Risky Biz News: Dutch government to physically replace tens of thousands of hackable traffic lights
In other news: Mozilla patches Firefox zero-day; hackers leak data of 31 million Internet Archive users; Chinese APT targets OpenAI employees.

This newsletter is brought to you by application allow-listing software maker Airlock Digital. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Spotify:
Dutch authorities will have to replace tens of thousands of insecure road traffic lights over the next six years by 2030.
Officials are taking this extreme and very expensive step after a security researcher found a vulnerability that could allow threat actors to change traffic lights on demand.
The issue was discovered earlier this year by Alwin Peppels, a security engineer for Dutch security firm Cyber Seals.
Peppels says threat actors can use a software-defined radio to send commands to the control boxes that sit next to traffic lights.
The exploit taps into an emergency radio signal used by ambulances and fire trucks to force traffic lights to go green so they can easily pass through intersections in the case of emergencies.
An attack could be executed from kilometers away and impact multiple intersections at once.
Details about the vulnerability were shared with the Dutch cybersecurity agency (NCSC) and have been shared publicly in a closed circle at the agency's security conference last week.
According to RTL Nieuws, the government has tasked local road authorities with the task of slowly replacing and phasing out its current vulnerable system.
Breaches, hacks, and security incidents
NPD files for bankruptcy: National Public Data has filed for bankruptcy in Florida after the company suffered a catastrophic security breach in August that exposed the personal details of hundreds of millions of users. [Additional coverage in PCMag] [h/t DataBreaches.net]
Volkswagen incident: The 8base ransomware gang has listed Volkswagen on its leak site. Unconfirmed incident, at the time of publishing.
Dr.Web denies leak: Russian security firm Dr.Web has denied that customer data was obtained in a hack last month. The company put out the statement after a threat actor named DumpForums took credit for the hack and advertised the company's data.
Muah.AI breach: Hackers have leaked the database of Muah.AI, a website that generates AI girlfriends. The leaked database exposed personal details and sexual fantasies of almost 2 million customers. According to 404 Media, some users used the site to generate CSAM.
FTC fines Marriott over data breach: The Marriott hotel chain has agreed to pay a $52 million civil penalty to 49 US states in a settlement with the FTC over its 2014 and 2020 data breaches. The two breaches exposed the personal and travel records of over 344 million customers from across the world. Marriott and its subsidiary Starwood Hotels & Resorts will also be required to implement a robust information security program. The company will also have to review customer accounts, restore stolen loyalty points, and provide customers with a way to delete their data from its database.
