Risky Biz News: Crypto-wallet service seized for helping ransomware gangs launder stolen funds
In other news: DARPA launches program to convert C code to Rust; a Chinese APT hacks an ISP to hijack software updates; class-action lawsuits filed over massive 2.9 billion breach at background-check firm.

This newsletter is brought to you by Material Security, the company that secures the cloud office with unified email security, user behavior analytics, and data loss prevention for Microsoft 365 and Google Workspace. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

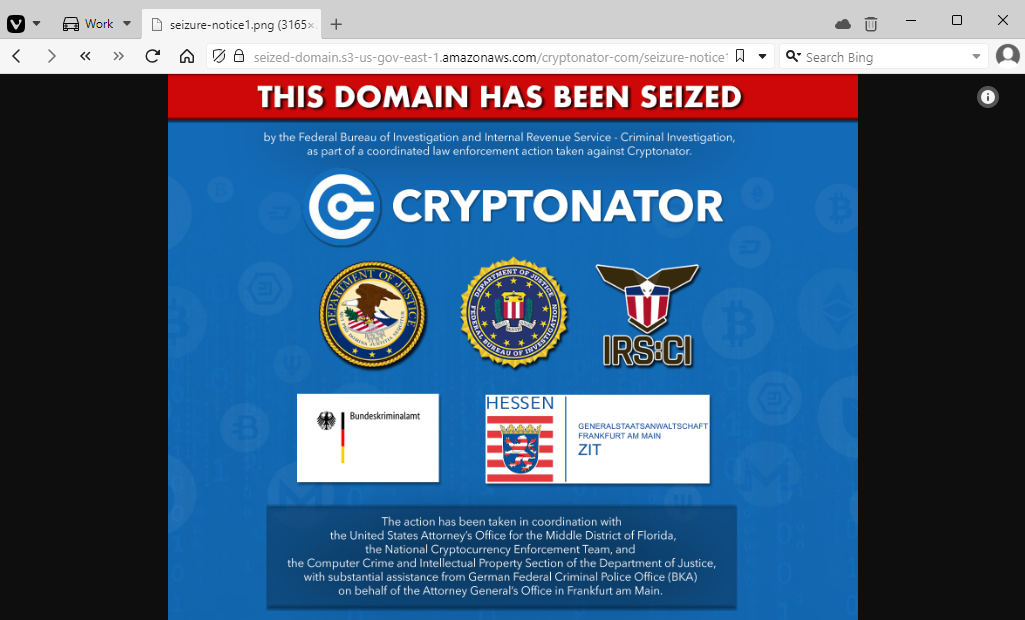
German and US authorities have seized a crypto-wallet service named Cryptonator on charges of money laundering and operating an unlicensed money service business.
The service allowed individuals to set up crypto-wallet funds that could receive and send funds from and to any type of blockchain service, effectively operating as a "personal cryptocurrency exchange" for each customer.
Officials say Cryptonator failed to implement anti-money laundering protections and knowingly allowed its service to be used for illegal activities.
Authorities seized the site's official domain at cryptonator.com and charged its founder and CEO, a Russian national from the city of Perm named Roman Pikulev.

