Risky Biz News: Dark web mega-hack as Kraken takes over Solaris
In other news: Chinese hackers breach Iranian government; Mailchimp hacked again; Bitzlato CEO arrested for laundering ransomware funds.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The administrators of the Kraken dark web marketplace have hacked and taken over the infrastructure of Solaris, one of their rivals.
The hack came to light on January 13 when the Solaris market started redirecting visitors to the Kraken portal, where they were greeted by a message from the Kraken admins claiming to have taken over Solaris infrastructure, cryptocurrency wallets, and source code repositories.
Blockchain analysis firm Elliptic, which documented and confirmed the hack, says Solaris was one of the largest drug markets on the dark web last year, processing around $150 million in sales of drugs and other illegal goods and services in its short lifespan.
Elliptic says the market was closely associated with Killnet, a pro-Kremlin hacktivist group, although it's unclear if the group was also in charge of the market itself.
In December last year, Alex Holden, a US security researcher with Ukrainian roots, claimed to have hacked Solaris and stolen $25,000 worth of cryptocurrency, which he later donated to Ukrainian charity organizations.
Elliptic believes this initial hack attracted the attention of the Kraken administrators and led to Solaris' demise.
But unlike Holden's intrusion, motivated by the Russian-Ukrainian war, Elliptic says the new Kraken admins are also pro-Kremlin group, so the hack is unlikely to be politically motivated.
Breaches and hacks
PayPal data breach: Payments processor PayPal says it fell victim to a credential-stuffing attack in early December last year. According to a data breach notification letter filed with the Maine Attorney General's Office, the incident impacted almost 35,000 user accounts, where hackers gained access using legitimate login credentials. PayPal said that despite the breaches, it did not find any unauthorized transactions in the breached accounts following an investigation.
Mailchimp data breach: Email delivery service Mailchimp says that one of its support employees was compromised, and hackers accessed account data on 133 of its customers. Mailchimp says the hack took place on January 11 and its security team managed to isolate the compromised employee account a day later on the 12th. According to TechCrunch, one of the 133 compromised Mailchimp accounts belonged to WooCommerce, a division inside Automattic that's behind the eponymous WordPress e-commerce plugin. The incident marks the second time Mailchimp got hacked in a year after threat actors also breached its systems last August. At the time, the hackers used their access to Mailchimp to send out phishing emails to customers of cloud hosting company Digital Ocean and multiple cryptocurrency platforms.
Yum! Brands ransomware attack: Fast food corporation Yum! Brands says it suffered a ransomware attack this week that forced it to close nearly 300 restaurants across the United Kingdom. In a press release on Wednesday, the company says that it has since resumed operations at the affected locations and it expects to restore affected IT systems in the "coming days."
Royal Mail ransomware attack: Royal Mail says it has resumed international parcel and letters shipping after its recent ransomware attack.
Midas Capital crypto-heist: DeFi platform Midas Capital lost $660,000 worth of crypto assets following a flash-loan attack earlier this week. Obligatory and almostcertainly illegal tweet asking the hacker to get in contact and negotiate a "bounty" to return the funds.
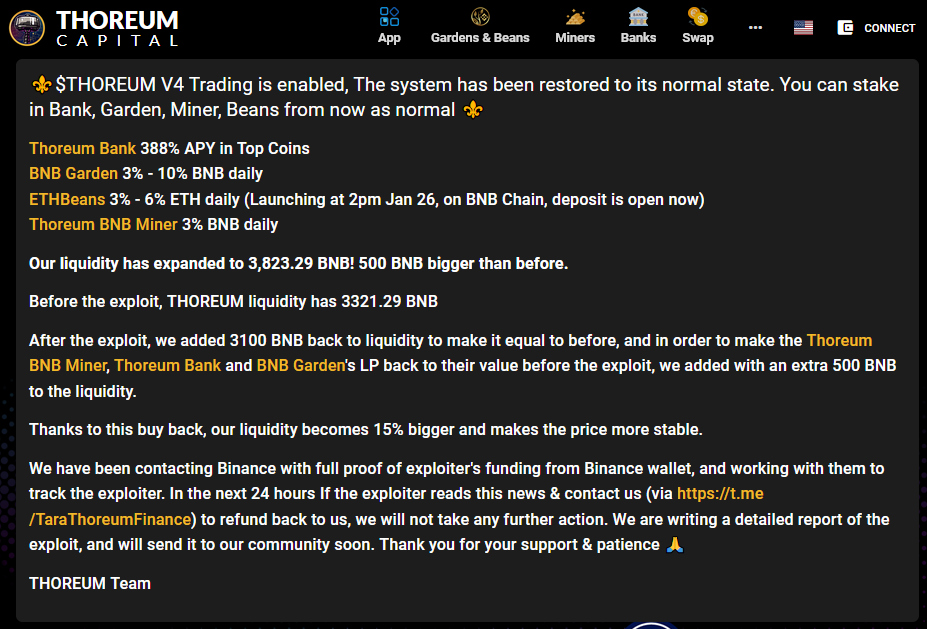
Thoreum Finance crypto-heist: Cryptocurrency platform Thoreum Finance says that a threat actor exploited a vulnerability in one of its smart contracts and stole 3100 BNB coins, estimated at around $900,000. An analysis of the hack is available via Numen Labs.
