Risky Biz News: Ebury botnet compromises entire ISPs and hosting providers
In other news: UK announces Share and Defend project; Helsinki discloses data breach; new RFDoS attack targets WAFs.

This newsletter is brought to you by Okta. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Breaches, hacks, and security incidents
Lazarus breach: South Korea's intelligence agency NIS says North Korean hackers stole over 1,000 GB worth of data and documents from the country's court computer network. The intrusion took place between January 2021 and February 2023 and impacted the IT network of the Seoul court. Officials linked the hack to the Lazarus Group APT. [Additional coverage in Yonhap]
BC breach: The government of Canada's British Columbia province says a recent security breach is the work of a foreign state-backed threat actor. [Additional coverage in CBC]
Helsinki breach: The City of Helsinki in Finland has disclosed a data breach of its Education Division. The hack took place at the end of April through a vulnerability in a remote access server. Helsinki officials say the intruder gained access to files and personal data of both students and city education personnel. Officials say some of the stolen files contain sensitive information.
Santander breach: The Santander banking group says a threat actor accessed the personal information of some of its customers. The breach impacted a database hosted by a third-party provider. The bank says the threat actor accessed data on its customers and employees in Spain, Chile, and Uruguay. Santander says the database did not hold any information that could permit financial transactions. [Additional coverage in Reuters]
More Victory Day TV hacking: Just as pro-Kremlin hackers were hijacking TV signals in Latvia and Ukraine to broadcast Putin's Victory Day (May 9) speech and Russian propaganda, anti-Kremlin hackers were hijacking TV signals of Russian TV stations to broadcast anti-war propaganda. [Additional coverage in Dagens]
General tech and privacy
Apple, Google block unwanted trackers: Apple and Google have released updates to iOS and Android this week with a new security feature to warn users about unauthorized Bluetooth trackers in their vicinity. The new feature works by showing an alert that reads "[Item] Found Moving With You" if a Bluetooth device is consistently following a user's phone. Apple added the new alert system to iOS 17.5, and Google backported the functionality to all Android 6.0 and later devices.
Apple Web Eraser: Apple is adding a new ad-blocking tool called Web Eraser to its Safari browser. The tool is AI-powered, and news orgs are already panicking that it will put a dent in their revenue. [Additional coverage in PYMNTS]
Free VMware apps: Broadcom has introduced free for personal use licenses to its Fusion Pro and Workstation Pro virtualization tools.
AWS S3 price changes: Amazon says it will stop charging S3 customers for the traffic linked to some server errors. The new price change applies only to 3xx and 4xx server error messages triggered by outside requests. The company's move comes after a customer reported a huge bill after their S3 bucket was flooded with web traffic that triggered millions of server error messages.
KeePassXC update: The maintainers of the KeePassXC Debian package have removed all networking features from the app to avoid security issues. A full version of the KeePassXC password manager is now available under the name "keepassxc-full."
Elsag EOC Plus: Forbes' Thomas Brewster has published a profile of Elsag EOC Plus, a new tool that can fingerprint drivers and passengers by scanning for anything that emits a signal from a car. The tool was developed by Italian defense contractor Leonardo and is currently marketed to law enforcement agencies, typically together with the company's license plate reader tech.
AI content on TikTok: TikTok says it will automatically label all AI-generated content on its platform.
Attacks on Signal: Right-wing news outlets, Telegram CEO Pavel Durov, Elon Musk, the blockchain ecosystem, and Russian troll farms are mounting a campaign to convince everyone that Telegram is more secure than Signal. It's too bad that actual cryptographers are on hand to explain the stupidity of all their claims. Definitely not a coordinated attack [eyeroll].
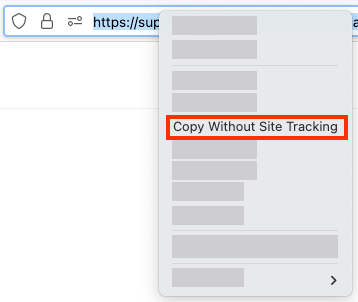
Firefox 126: Mozilla has released Firefox 126. New features and security fixes are included. The biggest change is support for the "Copy Without Site Tracking" option in the URL bar and the new ZSTD content encoding scheme. Mozilla says the new version also collects anonymized search data from Firefox US desktop users.
Government, politics, and policy
CISA guide for civil society members: CISA and nine other government agencies have published a guide on how members of the civil society can mitigate cyber threats with limited resources at their disposal.