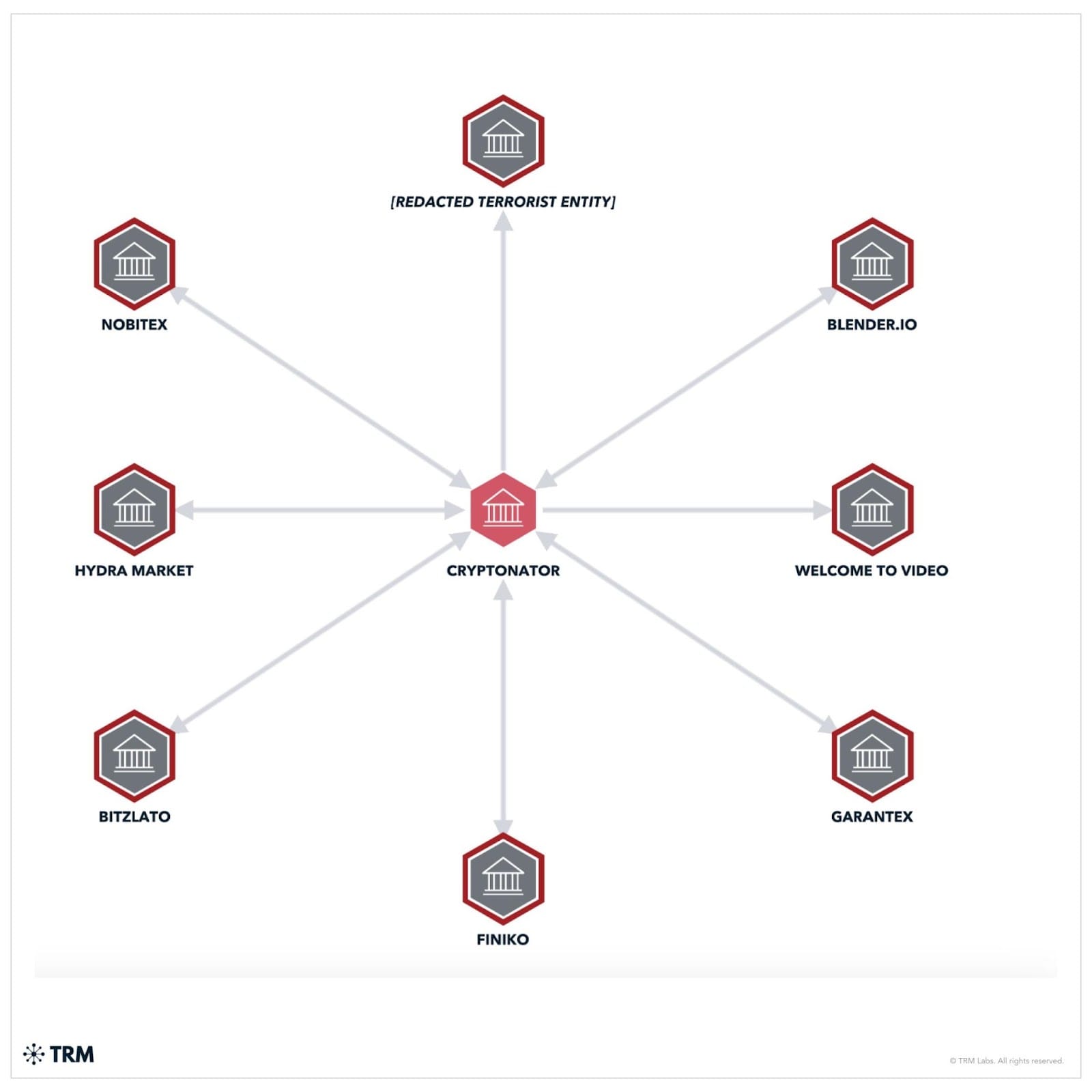
According to court documents, the service has been involved in transactions worth around $1.4 billion. According to blockchain tracking company TRM Labs, of these, more than $306 million have been linked to illegal sources, such as ransomware gangs, online scams, darknet markets, crypto-heists, and sanctioned entities.
- $25,000,000 with darknet markets, fraud, and carding shops
- $34,500,000 with scam addresses
- $80,000,000 with high-risk exchanges
- $8,000,000 with addresses associated with ransomware groups
- $54,000,000 with addresses associated with hacks and crypto theft operations
- $34,000,000 with cryptocurrency mixing services
- $71,000,000 with sanctioned addresses
Officials say Pikulev, who often signed documents as Roman Boss, knew the site was involved in illegal activity and never implemented any Know-Your-Customer (KYC) features, allowing customers to register fake or anonymous accounts.
He also allegedly built features to help customers anonymize the source of funds arriving in Cryptonator wallet addresses.
Pikulev and Cryptonator join a long list of cryptocurrency services seized by US and European authorities for enabling crypto money laundering. Several of these were based in Russia or were built by Russian developers and were linked to laundering ransomware profits.
