN AI resolution: The United Nations General Assembly has adopted a resolution on artificial intelligence. UN officials have called on tech companies to develop safe and reliable AI systems that comply with international human rights. Systems that don't comply should be taken offline. Officials said the same rights that apply offline should also be protected online, including against AI systems.
DOT privacy review of US airlines: The US Department of Transportation (DOT) will undertake a privacy review of the country's ten largest airlines. Officials will analyze how airlines collect, handle, and use passengers' personal data. The DOT seeks to find out if airlines are protecting user data and if they're secretly selling data to third parties.
Spain blocks Telegram: Spain's High Court has ordered ISPs to block access to the Telegram messaging service. Judges blocked the site following a complaint from the country's four media companies. Mediaset, Atresmedia, Movistar, and Eged complained that Telegram was "disseminating" their content without approval. [Additional coverage in Euronews]
New UK data breach fining guidelines: The UK's privacy watchdog has published public guidance the agency will use when determining fines for privacy violations and security breaches. The ICO has promised reduced fines for companies that report breaches and collaborate with the UK's cybersecurity agency. The fine reduction will vary based on each company's cooperation and engagement level. On the other hand, companies that benefit financially from their rule-breaking should expect higher fines than anyone else.
Chinese hackers target UK politicians: Deputy Prime Minister Oliver Dowden is set to brief Parliament this week about Chinese cyber-espionage operations that targeted the country's senior politicians. [Additional coverage in The Independent]
China revises data transfer rules: The Chinese cyberspace administration has relaxed its rules regarding cross-border data transfers. The agency says it will allow companies to transfer data overseas if the data does not contain personal information. Foreign companies and Chinese companies doing business overseas previously had to subject themselves to lengthy security assessments to be allowed to transfer data abroad. [Additional coverage in Reuters]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Josh Kamdjou, co-founder and CEO of Sublime Security. Josh describes how Sublime implemented the concept of attack surface reduction to email security last year, how it works, and what customers are saying about it.

Cybercrime and threat intel
Stream bot herder sentenced to prison: Danish authorities have sentenced a 53-year-old man to 18 months in prison for fraud and copyright infringement. Officials say the man uploaded both original and stolen altered songs to Spotify and Apple Music accounts. He then used bot accounts to generate billions of plays and collect royalties. According to Wired, the man's fraud helped him become the 46th highest-earning musician in Denmark.
UN report on DPRK hacking: North Korean hackers are suspected to have breached 58 cryptocurrency companies. In a report this month, the UN Security Council says North Korean hackers have stolen approximately $3 billion worth of crypto-assets between 2017 and 2023. Besides cryptocurrency, the UN says DPRK hackers also targeted defense companies and software supply chains.
Fake-SMS campaign: Aleksa Majkic takes a deep dive into Fake-SMS, an old tool that used to contain malware, and its supposed creator, an individual identified as Sikander Rasheed.
Spyware detection: Group-IB has published a how-to for detecting the "most common" forms of commercial spyware, such as Predator and Pegasus. [h/t Simon Tsui]
New npm malware: Twenty-four malicious npm packages were discovered last week. Check out GitHub's security advisory portal for additional details.
Threat/trend reports: Censys, CERT NZ, CyFirma, MTC RED, and Palo Alto Networks have recently published reports covering infosec industry threats and trends.
Malware technical reports
StrelaStealer: Palo Alto Networks has identified a large-scale StrelaStealer campaign impacting over 100 organizations across the EU and US in 2023 and 2024.
TellYouThePass ransomware: Chinese security firm Qihoo 360 has published a report on recent attacks across China with the TellYouThePass ransomware.
VexTrio fingerprinting: Malware analyst Gi7w0rm has published a report on the browser fingerprinting techniques used by VexTrio, a TDS platform that launched back in 2017.
Sponsor Section
The latest evolution of PikaBot is using phishing to gain initial access. Learn why it’s been effective and how to protect your organization from novel email attacks. Read the full post.
APTs, cyber-espionage, and info-ops
APT29 attacks German political parties: Russian hackers linked to the country's intelligence services are targeting German political parties. The attacks have been carried out by APT29, one of the cyber units inside Russia's SVR Foreign Intelligence Service. Mandiant says this is the first time APT29 has targeted political parties. The campaign comes as political tensions rise surrounding Germany's support for Ukraine.