Pravosodye cyberattack: Ukraine's military intelligence agency GUR has allegedly conducted a cyberattack that disrupted the central IT system used by Russia's courts and judicial system. According to Ukrainian media, the GUR worked together with a hacktivist group named the BO Team. The group claims it wiped servers, including backups. Russian authorities confirmed the incident and the fact they couldn't restore systems. Officials say a new system will go live on October 18, eleven days after the initial hack. [Additional coverage in Online.ua]
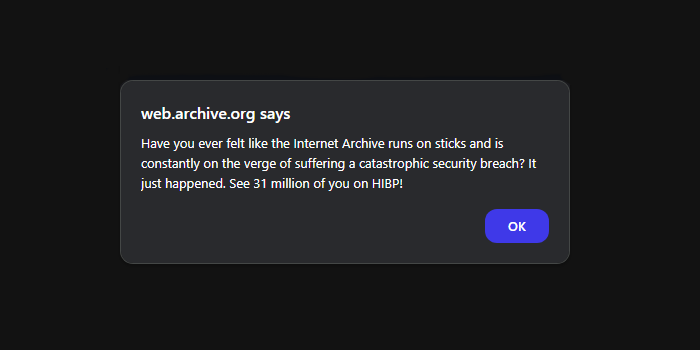
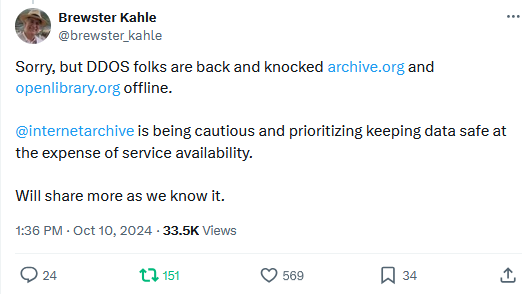
Internet Archive hacked: A pro-Kremlin hacker group has hacked and leaked the data of 31 million users of the Internet Archive. The hack took place last week, and the stolen data has been shared with the Have I Been Pwned platform. The SN_BLACKMETA group continued to pummel the site with DDoS attacks throughout the week. [Additional coverage in CyberDaily]
General tech and privacy
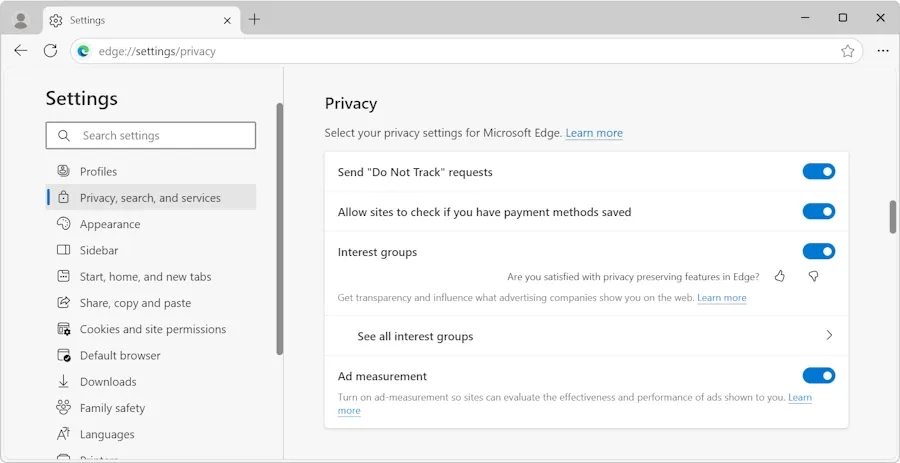
MS Edge adopts new Google ad tech: Microsoft will add support for Google's new Privacy-Preserving Ads API technology in its Edge web browser. The API will be supported in a limited test.
Passkeys on Windows: Microsoft has announced new passkeys support for Windows 11. This includes a plugin system to support third-party passkey providers, native UI support for handling passkey authentication, and the ability to sync passkeys via a Microsoft service.
PPTP and L2TP deprecation: Microsoft is deprecating the Point-to-Point Tunneling Protocol (PPTP) and Layer 2 Tunneling Protocol (L2TP) from future versions of Windows Server. Windows Server 2025 will be the last version of the OS to support the two protocols. Microsoft has asked organizations to start migrating to newer traffic tunneling protocols such as SSTP and IKEv2.
Meta moderation snafu: Multiple Instagram and Threads users have reported that their accounts have been restricted or plain-out deleted in what appears to be some sort of error in Meta's moderation systems. [Additional coverage in The Verge]
Samsung security updates: Galaxy has stopped providing security updates for smartphones launched in 2020, such as the Galaxy Z Fold 2 and Tab A7. [Additional coverage in Android Headlines]
Twitter fails to remove nudity: An academic study found that Twitter typically removes all copyright infringement images within 25 hours of a report, while non-consensual nudity is still live on the platform for three weeks or more. tl;dr: If someone posts nude photos of you on Twitter, just report it as copyright infringement.