General tech and privacy
Apple ADP available globally: With the release of iOS 16.3 next week, Apple plans to expand the Advanced Data Protection feature to all users worldwide. Advanced Data Protection is a feature that lets Apple users encrypt the data they store in their iCloud accounts. The feature launched in December last year for US users only. Twenty-three different iCloud data categories can be encrypted in iCloud via ADP. Starting next week, Apple says that three new categories will also be supported, namely iCloud Mail, Contacts, and Calendar.
Meta fined again: EU officials have fined Meta €5.5 million for breaking GDPR rules on its WhatsApp instant messaging service. The fine is related to a series of intentionally designed popup messages that Meta showed to WhatsApp users in previous years, urging them to accept its new Terms of Service or be unable to access WhatsApp going forward. The fine was imposed by the Irish Data Protection Commission, where Meta has its EU headquarters. This is the third fine Meta received from the agency this year after it was previously fined €210 million and €180 million for breaking GDPR rules on its Facebook and Instagram services, respectively.
Government, politics, and policy
Nordic common cybersecurity strategy: Nordic states including Denmark, Finland, Iceland, Norway, Sweden, the Faroe Islands, Greenland, and the Åland Islands, will develop a common defense-focused cybersecurity strategy. Norway, which currently holds the rotating presidency of the Nordic Council, will be in charge of developing the strategy, which will serve to enhance intelligence sharing between member countries as part of their efforts to improve their common military strategies. [Additional coverage in DefenseNews]
Intellexa fined: Greek data protection authorities fined Intellexa €50,000 for failing to respond to an official government inquiry. The company's main product, the Predator spyware, was used to spy on multiple government figures, prosecutors, and investigative journalisms, a scandal for which the Athens government has drawn the ire of EU officials.
