Risky Biz News: CryWiper hits Russian courts and mayor offices in data-wiping attacks
In other news: LastPass discloses second breach; Google exposes new spyware vendor; Guatemala government hit by ransomware.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
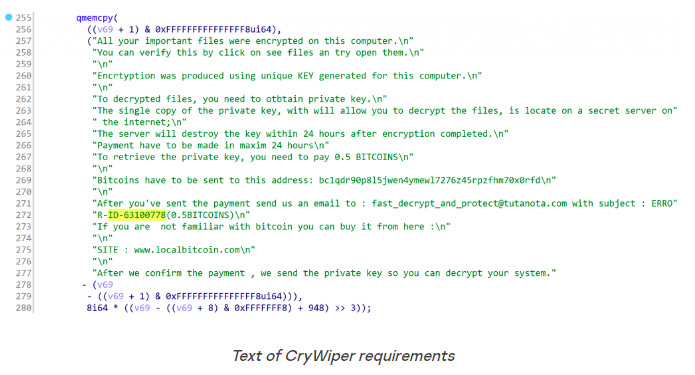
Judicial courts and mayor officers across several Russian regions have been hit by a new data-wiping trojan, according to reports from Russian antivirus maker Kaspersky and local news outlet Izvestia.
Named CryWiper, the malware goes through the motions of a ransomware attack, where it scrambles files and leaves a ransom note demanding money. But Kaspersky researchers say they found evidence of data destruction routines, meaning that even if victims paid the attackers, they would not be able to recover their files.
Neither Kaspersky nor Russian government officials have formally attributed CryWiper to any specific group or entity, but the attacks over the past month are most likely connected to the Russian-Ukrainian conflict, which involved the deployment of multiple wipers, on both sides of the conflict.
Ukraine was hit the most, with wipers such as WhisperGate, HermeticWiper, IsaacWiper, CaddyWiper, and DoubleZero.
Russia wasn't spared either, being hit in March by another wiper posing as run-of-the-mill ransomware, a wiper named RuRansom.
Breaches and hacks
LastPass discloses second breach this year: Password management utility LastPass says that a threat actor has breached one of its cloud storage servers using information the company believes was initially stolen during a previous security incident that took place in August 2022. LastPass says the intruder gained access to "certain elements of our customers' information," but that account master passwords remain safely encrypted. The company says it is working with Mandiant and law enforcement to investigate the incident. The incident also impacted the infrastructure of GoTo, a sister company part of the LogMeIn group.
Guatemala ransomware attack: The Guatemala government says it is investigating a ransomware attack that impacted the IT network of the Ministry of Foreign Affairs. The Ministry's data was added to the leak site of the Onyx ransomware group on September 27 and was added again on November 21, according to a report from The Record.
Full Medibank dump: The REvil ransomware gang has released the entire data set the group has stolen from Australian healthcare insurer Medibank. The data was published after the Australian company refused to pay the gang's extortion demand following a security breach in mid-October. Medibank has officially confirmed the leak of its entire data, which includes the personal and medical information of 9.7 million current and former customers.
Nomad Bridge hack: Google's Mandiant has a post-mortem report on the bug that led to the very "public" hack of the Nomad Bridge cryptocurrency exchange.
Vatican DDoS: The official website of the Vatican went offline on Wednesday following a DDoS attack carried out by pro-Russian hacktivists. As CNA points out, the attack came a day after Moscow criticized Pope Francis's latest condemnation of Russia's invasion of Ukraine.
General tech and privacy
Google sues review scammer: Google has filed a lawsuit against the owners of an online service called G Verifier that was allegedly defrauding small businesses by impersonating Google in telemarketing calls. Google said G Verifier was calling small business owners and offering to set up Google Business Profiles, a service that Google was providing for free. In addition, Google said that G Verifier agents also offered to provide fake reviews on the Business Profiles and boost a company's reputation. The lawsuit also alleges that G Verifier also ran websites that sold fake reviews, either positive or negative, to manipulate a company's business profile in Google Search results and Google Maps listings.