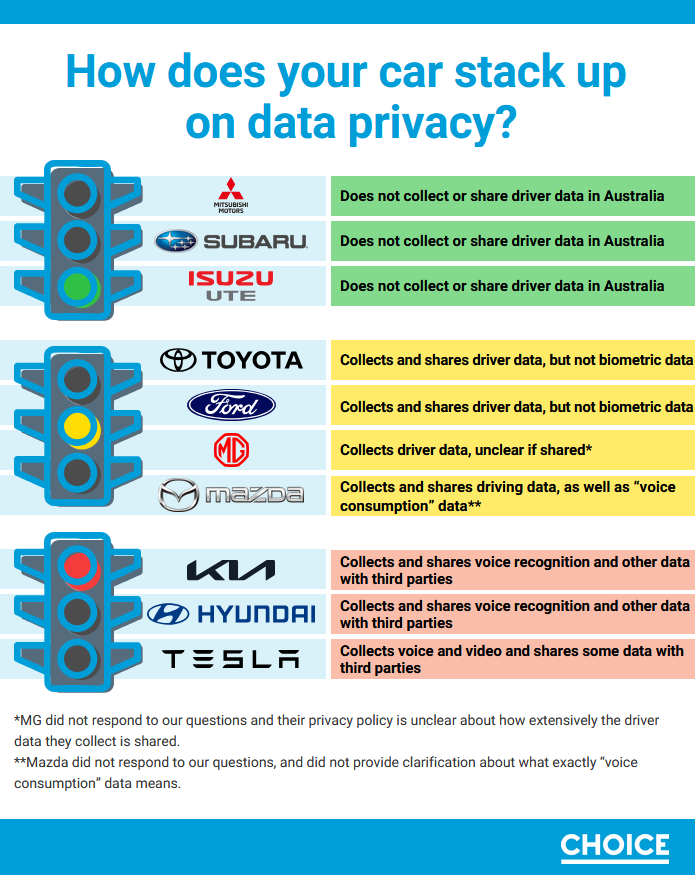
Car privacy research: Privacy experts in Australia are using the results of a recent car privacy study to call for better protections for car owners. A recent Choice study found that 7 out of the 10 car brands collect and share driving data with third-party companies. [Additional coverage in the ABC]
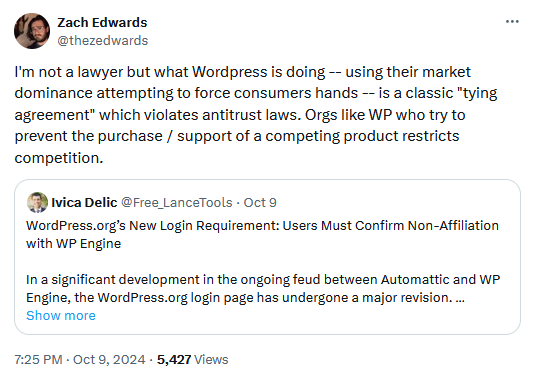
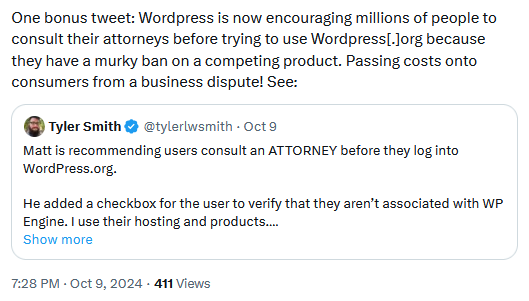
More WordPress drama: The dispute between Automattic and WP Engine is still going on. Through its control over the WordPress.org project, Automattic has added a checkbox on the WordPress.org website to force users to disclose if they're affiliated with WP Engine—a competitor for Automattic's WordPress.com paid WordPress hosting service. When users complained about the murky checkbox, Automattic CEO and WordPress creator Matt Mullenweg told users to consult their lawyers. Best showcase of antitrust abuse and market dominance you'll see these days online.
Government, politics, and policy
Iran election alert: CISA and the FBI have published another alert warning that Iranian hackers may try to undermine confidence in next month's US Presidential Election.
Russia and Türkiye ban Discord: Internet watchdogs in Russia and Türkiye have blocked access to the Discord social media platform. Turkish officials banned the platform after Discord refused to hand over user data in a criminal investigation. Officials claimed the platform was hosting obscenity and CSAM. Russia's Roskomnadzor claimed Discord was hosting terrorist and extremist content. Officials say the platform failed to remove more than 1,000 pieces of content—most likely related to its invasion of Ukraine. Russia's military and Parliament criticized Roskomnadzor's Discord ban. The Army had been using Discord to coordinate troop movements, and the app is also widely used by schools.
Steam ban in Russia incoming: In the meantime, there are rumors that Russian officials are preparing to block the Steam gaming platform. Seven complaints were filed with the Roskomnadzor against Steam in a single day. According to local bloggers, no other Western platform received so many complaints in a day before.
