Risky Biz News: Disgruntled member doxes and extorts URSNIF gang
In other news: PyPI and npm packages deploy ransomware; Japan wants to carry out preemptive cyber-attacks; Pwn2Own Toronto hacking contest results.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
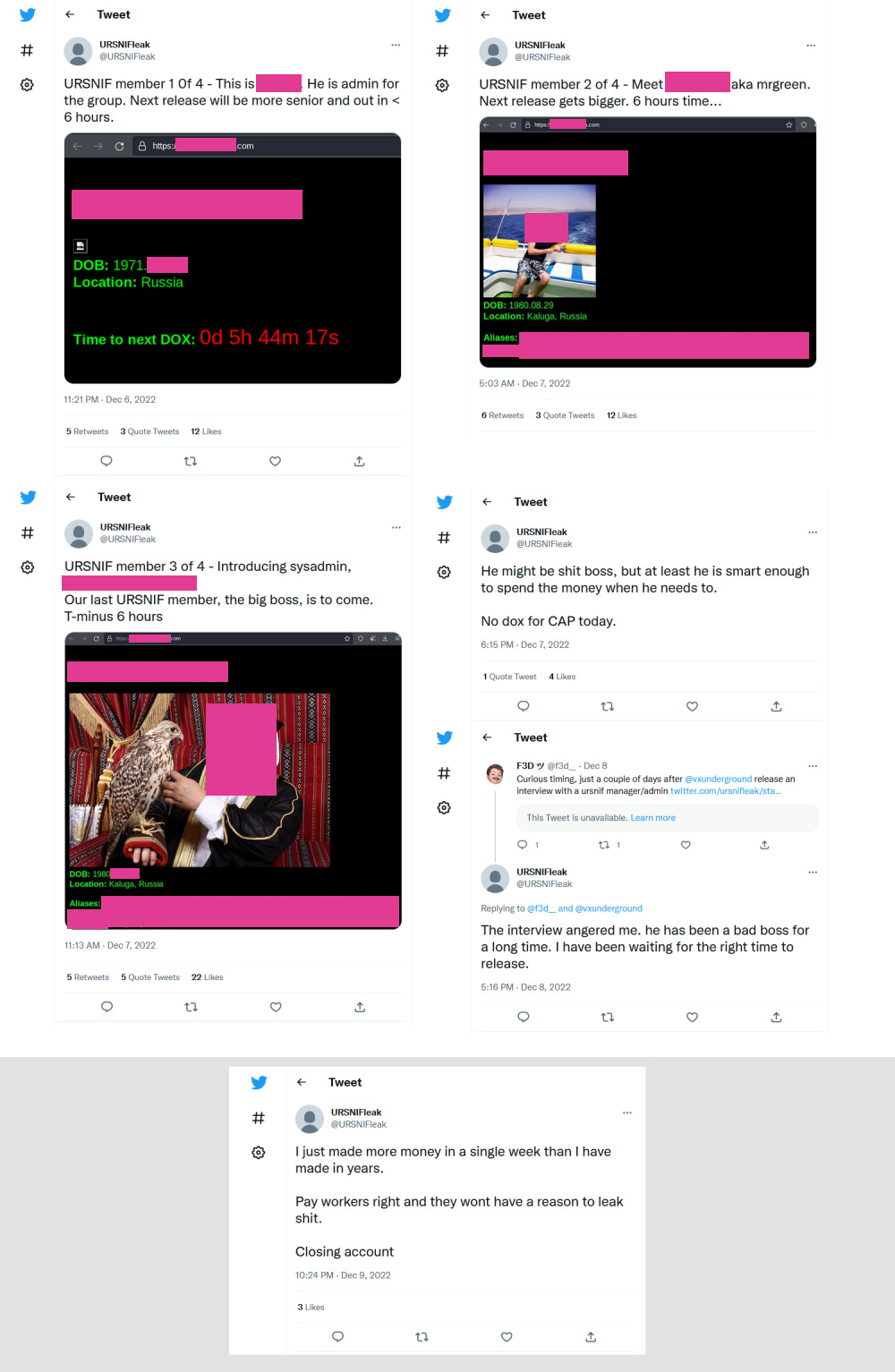
An individual claiming to be a former member of the URSNIF malware operation has leaked the real-world identities of three of the gang's members in a series of tweets last week.
The account, going by the name of URSNIFleak, has also released snippets from the gang's internal chats, along with screenshots of some of the URSNIF malware's source code and private messages sent via an underground malware forum, discussing topics like money laundering and the war in Ukraine.
The incident marks the fourth major doxing of a cybercrime operation this year after similar leaks exposed crucial and very sensitive information about the operations of the Conti ransomware, the TrickBot trojan, and the Yanluowang ransomware gang.