Breaches, hacks, and security incidents
Rabbit blames breach on former employee: AI startup Rabbit says that a contentious security breach from earlier this year was caused by a now-fired employee. In late June, a group of security researchers named Rabbitude claimed that Rabbit was exposing API keys that granted access to its source code and past AI agent responses. The group claimed that the AI startup did not reply to attempts to disclose the incident and only rotated the API keys after the breach became public. Rabbit now says that the incident was caused by one of its employees who leaked the API keys to the group, which the company chose to describe as "a self-proclaimed hacktivist group." Rabbit says it also commissioned a security audit of its infrastructure, which now appears to be secure.
Illinois voter data leak: A security researcher has discovered 13 database servers that were not protected with passwords that contained voter records for Illinois residents. According to DataBreaches.net, the data leak is different from ones in the past because highly sensitive personal information was also included in the leak. This included Social Security numbers, driver's license numbers, dates of birth, and precise physical addresses.
Metal Materials incident: In SEC documents, Metal Materials has blamed a recent IT outage on a former executive who intentionally deactivated the company's domain renewal procedure, leading to its official website and email servers going down in late July. [h/t Kevin Beaumont]
Date Hot Brunettes hack: The data from dating site Date Hot Brunettes was leaked online and is now on HIBP. The site has closed down a few months back. The leaked data included over 1.5 million unique email addresses along with IP addresses, usernames, user-entered bios, and MD5 password hashes.
BangBros leak: Adult movie studio and website BangBros has leaked the personal details of more than 37,000 users. The data leaked via an unsecured Elasticsearch database. According to CyberNews, the data included details such as usernames, IP addresses, user agents, geolocation data, and upvotes and downvotes on model pages.
Comprasal leak: Hacktivist group Guacamaya claims to have hacked Comprasal, the El Salvador government's electronic procurement system. The group claims it plans to leak the data of more than 15,300 state contractors. They haven't shared a reason for the leak, but the group, which now goes under the name of CiberinteligenciaSV, has leaked a bunch of El Salvador data in the past, and this appears to be some sort of grudge against the country and its current government.
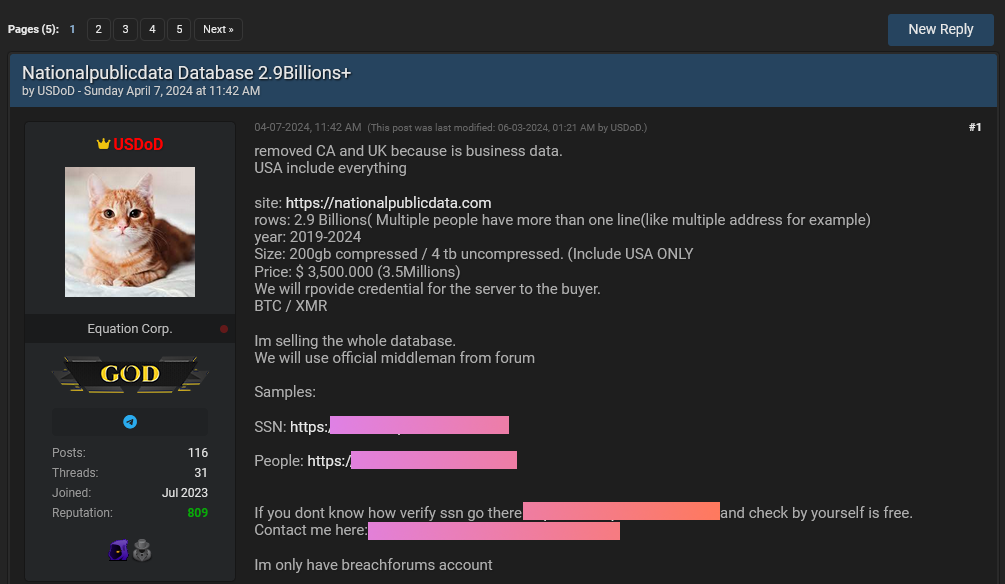
NPD/Jerico data breach and CLA: Background-check company Jerico Pictures is being sued in three class-action lawsuits over an alleged data breach that exposed 2.9 billion personal records. The company is known for doing business as National Public Data. A threat actor named USDoD claimed to have hacked the company earlier this year in April and advertised its data on an underground hacking forum for a whopping $3.5 million. The plaintiffs claim the company has failed to address the hack rumors. The lawsuit also claims the company illegally collected much of the data against the will of many of the affected individuals. The leaked data allegedly also includes entire family trees and information on dead people. [Additional coverage in Bloomberg Law] [h/t DataBreaches.net]
General tech and privacy
ICO warns on children's privacy: The UK's privacy watchdog has called on 11 social media and online streaming platforms to improve their children's privacy practices or face possible fines. The ICO says it audited 34 platforms and found that 11 use default settings for children's accounts that break UK privacy laws. Platforms were caught using children's data for targeted advertising, enabling data and geolocation tracking settings, and not requiring parental controls for setting up new accounts for children under the age of 13. The ICO did not name the platforms.
