Risky Biz News: EU adopts new sanctions framework to cover Russia's cyber warfare and disinformation
In other news: Largest US water utility provider hit by a cyberattack; hackers wipe servers at Russian state TV company; EU government orgs targeted with air-gap jumping malware.

This newsletter is brought to you by application allow-listing software maker Airlock Digital. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The European Council adopted on Tuesday a new sanctions framework designed to counter Russia's hybrid attacks against EU member states.
The new framework expands the type of actions the EU can leverage sanctions against the Russian government, organizations, and individuals involved in the Kremlin's ever-increasing aggression.
It's been expanded to cover:
- The use of coordinated disinformation, foreign information manipulation and interference (FIMI);
- Malicious cyber activities;
- The undermining of electoral processes and the functioning of democratic institutions;
- Threats and sabotage of economic activities, services of public interest, and critical infrastructure;
- And the instrumentalization of migrants.
Policy and cybersecurity experts have long criticized the EU in the past for failing to mirror many of the US' sanctions on Russian disinformation and cyber operations.
Just three weeks ago, the US sanctioned RT and its parent company for evolving from a news organization into a propaganda peddler and a fully active intelligence asset for the Russian government, complete with its own cyber unit. Such sanctions, and many others, were not mirrored by the EU, which, ironically, sees and deals with the brunt of most of Russia's disinformation and propaganda operations.
According to the EU, the new sanctions framework would provide a simpler way to respond to Russia, impose asset freezes, forbid interaction with sanctioned entities, and impose travel bans.
Breaches, hacks, and security incidents
US moves to seize DPRK crypto: The US government has seized $2.67 million worth of crypto assets stolen by North Korean hackers. The government has recovered $1.7 million stolen in the Deribit hack in November 2022 and another $970,000 stolen from Stake.com in September 2023. Both hacks were linked to North Korea's Lazarus group. Officials traced the funds even if they were laundered through the Tornado Cash mixer. [Additional coverage in The Block]
Comcast indirect breach: Comcast says that hackers have stolen the personal information of over 235,000 customers following a ransomware attack on a third-party debt collection service. The incident took place in February this year and impacted Financial Business and Consumer Solutions (FBCS). Comcast joins Truist Bank, another FBCS client that had data stolen in the incident.
American Water Works cyberattack: US public utility company American Water Works has taken some of its IT systems offline after a cyberattack last week. The incident paused online billing to customers but did not affect any water supply systems. American Water Works is the largest water utility provider in the US, with more than 14 million customers. [Additional coverage in CBS]
CreditRiskMonitor breach: Financial news and analysis service CreditRiskMonitor.com has disclosed a security breach in SEC filings this week. The incident took place in mid-July.
Casio security breach: Japanese electronics giant Casio says that hackers accessed one of its IT systems in a security breach last week.
ADT hack: Home alarm and physical security company ADT has disclosed a data breach in SEC filings. This was the company's second breach this year after another one in August.
MoneyGram notifications: Money transfer service MoneyGram has begun notifying customers who had data stolen in a security breach at the end of last month. [Additional coverage in TechCrunch]
Qantas Airlines frequent flier points theft: Australian airline Qantas says two employees from an Indian contractor stole frequent flier points from customer accounts. The two employees worked for India SATS, the ground handler for Qantas Airlines in India. Qantas alleges the two employees changed flight booking records and reassigned frequent flier points to an account they control. The scheme took place in July and August this year and impacted over 800 bookings. [Additional coverage in CyberDaily]
Dr.Web hack: A threat actor known as DumpForums has taken credit for the hack of Russian antivirus maker Dr.Web.