12k Twit accounts unsuspended: Twitter has unsuspended more than 12,000 accounts this past week, and the vast majority are linked to QAnon, the far-right, and old Russian bot farms.
Amazon Security Lake: Amazon has launched a new product called Security Lake, a service that can aggregate security feeds and data from cloud systems, on-premises, and custom sources, to help security teams have a better view of their security posture and threat levels. The service is currently in preview.
TrustCor removed from Mozilla root store: Mozilla's security team has decided to remove the TrustCor certificate authority from the Firefox root store, a system that controls which certificates are trusted by the Firefox browser. The decision comes after a group of academics found ties between the Panamanian company and companies from the surveillance industry, ties that were covered in this WaPo report in more depth. Although there was no official statement, Microsoft also appears to have removed TrustCor support from Edge hours before Mozilla's public announcement.

Government, politics, and policy
US shoots down US-Cuba subsea cable: The US Department of Justice advised the Federal Communications Committee to deny the application of two US telecom companies to build a subsea cable system to link the United States with Cuba. The DOJ says that its vision for the internet is for "an open, interoperable, secure, and reliable" system, which the Cuban government does not share. More from Assistant Attorney General Matthew G. Olsen of the Justice Department's National Security Division.
"As long as the Government of Cuba poses a counterintelligence threat to the United States, and partners with others who do the same, the risks to our critical infrastructure are simply too great."
South Dakota bans TikTok: South Dakota Governor Kristi Noem has banned the use of the TikTok mobile application on devices of state employees and contractors. Noem said the ban is the state's response "to the growing national security threat posed by TikTok due to its data gathering operations on behalf of the Chinese Communist Party (CCP)."
Spain refuses to answer spyware questions: Esperanza Casteleiro, the director of Spain's main intelligence agency, declined to answer questions addressed by members of the European Parliament related to Spain's repeated use of spyware and surveillance products against local political figures and Catalan pro-independence leaders. In a meeting of the EU's PEGA committee this week, Casteleiro restricted herself to explaining how the Spanish secret services operate and their legal framework but nothing more. In a report released in November, the PEGA committee said that many EU member states are using the blanket excuse of "national security" to cover up the abusive use of spyware for petty political reasons. [Additional coverage in Euronews]
Albania charges five government workers: Prosecutors in Tirana have charged and asked for the house arrest of five government employees in connection to an investigation of a series of cyberattacks carried out by Iranian state-sponsored hackers that crippled multiple Albanian government systems in July this year. Prosecutors say the accused failed to apply security updates to government systems and also failed to detect that hackers had been in their network as far back as April 2021. Albania cut diplomatic ties with Iran following the incident and also considered invoking NATO's infamous Article 5 over Iran's actions.
Dutch emergency warning: The Dutch government just told its citizens to stock up on food and medicine in the case of a national emergency, which also includes the likes of a debilitating cyber attack. Also, a nuclear attack. Thanks for the apocalyptic reminder, but a Happy Holidays would have sufficed!
Sponsor section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year, in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
Cybercrime and threat intel
Google exposes new spyware vendor: Google's TAG security team has publicly exposed the identity of a new commercial spyware vendor. Google says that Variston IT, a company based in Barcelona, Spain, is the author of a tool named Heliconia that can exploit vulnerabilities in products such as Chrome, Firefox, and Microsoft Defender. Google TAG researchers said they linked several past vulnerabilities to Variston's Heliconia framework. They said that while the vulnerabilities are patched now, they were most likely exploited as zero-days by Heliconia's customers.
"TAG became aware of the Heliconia framework when Google received an anonymous submission to the Chrome bug reporting program. The submitter filed three bugs, each with instructions and an archive that contained source code. They used unique names in the bug reports including, 'Heliconia Noise,' 'Heliconia Soft' and 'Files.' TAG analyzed the submissions and found they contained frameworks for deploying exploits in the wild and a script in the source code included clues pointing to the possible developer of the exploitation frameworks, Variston IT."