Russia linked to 80% influence ops in Europe: Speaking at a conference about foreign influence operations, Czech Foreign Minister Jan Lipavský says that Russia is responsible for 80% of foreign influence operations currently taking place across Europe.
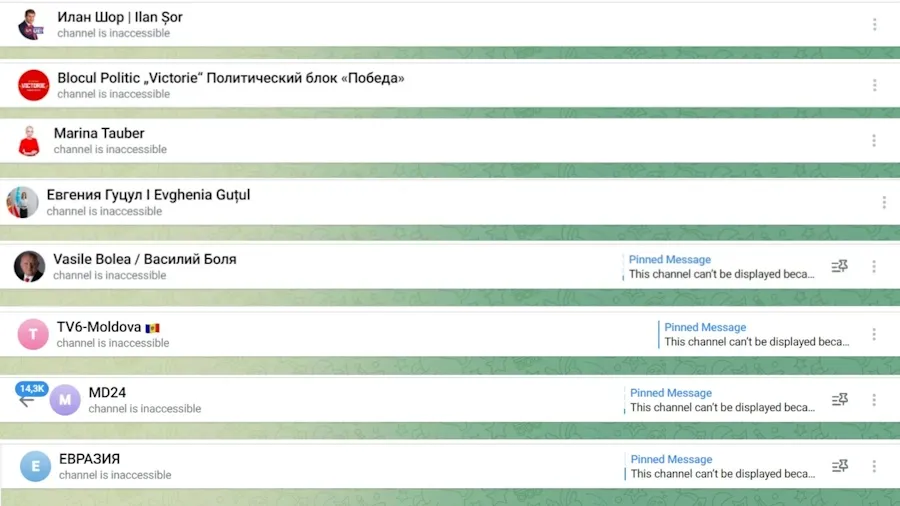
Telegram blocks some Moldavian channels: Telegram has suspended the channels of several Moldavian pro-Kremlin politicians. The channels are inaccessible across Moldova and the EU. The ban impacts Ilan Șor, a controversial Moldavian political figure, and several of his allies. Șor is a Moldavian businessman who fled Moldova after he was charged in a massive fraud case. He is the leader of a pro-Kremlin political party that tried to organize violent protests in Moldova in 2023. Șor is also sanctioned by the EU and the US. The Telegram channel ban comes ten days before Moldova is set to hold new presidential elections and a referendum to join the EU. Some of the channels were used to peddle Russian disinformation and conspiracy theories about the EU. In 2022, Moldova passed an anti-disinformation law but authorities have not confirmed that they used it in this case to take down the channels. [Additional coverage in TV8]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Airlock Digital founders Daniel Schell and David Cottingham about other things Microsoft can do to secure and harden Windows.

Cybercrime and threat intel
Ransomware negotiator trial in France: Le Monde has published a profile on Florent Curtet, a French cybersecurity expert who served as a ransomware negotiator for the Everest gang. He is currently on trial in France.
Crypto market manipulators charged: The US government has indicted four companies and 18 individuals for their involvement in a scheme to manipulate cryptocurrency markets. The group created crypto tokens, engaged in wash trading to boost their value, and then sold the tokens in pump-and-dump schemes. The FBI caught the group after it created its own token and contracted the companies to boost its value. Seven of the 18 suspects have been arrested, and four have already pleaded guilty.
Suspect's parents get kidnapped: Infosec reporter Brian Krebs has published a wild story on how the parents of a teen who stole $243 million cryptocurrency from a Gemini customer in August got car-jacked and then kidnapped while shopping for a new house in a new Lamborghini.
GitHub comments abuse: Cofense looks at a malspam campaign that abused GitHub comments to deliver the Remcos RAT.
"GitHub was used to deliver malware from trusted repositories, but the malware existed outside of the repository's code. The trusted repositories that were abused were affiliated with legitimate tax organizations."
QR phishing in San Francisco: The San Francisco Municipal Transportation Agency has warned drivers to be vigilant when scanning QR codes to pay for parking. The organization says it found malicious QR code stickers placed on five parking meters across the city. Drivers who scanned the QR codes made payments via fake payment portals. The warning comes two months after the UK Royal Automobile Club issued a similar warning for British drivers.

