Risky Biz News: Encryption and privacy pioneer Peter Eckersley has died
In other news: Samsung and the IRS disclose breaches; Chrome fixes new zero-day; and Cloudflare yeets KiwiFarms.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The cyber-security industry lost a seminal figure over the weekend with the death of Peter Eckersley, a beloved security software engineer and privacy activist who played a crucial role in many of today's web encryption technologies.
Born and educated in Australia, he spent 12 years working for the Electronic Frontier Foundation, where he helped co-found and co-create many of today's most notable privacy-inclined projects, including the likes of Let's Encrypt, Certbot, Privacy Badger, HTTPS Everywhere, SSL Observatory, and Panopticlick (later rebranded to Cover Your Tracks).
Mr. Eckersley shared a passion with the late Aaron Swartz (with whom he lived in a shared EFF house) for internet privacy, open knowledge, and anti-big-tech tracking. In recent years, after he left the EFF, he joined the Partnership on AI and then co-founded the AI Objectives Institute, two non-profits that advocated for the responsible use of AI by governments and tech firms, seeing it as a future threat to the ordinary people, similarly on how he foresaw the need for privacy and encryption on the world wide web.
Paul Ducklin of Naked Security and the Let's Encrypt team have touching obituaries on Mr. Eckersley's life and career.
According to Brave security engineer Yan Zhu, who used to work with Mr. Eckersley at the EFF and who shared the news of his death, he died on Friday night, September 2, due to pre-operation complications following a cancer diagnosis just days before.
He was only 43. May he rest in peace!
EFF mourns the loss of our friend and colleague Peter Eckersley. As EFF’s Chief Computer Scientist, Peter helped encrypt the web and make the internet a safer place.
— EFF (@EFF) 6:23 AM ∙ Sep 3, 2022
Peter has done a lot for keeping the Internet even moderately safe for users -- both directly and indirectly. Met him several times to try to get free SSL certs widely deployed.
— Ryan Lackey (@octal) 3:59 AM ∙ Sep 3, 2022
Peter’s contributions to securing the internet are incomparable. He will be deeply missed. Rest In Peace Peter.
— Aanchal Gupta (@nchlgpt) 6:13 PM ∙ Sep 4, 2022
At a Silicon Valley dinner, I was the token woman & (shocker) no one seemed interested in what I thought...except Peter. He talked to me. He made me feel like I belonged & had brilliant ideas. He remembered them, too, and brought them up as they become more relevant years later.
— MMitchell (@mmitchell_ai) 3:08 AM ∙ Sep 4, 2022
Damn. It’s so striking to me with Peter’s passing how much obviously worse off the world is without him.
— Moxie Marlinspike (@moxie) 5:01 AM ∙ Sep 3, 2022
Ultimately the world isn’t very good at saying thank you outside of the market, but Peter definitely deserved our thanks, and I fear we may not have thanked him enough.
🧵💔In 2010 this kind, clever and passionate privacy technologist / advocate casually told me @EFF was borrowing some @noscript code to build a "pre-release project" called @HTTPSEverywhere...
— Giorgio Maone (@ma1) 1:44 PM ∙ Sep 3, 2022
1/3
Breaches and hacks
IRS website snafu: The US Internal Revenue Service said on Friday that it accidentally leaked confidential information for 120,000 taxpayers who filed a form 990-T in the past. According to a data breach notification letter [PDF] obtained by the WSJ, the breach occurred due to a website error; after an XML file containing the affected taxpayers' data was left freely accessible via the IRS' official website. The file and subsequent leak were discovered by an IRS research employee.
Samsung breach: And just like any respectable company, Samsung sat on a security breach for more than a month to disclose it on the Friday right before the extended Labor Day weekend in the US. In a short message, the company said it was hacked in late July, found out about the breach on August 4, and disclosed the incident on September 2. The good news is that no SS or financial data was impacted and that hackers only took names, DOBs, and "contact and demographic information" (whatever that means). Samsung didn't say how many users were impacted.
seems @SamsungUS was hacked
— Johnathan Norman (@spoofyroot) 8:23 PM ∙ Sep 2, 2022
New Desorden leaks: Hacking group Desorden Group has leaked new data last week containing information from hundreds of Indonesian and Malaysian restaurants. More than 400,000 customer records and 16,000 employee records were leaked by Desorden, according to DataBreaches.net.
Another crypto-heist: DeFi platform Kyber Networks said last week that it was hacked for $265,000 after a threat actor exploited a vulnerability in its frontend to go after whale wallets (accounts with large deposits). More in the company's Twitter thread below.
1/ ❗️Notice of Exploit of KyberSwap Frontend:
— Kyber Network (@KyberNetwork) 7:28 PM ∙ Sep 1, 2022
We identified and neutralized an exploit on the KyberSwap frontend. Affected users will be compensated. We have summarized the details in this thread⬇️
And a second crypto-heist: Similarly, privacy coin ShadowFi also lost around $300,000 last week as well. This time, the attackers used an exploit in the company's smart contract, which according to ShadowFi, had previously passed not one but two security audits.