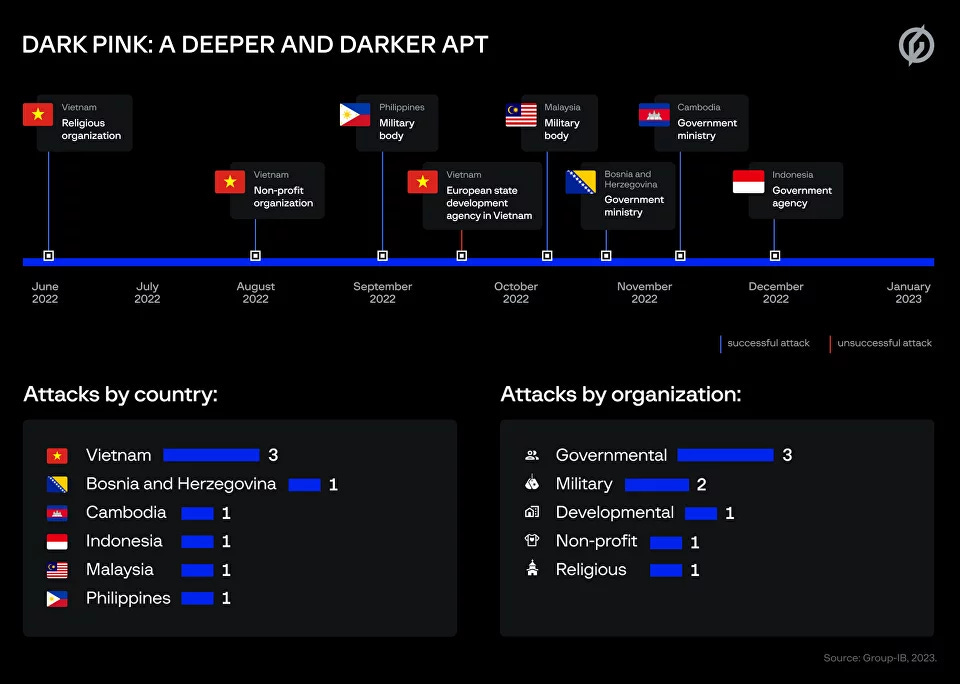
Malaysian Armed Forces cyberattacks: The Malaysian Armed Forces say they thwarted cyberattacks that targeted its national defense network. Officials said hackers launched a spear-phishing campaign aimed at several Armed Forces and Ministry of Defence agencies. Army officials attributed the spear-phishing operation to Dark Pink (Saaiwc), a new cyber-espionage group discovered this month by researchers from security firms Group-IB and Anheng. The Malaysian army was just one of the many organizations targeted by the group in the same campaign, which also went after government and military agencies in Vietnam, Cambodia, Indonesia, and the Philippines. [English press coverage here]
Sponsor section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year, in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
Cybercrime and threat intel
DDOS booter operator pleads not guilty: John Dobbs, the administrator of the IPStresser.com DDOS-as-a-service portal, has pleaded not guilty. Dobbs was charged in December last year after authorities seized more than 50 DDOS-for-hire portals.
Bitzlato owner detained: US authorities have detained and charged Anatoly Legkodymov, 40, a Russian national, and the owner of Bitzlato, a cryptocurrency platform based in Hong Kong. US officials say Legkodymov's platform failed to implement anti-money laundering safeguards and enabled criminal cartels to launder more than $700 million of illicit funds, representing profits from ransomware attacks and drug trafficking. Authorities listed Conti as one of the ransomware gangs that used Bitzlato to launder funds. Although a resident of the city of Shenzhen, in China, the Bitzlato CEO was arrested earlier this week while visiting Miami.
New npm malware: Twenty-three new malicious npm packages spotted. Check out GitHub's security advisory portal for details.
Vidar infrastructure: In a report on Thursday, Team Cymru noted that Vidar operators split their infrastructure into two parts; one dedicated to their regular customers and the other for the management team and premium users.
