Risky Biz News: Digital wallet apps, the new frontier for card fraud
In other news: Telegram CEO arrested in France; identity of a major hacker leaks from private CrowdStrike report; Meta takes down APT42 WhatsApp accounts.

This newsletter is brought to you by Thinkst, the makers of the much-loved Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

An academic study presented last week at the USENIX security conference has detailed several vulnerabilities in the modern financial ecosystem that can be exploited by threat actors to add stolen cards to digital wallet apps and conduct transactions with stolen funds without being detected.
The paper—titled "In Wallet We Trust: Bypassing the Digital Wallets Payment Security for Free Shopping"—is an eye-opener and wake-up call for app makers and banks that they need to improve the security of some of their underlying processes.
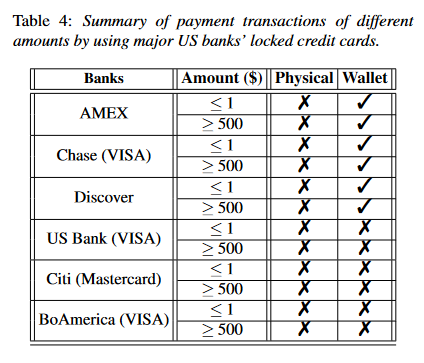
The study looked at the services of several major US banks (AMEX, Bank of America, Chase, Citi, Discover, US Bank, etc.) and three of today's top digital wallet providers in Apple, Google, and PayPal.
Researchers say they've discovered several issues impacting how banks and digital wallets interact that can be exploited for these attacks (see table below).
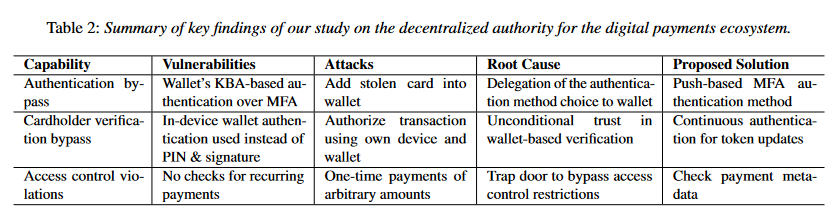
The first is an issue in how cards are added to digital wallet apps. The problem resides in the fact that some banks don't enforce multi-factor authentication (MFA) and allow users to add a card to a wallet via knowledge-based authentication (KBA)—a procedure for which attackers can use stolen PII data and pretend to be the real card holder when adding the card to the wallet.
For example, the attacker can add a stolen card to their digital wallet using the victim's ZIP code, billing address, or other personal details they can easily discover online or are typically included with the package of stolen cards.
This can be easily prevented by enforcing MFA and sending an SMS or push notification to the victim's phone number, a challenge not many attackers would be able to bypass.
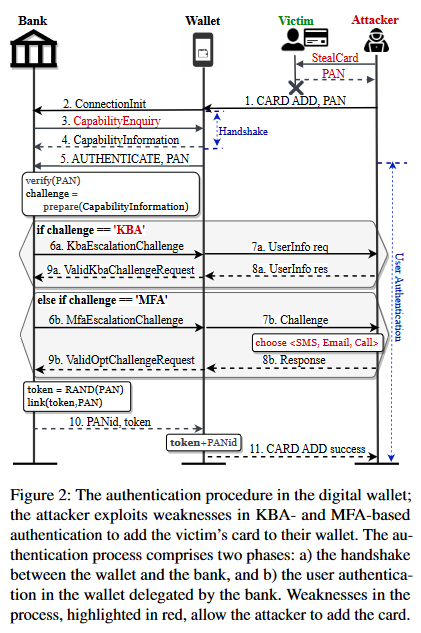
Second, even if the victim detects that their card was stolen, locking and replacing the card does not work, and the threat actor can still use the previously added card in their wallet without requiring (re)authentication.
The core issue here is that banks assign digital wallets a PANid (Primary Account Number ID) and a payment token when they add a card.
When a card is replaced, banks release a new PANid and payment token to all the wallets where the card was added, assuming that all wallets are controlled by the legitimate owner. Those tokens allow threat actors to continue using their digital wallets but now authorized to make purchases against the re-issued card.
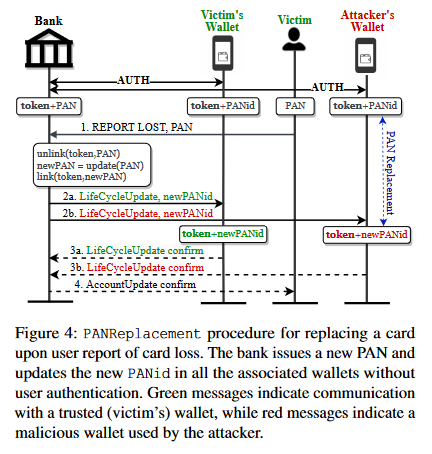
The third issue affects how digital wallets (storing stolen cards) can be used at in-store physical locations against Point-of-Sale terminals.