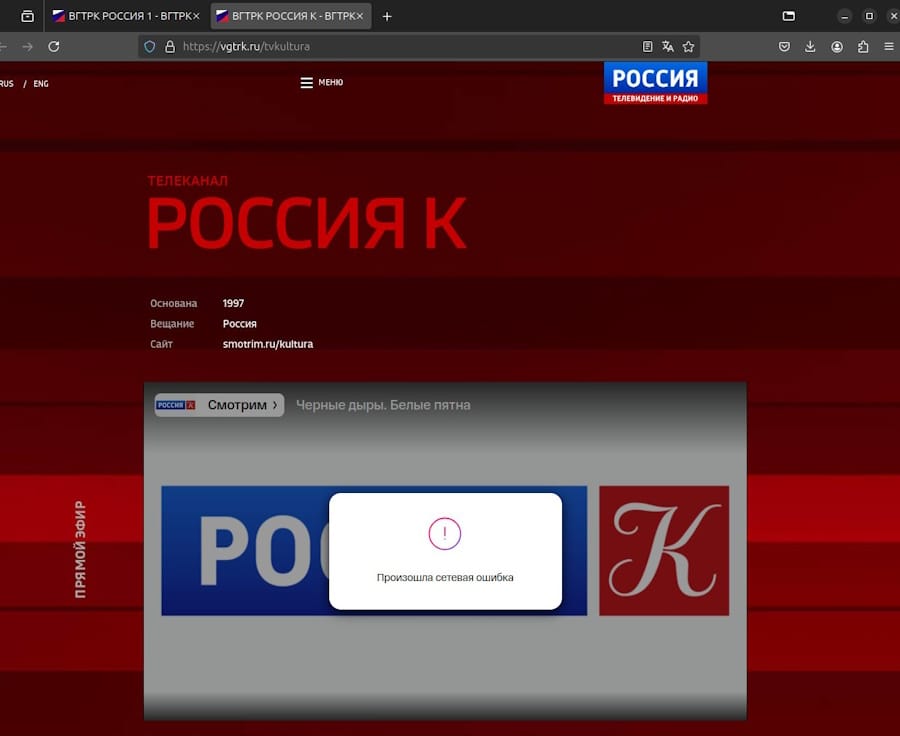
VGTRK wiper attack: Hackers have disrupted the broadcasts of Russian state radio and TV in a cyberattack that took place over the weekend. The attack targeted VGTRK (All-Russia State Television and Radio Broadcasting Company), a Russian state-owned company that operates Russia's main national TV and radio stations. The attack allegedly wiped internal servers and took down official websites and online broadcasts for TV channels like Rossiya-1, Rossiya-24, and others. A pro-Ukrainian group named "sudo rm –RF" took credit for the attack in a message posted on Twitter. [Additional coverage in Gazeta.ru/English coverage in Reuters]
General tech and privacy
US OAGs sue TikTok: Fourteen US states have filed a lawsuit against TikTok over the company's deceptive business practices. The attorneys general say the company lied about the safety of its platform for young children and that its algorithms harm children's mental health. Officials claim the company's safety tools don't work and that TikTok continues to recommend harmful behavior to young children. The lawsuit also accuses TikTok of breaching the Children's Online Privacy Protection Act and collecting children's data without parental consent.
Google loses Epic US case: A US judge ordered Google to open its official Play Store to third-party app stores. The Play Store must host the apps of other app stores and must allow third-party stores access to its database of Android apps. The judge has also prohibited Google from forcing apps to use the Play Store billing system and from paying developers to make apps exclusive through its store. The ruling came in a long-lasting lawsuit filed by Epic, the developer of the Fortnite game. Google says it plans to appeal the ruling. [Additional coverage in TechCrunch]
YouTube starts hiding Skip Ad button: Google has begun hiding the Skip Ad button for some of its ads on its desktop and mobile sites. [Additional coverage in Android Police]
Apple fixes bug that broke security tools: Apple has released a fix for its macOS operating system that fixes an issue that crippled security tools and VPNs. [Additional coverage in TechCrunch]
Government, politics, and policy
Security cameras across Finland: The number of security cameras across Finland's cities has exploded over the past year following a rise in robberies in public places and "hybrid attacks." [Additional coverage in Yle]
Ukraine military CERT: The Ukrainian government is creating a CERT-like structure for its military to deal with the ever-increasing number of Russian cyber operations.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Airlock Digital founders Daniel Schell and David Cottingham about other things Microsoft can do to secure and harden Windows.