The first two leaks were driven by an anti-Russian sentiment as the Conti gang (which also managed the TrickBot botnet) showed their support for Russia's brutal invasion of Ukraine. The reasons for the Yanluowang leak are still unknown.
However, the reason behind the URSNIF leak is much more mundane—and it's revenge and your run-of-the-mill extortion.
The leak was teased over several days (on a first now-suspended Twitter account); they first leaked details of low-level members to show they were serious (1, 2, 3); and the URSNIFleak account stopped posting new content after the leader of the URSNIF gang (an individual named CAP) paid them off to keep quiet.
"I just made more money in a single week than I have made in years. Pay workers right and they wont have a reason to leak s***," URSNIFleak wrote in their last tweet before allegedly closing the account.
In another tweet, URSNIFleak said they decided to go through with the leak and extortion after reading statements made by the URSNIF leader in a recent interview with the VX-Underground project. What particular part, they did not say.
"The interview angered me," URSNIFleak said. "He has been a bad boss for a long time. I have been waiting for the right time to release."
Compared to the Conti, TrickBot, and Yanluowang leaks, less information was released in the URSNif dox, but despite this, nobody in infosec is complaining. More cybercrime leaks, plz! Especially leaks like these that show how URSNIF's recent pivot to a ransomware operation was not as successful as the gang was hoping.
Breaches and hacks
Rackspace faces three CALs: Cloud hosting provider Rackspace will have to defend at least three different class-action lawsuits related to a ransomware attack that hit a part of its server infrastructure and has left countless companies without access to their email servers. In an interview last week, Rackspace suggested they might not be able to recover all their customers' data, which they referred to as "legacy data." The company also appears to have given up on hosting Exchange email servers in its cloud and said it was migrating all its existing customers to Microsoft 365. Migrating its Exchange customers to a rival will cost the company $30 million, according to documents Rackspace filed with the SEC.
Lodestar Finance crypto-heist: A threat actor has abused an exploit in the smart contract of the Lodestar Finance DeFi platform and has stolen more than $5.8 million worth of cryptocurrency. The platform said it already recovered $2.4 million of the stolen funds and is still working to secure the rest. Just like most cryptocurrency platforms that get popped these days, Lodestar has offered to let the hacker keep some of the stolen funds and hide the intrusion under a "white-hat agreement."
General tech and privacy
Edge support on Windows 7/8: Microsoft plans to end support for its Edge web browser on Windows 7 and Windows 8/8.1 versions next year, on January 10, 2023. This is the same date when both Windows 7 and Windows 8/8.1 will reach End-Of-Life (EOL) after their extended support periods expire. Google also announced earlier this fall that Chrome version 110 would be the last to support both Windows 7 and Windows 8/8.1. Chrome 110 is scheduled for release in February 2023.
Chrome passkeys support: Google has added formal support for the passkeys authentication mechanism to its Chrome web browser through an update released last week. Passkeys are an industry standard that allows users to log into apps or websites without entering a password and using a cryptographic token instead. Passkeys support is now available for Chrome running on Android, macOS, and Windows 11. Users can view and manage passkeys via the following Chrome settings URL.
chrome://settings/passkeysTwitter drama: After Elon Musk fired most of the team that deals with removing child exploitation materials from Twitter, three other members of the Twitter Trust and Safety Council resigned last week after being locked out of the platform. Immediately after the resignations became public, Musk personally led a harassment campaign against his former employees who dared reveal how Twitter, under Musk, was failing to honor its promises to crack down on child abuse and hateful language. More in this Mastodon thread.
Again, I tell you, Elon is full of shit, people. slate.com/technology/202…
— Matt Ortega (@MattOrtega) 11:18 PM ∙ Dec 9, 2022
I guess I shouldn't be surprised at this extraordinary hatefulness from Elon Musk, but I still am
— 🦀 Jon Schwarz 🦀 (@schwarz) 11:55 PM ∙ Dec 10, 2022
Government, politics, and policy
Japan to go on the cyber-offensive: The Japanese government is working to amend its National Security Strategy law to allow government agencies to conduct preemptive cyber-attacks against threat actors they might deem a potential threat. In its current form, Japanese law allows the country to respond with offensive cyber-attacks only in the case of a military attack. The Japanese government's efforts come after the Australian government said they would go after hacker groups as a preemptive measure before threat actors can get to attack Australian organizations. [Original coverage in Nikkei, non-paywall version here]
Mis/disinformation framework: The EU Agency for Cybersecurity (ENISA) and the European External Action Service (EEAS) have put forward an analytical framework for the study of misinformation and disinformation.