Malware technical reports
LemonDuck: NetbyteSEC has published a report on the LemonDuck crypto-mining malware, including its recent use of the EternalBlue exploit.
Mongolian web skimmer: JScrambler researchers have published a report on a new web skimmer that used Mongolian Unicode characters to hide malicious behavior on e-commerce sites.
AsyncRAT: G Data has published a report on AsyncRAT and its recent abuse of the Bitbucket platform.
DarkVision RAT: Zscaler has published a report on the old DarkVision RAT, a rentable remote access trojan that's been available on the market since 2020.
IMEEX Framework: Intezer looks at the IMEEX Framework, a new malware toolkit that targets Windows systems. So far, IMEEX samples were found on VirusTotal submitted only from Djibouti and Afghanistan. Intezer says there's weak connections tying the malware to past Chinese APT samples, but that's not enough for any kind of attribution.
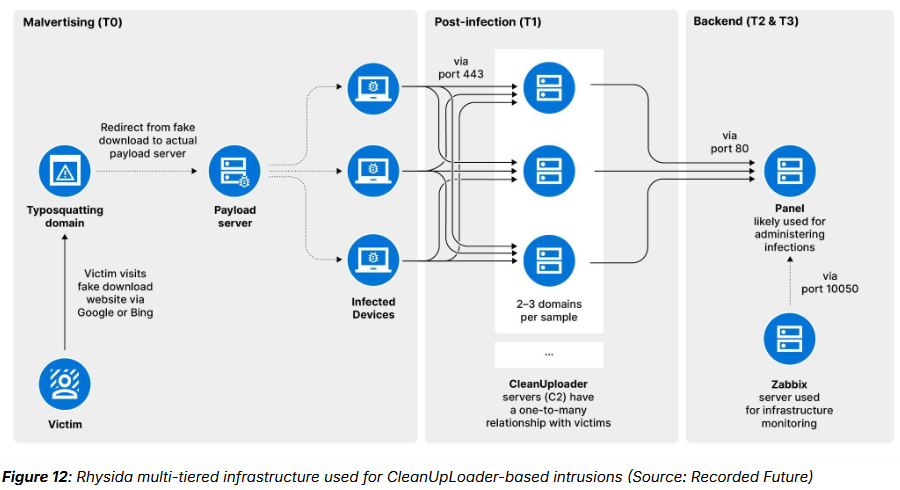
Rhysida's new CleanUpLoader: Threat intel firm Recorded Future has published a report on new infrastructure operated by the Rhysida ransomware gang. The company says that discovering this infrastructure allowed it to detect attacks around 30 days before victims would be listed on the group's leak site. The new infrastructure was primarily used to host typosquatted domains employed in SERP poisoning attacks. The main payload before the actual ransomware was a new backdoor named CleanUpLoader.
Sponsor Section
David Cottingham, CEO of Airlock Digital, shows Patrick how Airlock's execution control and allowlisting solution works.