Meeting on connected car risks: The US and key allies from Europe and Asia held a high-level meeting last week to discuss the new risks emerging from modern internet-connected cars.
US sues TikTok: The US Federal Trade Commission and the Department of Justice have sued social media giant TikTok for violating US children's online privacy. The agencies say TikTok failed to notify and obtain parental consent before collecting and using personal information from children under the age of 13. TikTok later allegedly used the data to target kids with advertising. The FTC says it learned of TikTok's practices from the company's own employees. TikTok broke the same rules and was previously subject to a 2019 FTC restraining order, which has now fast-tracked the current lawsuit.
Datarade scandal in Germany: A Netzpolitik investigation has found that a German government startup fund was used to support Datarade, a data marketplace that facilitates the sale of intrusive mobile app location data.
ROMHacking shuts down: ROMHacking, a website for sharing fixes for old games, has shut down. Game Informer, one of the oldest gaming magazines in the US, also shut down last week, in what appears to be one of the worst weeks for the gaming community in recent years. Also, see next topic.
EU petition against the gaming industry: There's a formal EU petition process taking place in the EU right now to get EU lawmakers to ban gaming companies from shutting down and making games unplayable once they're out of support. The petition has already reached over 10% of the one million signatures it needs in just a few days. TL;DR: Gamers are really mad that gaming studios are intentionally ruining their own games to make you buy their newer ones, which is something that seems to have hit a cord with everyone.
Impact of CrowdTangle's shutdown: A research group named the Coalition for Independent Tech has published a study on the impact the shutdown of Meta's CrowdTangle tool will have on the research community studying social media disinfo and influence operations.
Government, politics, and policy
CISA Chief AI Officer: CISA has named Lisa Einstein as the agency's first-ever Chief AI Officer. Einstein previously served as Executive Director of CISA's Cybersecurity Advisory Committee. The new position will govern CISA's own use of AI and ensure critical infrastructure partners develop and adopt AI in secure ways.
Pentagon cyber policy chief: The Senate on Thursday confirmed Michael Sulmeyer as Assistant Secretary of Defense for Cyber Policy at the Pentagon. He becomes the first individual to hold the position. [Additional coverage in NextGov]
GAO EPA cybersecurity report: A US government audit body says the Environment Protection Agency (EPA) is not doing enough to improve the cybersecurity defenses of US water and wastewater management utilities. A GAO report found the EPA needs to "urgently" develop a national strategy for dealing with cybersecurity threats. The GAO report comes a month after a US Supreme Court decision on the Chevron doctrine that curtails the powers of federal agencies on matters where Congress has not passed specific laws. [Additional coverage in CyberScoop]
US National Counterintelligence Strategy: The US National Counterintelligence and Security Center (NCSC) unveiled the US' new National Counterintelligence Strategy. The document provides a strategic direction for the US federal government and its counterintelligence community to counter foreign intelligence threats and align CI priorities.
- The People's Republic of China (PRC) and Russia represent the most significant intelligence threats, but a range of other state and non-state actors also target the United States. Commercial entities are playing increasingly important enabling roles for FIEs.