The issue here is that PoS terminals rely solely on digital wallets for cardholder verification. On the other hand, digital wallet apps approve transactions if the app is unlocked using some sort of strong biometric authentication.
None of these two operations account for the situation when a wallet is paired with stolen cards by a malicious party. As long as the attacker unlocks their own wallet app, they're good to go to make payments against someone else's card.
According to the researchers, this didn't work against all banks, but when it did, it also worked with card numbers that had been locked for weeks and for large transactions of over $500.
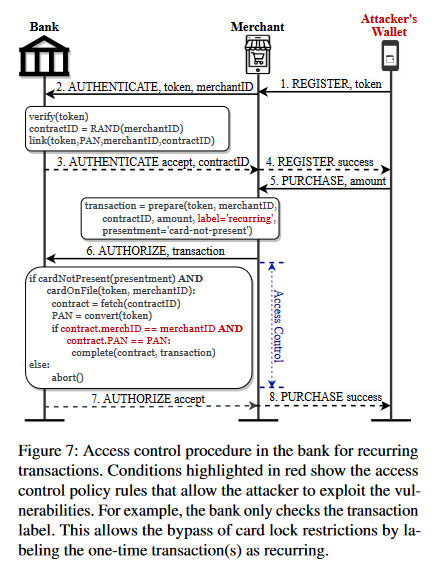
A fourth issue identified by researchers was that attackers could label one-time transactions as recurring payments. This way, with the help of a rogue merchant or as part of affiliate schemes, attackers could abuse digital wallets to enroll stolen cards into several types of recurring money-making schemes.
"The bank's decision to freely allow merchants to label any transaction as 'recurring' is a trade-off between usability and security. While this design allows the users to continue using the services after they have locked the physical card, it gives birth to access control bypass vulnerability even for one-time transactions. The bank relies on its security modules (e.g., access control, and fraud detection tools) to filter out unexpected transactions by the user. However, these tools cannot differentiate between recurring and one-time transactions (especially, when the transaction is already registered at the bank); and fail to verify the nature of the transactions. In consequence, the attacker can bypass the access control policies for one-time transactions, and can make purchases of any amount and at any time despite the card being locked by the cardholder."
The study took place in 2023 and primarily targeted the US banking ecosystem. The research team notified all affected banks and digital wallet makers in April 2023 but only received responses from Chase, Citi, and Google.
When they followed up in February 2024, Discover also acknowledged the issues.
Despite the severity of the issues discovered during their research, some banks and vendors did not take their work seriously enough—something that may end up biting the companies and their users on the a$$ later on.
"At the time of writing this paper, Google is working with the banks from its end to address the reported issues on Google Pay. The banks, however, reported to us that the disclosed attacks are not possible anymore. Chase confirmed that additional fraud detection and transaction limitation measures have been put in place to address the reported vulnerabilities; Citi and Discover, however, did not disclose the specific mitigation measures to us. We did not yet receive responses from AMEX, BoA, US Bank, Apple, and PayPal."
The research team says that many of the issues presented in their paper can be fixed with easy solutions like improving authentication procedures and better token management. The attacks described look bad but should be easy to address once vendors stop behaving like they're stuck in the 90s again. They should probably move on fixing the reported issues since threat actors and legal firms really love this kind of research.
Breaches, hacks, and security incidents
Nothing in this edition.
General tech and privacy
DOJ sues RealPage: The US government has sued real estate software company RealPage for antitrust violations. The DOJ claims RealPage has baked algorithms into its software to help landlords maximize rents they extract from customers. It also accused the company of using sensitive data collected by competing landlords to create price ranges a renter may be capable of paying in order to maximize the profits of a new landlord. The company denied any wrongdoing and said it would fight the lawsuit.
Germany's secret piracy blocklist: A 17-year-old student from Germany has discovered that some of the country's largest ISPs are running a secret blocklist. The blocklist is the result of a voluntary agreement between the ISPs and rightsholders signed in 2021. According to the student, the blocklist currently blocks access to 275 domains and subdomains. Most of the sites are used for streaming live sporting events or hosting pirated movies and TV shows. The student, going only by the name of Damian, has launched a special website where Germans can query the blocklist or add new sites to it. [Additional coverage in TorrentFreak]
Mozilla removes Adjust from Firefox: Mozilla has removed the SDK of German data collection service Adjust from its Firefox Focus mobile browser. According to German tech blogger Soeren Hentzschel, this is also the reason why the "Marketing Data" option is no longer available in the browser's Data Collection settings screen.