Intellexa sold spyware to Sudanese militia: A joint investigation by Israeli newspaper Haaretz, Greek newspaper InsideStory, and Lighthouse Reports has found that the so-called Intellexa "intelligence alliance" has sold its Predator spyware toolkit to the Rapid Support Forces, a paramilitary militia group linked to several cases of human rights abuses during the Sudanese political crisis of 2019, and most notoriously, to the Khartoum massacre.
NSO sued by journalists: Fifteen journalists, along with members of El Faro, an independent news agency in Central America, filed a lawsuit in a US court against Israeli spyware maker NSO Group. The lawsuit alleges that NSO Group broke multiple laws, including the US Computer Fraud and Abuse Act (CFAA), when it designed and then helped deploy the Pegasus spyware on the devices of El Salvador journalists and human rights activists.
"The plaintiffs are filing the lawsuit in the same district in which two other lawsuits have been filed against NSO Group: one by Apple and one by WhatsApp. The Supreme Court is expected to decide imminently whether to grant a cert petition filed by NSO Group in the WhatsApp case."
Lilac Wolverine: Abnormal Security has a detailed report on Lilac Wolverine, a Nigeria-based BEC group that's specialized in launching large-scale attacks against personal email accounts rather than corporate targets. Abnormal's research team says the group typically operates by asking the email recipients for help in purchasing gift cards for a friend or relative and that the tactic has been very successful, primarily due to most people's willingness to help others in a bind.
Predatory lending apps: Mobile security firm Lookout found 251 Android and 35 iOS lending apps that engaged in predatory and abusive behavior toward their users. The apps offered users loans but, in return, requested access to excessive permissions and personal user information, such as contacts, local files, and SMS messages. The apps also used hidden fees, high interest rates, and repayment terms that were different from the ones listed on their official app store listings. Once users defaulted on their loans, the apps would harass and threaten borrowers and even go as far as notify friends and other contacts in schemes meant to shame and put pressure on the borrower. Lookout said the Android apps were downloaded more than 15 million times and the iOS apps ranked high in the App Store finance category before being removed by both Apple and Google.
Insivible npm packages: JFrog researchers have found that several of the security tools built inside the npm CLI fail to show warnings for any malicious library that contains a dash or hyphen in their version number, in the form of 1.2.3-a.
WordPress backup scans: Wordfence says that it detected more than 70 million scan events of threat actors probing WordPress sites and looking for backup archives. Wordfence says that backup files often contain credentials to access a WordPress site and its database, which makes them ideal targets for threat actors looking to hijack and backdoor an unprotected website.
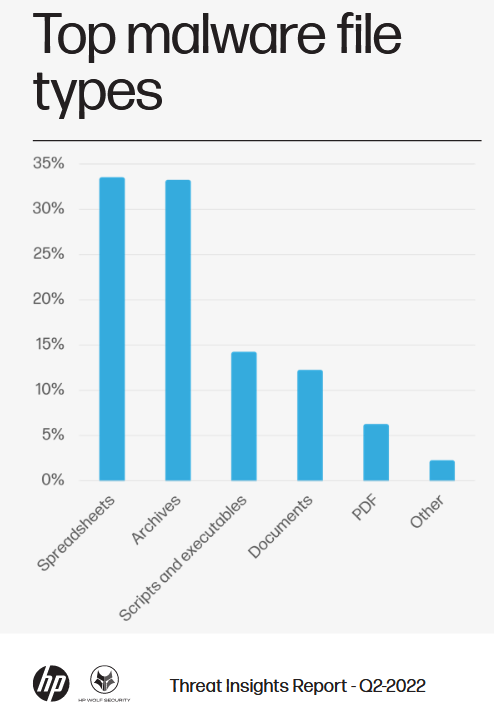
Malspam trends: HP's Wolf Security says that archive files have almost surpassed spreadsheets as the preferred method of delivering malspam in the second quarter of 2022—per its quarterly threat report.
Xiongmai exploitation: Threat intelligence company VulnCheck has a very interesting write-up about seven vulnerabilities in Xiongmai IoT devices, five of which have been exploited in the wild. Although the attacks have gotten little attention, VulnCheck believes they should, as there are more than 200,000 Xiongmai devices connected to the internet that can be ideal cannon fodder for botnets and initial access brokers.
