Risky Biz News: Cybercrime groups got bored of RU/UA hacktivism
In other news: Authy users affected by Twilio hack; Tykelab linked to SS7 attacks; and Moldova, Montenegro, and Slovenia deal with cyber-attacks.
This newsletter is brought to you by Airlock Digital, Proofpoint, RunZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
We all kind of knew this was the truth, but an academic study published last week puts numbers and research behind the theory that most of the hacktivist activity that surrounds the Russian-Ukrainian conflict was and is poorly coordinated and had no real impact on the "cyberwar" that actually takes place between the two countries.
The paper—entitled "Getting Bored of Cyberwar: Exploring the Role of the Cybercrime Underground in the Russia-Ukraine Conflict"—looked at data from two months before and four months after the war's start
Researchers from three UK universities analyzed website defacements, DDOS attacks, and hundreds of announcements in Telegram channels, but also conducted interviews with the people participating in the attacks.
The study started from the premise that both legitimate IT workers and members of the cybercrime underground would be drawn into the conflict as hacktivist militant forces—which it did happen, and on both sides.
However, researchers found that while interest was high in the first weeks following Russia's invasion of Ukraine, cybercrime groups lost interest. An analysis of the activity suggests that most defacements took place in the early days of the war, while DDOS attacks lasted longer "possibly due to the widespread availability of cheap DoS-for-hire services."
The participants mostly used off-the-shelf tools, which suggested that most were low-skilled actors, at best. As time went by, the activity subsided, and the researchers said they didn't find any "hard" evidence to suggest that the cybercrime underground was making any meaningful impact on the cyberwar compared to the damage caused in the actual kinetic war.
We'll leave you with an excellent quote that perfectly describes how much of an impact the recent hacktivist activity had on the war (beyond PR, at which it excelled and still does):
The so-called 'defacements' are the rough equivalent of breaking into a disused shopping centre on the outskirts of a mid-sized Russian city and spraypainting 'Putin Sux' on the walls. The DDoS campaigns by the cybercrime underground contributed around as much to the war as going to your local supermarket and hiding the vodka under the frozen peas. These are trivial acts of solidarity, teenage competition, and expressive delinquency, not a contribution to the armed conflict in any real sense.
Breaches and hacks
Authy users affected by Twilio hack: In an update last week, Twilio said that its August 4 security breach also impacted its own Authy 2FA service. The company said that following a subsequent investigation, they identified that the malicious actors behind its breach also gained access to the accounts of 93 Authy users, where they registered additional devices to their accounts so they could intercept 2FA challenges and hijack their accounts.
Akasa Air incident: Indian low-cost airline Akasa Air disclosed a security breach on Sunday. The company said that as a result of a configuration error, "unauthorized individuals" were able to view user information, such as names, gender, email addresses, and phone numbers.
Another crypto-heist: Not a week can go by without some sort of major cryptocurrency scam or hack taking place, and last week that honor went to DeFi platform KaoyaSwap, which managed to lose roughly $120,000 in a classic flash loan attack.
Russian security cameras hacked: Ukrainian hacktivists appear to have hacked IP security cameras across the occupied Crimea and Donbas. If the cameras had a connected speaker, the cameras also played patriotic Ukrainian music. The attack was launched to celebrate Ukraine's Independence Day last week, on August 24.
Today, to celebrate Ukraine’s Independence Day, dozens of IP cameras with speaker outputs have been hacked to play patriotic music in Russia as well as occupied Crimea and Donbas.
— Artoir (@ItsArtoir) 2:02 PM ∙ Aug 24, 2022
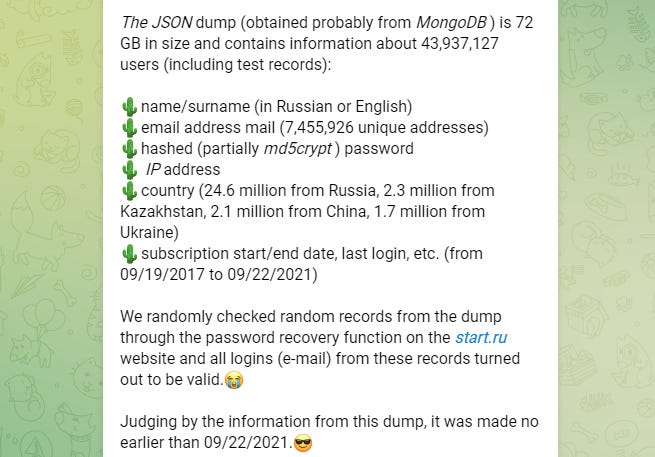
START.ru hack: Meanwhile, in Russia, local companies continue to see large data leaks in the aftermath of the country's invasion of Ukraine. The latest company to see its data shared online is START, one of Russia's largest cinema theatre chains. Earlier this week, hackers leaked details for almost 44 million of the company's customers. The hackers claimed the data came from an exposed MongoDB server they found online, which contained the details of users who signed up on the site until September 22, last year, including names, emails, IP addresses, and even MD5-hashed passwords. In a message posted on Russian social media site VK, the company confirmed the security breach on Sunday.
General tech and privacy
US ISP geolocation collection: Ten of the top 15 mobile carriers in the US collect geolocation data and provide no way for consumers to opt out of this process, according to the answers the carriers provided to the FCC last week. In their responses, companies generally cited the need to comply with law enforcement requests as well as FCC rules as their reason for being unable to allow consumers to opt out of collection and retention, Cyberscoop reported.
New Microsoft UEFI specs: Microsoft has announced a new security requirement for software developers that want to build apps on top of UEFI-based systems.