Open Hands claim: Iranian hacking group Open Hands claims to have hacked the personal phone of Mossad chief David Barnea and, as proof, posted photos from his recent dental work on their Telegram channel. In March this year, the same group also claimed to have had the Mossad chief under surveillance for eight years, also leaking tax documents and family photos.
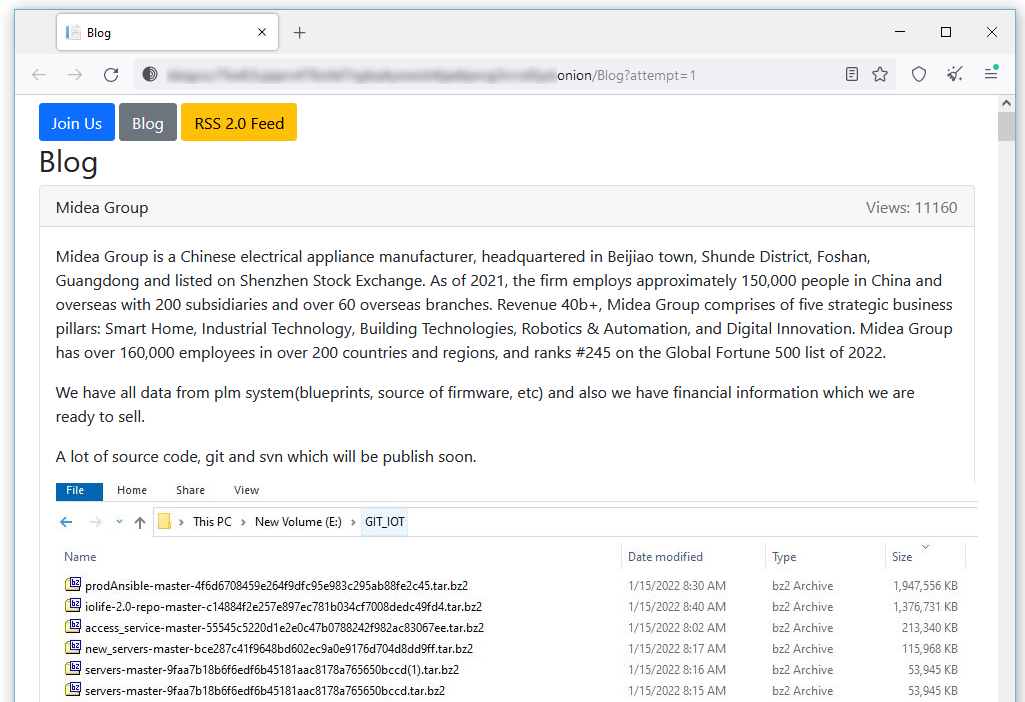
Midea Group ransomware attack: In a surprise to many security analysts, the original leak site of the now-defunct REvil gang was updated last week to claim another victim—Chinese electrical appliance manufacturer Midea Group; considered the world's largest appliance vendor and one of the world's largest companies. Midea officials have not yet confirmed the incident.
General tech and privacy
Cloudflare drops KiwiFarms (and probably regrets it): After an absurd amount of lobbying, internet infrastructure company Cloudflare decided to finally drop harassment forum KiwiFarms from its network. Cloudflare insisting on keeping KiwiFarms as a customer after weeks of complaints against the site and its users led to a hilarious and absurd situation where even the former operator of DDoS booter services was questioning Cloudflare's policy of sheltering the internet's scum on its network, including DDoS-for-hire platforms like his former service.
Tor in Rust: The Tor Project released Arti v1.0.0, the first production-ready release of the Tor protocol, re-written in the Rust programming language.
ALYac antivirus crashes systems: ESTsecurity's ALYac antivirus product caused havoc in South Korea last week when it crashed its customers' systems after identifying the Windows OS as ransomware. The issue was traced back to a bad detection rule, and the company said the rule only shipped to its free product and not the corporate commercial version.
Microsoft failing as well: But ESTsecurity is not the only company that has botched a detection rule update this week. You can also add Microsoft to this list, which detected Google Chrome on Sunday as a version of the Hive ransomware.
YouTube moves on election disinformation: Two months ahead of the US midterm elections, YouTube has announced a new set of rules (and penalties) around election videos.
As our systems connect viewers to authoritative content and limit the spread of harmful misinformation, we're also removing election content that violates our policies. This includes misleading voters on how to vote, encouraging interference in the democratic process, inciting violence, or advancing certain types of election misinformation.
Edge 105: And a little bit of good news for Microsoft Edge users from Johnathan Norman, the former head of Microsoft Edge's Vulnerability Research team.
Edge 105 will release to stable this week and include WASM support for Enhanced Security Mode on Windows x64 platforms. So far millions of users have tried jitless browsing and seem to enjoy it, despite the claims it would be too slow. 1/
— Johnathan Norman (@spoofyroot) 8:01 PM ∙ Sep 1, 2022
Government, politics, and policy
Romania and Ukraine cyber treaty: The governments of Romania and Ukraine signed a memorandum on cooperation in the field of cybersecurity defense. The new treaty is identical and comes after Ukraine signed a similar treaty with its neighbor to the northwest, Poland, a week before.