Malware technical reports
KmsdBot goes down: Akamai researchers said they found a bug in the C&C communication system used by the KmsdBot cryptomining botnet that allowed them to crash the malware on all infected systems worldwide. Bummer! Anyway...
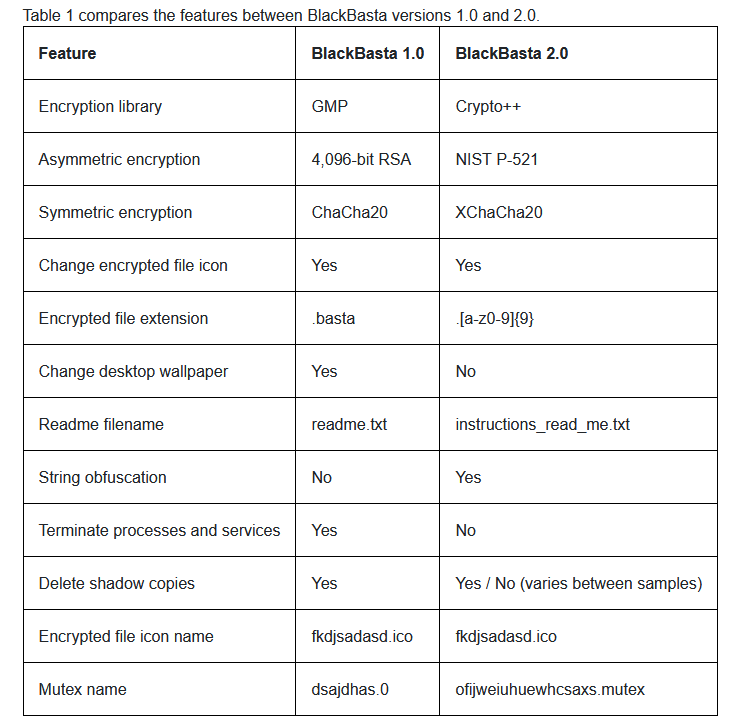
Black Basta: Zscaler has a breakdown of updates to the code of the Black Basta ransomware during November 2022. These include changes to the ransomware's file encryption algorithms, the introduction of stack-based string obfuscation, and the use of per-victim file extensions. Zscaler researchers believe the modifications are an attempt to better evade antivirus and EDR solutions.
LockBit 3.0 Black: Sophos published a report on the LockBit 3.0 ransomware, also known as LockBit Black. The report found several similarities between the LockBit 3.0 code and BlackMatter (also previously reported here and here) and the presence of various scripts that try to add self-spreading worm capabilities to the LockBit code.
Cuba ransomware: CISA and the FBI have published a joint report with TTPs for the Cuba ransomware. While the ransomware has been active since December 2021, the two agencies note that this year the ransomware has gone through considerable updates, including what appears to be a working relationship between Cuba operators and the RomCom RAT team and the Industrial Spy ransomware gang.
Trigona: There's also a new ransomware strain in town, and its name is Trigona.
Schoolyard Bully: Mobile security firm Zimperium said it discovered a new Android trojan named Schoolyard Bully that has been active since 2018. Disguised as educational apps in both the Google Play Store and other third-party app stores, this malware has been downloaded more than 300,000 times across 71 countries. Zimperium says the trojan appears to be focused on stealing Facebook credentials.
Eternity Stealer: Something we missed over the last weekend was this technical analysis of the Eternity Stealer. Nothing super fancy, just your regular infostealer trojan. Probably the most "interesting" thing in the whole report is that Eternity steals credentials for the OBS and Twitch streaming apps.