APTs, cyber-espionage, and info-ops
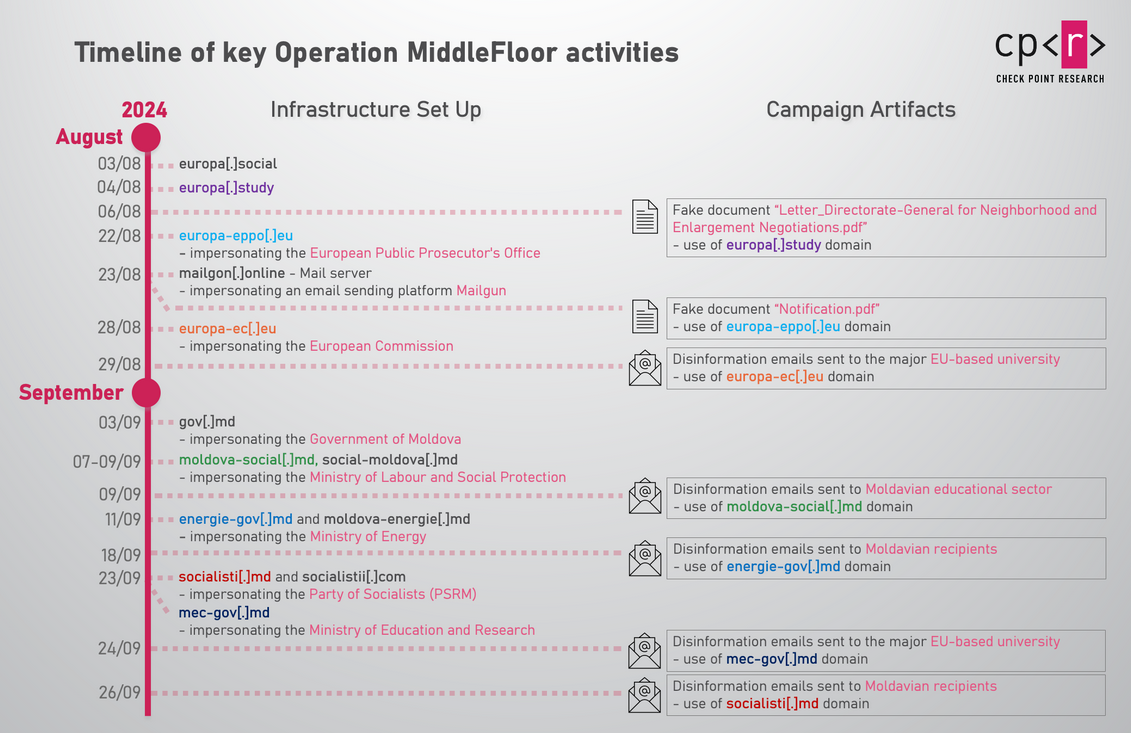
Operation MiddleFloor: A Russian-speaking threat actor is behind a major disinformation campaign targeting Moldova's election, set to take place later this month. The campaign started in August and is the work of a group known as Lying Pigeon. The campaign is trying to scare and mislead Moldavian citizens about the country's potential EU bid. The operation is unique from other disinfo-ops because it relies on emails to distribute fake documents allegedly originating from EU institutions, Moldavian ministries, or political figures. According to Check Point, the same group was previously involved in disinformation campaigns in Poland, Spain, and the NATO 2023 summit in Vilnius.
Ukraine sentenced two Armageddon members: Ukrainian authorities sentenced in absentia two members of the Armageddon (Gamaredon) APT group to 15 years in prison. Officials say the two suspects conducted more than 5,000 cyberattacks on government agencies and critical infrastructure facilities in Ukraine. Ukraine previously linked the Armageddon group to the Crimean branch of the Russian Federal Security Service, the FSB. Officials say the suspects are two former employees of the SSU Ukrainian intelligence service in Crimea who betrayed their oath and joined the FSB after Russia's invasion in 2014. Their names have not been made public.
APT29: American and British cybersecurity agencies have published a new report on APT29 operations. The report covers new techniques used by the group in recent attacks, such as the group's focus on Zimbra and TeamCity servers.
Core Werewolf (Awaken Likho): Russian security firm BI.ZONE has published a report on renewed attacks against Russian government organizations by an APT group tracked as Core Werewolf. The report comes after a similar one from Kaspersky, which tracks it as Awaken Likho.
Konni: South Korean security firm Igloo has published a report on recent Konni operations targeting the country.
Contagious Interview campaign: PAN's Unit42 looks at another DPRK campaign using fake job interviews to target job seekers in the tech and crypto space. This time, the final payload was the BeaverTail and InvisibleFerret trojans. Unit42 says the campaign is what Group-IB saw earlier this year.