Cybercrime and threat intel
Racoon Stealer dev pleads guilty: A Ukrainian man has pleaded guilty to creating and selling the Racoon Stealer malware. Mark Sokolovsky was arrested in the Netherlands in March 2022 after authorities seized and shut down his operation. Until US authorities announced his arrest in October of that year, fellow malware developers thought Sokolovsky had died in the war in Ukraine. Other malware developers have now taken over the Racoon Stealer malware and have released new versions.
Second Bohemia Market admin arrested: Dutch authorities have arrested one of the administrators of the Bohemia and Cannabia dark web marketplaces. He was arrested at the Schiphol airport in Amsterdam in June this year. Another Bohemia Market administrator was detained at the start of August in Dublin, Ireland. Officials say the two markets were used to advertise and sell drugs and cybercrime services, such as malware and DDoS attacks.
SE Asia scam groups make bank: A United Nations report estimates that victims in East and Southeast Asia have lost between $18 billion and $37 billion to online scams in 2023 alone. The vast majority of the losses were to crime cartels running scam compounds across Southeast Asia. The UN also noted a 600% rise in crimes that involved AI-driven technologies, such as deepfakes.
KMS passes: Rory Stephen Guidry, formerly known as KMS on the hacking forum Darkode, passed away on October 1. [h/t Brian Krebs]
Israeli spyware industry lobby effort: The Israeli spyware industry is spinning its lobby groups back up in the hopes of having sanctions lifted in the case of a Trump victory next month. [Additional coverage in IntelligenceOnline]
Buhtrap attacks: Russian security firm says it detected new attacks originating from the old Buhtrap gang, a cybercrime syndicate composed of Russian-speaking individuals that has been active since late 2014.
CosmicSting attacks: The number of threat actors exploiting the Magento CosmicSting vulnerability has now reached eight.
Mamba 2FA: Sekoia researchers have published a report on a previously unknown phishing service named Mambo 2FA (named so because it can intercept 2FA challenges).
Tmate abuse: InfoGuard's Stephan Berger looks at how the TeamTNT crypto-mining gang is abusing the Tmate terminal-sharing app to backdoor Linux servers.
File hosting service abuse: Microsoft looks at a recently re-popularized trend where phishing groups abuse file hosting services to store resources for their phishing pages. What's old is new again!
Trinity group attacks: The US Health Department has warned healthcare organizations to be on guard for attacks from a new ransomware operation named Trinity. The group appeared in May this year and has hit seven targets, including two healthcare organizations. The HHS cybersecurity team believes the gang may be a rebrand or have connections to the older Venus and 2023Lock ransomware groups. [Additional coverage in The Record/ See HHS alert/PDF]
Malware technical reports
Dark Angels ransomware: The Zscaler team has published a deep dive into Dark Angels, a ransomware group that's been around since April 2022.
"Dark Angels operate with more stealthy and sophisticated strategies than many other ransomware groups. Instead of outsourcing breaches to third-party initial access brokers that target a wide range of victims, Dark Angels launch their own attacks that focus on a limited number of large companies."
SilentCryptoMiner: Dr.Web looks at SilentCryptoMiner, a new crypto-mining trojan that is currently being distributed bundled inside office programs, game cheats, and online trading bots.
PhantomLoader: ANY.RUN has published a report on PhantomLoader, as it was used in a recent campaign where it was disguised as a DLL for an antivirus software called 360 Security Total. In this attack, it was used to deploy another malware strain named SSLoad.
Pronsis Loader: Trustwave has discovered a new malware strain named Pronsis Loader. The malware first appeared in November of last year and is currently being used to distribute other malware strains, such as Latrodectus and Lumma Stealer. Researchers say Pronsis bears similarities to the older D3F@ck Loader.