Threads tests disappearing posts: Meta's social networking site Threads is testing disappearing posts. The new feature will delete posts and replies after a 24-hour timer. Meta says Threads is slowly catching up to Twitter and already has more than 200 million monthly active users. [Additional coverage in Engadget]
Pavel Durov detained in France: French authorities have detained Telegram CEO and founder Pavel Durov. He was detained after his private plane landed at an airport near Paris. According to two French TV stations, Durov was detained in an investigation related to Telegram's lack of content moderation. The instant messaging service has become a popular host of stolen personal data, stolen cards, revenge porn, CSAM, malware, and all sorts of illegal content. [Additional coverage in TF1 and BFM]
Government, politics, and policy
Germany wants live facial recognition: German officials are floating the idea of using facial recognition technology to find suspects in live CCTV feeds—something that is not currently permitted under EU privacy laws. [Additional coverage in BR]
Russia wants a tax on foreign software: The Russian government is working on a law that will introduce a special tax for all companies that use foreign software. The new tax will only apply to big corporations but not SMBs and government organizations. The new bill will be introduced in the Duma in September. The new tax contradicts previous statements from the same government claiming that Russian organizations have migrated to domestic software. [Additional coverage in TASS]
Singapore OT plan: The Singapore government has published an Operational Technology (OT) Cybersecurity Masterplan designed to improve the security of companies managing the country's industrial control systems.
US government sues Georgia Tech: The US government has sued the Georgia Institute of Technology for allegedly lying about its cybersecurity posture in order to win government contracts. The Justice Department says Georgia Tech and its research division submitted false cybersecurity assessments in order to win DOD contracts. The assessment claimed the two organizations had cybersecurity plans in place to deal with sensitive DOD data. The DOJ says the assessments included scores for "fictitious" or "virtual" IT environments. The US government filed the lawsuit after two whistleblower complaints from former members of the Georgia Tech cybersecurity team.
FTC bans fake reviews: The US Federal Trade Commission has passed the final version of a new rule that bans companies from using fake or paid reviews to boost product sales and deceive consumers. The new rule also bans companies from operating their own review sites, prohibits companies from using negative reviews against competitors, and bans the use of legal or other types of threats to suppress bad reviews. The new rule also explicitly bans companies from buying or selling fake followers or likes to boost a product's popularity on social media. Companies that break the rules should expect to be taken to court by the FTC.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Haroon Meer, Founder and CEO at Thinkst, about the company's evolution over the past 15 years, its focus on hacker-like internal culture, and the UK NCSC's new deception network.

Cybercrime and threat intel
Russian money launderer detained: Argentinian police have detained a Russian national on suspicion of laundering money for North Korean hackers. The suspect was detained in Buenos Aires as part of an investigation into the Harmony Bridge hack. Officials say funds from the hack were traced to a Telegram channel run by the suspect that allowed customers to exchange cryptocurrencies across different blockchains. North Korean hackers stole more than $100 million worth of assets from the Harmony Bridge platform in June of 2022. [Additional coverage in La Nacion]
Hacker USDoD identified: A Brazilian tech news outlet has identified a prodigious hacker known as USDoD as a local Brazilian man. Reporters at TecMundo claim a leaked CrowdStrike report has identified USDoD as a 33-year-old man named Luan B.G. who lives in the state of Minas Gerais. CrowdStrike claims the individual has been involved in the hacker scene since 2017, when he joined a local Brazilian hacktivist group and later pivoted to cybercrime. The leaked report contains details linking USDoD's real persona to his hacker identity, hacker email addresses, and cybercrime transactions. The report confirms details USDoD has provided in interviews he gave out through the past years. [h/t DataBreaches.net]
Malicious Pidgin plugin: The Pidgin instant messaging service has removed a malicious plugin from addons index. The plugin was named ss-otr and claimed to provide support for encrypted off-the-record conversations for the Pidgin client. It was live for over a month and contained malware that logged keystrokes and took screenshots of a victim's screen. Following the incident, the Pidgin team will now require that all plugins open-source their code if they want to be listed on the official plugin repo.
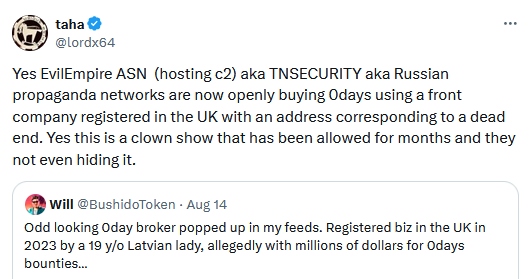
New zero-day broker pops up: There's a new exploit broker advertising on Twitter about buying zero-days. As several security researchers have pointed out, the threat actor is a Russian company that has ties to Russia's propaganda machine and uses a UK company as a front. Maybe someone in UK law enforcement decides to take a look!