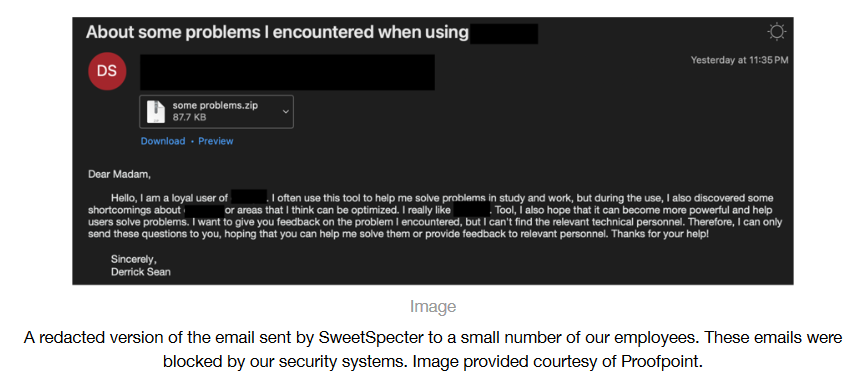
SweetSpecter targets OpenAI: OpenAI has disrupted over 20 operations over the past year that used its infrastructure for malicious purposes. This includes generating text for online disinformation campaigns, asking for help in discovering vulnerabilities, and writing and debugging malware. One of the groups abusing OpenAI's services also tried to phish some of the company's employees on both their personal and work accounts. OpenAI linked the operation to a suspected Chinese group named SweetSpecter. [Additional coverage in CyberScoop]
Vulnerabilities, security research, and bug bounty
PoC for unpatched Linear Emerge E3 vulnerability: Security firm VulnCheck has published a proof-of-concept for an unpatched vulnerability in the Nortek Linear smart door and access control platform. The vulnerability allows remote, unauthenticated attackers to cause the device to execute arbitrary commands. It can be used to unlock access ways and gain access to protected sites. The vulnerability was reported to the vendor more than five months ago and made public at the end of September after Linear failed to patch it. The vulnerability is very likely to be exploited. A Chinese APT named Flax Typhoon previously exploited other Linear vulnerabilities.
Major PAN firewall bug: Palo Alto Networks has patched vulnerabilities in the Expedition customer migration tool that can allow threat actors to steal usernames and cleartext passwords from the company's firewalls. The Expedition tool is typically used to migrate customers from competing products to Palo Alto firewalls. Security firm Horizon3 says the tool continues to store sensitive information from the migration process that can be extracted by attackers. The stolen information can be used to take over Palo Alto firewalls that went through a migration process. One of the five vulnerabilities has received a severity rating of 9.9 out of 10, and researchers say it's trivial to exploit. Palo Alto Networks is recommending that customers change all usernames, passwords, and API keys after applying the recent update. Proof-of-concept code is now available online, and active exploitation is expected to take place.
Invanti Connect Secure RCE: AmberWolf has published a write-up on CVE-2024-37404, a remote code execution in the Ivanti Secure Connect VPN appliance that was patched this week. The company also published a PoC.
AMD attacks: HN Security has published a three-part series on how to exploit the AMD atdcm64a.sys driver.
GitLab security updates: GitLab has released a security update to patch eight vulnerabilities in its enterprise self-hosted platform.
SonicWall security updates: SonicWall has released patches for three vulnerabilities in its SMA appliance.
KeePass security audit: The KeePass password management app has released security updates to patch a series of vulnerabilities found in a security audit paid by Germany's cybersecurity agency, the BSI.
OATH Toolkit vulnerability: The OpenSUSE security team has discovered a vulnerability in the OATH Toolkit, a library for building one-time password authentication systems. Tracked as CVE-2024-47191, the vulnerability can be used to elevate privileges and gain root access to a system. The library's developers rolled out a fix last week.
New Fortinet RCE exploitation: CISA says threat actors are exploiting CVE-2024-23113, an RCE in Fortinet devices that was patched in February this year.
Firefox zero-day: Mozilla has released an update to its Firefox browser to fix an actively exploited zero-day. Tracked as CVE-2024-9680, the zero-day was discovered by security firm ESET. Mozilla says attackers exploited a memory corruption bug in the feature that controls CSS animation timelines to run malicious code in the browser.