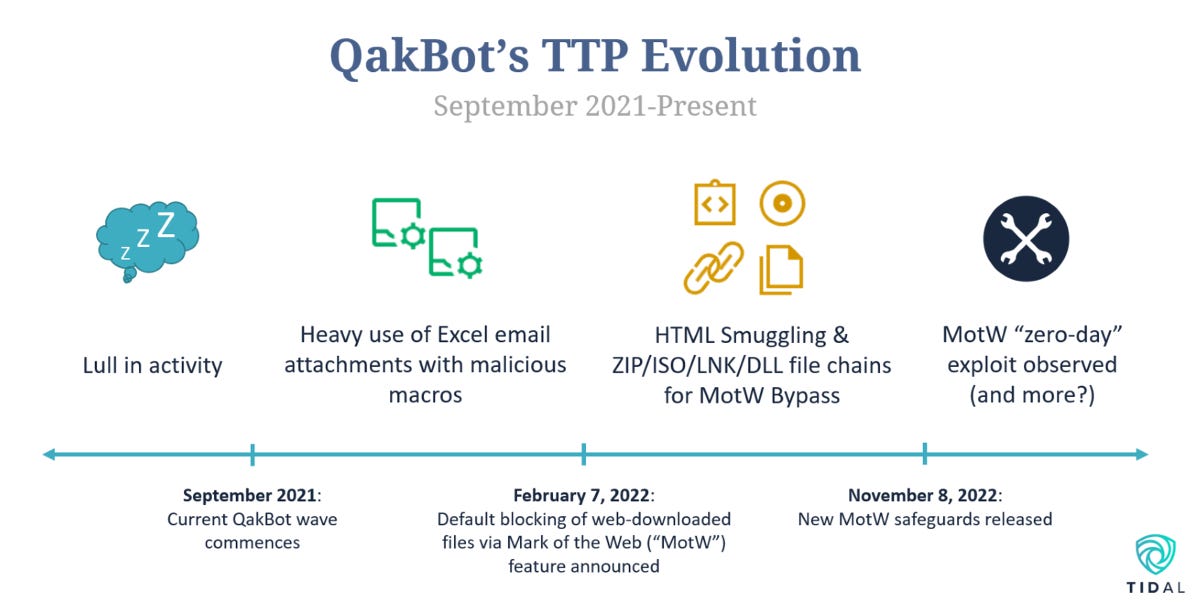
QakBot TTP evolution: A yummy report from Tidal on how QakBot TTPs have evolved over the past year.
APTs and cyber-espionage
TAG-56: Recorded Future says it spotted a spear-phishing campaign conducted by TAG-56, a cyber-espionage group the company considers to have an Iran nexus. The campaign took place in early November and targeted a Washington think tank using email lures related to the 2022 Sir Bani Yas Forum, an economic forum hosted by the government of the United Arab Emirates (UAE).
ScarCruft's Dolphin: ESET has put out a report on Dolphin, a new backdoor they spotted in attacks carried out by the ScarCruft APT. The malware can monitor local drives for specific content, steal files of interest, monitor keystrokes, take screenshots, and extract and steal credentials from browsers. Evidence suggests the backdoor has been used in attacks as early as April 2021.
"A notable feature of earlier Dolphin versions we analyzed is the ability to modify the settings of victims' signed-in Google and Gmail accounts to lower their security."
APT 29's Slack abuse: Chinese security firm QiAnXin has a report out detailing a recent APT29 campaign targeting Italy, where the Russian hacking group has deployed versions of the EnvyScout malware. QiAnXin notes that the attacks used collaboration platform Slack as a C&C channel and payload delivery system. Previously, APT29 used enterprise apps Dropbox and Trello in a similar fashion.
Operation ShadowTiger: The same QiAnXin team has a second report out on Operation ShadowTiger, a series of attacks carried out by an East Asian APT group they call Tiger Hibiscus, or APT-Q-11. The campaign took place from 2019 to 2021 and involved the use of spear-phishing, (browser and intranet) zero-days, and an intranet watering-hole attack.
LuckyMouse: Have some LuckyMouse APT TTPs, courtesy of Sekoia.\
Metador's Mafalda: SentinelOne has published a technical breakdown of Mafalda, a malware implant used by the mysterious Metador APT.
Vulnerabilities and bug bounty
Car hacking #1: Security researchers Sam Curry, Brett Buerhaus, and @_Specters_ have found a vulnerability in the web portal of Hyundai cars that could be used to take over a car owner's account and remotely control the locks, engine, horn, headlights, and trunk of all vehicles made after 2012. Curry&friends said the vulnerability resided in the fact that both portals did not require users to confirm their email addresses, allowing the researcher to use a malformed email address to access other users' accounts. The vulnerability also impacted Genesis cars, which is Hyundai's line of luxury cars sold under its own brand. Hyundai fixed the issue following the researchers' report.