Sponsor section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
Proofpoint will also be making an appearance on this newsletter’s podcast version where they will be talking about SocGolish, a malware delivery operation the company previously detailed in more depth last month.
Cybercrime and threat intel
Pig-butchering suspects detained: Australian police have detained four Chinese nationals as part of an investigation into a criminal syndicate involved in a new type of online investment scam known as "pig butchering." AFP officials say they detained the suspects following a tip from the US Secret Service back in August and that the four are linked to scams that have stolen more than US$100 million in losses worldwide. Officials also seized $22.5 million across 24 bank accounts linked to the four suspects and their gang.
BEC scammers detained in the US: The US Secret Service and the Department of Justice have announced the arrest of four individuals accused of participating in BEC attacks and credit card fraud schemes. Officials said the suspects stole and laundered more than $5.4 million following BEC attacks on US businesses. The gang also used stolen credit card numbers to fraudulently charge more than $3.4 million on the stolen cards via point-of-sale machines associated with companies registered in their names (galaxy brain idea right here!).
International SMS spam on the rise: AdaptiveMobile researchers said they are seeing a new trend of using international numbers for the delivery of SMS spam and phishing messages to mobile subscribers in other countries.
Ransomware via PyPI and npm: Researchers with SecDevOps company Phylum have discovered a cluster of 21 malicious PyPI packages and five npm libraries that were installing ransomware. The malicious libraries used names that were misspelled versions of legitimate packages, hoping to infect developers who didn't spot typos during installation routines. The same threat actor was behind both the Python and JavaScript campaigns, and all malicious packages are now removed from the PyPI and npm portals.
IAB market trends: CYFIRMA has published a review of the initial access brokers (IAB) market and the trends and insights they've observed this year. Some of the report's main conclusions:
- Before posting access to the underground forum, initial access brokers use ZoomInfo to compile data on the victim organization, including revenue, the industry it serves, the number of employees, and the type of business.
- Access to organizations in the United States is more expensive than in other countries.
- Access to banking domains is more expensive than any other domain. Banking access is sold for USD 10,000 to USD 160,000 (based on recent sales) by IABs.
- Some IABs post details on what data is available in the system to which they are selling access to provide heads-up to the buyer on what to expect in the system.
- Anti-Virus details in the victim system are shared in the sale posting.
Malware technical reports
Truebot: Back in 2020, several security firms claimed that a financially-motivated hacking group named Silence might have connections to EvilCorp, a Russian cybercrime cartel that was sanctioned by the US government. In a report published last week, Cisco Talos says they've seen attacks where the Silence gang's Truebot malware installed Grace (aka FlawedGrace and GraceWire), a malware strain formally linked to the EvilCorp gang, further supporting claims that Silence and EvilCorp are either the same or working together. Further supporting their claims, Talos researchers also noted that in some of these attacks, the intruders also deployed the Clop ransomware, another favorite of the EvilCorp (TA505) gang.
Python backdoor targeting ESXi: F5's security team has uncovered a new Python-based backdoor that has been deployed on compromised VMWare ESXi servers.
BlueFox: Russian security firm Positive Technologies has an analysis of BlueFox, a new infostealer advertised on underground forums under a Malware-as-a-Service model. Their report is in Russian. An English-language report on the same malware is also available via Sekoia.
New ransomware: Fortinet researchers have a round-up of new ransomware strains they've seen in the wild over the past week. The list includes the likes of Vohuk, ScareCrow, and AERST.
APTs and cyber-espionage
Cloud Atlas (Inception) APT: Check Point and Positive Technologies both published reports on the Cloud Atlas APT last week. Both companies observed that since the onset of the Russian-Ukrainian conflict, the group has narrowed down and focused its activities on Russia, but also Belarus and conflicted areas in Ukraine and Moldova.
DolphinCape: Ukraine's CERT says that a threat actor is using spear-phishing emails with lures related to Iran kamikaze drones to distribute a Delphi-based malware strain known as DolphinCape. Targets include Ukrainian government organizations. No official confirmation this is an APT campaign, but let's be candid here—what else could this be?
Cobalt Mirage APT sub-group: Secureworks researchers have published a technical analysis of Drokbk, a new malware strain used by what the company calls Cluster B, a smaller sub-group of the larger Cobalt Mirage Iranian APT. Secureworks researchers say Drokbk is deployed post-intrusion as a persistence mechanism and that the malware uses GitHub for command and control.
Phosphorus APT brazenness: Researchers with Team Cymru say that even if one of their servers was exposed in a CISA alert in September, Phosphorus, an Iranian threat actor group, has continued to use it for subsequent attacks throughout October and November 2022.