FIN7: Cynet has a report out on recent FIN7 phishing campaigns.
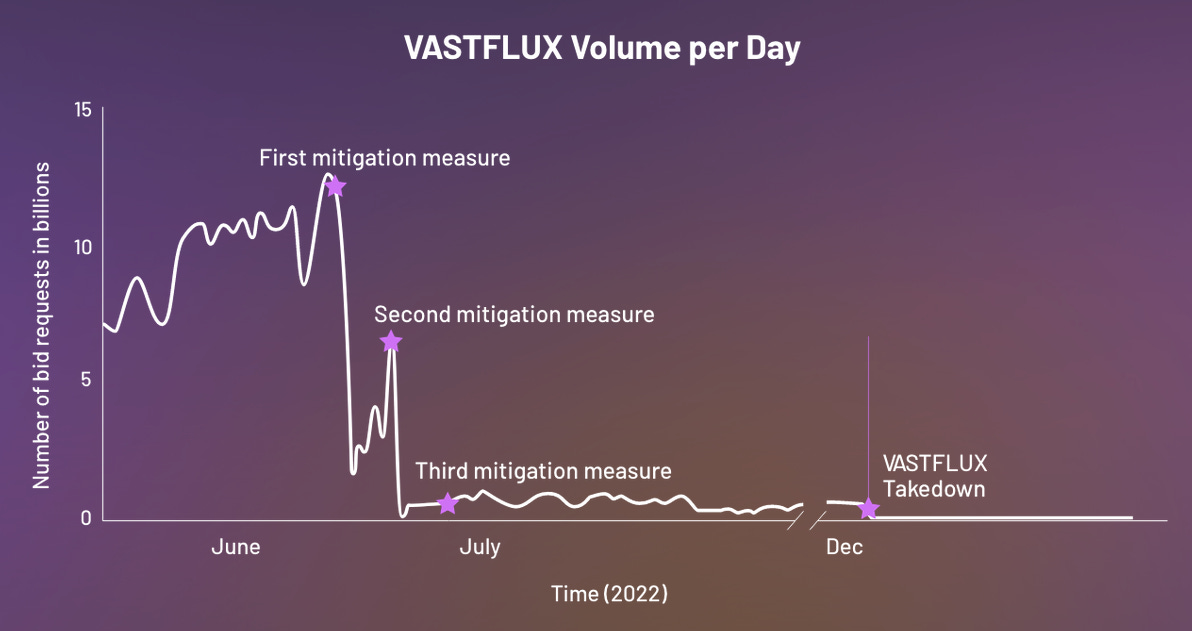
VASTFLUX takedown: Cybersecurity company HUMAN has orchestrated a takedown of VASTFLUX, a sophisticated ad fraud network that operated on the mobile ad market. HUMAN says the gang used more than 1,700 apps installed across 11 million devices to defraud advertising networks and their clients. The VASTFLUX gang used malicious code inserted inside mobile ads to stack as many as 25 video ads on top of each other, play, and get paid for all, but not actually show any. HUMAN said VASTFLUX was operated by individuals who had an intimate understanding of the digital advertising ecosystem. Researchers say VASTFLUX was one of the largest ad fraud networks they have ever seen, accounting for around 12 billion ad bid requests per day, on the same scale as other ad fraud operations such as Methbot, 3ve, and PARETO.
Malware technical reports
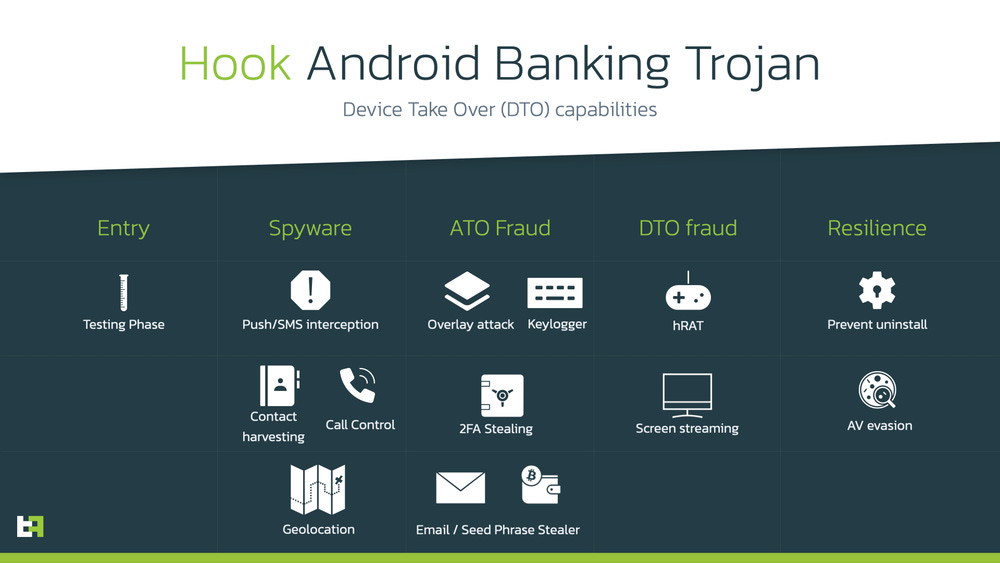
Hook malware: Researchers from mobile security firm ThreatFabric have discovered a new fork of the Ermac Android banking trojan, whose source code was sold and widely shared in previous years. This new version is named Hook and was developed by a threat actor named DukeEugene, the original author of the Ermac malware itself. ThreatFabric says that besides Ermac's classic financial fraud capabilities, Hook also added many features typically found in spyware, such as geolocation tracking, file system control, and social media monitoring. This new malware variant blurs the line that differentiates banking malware from spyware.
Remcos RAT: Minerva Labs has an analysis on the Remcos remote access trojan. I don't agree with Minerva calling Remcos a "legitimate commercial Remote Access Tool created by the security company Breaking Security," though. Come on now!
RapperBot: A report from Chinese security firm QiAnXin says the RapperBot botnet has evolved from launching DDoS attacks to deploying cryptomining payloads on the servers it manages to infect.