Lua malware: Morphisec has looked at the same Lua malware that OALABS spotted earlier this year.
Yunit Stealer: CyFirma looks at Yunit Stealer, another one of those new infostealers currently flooding the MaaS market.
"The stealer appears to have been named after the computer game 'Yunit.' The developer, who also claims to be from France, has a Twitch account (an American video live-streaming platform focused on gaming) and has referenced this connection on GitHub as well. Furthermore, the developer's YouTube channel features multiple live streams of games, reinforcing the idea that the stealer may have been inspired by the game or its branding."
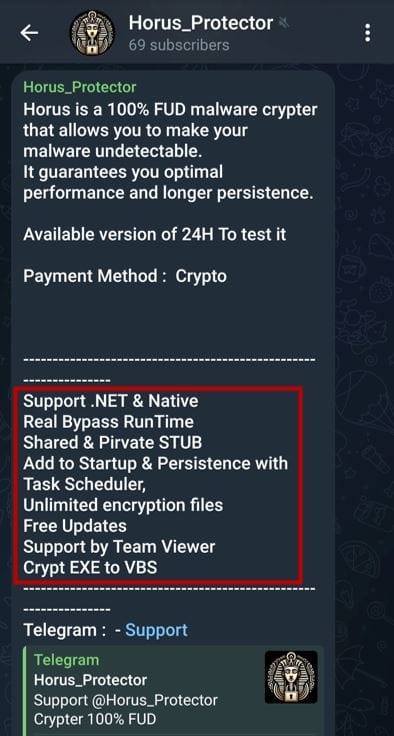
Horus Protector: SonicWall's security team has published a report on Horus Protector, a new crypting service advertised in underground cybercrime circles.
"The authors appear to be native French speakers. The files in the distribution mechanism have instructions in the French language and the desktops shown in YouTube demo videos have French as the default language for the software installed on their desktop."
Sponsor Section
David Cottingham, CEO of Airlock Digital, shows Patrick how Airlock's execution control and allow-listing solution works.
APTs, cyber-espionage, and info-ops
Awaken Likho: Kaspersky has published a report on Awaken Likho (Core Werewolf), an APT group targeting Russian government organizations.
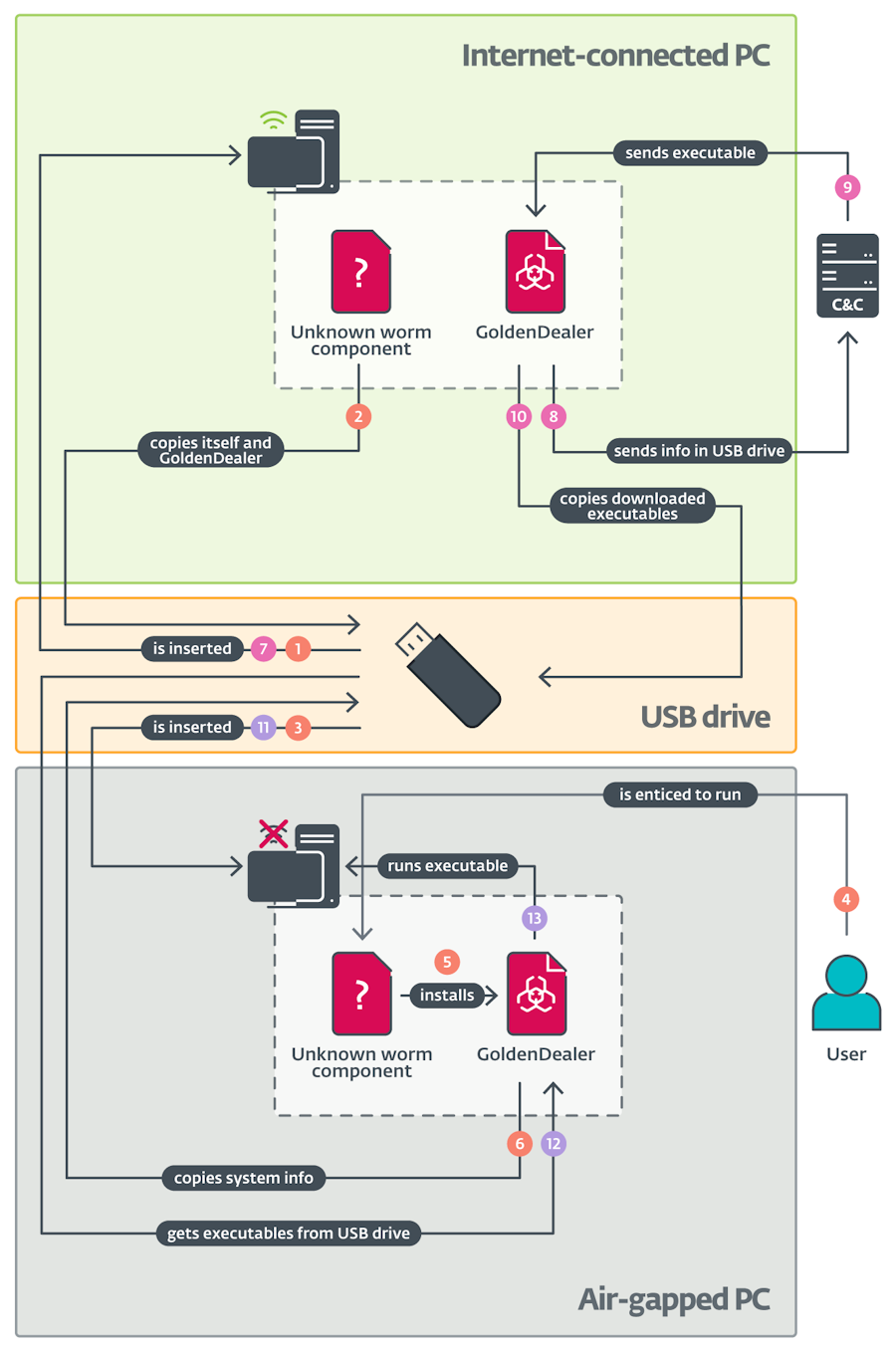