- Our leading adversaries view themselves as already engaged in an intense, multifaceted competition with the United States. As such, their intelligence services frequently conduct more aggressive operations that fall in the "gray zone," a space between war and peace that encompasses intelligence activities that push the boundaries of accepted norms, such as covert influence, political subversion, and operations in cyberspace.
- We also see our leading adversaries cooperating more frequently with one another, enhancing the threat they pose to the United States.
DARPA TRACTOR program: DOD research agency DARPA has launched a new program named TRACTOR (Translating All C to Rust) to translate old C source code to the newer Rust programming language. The program will target C code used in DOD legacy apps. DARPA says it will look to create an automated solution to translate the old C code to safe and idiomatic Rust code.
UK ACD 2.0: The UK NCSC says it plans to build a new and improved version of its Active Cyber Defence suite of security tools.
Malaysia establishes NSRC: The Malaysian government has established a National Scam Response Centre (NSRC). The new center will allow the government to receive reports of scams from consumers and quickly mount a coordinated national reply. [Additional coverage in The Malaysian Reserve]
Indonesia blocks DuckDuckGo: The Indonesian government has blocked access to the DuckDuckGo search engine because the site allows users to find pornography and gambling sites. DuckDuckGo said on Reddit there's no way to fight the block. The site is also blocked in China for more than a decade for not complying with Beijing's strict censorship rules.
Russia warns against its own browser: The Russian National Coordination Center for Computer Incidents (NKTsKI) has told Russian companies and users to stop using a Russian-made browser known as Sputnik. The agency has designated the browser as a security risk after the company behind it went bankrupt in 2023. The NKTsKI says the browser's domain is now owned by American company Global Internet Telemetry Measurement Collective and may be used to deliver malicious updates to Russians.
Russia implies of broader Google block: One of the Russian government officials involved in the recent YouTube traffic throttling incident has implied that a broader block of all Google services is also a possibility. [Additional coverage in RuNews24]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Rajan Kapoor, VP of Customer Experience at Material Security, on how threat actors view email inboxes as the targets of their attacks and not just an entry point into organizations.

Cybercrime and threat intel
Tech support scammer sentenced: US authorities have sentenced an Indian man to seven years in prison for his role in a large-scale tech support scam operation. Vinoth Ponmaran was the leader of a scam group that used pop-up windows to trick victims into calling tech support numbers and paying for unneeded IT services. According to US officials, Ponmaran's group earned more than $6 million from over 6,500 across the US and Canada. Most of the victims were elderly citizens.
Project Disrupt arrests: Canadian authorities have detained 10 suspects for their roles in a SIM-swapping gang. The suspects are believed to have stolen more than CAD$1 million from more than 1,500 individuals by taking over their phone numbers and then emptying financial accounts. Most of the gang's members operated out of Toronto. Two suspects are also still at large and wanted by police.
Panamorfi: AquaSec looks at Panamorfi, a threat actor using an open-source Java toolkit to launch DDoS attacks on Minecraft servers by abusing misconfigured Jupyter notebooks.
TryCloudflare campaign: eSentire has published details of a malware campaign that abuses the TryCloudflare service to create one-time (demo) tunnels as part of their malware operations. See a similar report on the same campaign from Proofpoint.
Disabling 2G: Google has reminded users to disable 2G support in their Android devices as a way to prevent threat actors from using Stingray-like devices to blast SMS spam messages to their phones in crowded spaces.
New npm malware: Fifty malicious npm packages were discovered last week. Check out GitHub's security advisory portal for additional details.
Malware technical reports
Rhadamanthys: Security researcher Maor Dayan has published an analysis of Rhadamanthys, an infostealer recently used in a campaign targeting Israeli organizations.
BlankBot: Intel471 has published an overview of BlankBot, a new Android banking trojan. The malware launched in July this year and currently can only target Turkish banks.
Cobalt Strike: Embee Research looks at how to detect early Cobalt Strike downloader scripts.