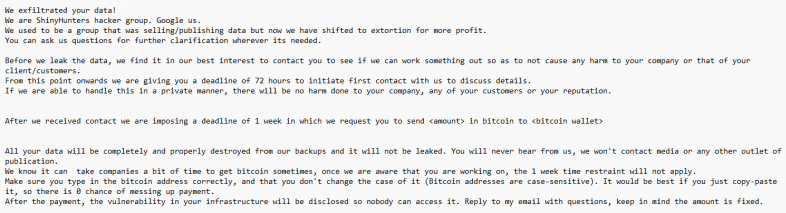
Bling Libra: Palo Alto Networks has published a profile on Bling Libra, the threat actor behind the hacker identity of ShinyHunters. Researchers say the group shifted this year from trying to sell hacked data to privately extorting companies and targeting cloud environments.
Malware technical reports
Greasy Opal: Arkose Labs has published a technical breakdown of Greasy Opal, a CAPTCHA-solving service sold on underground cybercrime forums.
Perfctl rootkit: Security researcher Purpleroc has published an analysis of Perfctl, a Linux rootkit that has been used in attacks against the customer infrastructure of Chinese web hosting providers over the past year. The final payload was a crypto-miner, obviously.
Copybara: Zscaler has published an analysis on a new version of the Copybara Android trojan.
"This new variant of Copybara has been active since November 2023, and utilizes the MQTT protocol to establish communication with its command-and-control (C2) server. The malware abuses the Accessibility Service feature that is native to Android devices to exert granular control over the infected device. In the background, the malware also proceeds to download phishing pages that imitate popular cryptocurrency exchanges and financial institutions with the use of their logos and application names. These pages are designed to deceive victims into entering their credentials, which can then be stolen by the malware."
Sponsor Section
Thinkst launched earlier this month a new fake mobile app Canarytoken for your smartphone. The token can be configured to look like any app you want and alert security teams when it is opened—an indication the employer's device was either infected with malware looking for juicy stuff or fell in the hands of an unauthorized third party (also looking for juicy stuff).
APTs, cyber-espionage, and info-ops
Meta takes down APT42 accounts: Social media company Meta has taken down a cluster of WhatsApp accounts used by Iranian state hackers to target victims abroad. The accounts posed as technical support representatives for US tech companies such as AOL, Google, Yahoo, and Microsoft. Meta says the accounts were operated by APT42, a cyber-espionage group linked to Iran's IRGC-IO cyber unit. The company says it learned of the accounts after users reported the suspicious conversations.
Iranian attacks on Utah: The Iranian hackers who targeted both US presidential campaigns also tried to hack multiple Utah government sites. According to NBC News, the group targeted a county in Utah, geological archive data, oil and gas, and other geographical resources related to the US state. The hacking campaign took place between March 2023 and March 2024, according to Utah officials.
Vulnerabilities, security research, and bug bounty
Traccar RCEs: Horizon3 researchers have published a report on two RCEs in the Traccar GPS tracking system.
NTLM thefts from Python apps: Security firm Horizon3 has published a report detailing vulnerabilities in three Python apps that can be exploited for NTLM credential thefts.
Honeywell BEDQ exposed API: Traceable researchers have found an unprotected API in Honeywell BEDQ, an internal system used by Honeywell employees and partners. The company says it used the bug to take "complete control over the entire system."
MSKSSRV vulnerabilities: DEVCORE researchers have published a write-up on how they found several issues in the Microsoft Kernel Streaming Service (MSKSSRV). This is part one of a multi-part series and looks at multiple CVEs.
Zoho security update: Zoho has released a security update to fix an RCE vulnerability in the user interface of its ManageEngine OpManager component. [h/t ScreamingGoat]
SonicWall security update: SonicWall has fixed an improper access control vulnerability in SonicOS. The company says the bug could have led to unauthorized access to firewall resources or could have crashed the device. [h/t ScreamingGoat]
Infosec industry
Threat/trend reports: At-Bay, Forrester, Positive Technologies, and Red Canary have recently published reports covering infosec industry threats and trends.
TTIS 2024 videos: Live streams from the Telecom Threat Intelligence Summit 2024 security conference are available on YouTube [Day 1, Day 2].
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq examine how the cybersecurity industry is very strange when compared to other professional fields, such as doctors and accountants.
In this podcast, Tom Uren and Patrick Gray discuss an Australian government effort to bridge the gap between online and real identity across the whole economy. It addresses a real need, but Tom doesn't think it will go smoothly.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!