GoldenJackal: A cyber-espionage group named GoldenJackal has targeted high-value air-gapped systems located at government organizations across Europe. The attacks took place between May 2022 and March 2024 and used previously undocumented malware. The malware infected USB devices that were used to transport data from internet-connected PCs to air-gapped systems. ESET says the group has experience with these types of attacks, having conducted a similar operation against a South Asian embassy in Belarus in 2019.
Vulnerabilities, security research, and bug bounty
Patch Tuesday: Yesterday was the October 2024 Patch Tuesday. We had security updates from Adobe, Microsoft, Ivanti, Fortinet, Intel, SAP, Schneider Electric, Siemens, Rockwell, and Zoom. The Android Project, Apple, Chrome, Firefox, Citrix, Cisco, Kubernetes, JetBrains, Okta, NVIDIA, QNAP, and Jenkins released security updates last week as well.
Microsoft Patch Tuesday: This month, Microsoft patched 121 vulnerabilities, including two actively exploited zero-days.
- CVE-2024-43572 - Microsoft Management Console RCE
- CVE-2024-43573 - Windows MSHTML Platform Spoofing
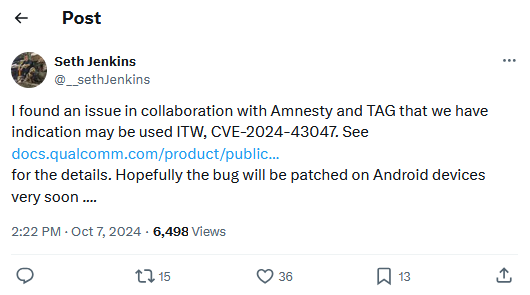
Qualcomm zero-day: American chipmaker Qualcomm has released a security update to fix an actively exploited zero-day (CVE-2024-43047) in its FASTRPC driver. Attacks exploiting the zero-day were spotted and confirmed by Amnesty International and the Google TAG security teams. Patches have been made available to smartphone vendors and are expected to roll out to Android users.