Car hacking #2: The same trio also found a vulnerability in the SiriusXM app that ships with cars from Honda and Nissan. Curry&friends said the vulnerability could be used to remotely unlock, start, locate, flash, and honk the horn of cars running the vulnerable app. Unlike the first vulnerability, to exploit this one, an attacker would have had to know a targeted car's VIN number. The same app also ships with cars from BMW, Hyundai, Jaguar, Land Rover, Subaru, and Toyota, although the researchers said they didn't test these models. SiriusXM has since fixed the vulnerability.
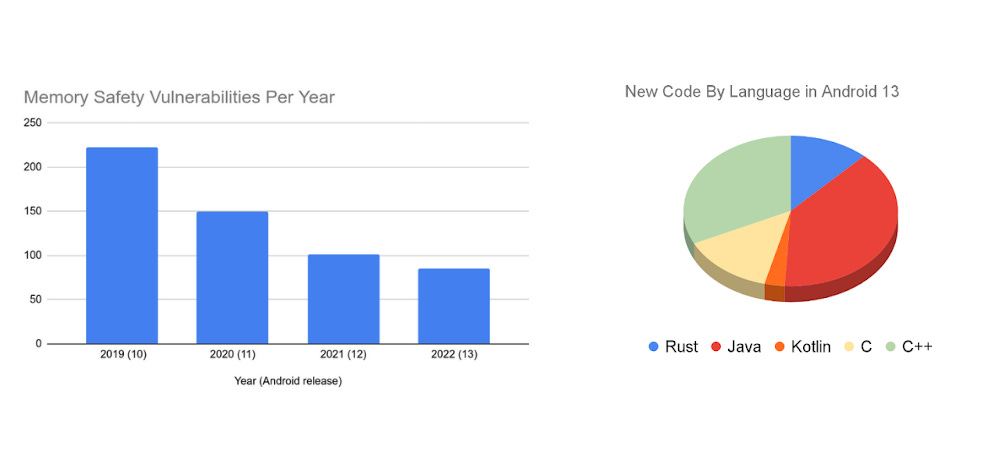
Android and safe languages: Google says that Android 13, the latest version of the Android mobile operating system that was released in August this year, is the first Android release where a majority of new code added to the project was written in a memory-safe language, such as Rust, Java, and Kotlin. The OS maker noted that since shifting its focus on using memory-safe languages, the number of memory safety vulnerabilities reported in the Android OS has gone down by more than half.
e-Tugra vulnerabilities: Security researcher Ian Carroll has disclosed a series of misconfigurations in the infrastructure of e-Tugra, a Turkey-based certificate authority. Carroll said the misconfigured infrastructure allowed them to get access to backend systems controlling the CA's systems and even to massive troves of highly-sensitive customer data.
"In many regards, certificate authorities are audited comprehensively against industry-specific audit standards. Certificate authorities also routinely get hacked. Despite this, not a single certificate authority runs a bug bounty program, and of the major CAs, only GlobalSign and Let's Encrypt even offer a security.txt to help disclose issues. Only an annual penetration is generally required of CAs."
Log4Shell, one year later: Vulnerability management platform Tenable says that following a series of tests, it found that 72% of organizations still remain vulnerable to the Log4Shell vulnerability, disclosed a year ago in December 2021. Tenable says that 28% of organizations across the globe have fully remediated Log4Shell as of October 1, 2022, doubling the figure from May 2022.
FreeBSD vulnerability: The FreeBSD project has issued a rare security advisory, this time for a vulnerability in the ping utility (CVE-2022-23093). Probably not that bad, though.
"The memory safety bugs described above can be triggered by a remote host, causing the ping program to crash. It may be possible for a malicious host to trigger remote code execution in ping. The ping process runs in a capability mode sandbox on all affected versions of FreeBSD and is thus very constrainted in how it can interact with the rest of the system at the point where the bug can occur."