Russian disinformation in Africa: Gen. Michael Langley, the head of US Africa Command, said that Russian online disinformation campaigns helped the Kremlin-backed junta gain control of Niger and kick US troops out of the country. [Additional coverage in DefenseOne]
Germany's nomenclature: Germany's cybersecurity agency BSI has published its names/nomenclature for APT and cybercrime groups active in the country.
Patchwork (APT-C-09): Qihoo 360 has published a report on Patchwork (APT-C-09) campaigns using Pakistani tax revenue agency lures.
Vulnerabilities, security research, and bug bounty
GoFetch side-channel attack: A team of academics has discovered a side-channel attack that can extract secret keys from Apple CPUs. The attack is named GoFetch and can leak data from a CPU cache system named the data memory-dependent prefetchers (DMPs). GoFetch attacks affect Apple M1, M2, and M3 chips. It is a microarchitectural issue and can't be fixed via a software update. GoFetch defenses can be added inside third-party software, but they drastically degrade performance. [Additional coverage in Kim Zetter's Zero Day]
Unsaflok vulnerabilities: A team of security researchers has discovered vulnerabilities in Saflok RFID locks. The vulnerabilities are collectively known as Unsaflok and affect all Saflok models. They impact over 3 million locks installed in more than 13,000 homes and hotels across the world. The vulnerability was discovered in September 2022 but was disclosed this month to allow patches to roll out. Wired reports that despite the vendor's effort, only 36% of locks were patched.
"For many of the Saflok systems sold in the last eight years, there's no hardware replacement necessary for each individual lock. Instead, hotels will only need to update or replace the front desk management system and have a technician carry out a relatively quick reprogramming of each lock, door by door."
GLPI vulnerabilities: Quarkslab has published a report on two vulnerabilities they found in GLPI, an open-source IT management platform.
Zephyr OS vulnerability: Synopsys has found a vulnerability (CVE-2023-7060) in the Zephyr real-time operating system.
Crowdfense returns: UAE-based vulnerability acquisition program is back online after what has been described as a restructuring. [Additional coverage in Intelligence Online]
Infosec industry
Cyber reporter moves: Tim Starks has re-joined CyberScoop after his stint at the Washington Post.
New tool—TrailDiscover: Cybersecurity engineer Adan Álvarez has open-sourced a tool named TrailDiscover, a collection of AWS CloudTrail events that usually trigger and are linked to security incidents or actions.
New tool—XProtect-Malware-Families: SentinelOne has published a tool that maps XProtect's obfuscated malware family names to common malware names used by the infosec industry.
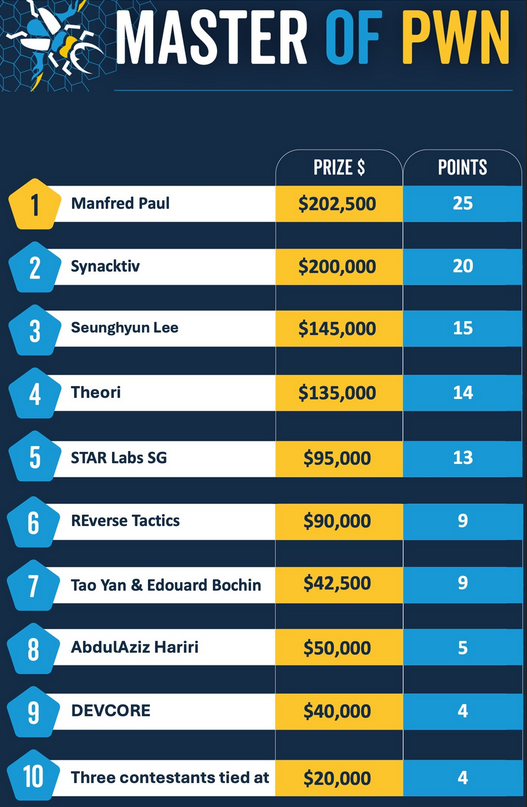
Pwn2Own Vancouver 2024: Security researcher Manfred Paul has won the Pwn2Own hacking contest after hacking all four major browsers. Paul found exploits in Chrome, Edge, Firefox, and Safari. Mozilla patched the Firefox exploit within hours of being demoed at the contest. Security researchers successfully demoed 29 zero-days during the contest and took home $1.1 million in money prizes.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at Russia's recent leak of an intercepted German military discussion. From an intelligence point of view, the content of the discussion is only moderately interesting, but Russia decided to leak it in an attempt to influence European attitudes towards providing military aid to Ukraine.