New Ivanti CSA zero-days: Ivanti has patched three new zero-days that were exploited in the wild to target owners of its Cloud Service Appliance (CSA). The new zero-days were used together with an older zero-day from last month as part of a complex exploit chain. Over the past month, Ivanti has now patched five different CSA zero-days. Details about who is behind the attacks are still unknown.
Docker Zombie Layers: GitGuardian researchers have discovered that Docker image layers continue to exist in registries after they've been removed from manifest files. The files can live up for multiple weeks before being removed by the registry garbage collector. These zombie files may contain API tokens and various secrets and may expose companies to unforeseen attacks.
Redis vulnerability: Security researcher Axel Mierczuk has published a write-up on CVE-2024-31227, a DoS bug that's been present in the Redis code for close to three years.
Apache Avro vulnerability: Kostya Kortchinsky, a security researcher from the Databricks security team, has discovered and helped patch an RCE vulnerability (CVE-2024-47561) in the Apache Avro data serialization library.
PrintNightmare bypass: Mod0 security researchers have found a bypass for the PrintNightmare patches.
Infosec industry
NCSC board guidance: The UK's cybersecurity agency has published a guide on how security execs (i.e., CISOs) can communicate more effectively with board members to improve cybersecurity decision-making.
Kasperky Play Store ban: Russian security firm Kaspersky says that Google removed its apps from the official Play Store following a recent US government ban. The US Commerce Department banned Kaspersky from operating in the US in June and told the company to exit the US market by September 29. Kaspersky sold its US business to Pango and replaced all Kaspersky US installs with the UltraAV antivirus last month. The Russian company contested Google's decision,, and called it an overinterpretation of the US government ban, which did not prohibit Kaspersky from distributing its software outside the US. Its beef with Google comes in the same week it also closed its UK offices and laid off dozens of employees.
Acquisition news: Cloudflare has acquired cloud security and compliance company Kivera.
New book: "PROPAGANDA: from disinformation and influence to operations and information warfare," a book by Polish researcher Lukasz Olejnik, is now out.
Threat/trend reports: Deloitte+The Female Qoutient, FalconFeeds, Imperva, Portnox+Wakefield Research, PwC, Secureworks, and Tenable have recently published reports and summaries covering various infosec trends and industry threats.
New tool—cred1py: SpecterOps has released cred1py, a tool to exploit CRED-1 over a SOCKS5 connection.
New tool—SharpExclusionFinder: Friends & Security has released SharpExclusionFinder, a tool to find Microsoft Defender excluded paths and folders.