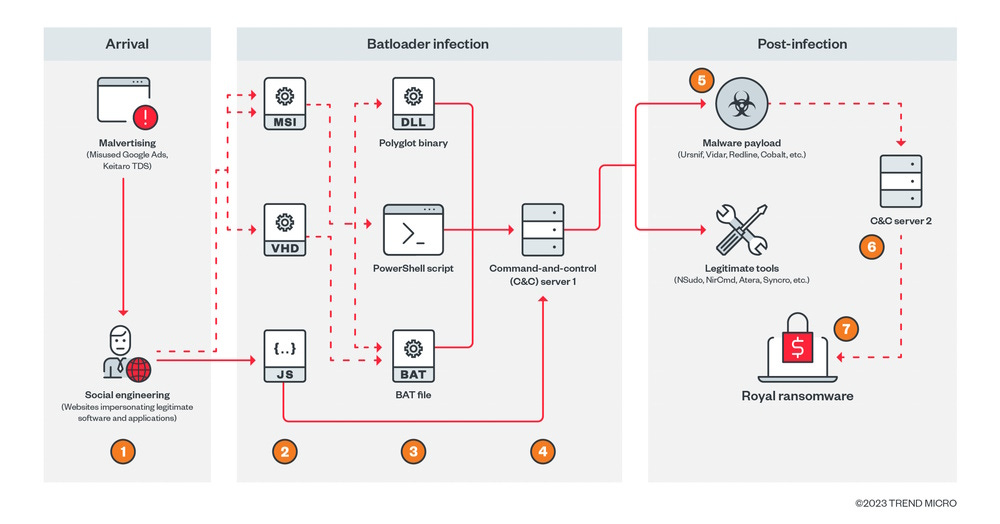
BatLoader: Security firm Trend Micro has published a report on the operations of the BatLoader malware gang in Q4 2022. The BatLoader malware is known to be distributed via malicious ads leading to web pages posing as legitimate software tools. Trend Micro has linked the BatLoader malware to a threat actor it tracks as Water Minyades.
"The actors behind Water Minyades are known for delivering other malware during the last quarter of 2022, such as Qakbot, RaccoonStealer, and Bumbleloader via social engineering techniques."
APTs and cyber-espionage
APT report: Qihoo 360 has published its annual APT report. Full copy on GitHub here.
Ukrinform attack: Ukrinform, one of Ukraine's largest news agencies, was hit by a major cyber-attack on January 17. Ukrainian cybersecurity agencies say the attack was carried out by a Russian group named Sandworm, using a data-wiping malware strain named CaddyWiper. Intelligence and cybersecurity agencies from Ukraine, the US, and the UK previously linked this group to Russia's military intelligence agency, known as the GRU.
Fortinet zero-day: Researchers with security firm Mandiant say that a zero-day vulnerability (CVE-2022-42475) that was patched last month in Fortinet SSL-VPN devices was exploited by a Chinese cyber-espionage group. Mandiant says it observed attacks from this (yet-unnamed) group as far back as October 2022. Known targeted entities include a European government organization and a managed service provider located in Africa. In the case of successful intrusions, Mandiant says the group would typically deploy either Windows or Linux versions of a new backdoor the company has named BoldMove. Last week, Fortinet published its own analysis of the zero-day. Fortinet said the vulnerability was used to attack government-related targets and hinted in its conclusion that the zero-day might be the work of a Chinese APT.
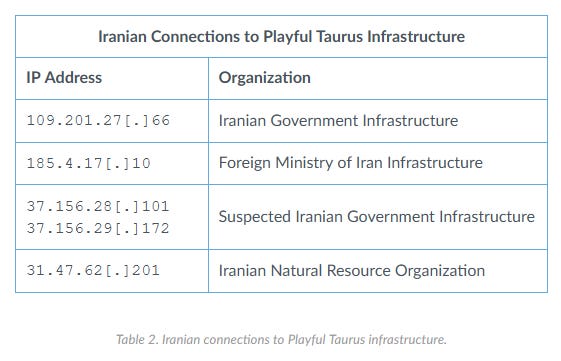
Playful Taurus (APT15): Playful Taurus, a Chinese cyber-espionage group also known as APT15 and Vixen Panda, has compromised several Iranian government networks. Cybersecurity firm Palo Alto Networks discovered the intrusion while analyzing server infrastructure linked to Turian, a backdoor developed by the Playful Taurus group. Based on telemetry, researchers say the group lurked in the compromised networks for seven months between July and December 2022. Besides the intrusions into Iranian networks, Palo Alto Networks says the group has also developed new versions of the Turian backdoor.