Sponsor Section
New attacks are harder to spot at greater volumes than your security team can handle. The legacy and so-called modern email security market has left you with two extreme options – write and maintain your own set of detection rules or trust a black box with no way to customize. Either route is a burden on security teams when testing and tuning rules or building and implementing response workflows. Watch a demo to see the Material difference for inbound email detection. Leverage the combined power of AI, behavioral analysis, custom detections, and collective intelligence to thwart new flavors of email attacks with precision and speed.
APTs, cyber-espionage, and info-ops
Fighting Ursa: Russian cyber-espionage group Fighting Ursa (APT28) has been seen using ads for the sale of diplomatic cars as phishing lures to infect diplomats across the EU. The emails advertised an Audi Q7 Quattro for diplomats looking to be stationed in Romania. The lure appears to have been borrowed from fellow Russian espionage group Cloaked Ursa (APT29), which used it to target diplomats working in Ukraine in early 2023—that time with a BMW ad. According to Palo Alto Networks, the Fighting Ursa group is known for repurposing successful tactics—even continuously exploiting known vulnerabilities for 20 months after their cover was blown.

Olympic info-ops: DFRLab takes a deep look at all the Russian disinfo efforts targeting the ongoing Paris 2024 Olympics.
PAN nomenclature: Palo Alto Networks has published a document detailing how it names APT groups and the names of all groups it is currently tracking.
LilacSquid: Security firm HackersEye has published an IR report from an intrusion by the LilacSquid APT at a company. The intrusion took place through the company's Check Point firewall and resulted in the deployment of a Mesh agent on the compromised system.
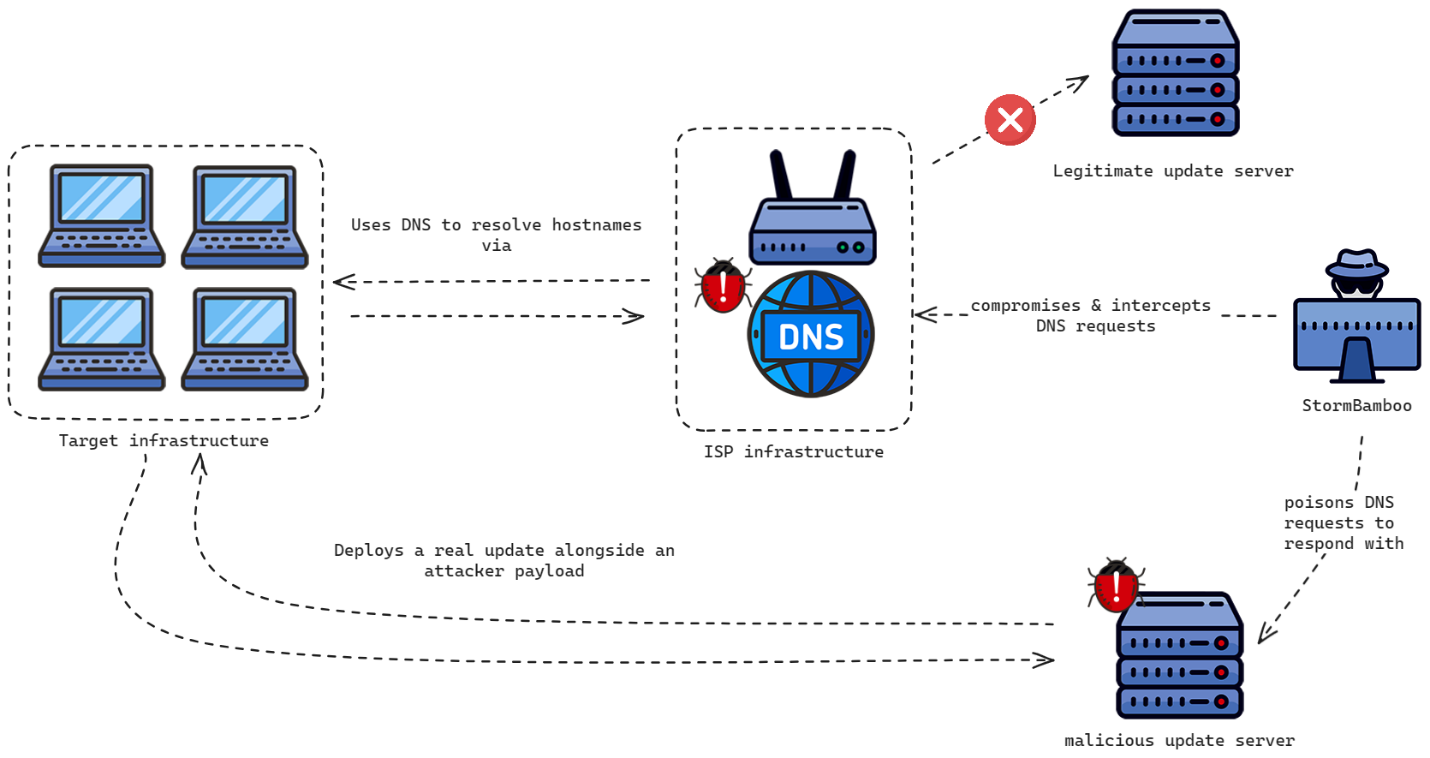
StormBamboo compromises an ISP: A Chinese APT group named StormBamboo (Evasive Panda) has compromised the infrastructure of an internet service provider to infect targets with malware. The attacks took place earlier this year and targeted both macOS and Windows users. Security firm Volexity says StormBamboo modified the ISP's DNS servers to redirect users performing software updates to malicious servers that installed the malware. Only software that used cleartext HTTP connections and didn't validate digital signatures was targeted. Users were infected with backdoors and in some cases with malicious browser extensions.