Vermont privacy bill: The US state of Vermont passed a privacy bill last week. The new law has been described as one of the toughest in the US. It includes language to allow consumers to sue companies for violating their privacy. [Additional coverage in The Record]
The FTC is watching auto-makers: The US Federal Trade Commission has published a veiled warning in a blog post this week aimed at US automakers. The agency says it's closely watching how companies collect and use data from their cars. The FTC says it's ready to bring cases against automakers and other businesses that fail to protect car and driver data or abuse the information. [Additional coverage in The Record]
UK NCSC Share and Defend: The UK's cybersecurity agency will work with local ISPs as part of a new project named Share and Defend to block access to malicious websites. The UK NCSC says it will create blocklists of malicious sites using data from threat intelligence and security vendors. The agency will then share this data with local ISPs to block their customers from accessing any of the websites. The blocklist will primarily contain links to known phishing, fraud, and malware sites.
UK recommends not paying ransoms: The UK's cybersecurity agency has published new guidance and is now officially recommending that victims of ransomware attacks not pay ransom demands. The NCSC worked on the new guidance with three of the UK's insurance industry bodies (ABI, BIBA, and IUA). The guide recommends that victims leave a paper trail of their decision, involving authorities, and consider that payment won't guarantee data privacy or recovery. The three insurance industry bodies have pledged to help the NCSC to reduce the number of payments and promote alternatives to payment.
"The NCSC does not encourage, endorse or condone paying ransoms, and it's a dangerous misconception that doing so will make an incident go away or free victims of any future headaches. In fact, every ransom that is paid signals to criminals that these attacks bear fruit and are worth doing."
Sponsor section
In this Risky Business News sponsored interview, Adam Boileau talks to Okta's Cassio Sampaio about how cloud-native applications can move authorization into a centralized model. This brings real benefits for consistency, control, and auditing in distributed applications beyond just the authentication part Okta is normally known for.

Cybercrime and threat intel
Tornado Cash developer sentenced: Dutch authorities have sentenced a Russian national to five years and four months in prison on money laundering charges. Officials say Alexey Pertsev worked with two other Russian nationals to develop and operate the Tornado Cash crypto-mixing platform. Criminal organizations and cybercrime groups abused the platform to launder more than $2 billion worth of cryptocurrency. Pertsev was arrested in August 2022, days after the US sanctioned the Tornado Cash platform. The sentence is exactly what the prosecution requested last month.
LockBitSupp past: Infosec reporter Brian Krebs has gone dumpster-diving into the past life of Dmitry Yuryevich Khoroshev, the Russian national accused by US authorities of being LockBitSupp, the leader of the LockBit ransomware. Krebs' investigation found a trail linking Khoroshev to malware and cybercrime forums for almost 14 years.
"Does the above timeline prove that NeroWolfe/Khoroshev is LockBitSupp? No. However, it does indicate Khoroshev was for many years deeply invested in countless schemes involving botnets, stolen data, and malware he wrote that others used to great effect. NeroWolfe’s many private messages from fellow forum members confirm this."
Scam revenue estimates: The US Institute of Peace estimates that cybercrime groups based in Southeast Asia are making around $64 billion per year from online scams. Most of the gangs are from China, but they base their operations mostly in Myanmar, Cambodia, and Laos. Researchers say there's evidence to suggest that some groups receive political protections in some countries, such as Myanmar and Cambodia, because of their profitability.
"The criminal groups masterminding these scams have set up complex money-laundering operations to move funds into the formal economy, risking corruption of major international financial institutions."
Royal Tiger: The FCC has designated a company group named Royal Tiger as a "repeat robocall bad actor" in the company's first Consumer Communications Information Services Threat (C-CIST) security alert.
Estate PhaaS leak: The Estate phishing-as-a-service operation has misconfigured a database and leaked information on its owner and operations. The service allows threat actors to obtain 2FA codes from users who had compromised accounts. Two security researchers found the server and shared the data with TechCrunch. According to the news outlet, the Estate platform launched in mid-2023, launched over 90,000 attacks, and was created by a Danish programmer in their early 20s.
New DNS tunneling abuse: Palo Alto Networks says it detected threat actors using DNS tunneling to scan victims' networks and gather information for future attacks. The technique is novel, as threat actors previously used DNS tunneling for C2 traffic and data exfiltration. Researchers say they've spotted at least two campaigns named TrkCdn and SecShow abusing the new technique already.
Trik campaign: A threat actor is using the Trik (Phorpiex) botnet to distribute custom-made versions of the LockBit ransomware. The threat actor has been linked to several spam waves delivering the ransomware inside malicious ZIP attachments, according to Proofpoint and the NJCCIC. The campaign is not linked to the LockBit group and is just using an older leaked version of the ransomware.