Vulnerabilities and bug bounty
Security updates: Since our last newsletter, Drupal, Oracle, Cisco, and Git/GitLab have released security patches.
NetComm router bugs: Netcomm router models NF20MESH, NF20, and NL1902 are vulnerable to two security flaws that can allow threat actors to bypass authentication procedures and take files off the devices. Technical details here.
"The tested models that were impacted are Netcomm routers using a Broadcom chipset that had third-party code added by Shenzhen Gongjin Electronics. The third-party code introduced the vulnerabilities. These routers are deployed by residential internet service providers."
TP-Link router bugs: There's also a clever side-channel attack against TP-Link routers where attackers could infer usernames and their passwords.
Centreon plugin vulnerability: Researchers from French security firm DSecBypass have found a vulnerability in the MAP plugin of the Centreon IT monitoring solution. The vulnerability can allow attackers to bypass authentication via the plugin's API and read the server's memory, which in turn could lead to the full takeover of Centreon servers.
Historian vulnerabilities: Claroty researchers say they identified five vulnerabilities in GE Proficy Historian industrial automation and logging servers. Per the researchers, the vulnerabilities can be used to access the historian server, crash the device, or remotely execute code.
Sudo vulnerability: Synacktiv researchers have found a privilege escalation in the sudo utility. Tracked as CVE-2023-22809, this vulnerability [PDF] may lead to privilege escalation while editing unauthorized files.
Azure AD vulnerability: Secureworks has published a technical write-up of a SAML persistence vulnerability in the Azure AD service. The issue was discovered last summer and later patched in October.
EmojiDeploy: Ermetic researchers have published a write-up on EmojiDeploy, a CSRF vulnerability in the Azure SCM service Kudu. The company says it was awarded a $30,000 reward for its finding. The attack is called EmojiDeploy because the exploit code uses the ._. emoji.
https://<my-webapp>.scm.azurewebsites.net._.<attacker-site>./MarkdownTime: Researchers with Legit Security have discovered a denial of service (DoS) vulnerability in "commonmarker," a very popular Ruby library for the Markdown syntax and formatting language. Legit researchers say the vulnerability, which they named MarkdownTime, can be used to trigger DDoS attacks on GitHub and GitLab servers, where the library is used.
AppLocker bypass: Not exactly a vulnerability, but security researcher Assume Breach has published research on how threat actors or read teams can use LNK files to bypass the Windows AppLocker security feature.
ColdFusion RCE: ZDI published the write-up on CVE-2022-35690, an RCE fixed in ColdFusion last October.
Cisco device exposure: Censys says it discovered more than 20,000 Cisco routers connected to the internet and exposed to a recently disclosed pre-auth RCE security flaw (CVE-2023-20025). Cisco did not release security updates for the affected router models as all had reached End-of-Life, and proof-of-concept code for this vulnerability exists in the wild, which means attacks are very likely to follow soon.
Exploit-DB: The Exploit-DB website appears to have gone inactive. As Marco Ivaldi has spotted, no new exploits have been added to the DB since November 11, last year, a day after the site rolled out a planned update.
CVE-2022-47966 (Zoho): As it promised earlier this week, security firm Horizon3 has released proof-of-concept code for CVE-2022-47966, a pre-authentication remote code execution in the Zoho ManageEngine server, patched in October.
Infosec industry
WEF cybersecurity outlook: Industry experts who attended the World Economic Forum this year in Davos, Switzerland, have designated cybersecurity as an area that will need addressing in the coming future. Experts warn that cyberattacks are increasing in sophistication and frequency. They also warn "that cyberattackers are more likely to focus on business disruption and reputational damage." That's one long way of writing ransomware. More in their 36-page report.
Acquisition news: Password manager Bitwarden has acquired EU-based startup Passwordless.dev, a company specializing in FIDO2 Webauthn authentication solutions.
Layoffs: Cybersecurity firm Sophos has laid off around 450 employees, roughly 10% of its workforce, according to reports.
New tool—Project Copacetic: Some of the Azure developers have open-sourced a new tool called Project Copacetic, a CLI tool for directly patching container images using reports from vulnerability scanners.
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere..