Tor Project worried about Google's MV3: The Tor Project expressed its worries about Google's plan to implement its immensely-criticized Manifest V3, a new set of rules for what kind of access extensions have to browser features. Tor developers said that this new restrictive extensions API would hinder its Snowflake anonymization extension, and not just ad-blockers and security extensions, as it was initially thought.
Government, politics, and policy
Rights group pressure US authorities on NSO Group: A coalition of human and privacy rights organizations have sent an open letter [PDF] to officials from the US Departments of Commerce, State, Energy, and Defense, and have asked them not to consider overturning sanctions they imposed on NSO Group in November last year. According to John Scott Railton of Citizen Lab and one of the letter's signatories, NSO Group representatives have been engaged in lobby efforts to have the sanctions lifted.
NATO investigating hacker sale of missile firm data: NATO officials said they are trying to assess the impact of a security breach at French arms company MBDA Missile Systems. Initially, on August 1, MBDA denied getting hacked, but the company had to backtrack on its statement after hackers started selling more than 80GB of its internal files, including weapons design systems, for 15 BTC. The company told the BBC that the data was not sensitive, but the British news outlet also found documents labeled "NATO CONFIDENTIAL," "NATO RESTRICTED," and "Unclassified Controlled Information" in the files being sold online.
Cyber-attacks on Moldova: Moldova's cybersecurity agency said that around 80 government websites were hit by attacks last week after the Killnet Russian hacktivist group announced a coordinated campaign against its government.
Cyber-attacks on Montenegro: The US Embassy in Montenegro issued a security alert on Friday about an ongoing cyber-attack that hit local government websites and services. Montenegro's security service said the attack hit attack IT systems of the Minister of Public Administration and blamed it on the Russian government. France's ANSSI security agency has been involved in the small Balkan state's response to the attack.
Cyber-attacks on Slovenia: A cyber-attack also hit the Administration for Protection and Rescue of the Republic of Slovenia (URSZR), but government officials said that emergency services, such as the 112 number, were not impacted. Officials blamed the incident on outdated older software and said they plan to replace all impacted systems. Slovenia's CERT team said that despite copies of its incident report leaking online, it would not comment on the incident as the report was still labeled TLP:RED.
The US is hiring "nation state hackers": Now's your chance!
Interested in becoming a nation state hacker? We will develop your skills in offensive and defensive cyber operations. Defend. Attack. Exploit. goarmy.com/careers-and-jo…
— U.S. Army Chief of Cyber (@ArmyChiefCyber) 10:41 PM ∙ Aug 26, 2022
Sponsor section
RunZero (formerly Rumble Network Discovery) is one of this newsletter's four main supporters and this week's featured sponsor. Last week, the runZero team held a live chat about the history and evolution of network scanning, which we thought would be an ideal watch/listen for anyone looking to learn more about this topic:
Cybercrime and threat intel
Tornado Cash arrest: Dutch authorities have extended the arrest order of Tornado Cash developer Alexey Perksov for another 90 days as they prepare the case in which he's accused of facilitating and concealing money laundering operations on the Ethereum blockchain.
KEV update: CISA has updated its KEV database with ten new vulnerabilities that are currently being actively exploited. This includes vulnerabilities for dotCMS, Apache CouchDB, Apache APISIX, Spring Cloud, WebRTC, Grafana, DOPSoft, PEAR's Archive_Tar, and Apple's iOS and macOS.
Tykelab linked to SS7 attacks: Investigative journalism group Lighthouse Reports said that Italian company Tykelab appears to be in possession of a global tellecommunications tracking system that allows it to track mobile devices by abusing the SS7 telephony protocol. The news comes after Tykelab was linked to a powerful Android and iOS spyware strain named Hermit back in June by cybersecurity firm Lookout. Now, Lighthouse Reports says that Tykelab, which appears to be a front for known Italian surveillance vendor RCS Lab, has also been abusing "dozens of phone networks, often on remote Pacific islands" to spy on targets across the world, in countries such as Italy, Libya, Nicaragua, Malaysia, Costa Rica, Iraq, Mali, Greece, and Portugal.
Venom RAT: CyberInt has a report out on a new remote access trojan sold on underground markets called Venom RAT.
Void Griffon: Trend Micro published a report on Void Griffon, a cybercrime group founded in 2006 that has been managing a bulletproof hosting service since 2015 for the benefit of other operations. Trend Micro says Void Griffon operates server infrastructure in Russia, Germany, the US, and the UK.
Malware technical reports
Gwisin ransomware: South Korean security firm SK Shielders published a technical report [PDF] on the new Gwisin (Ghost) ransomware strain, which has been heavily hitting South Korean companies in recent weeks.
Infosec industry
New tool—Ghidrathon: Mandiant open-sourced last week a new tool called Ghidrathon, an extension that adds Python 3 scripting capabilities to the Ghidra reverse-engineering toolkit. Ghidra natively supports scripting in Java and Jython (through which Python 2 extensions were typically loaded). Ghidrathon replaces the existing Python 2 extension implemented via Jython with its own system.
New tool—JWT Reauth: NCC Group open-sourced a new tool called JWT-Reauth, a Burp plugin to cache authentication tokens from an "auth" URL and then add them as headers on all requests going to a certain scope.
New tool—Matano: Software engineer Samrose Ahmed has launched a new open-source project called Matano, a serverless security lake platform for AWS.
TL;DR: Matano is a high-scale, low-cost, serverless platform deployed to your AWS account that lets you ingest logs from any source, transform and normalize them according to a standard schema such as the Elastic Common Schema, store logs in S3 object storage, query them from an Apache Iceberg data lake, and create realtime detections as code using Python.