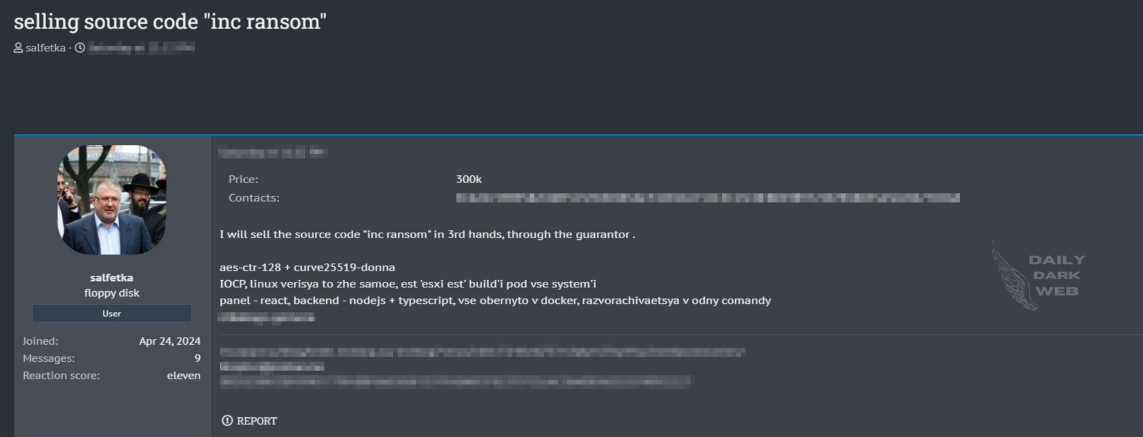
INC ransomware code sold online: A threat actor is claiming to sell the source code of the INC RaaS for a whopping price of $300,000. [Additional coverage in DailyDarkWeb]
"Allegedly, while the user interface of the software is developed using React, the backend is built with Node.js and TypeScript. All components are packaged in Docker containers and can be deployed with a single command."
GoTo campaign: G DATA has published details about a malspam campaign that uses malicious versions of the GoTo Meeting client to infect targets with malware.
MS-SQL campaign: Sekoia has published details on a brute-force campaign targeting MS-SQL databases and deploying the Mallox ransomware.
GitCaught campaign: Recorded Future has discovered a Russian-speaking threat actor using GitHub to impersonate and host malicious versions of popular software infected with malware. Mimicked apps include 1Password, Bartender, Parallels Desktop, Figma, and Pixelmator. The final payload is either Vidar, Lumma, Octo, or AMOS, depending on the targeted platform, Windows, or macOS.
FoxIT exploitation: Check Point looks at all the malware campaigns abusing vulnerabilities in the FoxIT PDF reader. It's quite a lot.
Copyright violations campaign leads to ransomware: AhnLab has spotted a malspam campaign using alleged copyright violations to trick victims into infecting themselves with the Vidar infostealer and Beast ransomware.
Malvertising campaign leads to ransomware: Rapid7 has published a report on a malvertising campaign that delivers various sorts of malware, including ransomware.
"The related techniques, tactics, and procedures (TTP) observed by Rapid7 are reminiscent of past BlackCat/ALPHV campaigns as reported by Trend Micro last year. This campaign, referred to as Nitrogen by Malwarebytes, and eSentire, has previously been reported to use similar methods."
DDoS attacks on Australia: Pro-Russian hacktivist groups have now started launching DDoS attacks against Australian sites, their largest and most sustained campaign aimed at Australia so far, according to CyberKnow.
The LinkedIn recruitment ruse: The US Air Force's Air University has published a paper looking at the various tactics used by threat actors to recruit US military defense insiders via LinkedIn.
"In conclusion, LinkedIn espionage poses a significant threat to national security. Virtual espionage is characterized by its low cost and risk, as it bypasses traditional clandestine officer training requirements such as weapons training and specialized communication techniques. This is because LinkedIn provides a platform for attempting to recruit foreign nationals to steal secrets without the need for such training. Moreover, LinkedIn espionage eliminates the risk of these virtual intelligence officers being apprehended in foreign territory. The extent of this problem, as highlighted by US and other Western government officials, demands increased attention and action from policy makers, the DOD, and the defense industrial base to safeguard the resilience of both former and current DOD members."