Vulnerabilities, security research, and bug bounty
First Sequence Sync: Flatt Security's RyotaK has published details on First Sequence Sync, a combination of a race condition and a single packet attack. The technique can be used to send a very large number of packets in a very short period of time. RyotaK proved the attack's potential for bypassing rate-limiting on one-time token authentication.
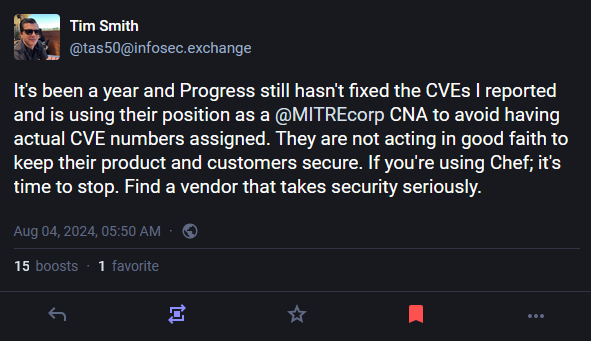
Progress Software disclosure drama: According to software engineer Tim Smith, Progress Software is dragging its feet on fixing a vulnerability in its DevOps automation project Chef. [h/t ScreamingGoat]
SLUBStick attack: A team of academics from the Graz University of Technology has discovered a new side-channel attack named SLUBStick [PDF] that can elevate privileges in the Linux kernel. Researchers say the attack can be used to break out of security containers and works against all modern Linux kernel defenses, including SMEP, SMAP, and KASLR. The attack allegedly has a success rate of 99%. [Additional coverage in Bleeping Computer]
Email server misconfig warning on shared hosting: Some multi-tenant shared hosting providers are running misconfigured email servers that allow threat actors on the same service to impersonate other hosted domains. According to a security advisory by the CERT/CC at Carnegie Mellon University, the issue resides in how the hosting providers have configured their SPF and DKIM settings. The misconfiguration has already been used in the wild this year for a campaign known as EchoSpoofing that abused Proofpoint products and Microsoft customers. Two other shared hosting providers have now also confirmed they are vulnerable.
Unpatched AVTech vulnerability: CISA says that Taiwanese company AVTech has failed to address a major vulnerability in the firmware of its AVM security cameras. The vulnerability (CVE-2024-7029) was discovered by Akamai researcher Larry Cashdollar and independently confirmed by another third party. The issue can allow remote attackers to inject commands in internet-connected AVTech AVM cameras and take over the device without needing to authenticate. Public exploits are already available and are trivial to execute. CISA says AVTech network video recorders (NVRs) may also be vulnerable.