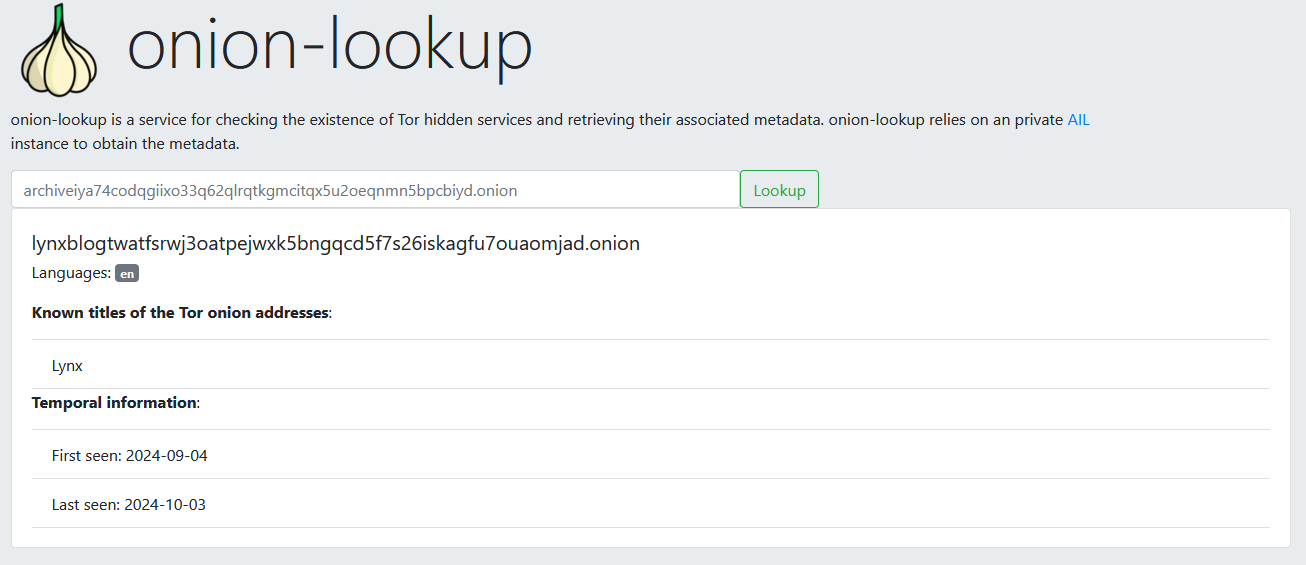
New tool—onion-lookup: Infosec researcher Alexandre Dulaunoy has launched onion-lookup, a web tool to check the existence of Tor hidden services and retrieve associated metadata. The tool's source code is also available on GitHub.
New tool—Drasi: Microsoft has open-sourced Drasi, a Data Change Processing platform that can detect and react to data changes that occur in existing databases and software systems. While the project has applications in various forms of software development, it can also used for raising alarms when a threat actor modifies existing infrastructure. The project's code is also available on GitHub.
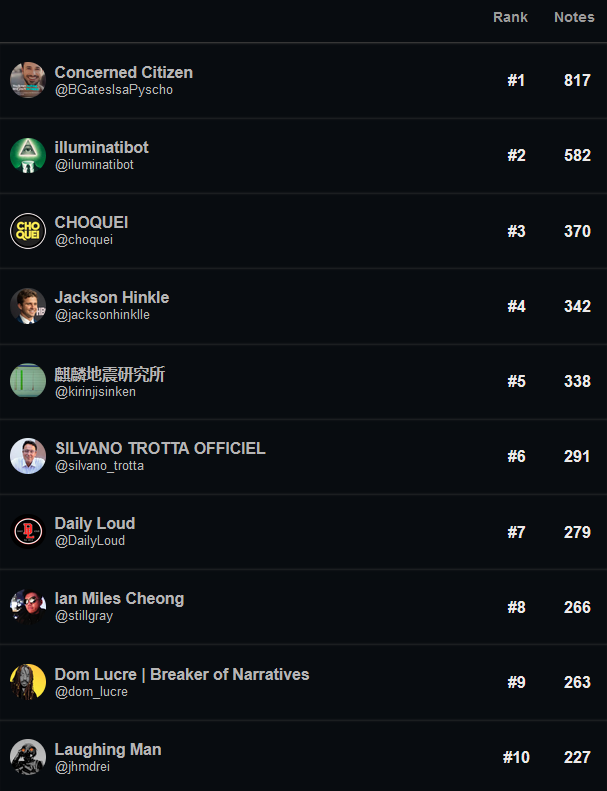
New tool—Community Notes Leaderboard: There's now a project named Community Notes Leaderboard that keeps track of the Twitter accounts that received the most community notes for misleading tweets.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about 'cyber persistence theory.' They cover what it is, why it is increasingly popular amongst America's allies, why we think the theory is right, and also cover some critiques of the theory.
In this podcast, Tom Uren and Adam Boileau talk about how the US government's response to Iranian election interference is proceeding at light speed. This allows other actors, such as Meta, to make decisions relating to interference with certainty.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!