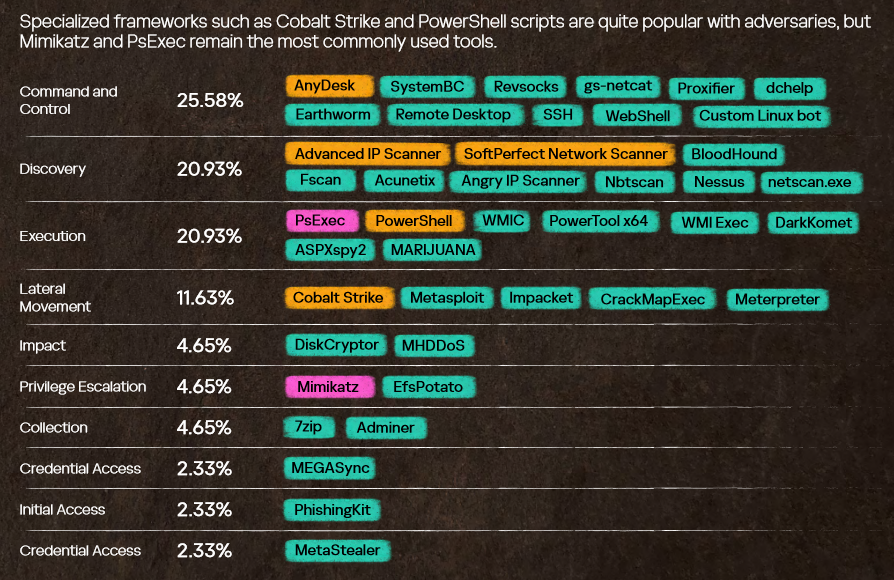
Threat/trend reports: Avast, the Canadian Security Intelligence Service, Dr.Web, ESET, Kaspersky, LayerX, Marsh, Tenable, and Trustwave have recently published reports covering infosec industry threats and trends.
Malware technical reports
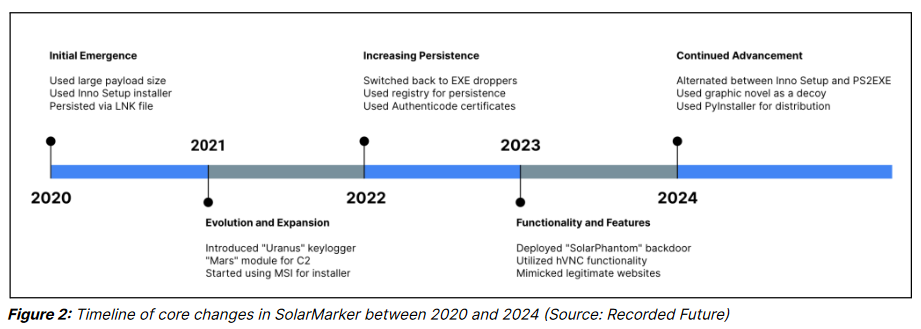
SolarMarker malware family: Recorded Future has published a history of the SolarMarker infostealer malware family, which includes the likes of SolarMarker, Jupyter, Uranus, Mars, and SolarPhantom.
Black Basta: Intel-Ops shows how to track the Black Basta ransomware gang's Cobalt Strike command and control servers in the wild.
Creal Stealer: OALABS covers Creal Stealer, a new infostealer advertised via Telegram.
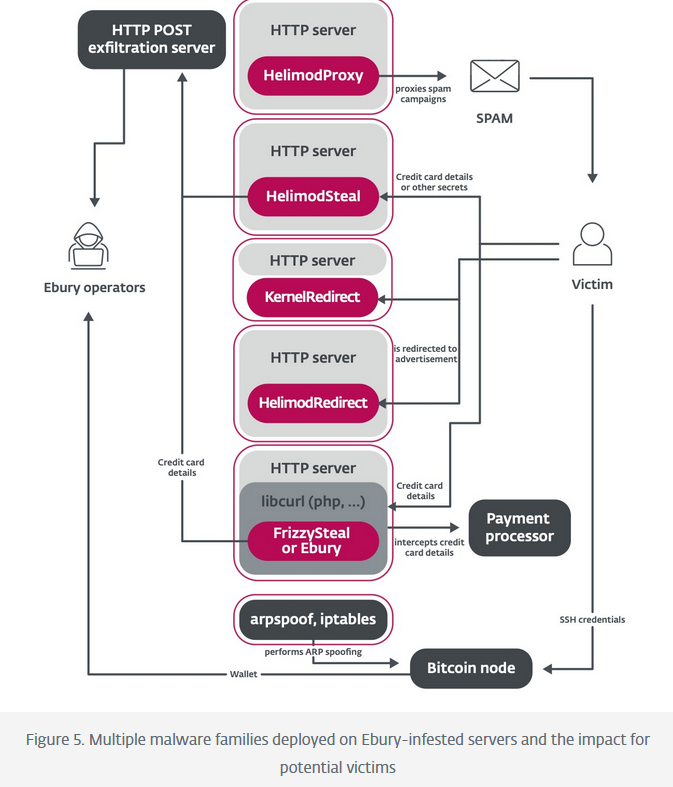
Ebury botnet: Security firm ESET says that 15 years after it launched, the Ebury botnet is still operating and installed on more than 100,000 Linux and *NIX servers. The botnet is currently being used to spread spam, perform web traffic redirections, and steal credentials. It was recently modified to also plant web skimmer malware to steal payment card details, and perform AitM attacks to steal SSH credentials and crypto-wallet keys. ESET says Ebury operators are also selling access to infected hosts as part of initial access schemes. Recent Ebury attacks involved the use of zero-days in administrator software to compromise servers in bulk. Some Ebury campaigns gained full access to large ISPs and well-known hosting providers. The group also hacked the server infrastructure and stole data from other cybercrime crews.