Apache OFBiz exploitation: Threat actors have started exploiting a major vulnerability in the Apache OFBiz open-source ERP solution. The attacks leverage a vulnerability that was initially patched in May but went under the radar for two months before the attacks started. Tracked as CVE-2024-32113, the vulnerability is a simple path traversal that allows threat actors to execute code on unpatched OFBiz systems. The exploit is dead simple and works by adding a semicolon (;) after a public URL and then a private URL the attacker wants to access. Using carefully selected private URLs, attackers can bypass authentication and execute code on the server. According to the SANS Internet Storm Center, one of the threat actors exploiting the bug is a Mirai botnet.
Rockwell vulnerability: Claroty researchers have found a way to abuse the CIP protocol and bypass security isolations in Rockwell Automation ControlLogix PLCs.
Elastic security updates: Elastic has released security updates for its APM and Kibana servers.
KnowBe4 vulnerabilities: British pen-test shop PenTest Partners has discovered two vulnerabilities in the update mechanism of the KnowBe4 Windows client apps. The vulnerabilities could have allowed threat actors with access to a compromised system to elevate their privileges and run malicious code through the security company's app. PenTest Partners says the company downgraded the vulnerabilities at the beginning but then accelerated a fix after they contacted its CEO.
Atlassian plugin vulnerabilities: Cyllective researchers have discovered 53 vulnerabilities across multiple plugins listed in the Atlassian store. For now, they've published details on five while the rest are being patched.
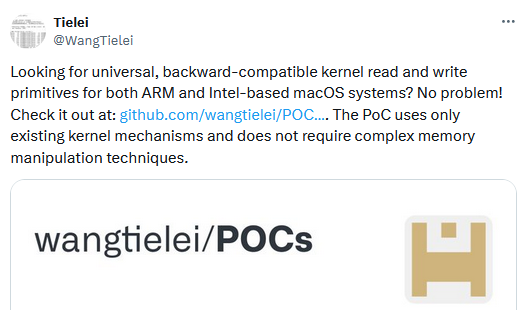
AppleTalk PoC: Security researcher Wang Tielen has published a PoC for CVE-2024-27878, a vulnerability in the AppleTalk Session Protocol (ASP) patched last month that allows macOS apps to run arbitrary code with kernel privileges.
Infosec industry
New tool—PANIX: Elastic security researcher Ruben Groenewoud has released PANIX, a customizable Linux persistence tool.
New tool—Huntsman: Security consultant MLCSec has open-sourced Huntsman, an email enumerator, username generator, and context validator providing detailed coverage of the hunter.io, snov.io, and skrapp.io APIs.
New tool—smbtakeover: SpecterOps' Nick Powers has published smbtakeover, a tool to unbind and rebind 445/tcp on Windows without loading a driver, loading a module into LSASS, or rebooting the target machine. More in Nick's blog post.
Tool update—TruffleHog: TruffleHog can now detect leaked secrets and tokens inside deleted or private GitHub commits and repos. This is thanks to a new technique known as Cross Fork Object Reference.
Threat/trend reports: Cloudflare and Wordfence have recently published reports covering infosec industry threats and trends.
New SentinelOne CISO: Security firm SentinelOne has named Alex Stamos as its new Chief Information Security Officer (CISO). Stamos previously served as CISO for Yahoo and Facebook. Stamos joined SentinelOne last year after the security firm acquired the Krebs Stamos Group. He's been SentinelOne's Chief Trust Officer since the acquisition.
ACM SIGCOMM 2024 videos: Talks from the ACM SIGCOMM 2024 security conference, which took place over the weekend, are now available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss what the widespread disruption caused by CrowdStrike's faulty update tells us about how useful cyber operations are for war.
In this podcast, Tom Uren and Patrick Gray discuss the Israeli government seizing documents from NSO Group so that they couldn't be shared with opposition counsel in a US lawsuit during discovery. It's a terrible look.
The Risky Business team has recently started publishing video versions of our podcasts. Below is the main weekly show, with Pat and Adam at the wheel!