Linux vulnerability: Qualys researchers have found a race condition vulnerability (CVE-2022-3328) in one of the default packages installed on several Linux distros, including the highly popular Ubuntu.
Huawei hypervisor vulnerability: More than a year after it was patched, Impalabs has published details on CVE-2021-39979, a vulnerability that can be used to execute malicious code inside the secure hypervisor used by Huawei's HarmonyOS mobile operating system. Impalabs discovered the vulnerability during their extensive research of the HarmonyOS security hypervisor.
iOS updates: Apple has also released iOS 16.1.2, which the company marked as a security update, so make sure to update.
Snyk vulnerabilities: There are also two code injection vulnerabilities in the Snyk CLI and IDE plugins, two popular source code-checking utilities.
Hive Social vulnerabilities: Researchers have found several vulnerabilities in Hive Social, one of the many social networking apps that have popped up as Twitter replacements. The vulnerabilities can allow attackers to access a user's private data, including private posts, private messages, shared media, and deleted DMs. Shortly after researchers publicly disclosed their findings and said that Hive Social lied about fixing the issues, the company announced it was temporarily shutting down servers for the upcoming days to finally address the vulnerabilities.
Vulnerabilities in remote keyboard apps: Synopsys researchers said they found seven vulnerabilities across three Android apps that can be used as remote keyboards for a user's computer. The research team says the vulnerabilities can be used to intercept keystrokes and/or run malicious code on connected computers. The three apps are named Lazy Mouse, Telepad, and PC Keyboard, and they have more than two million combined downloads via the Google Play Store. None of the app developers replied to Synopsys's reports, and the vulnerabilities remain unpatched.
Delta Electronics vulnerabilities: Austrian cybersecurity firm CyberDanube has helped patch several vulnerabilities in Delta Electronics wireless devices, typically deployed in industrial networks to provide internet connectivity for ICS/SCADA equipment in remote locations.
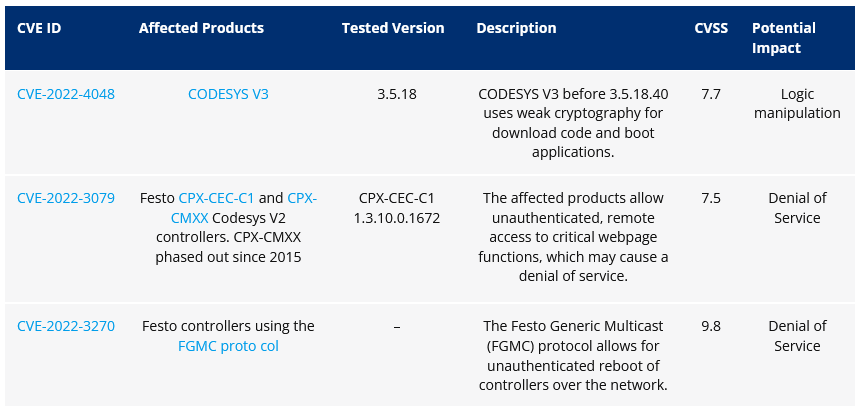
OT vulnerabilities: Security firm Forescout says it found and helped patch three vulnerabilities impacting industrial equipment. The vulnerabilities impact the Festo automation controllers and the CODESYS runtime. The two Festo vulnerabilities allow unauthenticated reboots of devices, which could pose a big physical security risk in some industrial networks.
Infosec industry
AllInfosecNews: Looking for an aggregator for infosec news, podcasts, videos, and jobs? Meet AllInfosecNews from Foorilla. This is an ideal default browser homepage.
Pwn2Own ICS hacking contest: ZDI has published the rules and targets for its Pwn2Own hacking contest that will take place in Miami in mid-February. This is the Pwn2Own contest that's dedicated to hacking ICS gear. For this edition, the target list includes equipment from the likes of Prosys, PTC, Triangle Microworks, Softing, AVEVA, and Inductive Automation.
Black Hat USA 2022 videos: Talks from the Black Hat USA 2022 security conference, which took place in August, are finally out and available on YouTube. Enjoy!
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