Likewise, dear Dan! We definitely look forward to our fruitful cooperation in helping our countries staying resilient to emerging cyberthreats 🇺🇦🤝🇷🇴
— Victor Zhora (@VZhora) 2:14 PM ∙ Sep 2, 2022
Sponsor section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
Cybercrime and threat intel
Korean perv sent to prison: South Korean authorities have sentenced a 28-year-old to four years in prison for hacking internet-connected security cameras and recording 7,092 videos of women in their homes, including while naked and when having intercourse. The hacks took place between May 2021 and February 2022, and the suspect's activities were discovered after selling some of the videos online.
New wave of DeadBolt ransomware attacks: As of last week, the QNAP forums have been filling up with new complaints of NAS devices getting encrypted with the DeadBolt ransomware. The company's NAS devices has been hit by this new ransomware in several waves in January, March, May, and June this year as well. QNAP NAS devices have also been hit by the ech0raix and Checkmate ransomware strains this year as well.
EvilProxy: Resecurity's research team published a report last Friday on EvilProxy (aka Moloch), a new phishing-as-a-service (PhaaS) advertised in the cybercrime underground. According to the research team, EvilProxy is part of a new wave of phishing services that use an AitM model of reverse proxies and cookie injection capabilities to bypass MFA protections.
Raspberry Robin malware: The Raspberry Robin, a worm that spreads via infected USB devices, has been making waves over the past few months, infecting a large number of Windows systems [1, 2, 3]. According to a series of tweets from Deutsche Telekom's security team, several of these infections have been traced back to users who used their USB thumb drives at print copy stores, a likely source of infection for many users in corporate environments and a cautionary tale against visiting one of these stores using your USB thumb drive these days.
In many cases, we had a chance to talk to the affected user. Independently of each other, every user reported to have used the USB stick for printing in print/copy stores🖨️. 🧵 4/12
— Deutsche Telekom CERT (@DTCERT) 11:36 AM ∙ Sep 2, 2022
Malware technical reports
SharkBot back in the Play Store: Fox-IT researchers said they found at least two Android applications that made it on the official Google Play Store that were infected with the SharkBot malware dropper.
CodeRAT: A SafeBreach report takes a deep dive into CodeRAT, a new remote access trojan that was open-sourced on GitHub after the company identified and confronted the malware's creator. An interesting feature of this new malware is that instead of using a classic C&C control web server, CodeRAT uses a public anonymous file upload API instead (i.e., AnonFile).
Redeemer ransomware: India-based security company CloudSEK published a report on Friday on Redeemer, a new ransomware strain advertised on cybercrime forums like Dread and Breached by a threat actor named Cerebrate. One of this ransomware's stand-out features is the fact that it requires payments to be made in Monero instead of Bitcoin.
Vice Society: Sygnia researchers have published a report from a recent IR engagement where they had to deal with the aftermath of an attack carried out by Vice Society; a ransomware group known to use the Zeppelin ransomware to encrypt Windows systems and the HelloKitty ransomware for Linux systems.
PLAY (PlayCrypt) ransomware: Georgia Tech CS student Chuong Dong published an analysis of PLAY (PlayCrypt), a new ransomware strain spotted in attacks since mid-July this year. This ransomware strain made headlines in mid-August when it was used in an attack against Argentina's Judiciary of Córdoba.
APTs and cyber-espionage
BumbleBee: Trend Micro has a report out on the Bumblebee backdoor trojan. This is different from the recent BumbleBee malware loader.
This type of backdoor is similar to another of its kind called BookWorm, in which it can be inferred that BumbleBee is a refactored version of BookWorm. At the time of writing, BumbleBee has only been deployed in Taiwan; together with its use of Simplified Chinese as the language for its user interface, this malware can be suspected to be deployed by malicious Chinese actors
Vulnerabilities and bug bounty
Chrome zero-day: Google released Chrome v105.0.5195.102 late Friday to address an actively-exploited zero-day vulnerability (tracked as CVE-2022-3075).
Unisoc vulnerabilities: NCC Group researchers have published a write-up on a series of vulnerabilities they discovered in Unisoc (formerly Spreadtrum), a vendor for SoC boards for modern smartphones.
CSRF flaw in anti-CSRF library: Researchers from security company Fortbridge said they found a CSRF vulnerability in Csurf, an npm library to protect applications against CSRF attacks. Since the project had not been maintained for almost two years, as a result of this bug report, the project's authors decided to mark Csurf as "vulnerable & deprecated." [Additional coverage in PortSwigger]
Infosec industry
Passkeys: A video from July, but still a great video demo on "passkeys" and how they work for those who need a simple explanation that doesn't involve reading FIDO Alliance standards. Passkeys will be coming to most of your devices in the next few years, so you better learn about them and how they work now.