Sponsor Section
In this video, Okta demonstrates how you can enforce zero standing privileges for sensitive admin access to an Okta environment with access requests and approvals.
APTs, cyber-espionage, and info-ops
Lazarus: Security researcher Dmitry Bestuzhev has published a report on one of Lazarus' campaigns targeting blockchain developers.
PhantomCore APT: Russian security firm FACCT has published a report on PhantomDL, a malware downloader used by PhantomCore, a group the company previously linked to Ukraine.
APT AI use: Novartis security researcher Rachel James is keeping track of all the APT groups and their use of AI tools.
CeranaKeeper: In its quarterly APT activity report, ESET says it spotted a new Chinese APT group in the wild that the company named CeranaKeeper.
"Based on the data leak from I-SOON (Anxun), we can confirm that this Chinese contractor is indeed engaged in cyberespionage. We track a part of the company’s activities under the FishMonger group. In this report, we also introduce a new China-aligned APT group, CeranaKeeper, distinguished by unique traits yet possibly sharing a digital quartermaster with the Mustang Panda group."
Vulnerabilities, security research, and bug bounty
Patch Tuesday: Yesterday was the May 2024 Patch Tuesday. We had security updates from Adobe, Apple, Microsoft, SAP, VMware, Fortinet, Google Chrome, Firefox, Intel, Git, Schneider Electric, Siemens, Cacti, and Zoom. The Android Project, Kubernetes, Cisco, F5, JetBrains, NVIDIA, and Veeam released security updates last week as well. This month, Microsoft patched 67 vulnerabilities, two zero-days.
- CVE-2024-30040 - Windows MSHTML Platform Security Feature Bypass Vulnerability;
- CVE-2024-30051 - Windows DWM Core Library Elevation of Privilege Vulnerability (Kaspersky linked this zero-day to the Qakbot botnet).
Chrome 6th zero-day: Google has released an update for its Chrome browser to fix a zero-day (CVE-2024-4761) exploited in the wild. The zero-day is a vulnerability in Chrome's V8 JavaScript engine. This is the sixth Chrome zero-day patched this year. It comes days after Google patched another Chrome zero-day (CVE-2024-4671).
RFDoS attack: Sicuranext researcher Andrea Menin has discovered a new denial of service attack that impacts websites protected by a web application firewall (WAF). The technique is called Response Filter Denial of Service (RFDoS) and leverages an attacker’s ability to post content such as comments or reviews to trick a WAF into blocking the server it’s meant to be protecting. The firewall’s behavior is intended to detect SQL injection or other verbose debug messages, but can be abused to cause denial of service.
Infosec industry
New tool—Fiddleitm: Malwarebytes' Jérôme Segura has released Fiddleitm, a tool to analyze malicious web traffic using the mitmproxy tool.
New tool—IconJector: Security researcher 0xda568 has published IconJector, a tool to perform DLL injections using the change icon dialog on Windows.
New tool—wayback-keyword-search: Software engineer Lorenzo Romani has released wayback-keyword-search, a tool that can download web snapshots from the Wayback Machine and search for specific keywords inside the pages.
CYBERUK 2024: Talks and live streams from the UK NCSC's CYBERUK 2024 security conference, which took place this week, are available on YouTube.
Risky Business Podcasts
The regular two nerds have the week off, but the former Director of the CIA's Center for Cyber Intelligence Andy Boyd joins Patrick Gray for a rollicking conversation in front of a live audience in San Francisco. Grugq and Tom return next week!