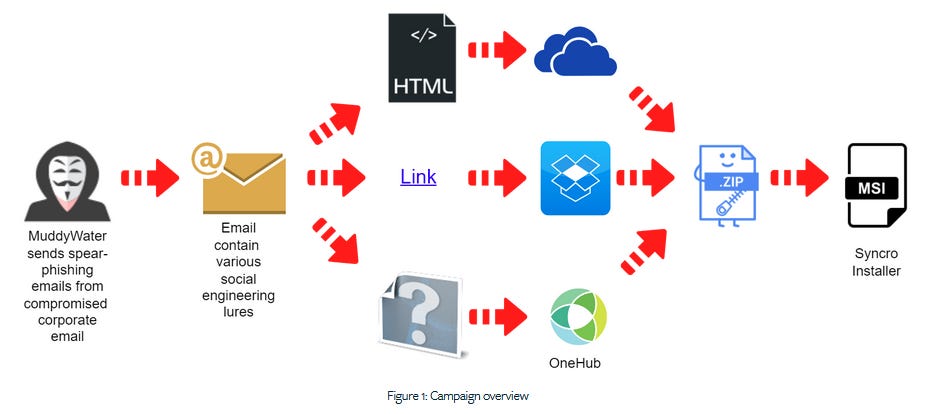
MuddyWater APT: Deep Instinct researchers have a report out on a recent spear-phishing campaign carried out by the MuddyWater Iranian APT. This particular campaign was of note because of two things. First, the group used compromised corporate accounts to send out emails to their targets. Second, the final payload was Syncro, a legitimate remote access tool often used by MSPs (but also many threat actors).
Vulnerabilities and bug bounty
Medical lab vulnerability: BishopFox researchers found a vulnerability in the servers of Avicena Medical Laboratory, a Bosnian healthcare organization, which allowed researchers to get access to COVID-19 patient records just by querying a publicly exposed API. Researchers said they obtained details for more than 160,000 patients using this vulnerability.
Dirty Vanity technique: At the Black Hat Europe 2022 security conference last week, researchers from Deep Instinct presented details about Dirty Vanity, a new code injection technique. A public proof of concept is available here.
"This technique abuses the lesser-known [process] forking mechanism which is built in Windows operating systems."
Vulnerability does not compute: VulnCheck researcher Jacob Baines has discovered that CVE-2022-28958, a vulnerability in D-Link routers, does not actually exist. This didn't stop the Moobot botnet from integrating an exploit for it and obviously failing to infect any devices with it.\
"We conclude that CVE-2022-28958 is not a real vulnerability and at-scale exploitation has never occurred. The vulnerability should not be listed by MITRE, and it should not be in the CISA Known Exploited Vulnerabilities Catalog. We filed a dispute with MITRE and shared our findings with CISA in October 2022."
Google One VPN security audit: A security audit of the Google One VPN service conducted by the NCC Group has identified 22 vulnerabilities across the VPN's desktop and mobile apps, libraries, and architecture. The UK-based security assurance firm said that while "no significant risks were identified in this assessment," the found issues should be addressed to ensure a robust defense and in-depth design.
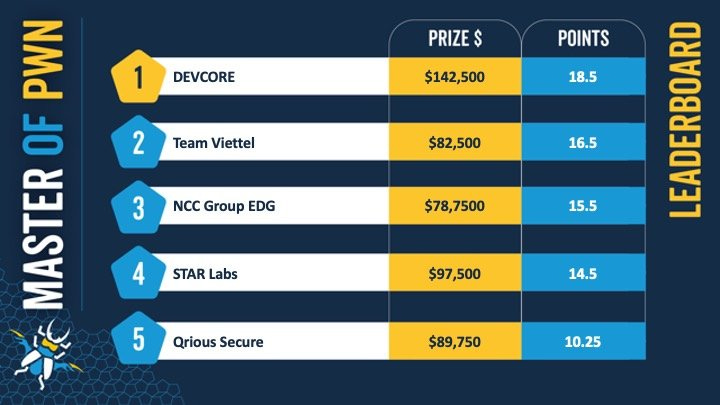
Pwn2Own Toronto 2022 results: The fall edition of the Pwn2Own hacking contest has ended. The contest is focused on the hacking of routers, smartphones, printers, and other smart devices, and this year it was won by DEVCORE, a Chinese Taiwanese pen-testing company. The contest took place across four days. Results for each are here [1, 2, 3, 4], and the final standing is embedded below. DEVCORE won the contest with successful exploits for Sonos One smart speakers, Mikrotik routers, and Canon, HP, and Lexmark printers.
Log4Shell one-year anniversary: Happy birthday to one of the most over-hyped vulnerabilities in recent years! Here's a collection of excellent memes that came out of it.
Infosec industry
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