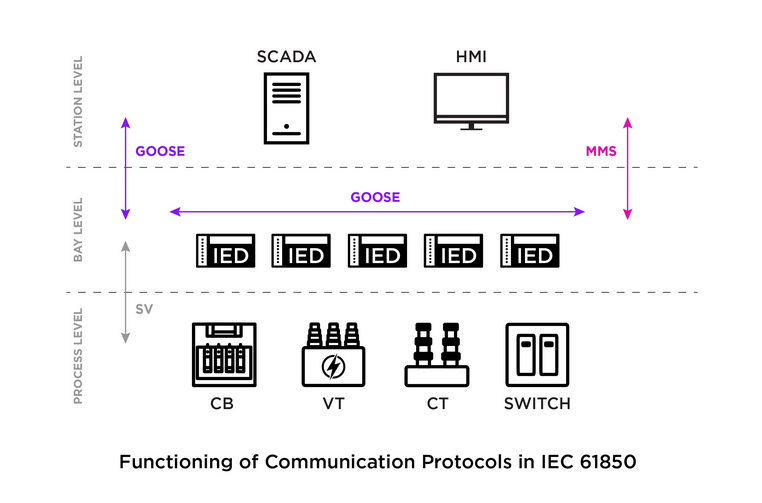
MMS vulnerabilities: Claroty has found five vulnerabilities in the Manufacturing Message Specification (MMS), a protocol used by SCADA devices to exchange information with HMI systems upstream. The vulnerabilities could allow an attacker to crash an industrial device or, in some cases, enable remote code execution. The company says it reported the issues to all affected vectors and their MMS implementations.
Infosec industry
Former Uber CISO lawsuit: Former Uber CISO Joseph Sullivan is seeking a new trial to overturn a 2023 conviction for covering up a data breach. Sullivan was convicted by a jury in 2022 of paying hush money to hackers who stole Uber customer data. The former Uber CISO claims the jury received improper instructions before his conviction. The judge has taken the case under consideration. [Additional coverage in Courthouse News]
New tool—Global Signal Exchange: Google launched Global Signal Exchange, a new platform where tech companies can report and share information on fraud and online scams.
New tool—CUPS-Scanner: Security researcher Marcus Hutchins has released a tool to scan networks for systems vulnerable to the recent CUPS vulnerabilities.
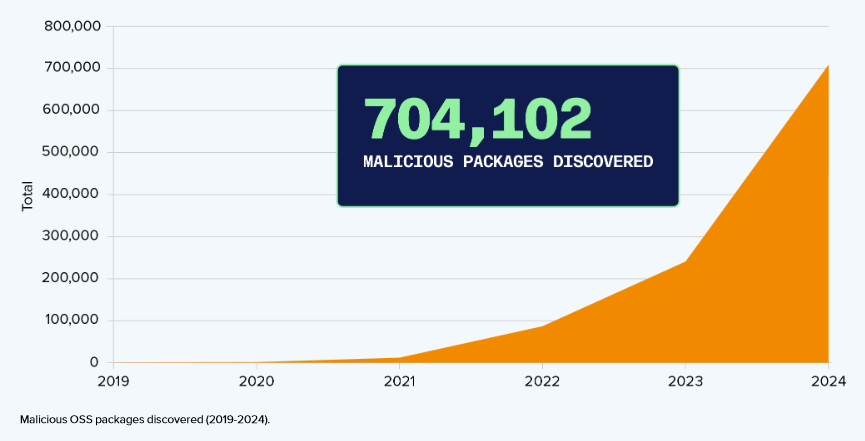
Threat/trend reports: BforeAI, Censys, Coalition, HYPR, Positive Technologies, Sonatype [PDF], and Spamhaus have recently published reports and summaries covering various infosec trends and industry threats. The most interesting report is the Sonatype one, which found a 156% increase in the number of malicious packages year-over-year, reaching more than 700,000 malicious packages identified since 2019.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about 'cyber persistence theory.' They cover what it is, why it is increasingly popular amongst America's allies, why we think the theory is right, and also cover some critiques of the theory.

In this podcast, Tom Uren and Adam Boileau talk about a new UN report that spells out the role Telegram plays as a massive enabler for transnational organized crime. They also discuss China's hacking of US telcos to possibly target lawful intercept equipment and a remarkably entertaining account of North Korean IT workers being employed by over a dozen cryptocurrency firms.

Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!







